Back to blog
Evaluating Auth0 alternatives for authentication and authorization
Auth & identity
Oct 3, 2023
Author: Stytch Team

Auth0 is a popular auth provider offering numerous authentication methods and access management features.
Founded in 2013, Auth0 became a popular user authentication choice over the past decade. Since being acquired by Okta in 2021, however, many developers have grown frustrated with the platform.

Reasons to consider Auth0 alternatives
There are several factors that spur developers to search for Auth0 alternatives.
Limited UI/UX flexibility
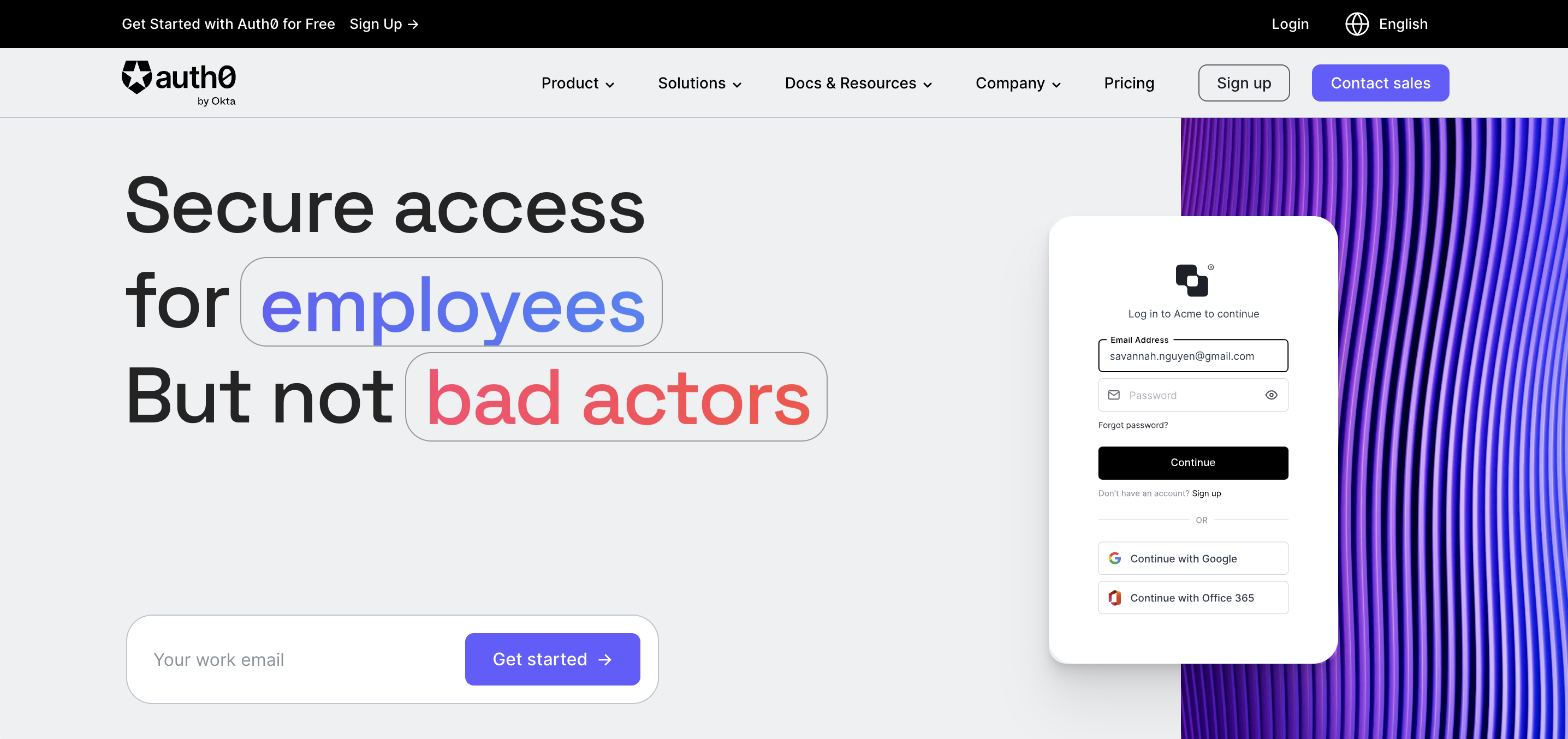
Auth0’s Universal Login offers few customization options and requires a redirect to their domain, affecting user experience and lowering conversion rates.
Their authentication logic also doesn’t sit within your application’s backend, which results in a heavy reliance on Auth0’s Actions. But because actions don’t easily allow for a lot of the things developers want to do, they end up having to write a lot of extra code to get their auth flow to function the way they want.
Lacking fraud prevention
Auth0’s fraud detection is basic, so depending on the sophistication of bot attacks your app faces, an additional security vendor might be necessary. This increases complexity and costs.
B2B limitations
Auth0’s approach to B2B multi-tenancy is not comprehensive, posing challenges for complex, scalable authentication needs. Based on a user-first rather than an organization-first data model, Auth0’s single sign on design makes it difficult to manage the growing enterprise requests for bespoke, org-specific auth settings as you scale.
Rising costs
Since its acquisition by Okta, Auth0’s pricing has continuously increased, becoming a growing concern for cost-sensitive businesses. There is also often a significant price jump to their enterprise plan, posing a challenge for growing businesses.
Feature gaps
Auth0 lacks conversion-focused, B2C features like Google One-Tap and WhatsApp OTP. Their user-first B2B data model, as mentioned above, also means you’ll likely need to spend time building enterprise-level customization features on top of your Auth0 integration.
Types of authentication solutions
Depending on your team’s use case, there are two types of authentication providers to consider.
Managed service
Managed services, like Stytch or Auth0, come with built-in best practices that save developer time and increase security.
By taking care of features like multi-factor authentication and fraud detection, managed services allow developers to focus on their core product while passively benefiting from compliance readiness and ongoing updates.
Open source
Open source identity and access management solutions like Keycloak allow developers to self-host their own auth solution. Although well-priced and fully-featured, the developer lift is heftier as you’ll need to bring your own database and manage ongoing provider updates.
Popular Auth0 alternatives
Below we’ve gathered four of the best alternatives to Auth0 (note: these are all managed services).
Option 1: Stytch
Stytch is a developer-focused customer identity and access management platform. Our infrastructure, fraud/risk suite, and account takeover-resistant authentication enable your company to build and manage secure access for B2C and B2B user management use cases.
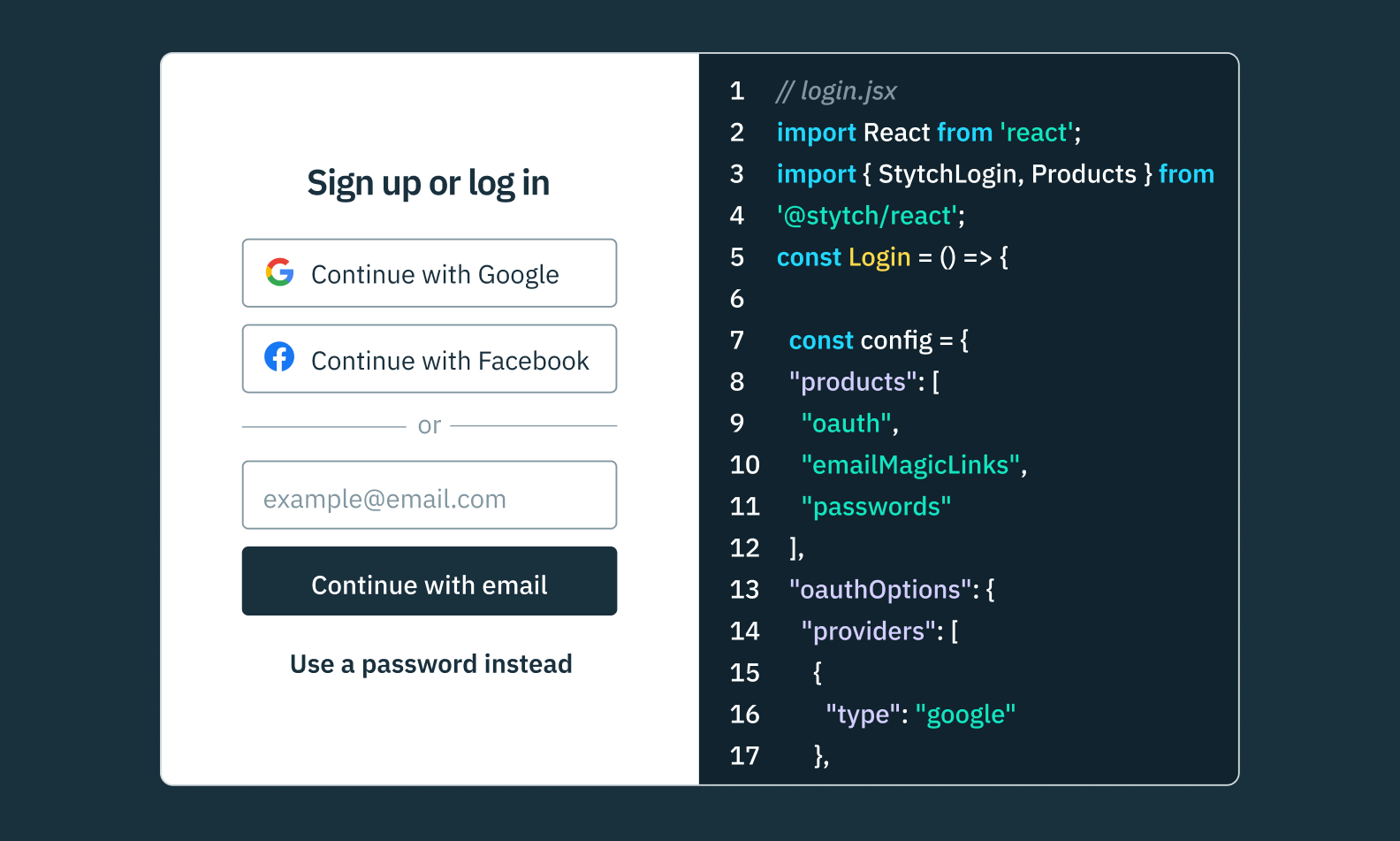
As an identity and access management solution designed for both startup and enterprise, we offer scalable user management for businesses at all stages.
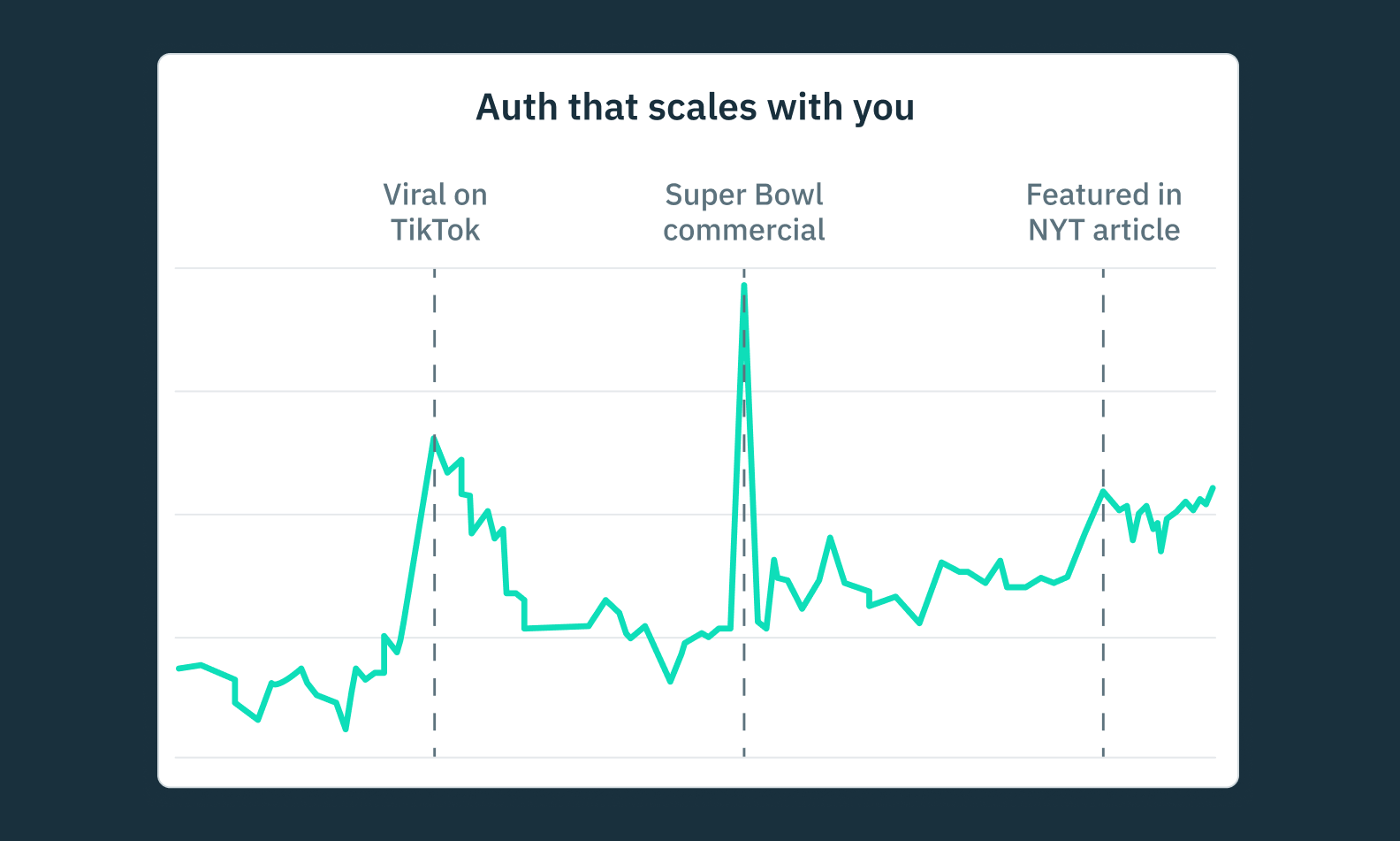
Whether you need passwordless authentication, social logins, multi factor authentication, single sign on multi-tenancy controls, or a more bespoke auth flow, Stytch’s SDKs and API can be used alone or alongside Device Fingerprinting that provides fine-grained traffic shaping and bot mitigation.
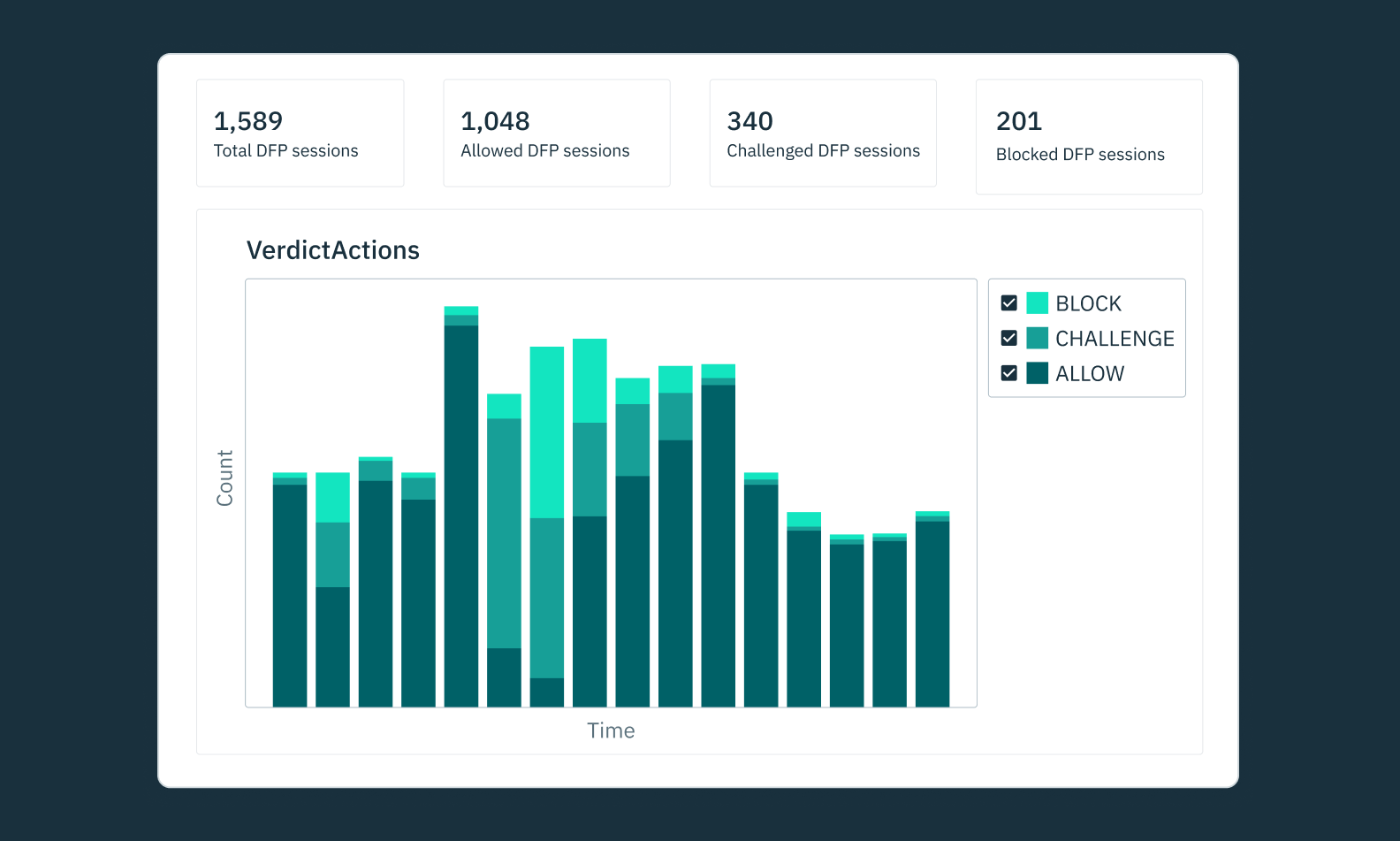
Key features of Stytch
- Comprehensive auth and fraud: Stytch offers both user management and advanced bot mitigation capabilities. This means that developers can use Stytch in three ways – auth, fraud, or auth and fraud.
- Flexibility to build for your use case: Customizable frontend SDKs and core APIs for custom-built UI flows and headless SDK methods.
- Future-proof infrastructure: Infrastructure with 99.999%+ uptime SLA, SMS/email provider failover, and account deduplication are built to handle customer growth.
- Consumer-centric B2C features: Passwordless authentication, passwords, social logins, Google One-Tap, and Whatsapp OTPs help seamlessly onboard and convert users.
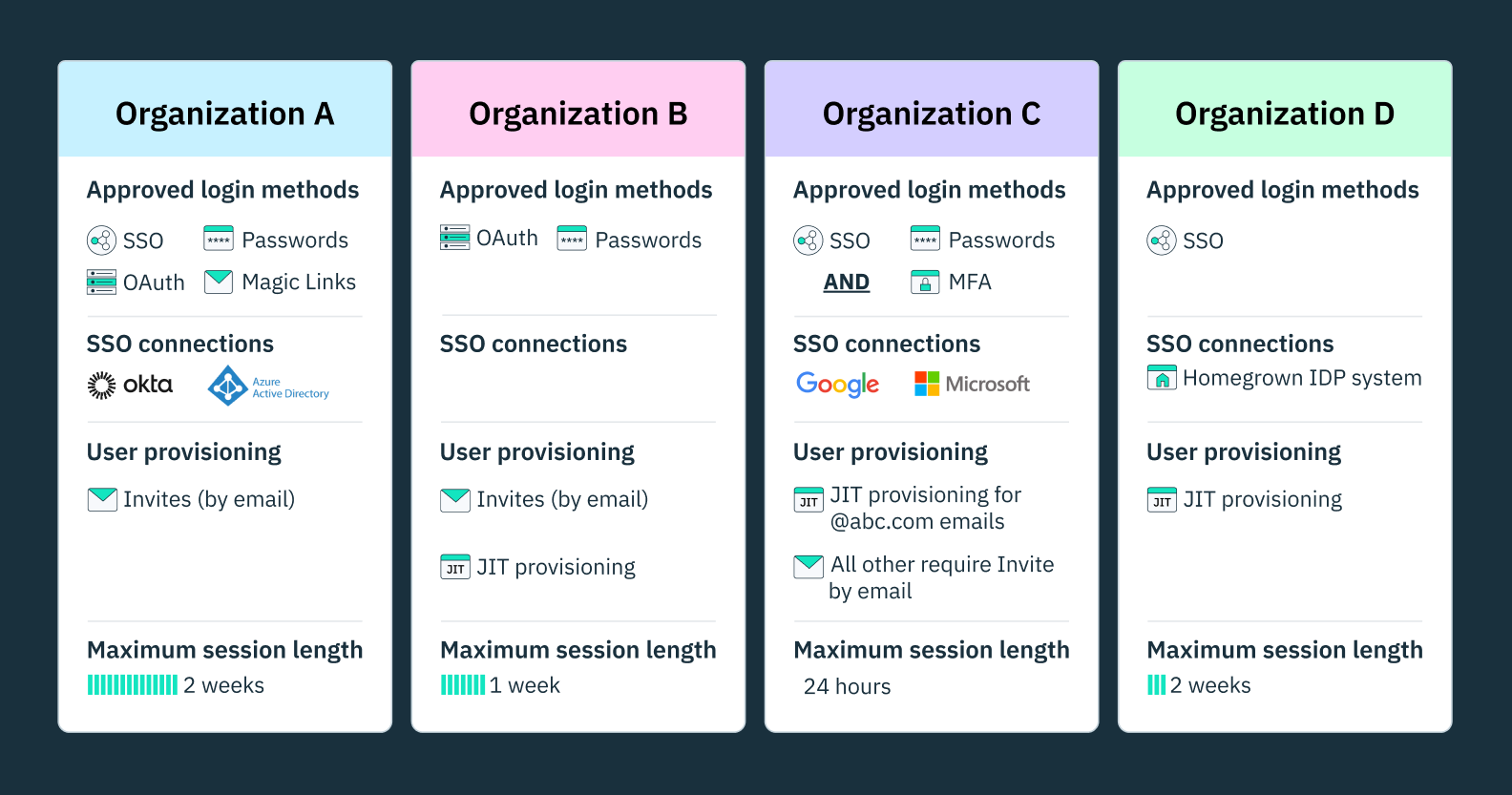
- Comprehensive B2B features: Our B2B platform includes single sign on with multi-tenancy and organizations built into the data model. It also includes just-in-time provisioning, discovery flows, enterprise onboarding, and self-onboarding features.
Because we’ve built our data models organization-first, it’s easy to customize single sign on requirements and flows on an organization-by-organization basis, as can be seen below.
Advantages over Auth0
- No need for external security vendors: With a Device Fingerprinting product that rivals industry leaders, Stytch’s comprehensive auth and fraud solution means one less vendor to manage.
- Greater UI/UX control: Build a native auth experience without redirects to Auth0’s domain.
- Scalable pricing with more features: If you are concerned about rising costs, Stytch pricing does not include the same price jump to enterprise plans as Auth0’s does and includes more features across the board.
Shortcomings
- Less out-of-the-box: Although we find that developers value the control from Stytch’s API-first model, if you’re looking to get basic authentication up and running quickly, Auth0 can be dropped in quickly, so long as you don’t need to customize.
- Self-implementation for uncommon MFA: Auth0 supports push notifications, voice call, Duo, and recovery code multi factor authentication on enterprise plans, whereas those features must be self-implemented on Stytch with our API.
Want auth without the headaches? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Conclusion
If you’re looking for an expertly-designed auth and fraud platform, Stytch is an excellent Auth0 alternative. Check out our Stytch vs. Auth0 side-by-side for feature comparisons.
Option 2: Amazon Cognito
Amazon Cognito provides identity services for applications hosted on the AWS ecosystem. It offers functionalities like user registration, authentication, and user data synchronization across devices. As an AWS offering, Cognito seamlessly integrates with other AWS services, offering a unified solution for developers deeply invested in the AWS stack.
Key features of Amazon Cognito
- AWS Integration: Cognito offers tight integration with the AWS ecosystem, with advantages like single billing and native support for AWS-based apps.
- Scalability: Built to handle AWS-level scale, Cognito is suitable for applications expecting rapid growth or high user loads.
- Customization: While not as flexible as Auth0 in terms of user interface customization, Cognito does offer some customization for workflows.
- Identity Pools: Provides the ability to federate identities from social identity providers like Facebook, Google, and even enterprise identity providers via SAML.
- Security: Strong security measures, including multi-factor authentication and encryption, although less focus on specialized fraud detection tools.
Advantages over Auth0
- Cost-effectiveness: Generally less expensive, especially for businesses already utilizing other AWS services.
- AWS Ecosystem: If your application is built around AWS services, using Cognito simplifies the architecture and potentially reduces latency.
Shortcomings
- Minimum Flexibility: Cognito is not as developer-friendly as Auth0 when it comes to customizing authentication flows or UI.
- Minimum Focus on Fraud Detection: While Cognito offers basic security features, it doesn’t have as robust a set of fraud detection capabilities as Auth0.
Conclusion
Although both Amazon Cognito and Auth0 offer robust solutions for managing user identity, the choice between the two often boils down to the specific needs of your application and your investment in the AWS ecosystem. Auth0 offers greater flexibility and specialized fraud detection tools, whereas Amazon Cognito excels in scalability and AWS integration.
Option 3: Firebase Authentication
Firebase Authentication is part of Google’s Firebase platform, a suite of services designed to help build mobile and web applications. Firebase Authentication aims to make it easier to add secure sign-in features to your web and mobile applications too, supporting a variety of standard identity providers like Google, Facebook, and Twitter, as well as email/password and phone number authentication.
Key features of Firebase Authentication
- Platform Ecosystem: Being a part of Google’s Firebase, Firebase offers seamless integration with other services like Firestore, Analytics, and Cloud Messaging.
- Client-Side Focus: Designed with a client-side architecture in mind, Firebase is particularly well-suited for mobile and web applications.
- UI Libraries: Comes with ready-made UI libraries for common authentication tasks, making it easy to get up and running quickly.
- Social Sign-In: Supports a variety of third-party identity providers right out of the box.
- Security: Offers basic security features like multi-factor authentication and account recovery.
Advantages over Auth0
- Simplicity: Generally simpler to set up and integrate into mobile and client-focused applications.
- Cost: The free tier is generous, making it a good choice for startups and smaller projects.
- Google Ecosystem: If you’re already using other Google services, Firebase Authentication integrates seamlessly.
Shortcomings
- Limited Customization: Not as customizable in terms of authentication flows and user experience compared to Auth0.
- Enterprise Features: Lacks some advanced enterprise features like detailed auditing and specialized fraud detection.
- Server-Side Limitations: Less suited for server-to-server authentication compared to Auth0.
Conclusion
Firebase Authentication is an excellent choice for projects that benefit from its simplicity, client-side focus, and integration with other Firebase services. However, Auth0 offers more depth in customization, enterprise features, and server-side capabilities.
Your choice between Firebase Authentication and Auth0 will depend on your specific needs, whether you prioritize ease of use and client-side features, or require more complex, customizable authentication solutions. Understanding the unique selling points of each will help you make an informed decision on an access management solution that aligns with your application’s requirements.
Option 4: Ping Identity
Ping Identity is an enterprise-focused identity management solution that offers single sign on, multi factor authentication, and API security among other features. It’s designed to offer a secure, seamless experience for both internal and external users, bridging the gap between various application types including legacy, cloud, and hybrid applications.
Key features of Ping Identity
- Enterprise Focus: Designed to meet the stringent requirements of large organizations, offering advanced compliance and governance features.
- Identity Governance: Includes a full suite of identity governance tools, something often lacking in competitors like Auth0.
- Wide Range of Integrations: Extensive out-of-the-box integrations, including support for older, legacy systems.
- API Security: Strong focus on API security, making it a suitable choice for businesses with extensive API integrations.
- Customization: High level of configurability, allowing businesses to tailor the service to meet unique requirements.
Advantages over Auth0
- Enterprise Readiness: Well-suited for large organizations with complex governance and compliance needs.
- Holistic Identity Governance: Provides a comprehensive set of digital identity governance tools for full lifecycle management of user identities.
- Legacy Support: Better equipped to handle businesses running a mix of legacy and modern application architectures.
Shortcomings
- Complexity: The enterprise focus means it can be overkill for smaller businesses or simpler applications.
- Cost: Generally more expensive, particularly for smaller businesses that don’t need all of the enterprise-level features.
- Learning Curve: Due to its extensive features and focus on enterprise-level customization, it may have a steeper learning curve compared to Auth0.
Conclusion
Ping Identity is an identity and access management solution that caters to large organizations with identity governance, compliance, and single sign on requirements.
If you are a smaller company that doesn’t require an enterprise-level, robust solution, however, you’re better off choosing a developer-focused identity platform that can be quickly and easily integrated.
In summary
When evaluating authentication providers ten years ago, Auth0 was the default choice. But today, developers have more customer identity and access management providers to choose from.
If you’d like to explore all the features of Stytch, in particular, click here start building for free.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.