Back to blog
A guide to passwordless authentication solutions by business vertical
Auth & identity
Nov 12, 2021
Author: Reed McGinley-Stempel

You’ve just decided to go passwordless (an excellent choice), and now it’s time to figure out which passwordless authentication solution is right for your business. There are many options on the table, including email magic links, SMS one-time passcodes, WebAuthn, OAuth, and multifactor flows using a combination of these methods.
To help you navigate options, we’ve compiled years of experience and expertise building passwordless authentication solutions (at both Stytch and Plaid) into a simple guide.
Essentially, which method you should choose comes down to two basic questions:
- What are the security requirements for your app given the sensitivity of the user data you work with? And,
- Who is your target audience, and how do they engage with your product?
Below, we break these points down one by one and explore how they play out in different business scenarios and use cases.
Keep in mind, while we use specific verticals we’ve worked with as examples—including e-commerce, fintech, healthcare, B2B SaaS, and B2C tech—our recommendations apply across industries and for a much wider swath of businesses.
User data sensitivity and security requirements
First, consider the following questions:
- Are you involved with storing or handling sensitive customer data?
- Are you in a heavily regulated industry?
- Do you consider your industry to be vulnerable when it comes to fraud and cybersecurity attacks?
If you answered “yes” to any of the above, then you’re among companies like fintech, healthcare providers and government agencies that access sensitive user data such as bank account information and medical records.
Industries like yours tend to be highly regulated and allow customers a wide range of activities, from facilitating mobile transfers and cryptocurrency trades to scheduling and accepting payments for medical procedures. Security is likely a top priority for your business, and you should opt for higher-friction methods of authentication (we’ll get into what that means later in the guide).
If you answered “no” across the board, you’re likely operating in a highly competitive, crowded B2C market like e-commerce, media, entertainment, or edtech.
You might face challenges related to rising customer acquisition costs, high cart abandonment rates, and low account creation and user engagement. But overall, you access less sensitive data, and—while security is still a priority—your primary focus is on maximizing customer conversion. You’re better off building a low-friction yet secure passwordless authentication experience, which can help move the needle when it comes to succeeding in competitive B2C markets.
How your target audience engages with your product
There are hundreds of ways you can segment your audience, but when it comes to authentication, there are two key factors to consider:
- Audience demographics (namely age) and
- Behavior related to mobile and desktop device usage
These two data points are strong indicators of how your audience will interact with your application. They’re also often correlated. For example, research has shown that people below the age of 25 use their phones more frequently and are likely to have them in close proximity at all times.
Depending on whether you offer a desktop- or mobile-first product—and whether your customers are likely to have their phones nearby while going through your onboarding flow—your path to building a great user experience and maximizing conversion can vary significantly.
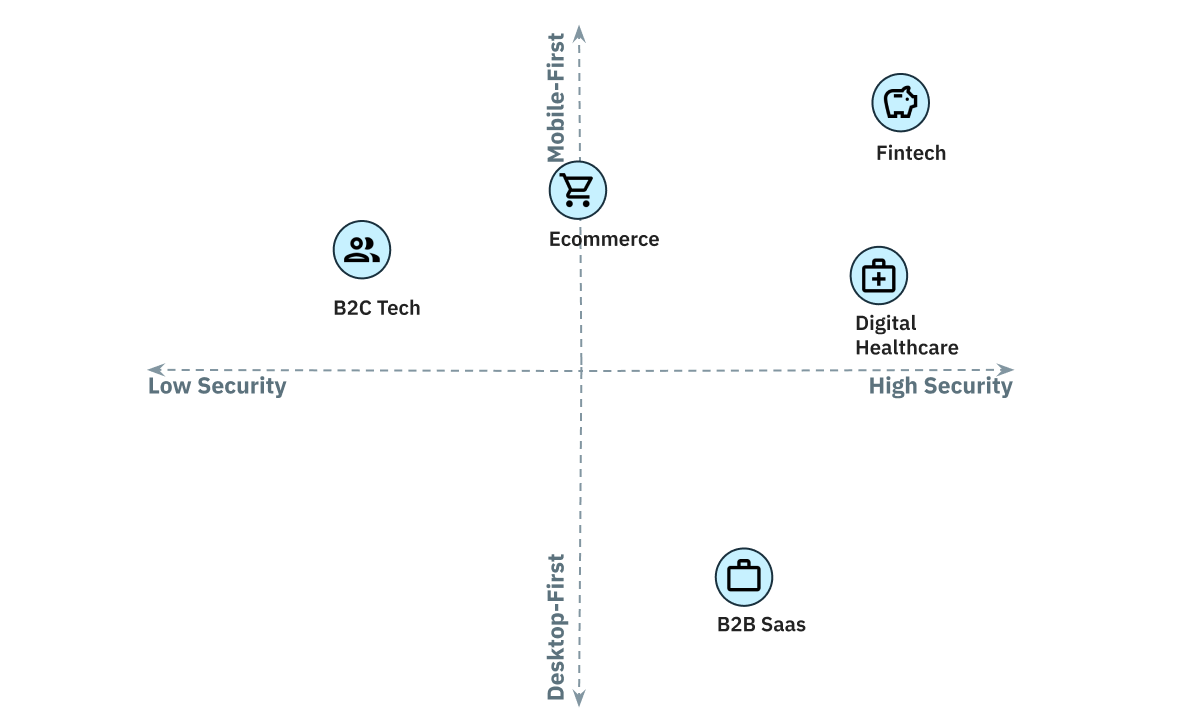
Toward that end, we’ve put together a helpful graph that plots common verticals along axes related to data sensitivity and audience reach. While this simplistic view won’t capture all edge cases, it’s a helpful starting point when evaluating your authentication needs:
Taking this a step further, we’ve also plotted the most popular passwordless authentication methods using similar criteria:
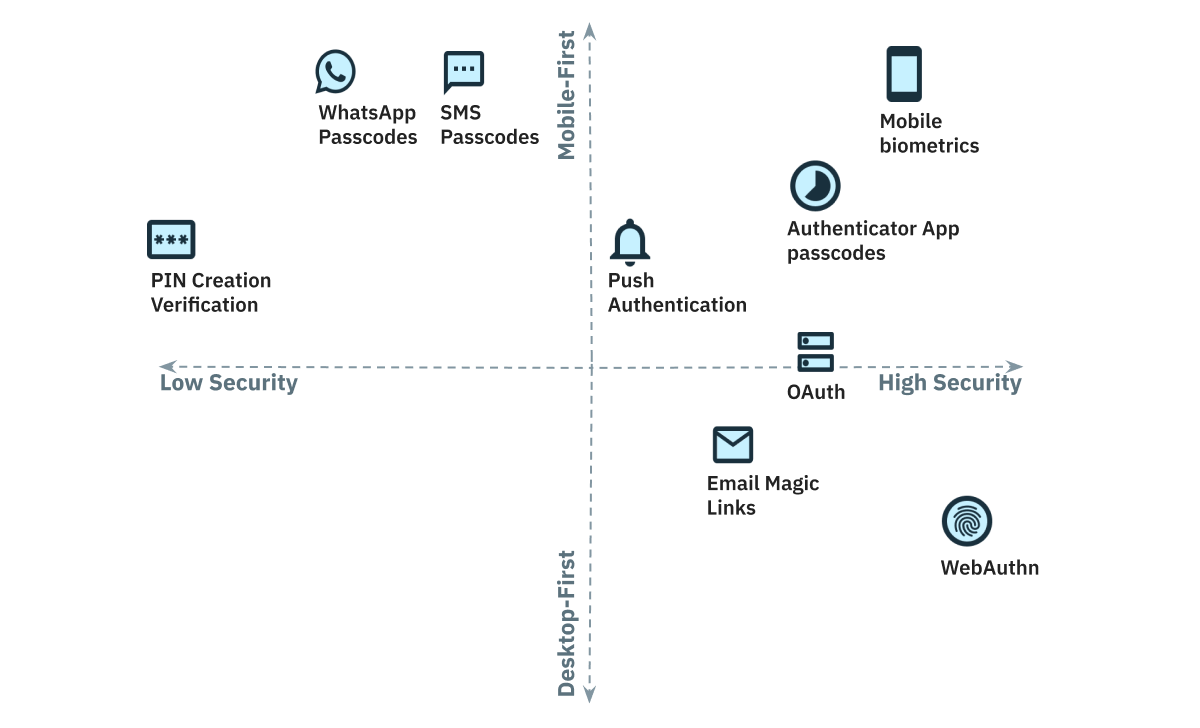
While passwordless authentication options are unquestionably more secure than password-based authentication (and thereby suitable for businesses that have access to all types of sensitive data), you can further distinguish them into remotely accessible (e.g. SMS, email) and device-tied factors (e.g. mobile biometrics). Remotely accessible passwordless factors are typically used for primary authentication, while device-tied factors are considered even more secure and are typically used for 2FA.
Another thing to keep in mind when choosing one or several passwordless authentication solutions is that methods are often designed with specific users in mind. For example, as you can see in the above matrix, SMS and authenticator app passcodes are designed for mobile-friendly applications, while email magic links and WebAuthn make for great user experiences via desktop.
You can read about each passwordless authentication option in detail in our comprehensive guide to authentication.
Now that you have a sense of how both your business and popular passwordless auth methods measure up when it comes to security and audience, let’s explore our cheat sheet on the best passwordless authentication solutions for each vertical:
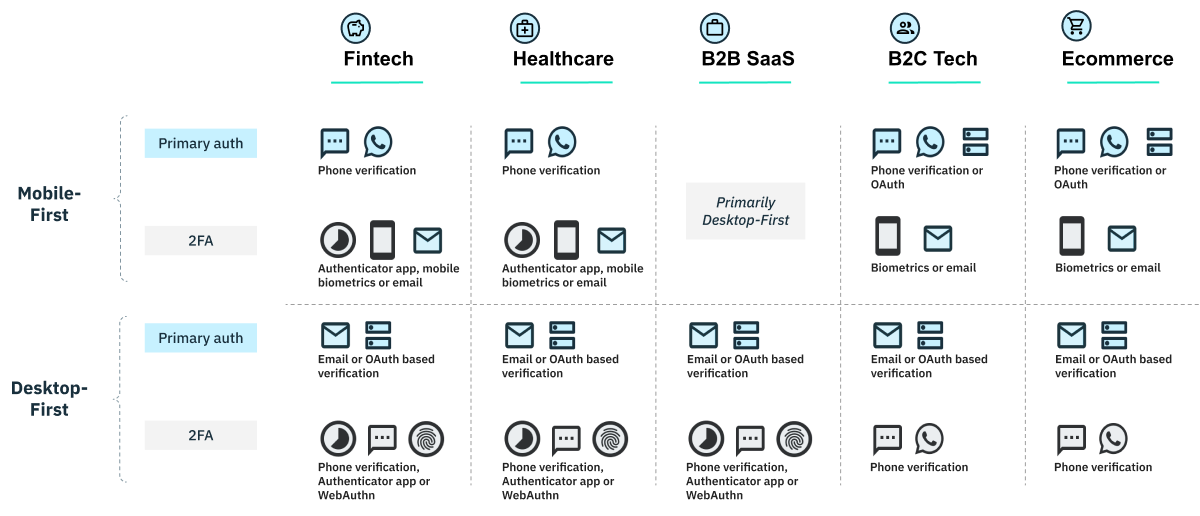
We developed this data over more than two years of research and conversations with customers and leads, and we’re excited to share it publicly to help make your authentication journey easier.
Before we dive into our specific recommendations, it’s worth reviewing a couple general tips that apply across verticals:
- While MFA is your friend, we recommend introducing friction only when truly necessary using just-in-time authentication.
- Don’t be afraid to let your audience choose how they want to be authenticated. Take Square’s Cash App as an example -- they let their users decide whether they want to sign-up/login with their email or phone number.
In the following sections, we’ll go vertical by vertical and take a closer look at how we arrived at each recommendation.
Fintech and digital healthcare
Objective: Maximize security while maintaining higher conversion rates compared to password-based authentication
For mobile-first, consumer-facing applications in fintech and healthcare, we recommend a low-friction yet secure authentication method as a primary factor and a much higher friction authentication method in an optimized 2FA flow.
Specifically, we recommend SMS one-time passcodes as a primary authentication method—or WhatsApp passcodes if your target audience is outside North America. Using SMS/WhatsApp one-time passcodes for primary authentication will help you achieve a 50%+ increase in conversion versus password-based methods (due to the auto-fill capabilities of iOS and Android) while still offering the security benefits of preventing password re-use and the associated account takeover risk. OAuth login options like Sign in with Google + Apple can also be great primary authentication options given their ease of use and the ways users frequently secure those core accounts.
For your secondary authentication method, we recommend using mobile biometrics or an authenticator app like Google Authenticator.
For desktop-first applications in fintech and healthcare, we recommend a combination of low-friction yet secure passwordless sign-up or login flows. These could include email magic links or OAuth for primary authentication and authenticator apps or WebAuthn for 2FA.
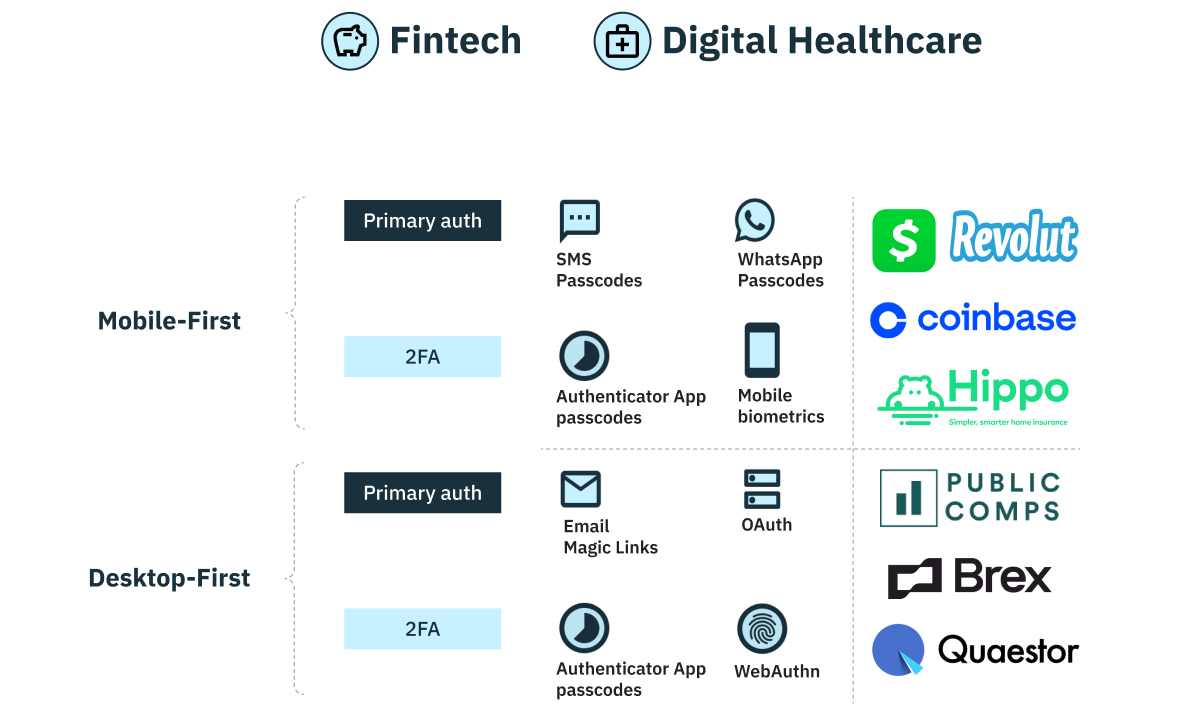
Note: The brands in the above and below tables use passwordless authentication methods for either primary authentication or 2FA.
E-commerce and B2C tech
Objective: Maximize customer conversion through a low-friction yet secure passwordless authentication experience
Similar to fintech and healthcare, for mobile-first e-commerce and B2C tech applications, we recommend a low-friction yet secure authentication method such as SMS or WhatsApp one-time passcodes. Again, OAuth login options like Sign in with Google + Apple can also be great primary authentication options given their ease of use. If it’s necessary to add 2FA for your use case, use mobile biometrics or a relatively low-friction PIN verification method.
For desktop-first applications, we recommend introducing a combination of low-friction, high-security passwordless user sign-up or login flows. These could include email magic links or OAuth for primary authentication and SMS or WhatsApp passcodes for 2FA.

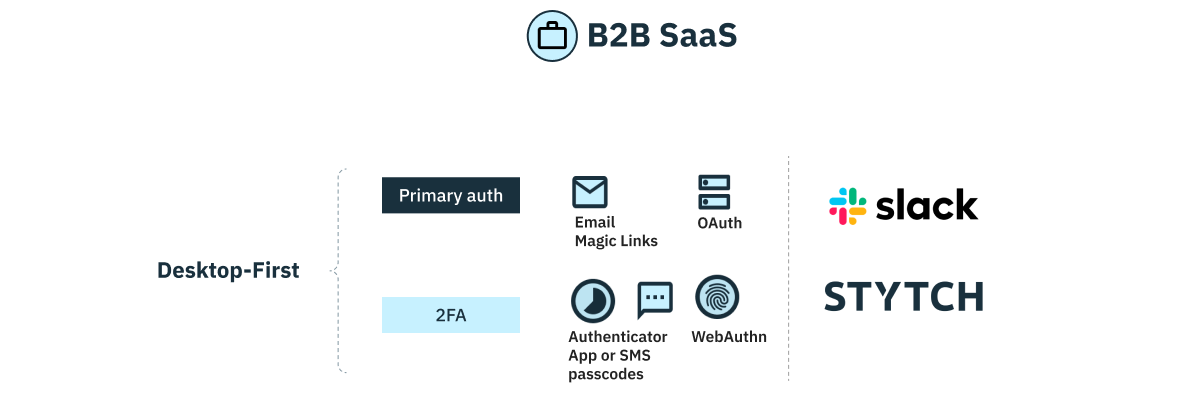
B2B SaaS
Objective: Strike the perfect balance between protection and ease of use for B2B customers
For desktop-first B2B SaaS applications—which comprise the majority of this industry—we recommend a combination of low-friction, high-security passwordless sign-up or login flows. This could include email magic links or OAuth for primary authentication and either authenticator apps or SMS passcodes plus WebAuthn for 2FA, depending on how much friction you want to introduce to your user onboarding flows.
Continuing your authentication journey
Once you’ve built your user onboarding flow, that doesn’t mean your authentication journey is over. In fact, authentication will underpin and impact all user interactions with your application moving forward—so why not get creative with your solutions?
With embedded authentication methods, you can create smooth user experiences by weaving authentication solutions seamlessly into all interactions with your app. Stytch offers several options, including:
- Embeddable magic links which embed authentication into any customer communication channel—including SMS, email, and WhatsApp—to always provide a logged-in experience to your users
- Embeddable OAuth solutions which embed authentication methods like Google Sign-In directly into customer communications
Learn more about our passwordless authentication solutions
Looking for more information on the passwordless methods mentioned in this guide?
Jump into Stytch’s API docs to get a closer look at our industry-leading products—or join our Slack community to chat with fellow engineers.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.