Back to blog
Introducing TOTP Authentication for Next-Level Security
Product
Jan 24, 2022
Author: Reed McGinley-Stempel
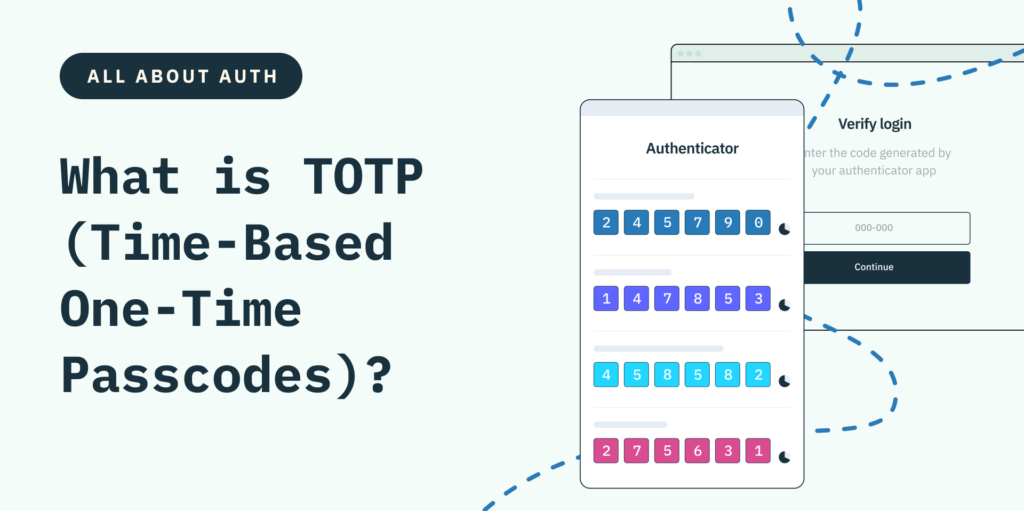
Today, we’re excited to introduce TOTP (time-based one-time passcodes), an important passwordless two-factor authentication option that can be used in situations where you need high security assurance. TOTP authentication solutions are ideal for particularly sensitive use cases that are also highly attractive to attackers in terms of the potential payoff they offer–think money movement in fintech or cryptocurrency spaces or access to a company’s HR or payroll information. With Stytch, developers can now embed TOTP into their authentication flows in minutes rather than months.
How TOTP authentication works
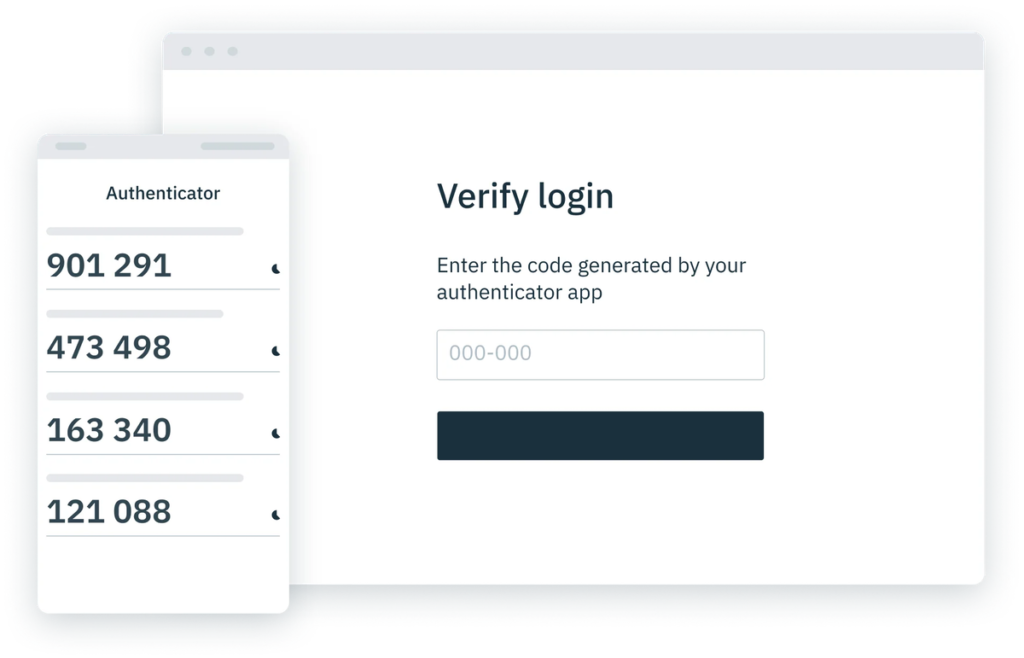
When integrated as a second authentication factor, TOTP serves as an additional safeguard by requiring users to prove possession of their device. It works by generating a one-time passcode that’s based on the current time and a shared secret between an authenticator app like Google Authenticator and the server (in this case, Stytch).
Users, who must have an authenticator app downloaded on their device, are asked to input the unique passcode within a certain period of time, usually 30 seconds, as evidence of their identity. Once the user supplies the TOTP code, developers can use Stytch’s /totps/authenticate endpoint to verify that passcodes are valid and, ultimately, grant users access.
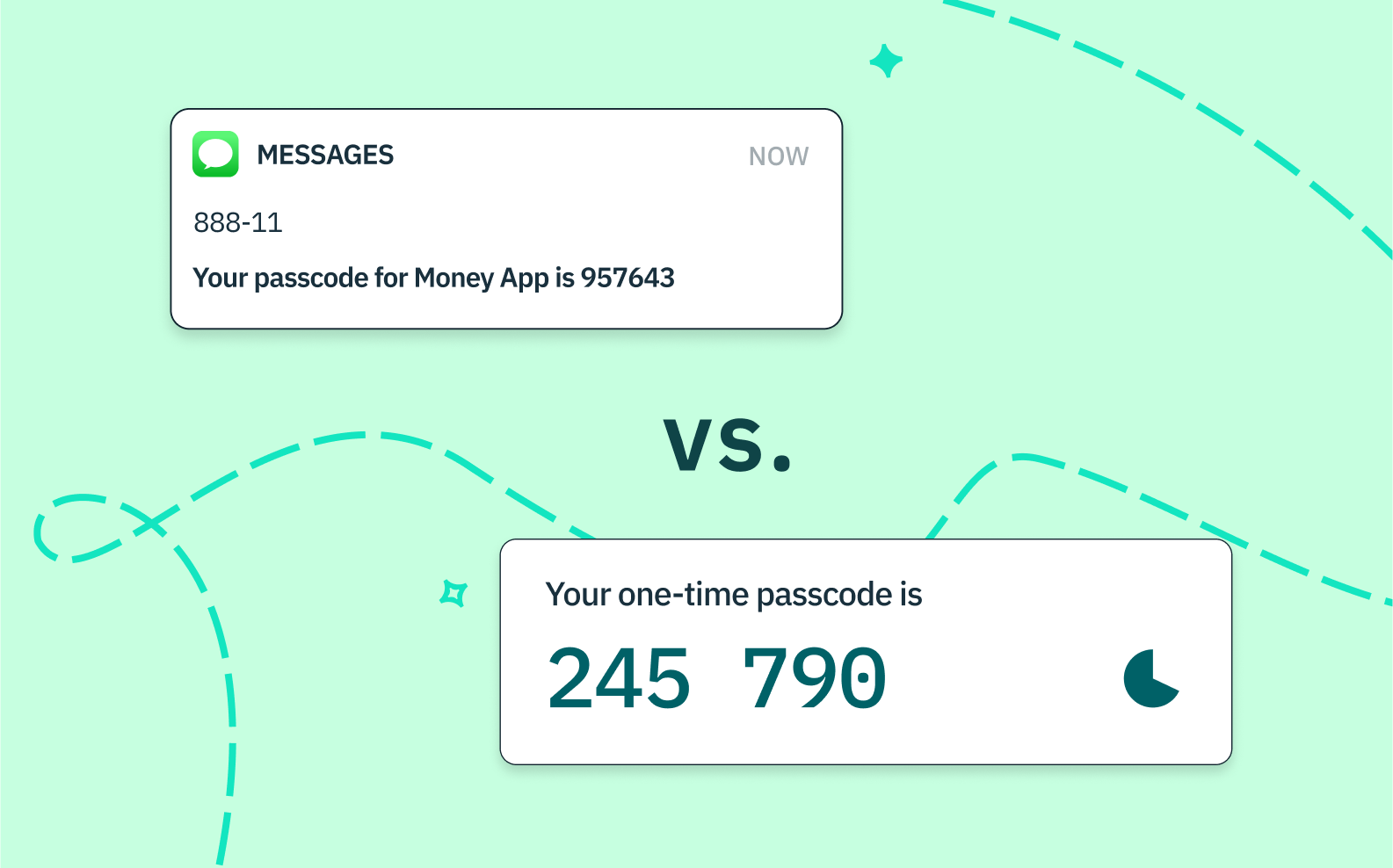
TOTP vs. SMS passcodes
If you’re familiar with SMS one-time passcodes (another great passwordless solution for most use cases), you may be wondering why you would opt for TOTP instead.
It’s true that SMS passcodes are very convenient, and many users are familiar with them. Anyone who has placed an online order with a business that uses Square as its point of sale system, for example, has interacted with SMS passcodes. In this instance, users receive a text with a unique code that unlocks access to the payment information associated with their Square account, allowing them to complete a purchase. iOS and Android devices even auto-fill passcodes with a simple permissioning click. There’s nothing for users to remember, and friction is minimal; they just need to be in possession of a device linked to their phone number.
While it’s possible that a hacker could steal a user’s phone number (called “SIM swapping” or “porting”), the significant effort and resources required to successfully pull off such an attack usually makes it a nonstarter. In other words, for low-to-moderate risk use cases, the cost generally outweighs the relatively modest potential reward.
When elevated risk requires elevated security
If, however, there’s a potential for a lucrative payoff, such as use cases involving large volumes of money movement or sensitive HR records, a hacker’s cost-benefit analysis may tip in the other direction. In 2021, for example, hackers carried out sophisticated phishing attacks against Coinbase users. By tricking them into sharing their phone numbers and other personal credentials, hackers were able to intercept SMS passcodes and access users’ accounts.
TOTP evades the threat of SIM swapping by removing users’ phone numbers from the equation, tying authentication to an app on their local devices instead. By welding the one-time passcodes being generated to your local device, it no longer matters whether a phone number is stolen as the device remains with the user. This is why cryptocurrency custodians like Gemini and other applications with high-risk interests leverage the TOTP standard.
As an added benefit of this design, TOTP can function offline, which may be important for users in areas of poor or no connectivity like airplanes. Meanwhile, SMS passcodes remain a great authentication option for low- to moderate-risk use cases given how convenient they are for users.
Time for Stytch
Stytch makes building a TOTP authentication flow fast and easy, so you can focus on your core competencies. Our product works out-of-the-box with any authenticator app that follows the TOTP protocol (e.g., Google Authenticator, Authy, Microsoft Authenticator, etc.), giving your users the freedom of choice without any additional development on your part. If you’re interested in integrating TOTPs into your apps, you can sign up for a developer account here to get started or contact support@stytch.com.
Build auth with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.