Back to blog
Auth0 2024 Pricing Update: What They’re Hiding About the Real Cost
Auth & identity
Sep 25, 2024
Author: Stytch Team

Today, several pricing changes were announced for Auth0. Since Okta acquired Auth0 in 2021, most adjustments have resulted in rate increases for enterprise and startup customers. However, today’s changes deserve more attention as they appear, on the surface, to provide significant value.

The changes are described as a benefit to the customer. Specifically, they’ve raised the number of included monthly active users (MAUs), provide access to passwordless features, and claim to now include “unlimited” Okta SSO Connections". But a closer examination of these changes and their pricing terms reveal that a lot of the bait-and-switch tactics Auth0 has become notorious for are even more egregious.
Let’s evaluate some of these claims further to see what you’re actually getting with Auth0’s new pricing.
Does Auth0 really offer Unlimited Okta Connections?
Auth0's promotion of Okta Connections—a type of Enterprise SSO connection—as 'unlimited' seems too good to be true. And unfortunately it is. If you look closer at the terminology and what’s defined as an "Okta Connection," you'll find that the only connection type with unlimited usage is a specific variation of Okta OIDC connection configured via an "Okta Workforce" setup.
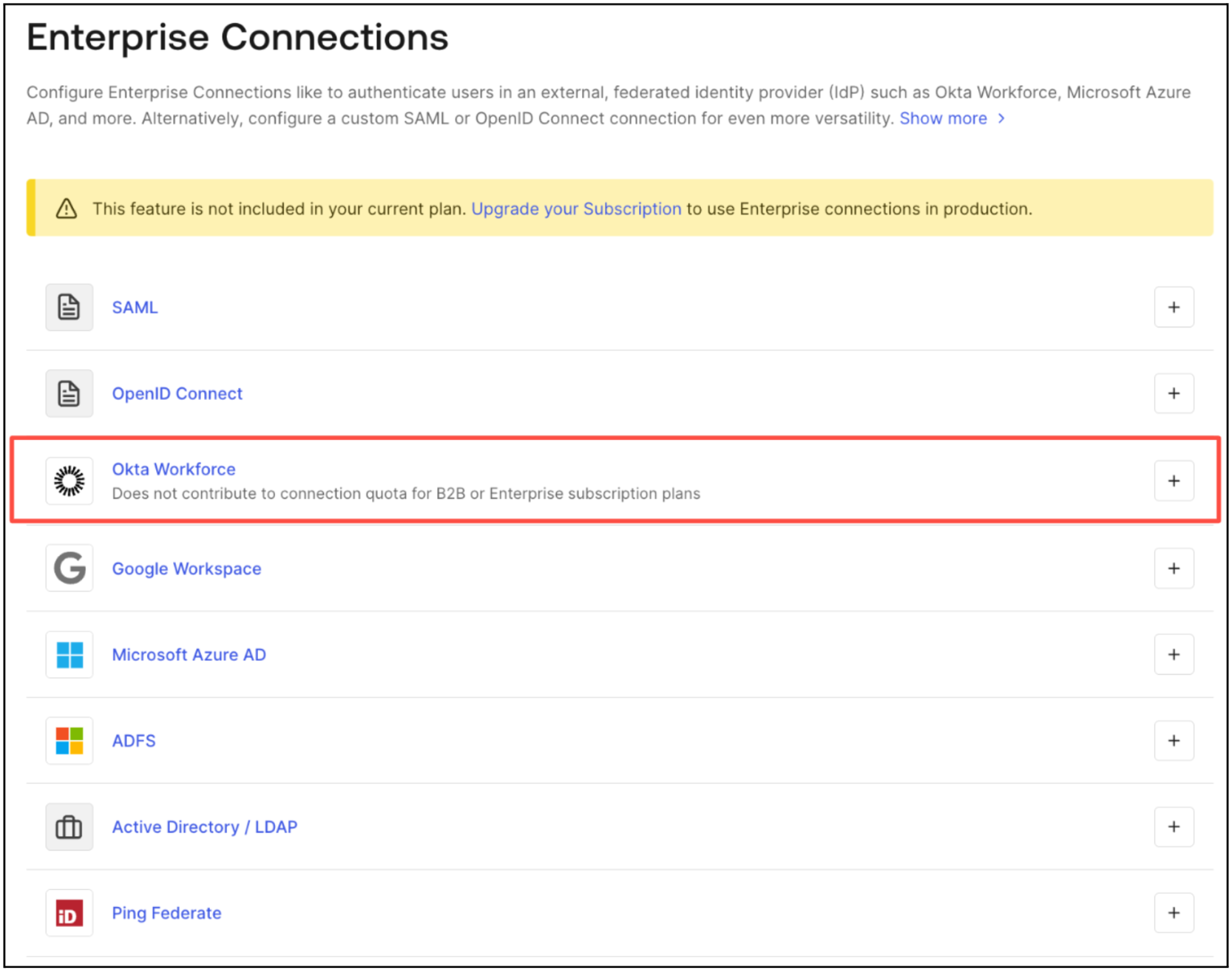
This matters because, if you're supporting SSO for your B2B SaaS application, there are two key elements not included that actually make up the bulk of your costs:
1. Okta SAML connections are an additional, undisclosed amount
The offer only covers Okta OIDC connections, which, according to our data, typically represent less than 10% of all SSO connections. In other words, when a customer requests Enterprise SSO support, they are more likely to require a SAML connection, which is not covered by this offer. You’ll still need to pay for SAML connections with Auth0, but they won’t tell you how much those connections cost unless you speak directly with sales. Pricing isn’t disclosed on their site.
2. OIDC and non-Okta SAML connections are also an additional, undisclosed amount
This offer does not include connections for providers like Google, Ping, or Azure. Once again, Auth0 does not disclose the pricing for these connections, making it difficult to estimate the actual cost of using them.
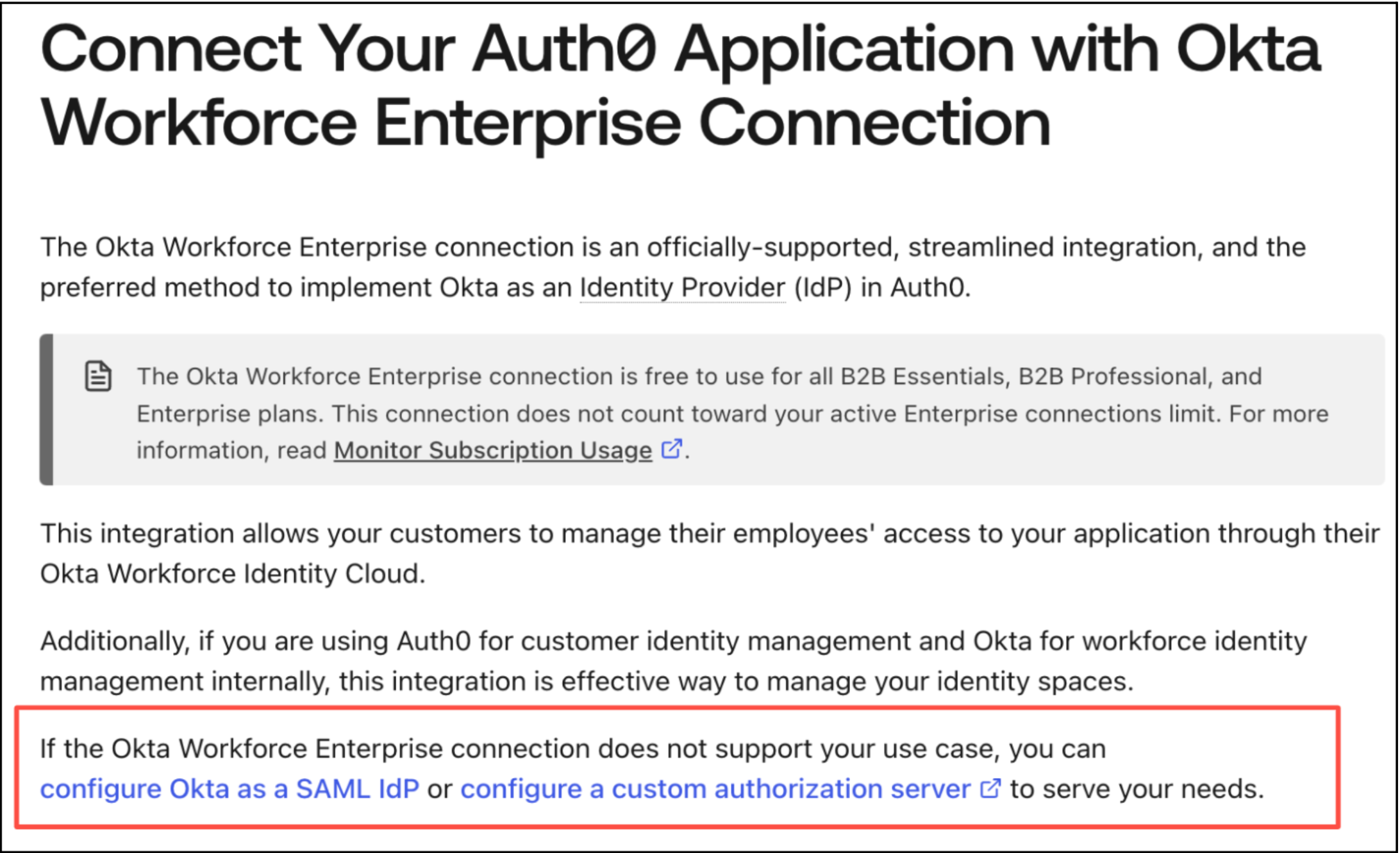
In other words, 'Unlimited Okta Connections' really means something more like "a trivial discount on some of your Enterprise SSO connections in order to hide the costs of your other primary SSO connections. And we'd rather not share what those cost are unless you talk to us live."
What’s hiding behind the increase in “free” MAUs?
Another key update from Auth0’s pricing changes is the increase in monthly active users (MAUs) included in the Free plan, from 7,500 to 25,000.
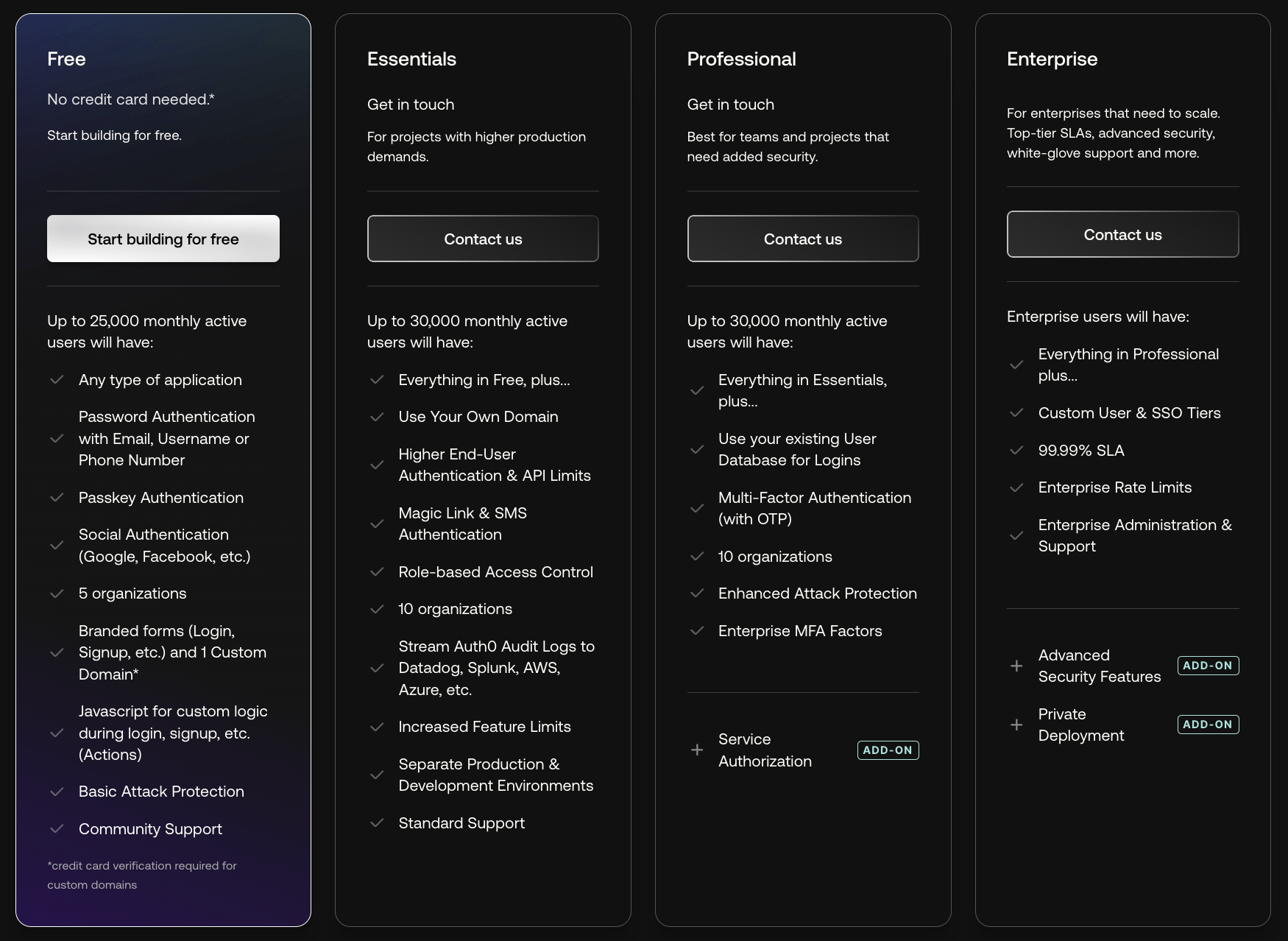
This is a 3X increase, which might seem generous at first glance. However, what they don’t tell you is that you can’t actually use that plan if any of the following conditions apply:
- You want to use your own domain (rather than something like myapp.auth0.com)
- You need multi-factor authentication (MFA)
- You need roles & permissions (RBAC)
- You need performant bot protection
- You want support beyond their community forum
- You want more than 5 organizations
- You want more than 5 SSO connections that aren’t Okta OIDC
- And more than a dozen other exceptions…
If you’re just testing Auth0 and don’t need any of these additional features, the increase in free MAUs is a welcome improvement. However, if you’re building a production app or even validating a proof of concept, then the Free plan is likely off the table and these changes won't matter to you.
Unfortunately, the caveats don’t end there. You also need to consider the following:
- There are hard caps on MAUs in Auth0's self-service plans: If you look closer at Auth0’s pricing plans, you’ll find a hard cap of 30,000 MAUs for B2C and 10,000 MAUs for B2B. That’s a pretty low limit for a growing app. At Stytch, we’ve seen engineering teams that were with Auth0 face large unexpected surges in annual costs—sometimes from around $3k to high five-figures or low six-figures—when they hit these limits. Worse, they often feel completely blindsided by these hidden pricing details, finding themselves forced into expensive enterprise agreements just as their app gains traction, with neither the time nor resources to migrate away.
- MAU pricing gets very expensive beyond Auth0's Free plan: Auth0’s MAU pricing becomes quite expense once you move beyond the Free plan. For example:
- B2C Pricing: You’ll pay 7 cents per MAU on the Essentials plan and it shoots up to 16 cents per MAU on the Professional plan.
- B2B Pricing: You’ll pay a whopping 23 cents per MAU on the Essentials plan and 24 cents per MAU on the Professional plan.
When you exceed the 30,000 MAU threshold for B2C or 10,000 MAUs for B2B, quotes typically rise to 30 cents or more per MAU.
Conclusion: More of the same obfuscation
Auth0’s latest pricing changes are positioned as offering more value and flexibility, but this really only applies to simple starter apps using the Free plan. Any actual improvements to pricing are overshadowed by what seems to be a continuation of their strategy to obscure the true costs and the various ways you’ll outgrow the Free plan’s limits. It feels like a classic bait-and-switch, where engineers are lured into investing heavily in Auth0 before realizing that much of the terminology (e.g., "Unlimited Okta Connections") is designed to make them think they’re getting a better deal than they actually are. This approach often leaves developers stuck with Auth0, facing significant unexpected costs at a time when migration has become too expensive and difficult.
We had hoped this pricing overhaul would address some of Auth0’s price transparency issues that have historically misled developers, but instead, they seem to have doubled down with this latest revision.
See how Stytch compares to Auth0
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.