Back to blog
Scalper bots: The box office boom no one wants
Auth & identity
Dec 29, 2023
Author: Alex Lawrence
Ticket scalpers have a mixed reputation. On the one hand, they might be your one chance at attending that sold-out Taylor Swift concert you’ve been dreaming of, but on the other, you’re getting ripped off to high heaven and back, dropping 5x what was originally paid.
Scalper bots, on the other hand, likely won’t be getting you into that concert of your dreams. These malicious bots are a significant threat that can mimic human users and disrupt online platforms by buying up products and tickets at an alarming rate. This scalper bot ‘routing’ of the box office hurts event organizers, ticketing companies and, of course, the Swiftie dreamer looking for their golden ticket.
This article looks at the bad bots known as scalper bots (or scalping bots), examining their nature, the problems they cause, and the strategies that can be used to combat them effectively.
Understanding scalper bots
Scalper bots, in simple terms, are automated software scripts specifically programmed to purchase items faster than human users. They are predominantly used in ticket scalping and retail, where high-demand products are bought quickly for resale at inflated prices. These bots represent a significant portion of bot traffic on many e-commerce platforms, often leading to rapid sellouts of popular items (much to the dismay of genuine customers).
The use of these scalping bots has become increasingly prevalent in recent years, leading to a growing number of complaints from customers and online retailers. Whether it’s trying to buy tickets for a concert or sporting event, limited edition sneakers, or high-demand tech products like new iPhones, scalper bots leave a trail of frustration and disappointment in their wake.
The evolution of online scalping and ticket bots
Unlike traditional scalpers who physically bought and resold tickets, modern scalpers use scalping bots to automate the process. Scalper bots are capable of executing large-scale purchases within seconds of an item’s release, a feat impossible for a human user. This evolution has not only made scalping more efficient but also more widespread, affecting a broader range of industries, from gaming to live events.
How scalper bots work
Scalper bots automate the process of buying products or tickets through rapid and repetitive access to web pages. They frequently use auto-refresh features to monitor for new sales and act instantly to gain an advantage. These bots can mimic the browsing patterns of human users to evade detection, filling out online forms, navigating through ecommerce sites, and even completing purchases using saved credit card details. Such sophisticated automation makes it challenging to distinguish between genuine users and bots.
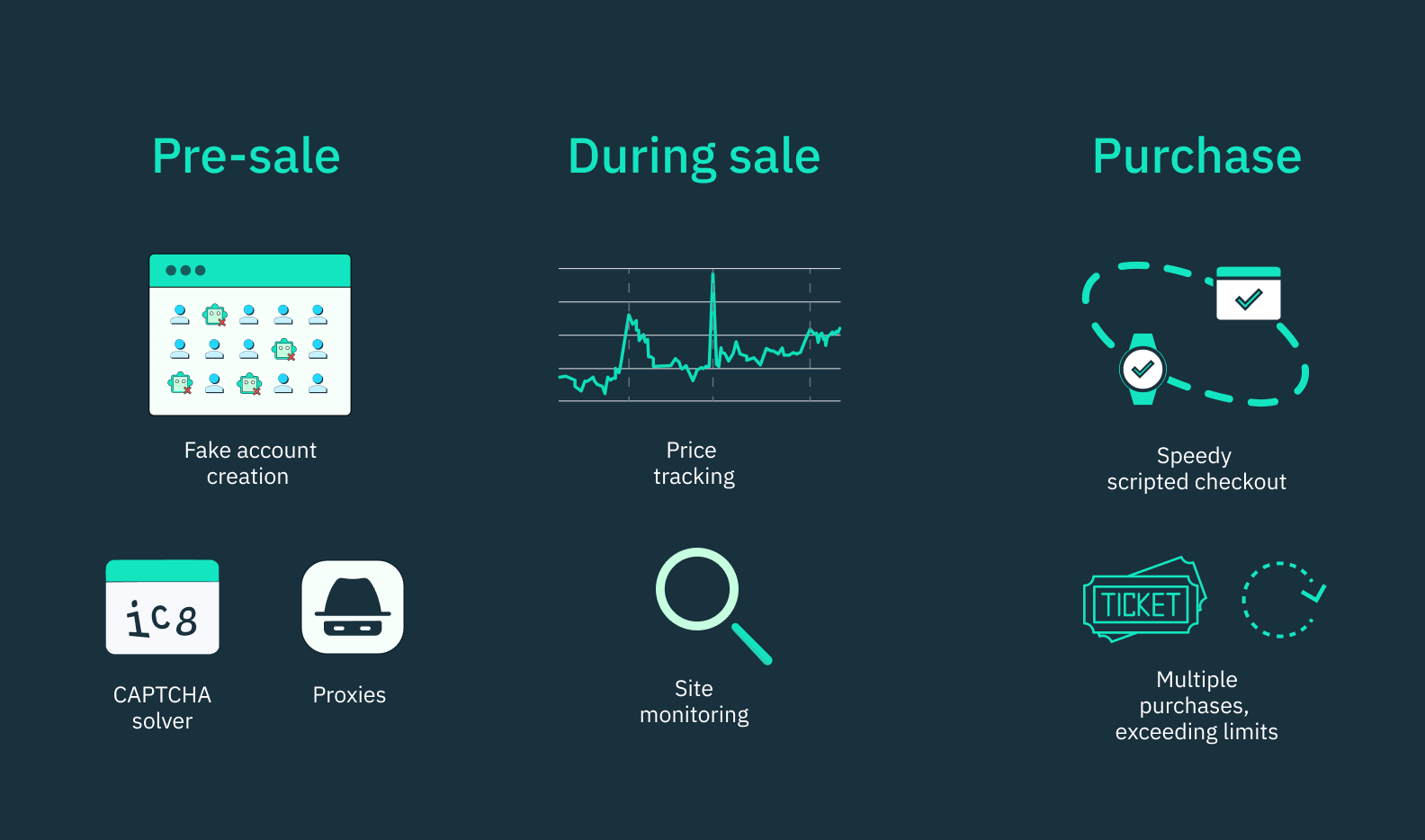
Specializations and types of scalper bots
There are various types of specialized scalper bots for different tasks and bot attacks. They include:
- Account creation bots: These bots are used to create multiple fake new accounts on websites, helping scalpers bypass purchase limits. Examples include Nike account creation bots, Supreme account creation bots, etc.
- Monitor bots: These bots continuously scan and auto refresh web pages for product launches and alert bot operators the moment items go on sale. Examples include sneaker monitor bots and ticket monitor bots.
- Price tracking bots: These bots track price fluctuations of products and notify scalpers when prices drop to a desired level. They include Amazon price tracker bots, eBay price tracker bots, etc.
- Checkout bots: These bots automate the checkout process, allowing scalpers to quickly complete purchases before others. Examples include Shopify checkout bots, Yeezy checkout bots, etc.
- Proxy bots: These types of scalper bots facilitate the use of multiple IP addresses to mask the identity of scalpers and avoid detection. Examples include residential proxy bots, datacenter proxy bots, etc.
- Captcha solver bots: These bots are used to bypass captcha tests that prevent automated activities on websites. These include reCAPTCHA solver bots and hCaptcha solver bots.
Breaking down the threat
Like the grinch stealing your gifts at Christmas, scalping bots ruin the fun by outpacing human users and making it difficult for customers to purchase popular products and tickets. At the same time, industries also suffer from the impact on the consumer experience, potential revenue loss, and the need to invest heavily in bot detection and mitigation strategies.
Let’s break down the potential impacts of these ‘grinch bots’ across availability, pricing, competition, and revenue.
The impacts of scalper bots
The use of scalper bots has significant impacts on both businesses and consumers, including:
- Artificial scarcity: By using bot technology to quickly purchase large quantities of products, scalpers create an artificial scarcity of the desired products, driving up demand and prices.
- Higher prices: With limited supply and high demand for certain products, scalpers can sell them at inflated prices, making a profit while also increasing the cost for consumers.
- Unfair competition: Scalper bots give an unfair advantage to those who use them, allowing them to bypass purchasing limits and secure items before others who are trying to purchase legitimately.
- Damage to brand reputation: When scalpers can buy large quantities of products from a brand’s website or third-party retailers, it can lead to negative reviews and damage the brand’s reputation for not being able to meet demand.
- Loss of revenue for businesses: Scalper bots can lead to a loss of revenue for businesses, as they miss out on legitimate sales and have to deal with an influx of negative feedback from consumers.
- Frustration for consumers: The use of scalper bots makes it difficult for genuine customers to purchase products at fair prices, leading to frustration and disappointment. This can also damage the relationship between the brand and its customers.
The scalper bot effect on markets
With regards to unfair competition, one of the most damaging outcomes is that scalper bots can be used to monopolize markets by a few individuals or groups who have the resources and technical knowledge to constantly purchase large quantities of products. This creates an imbalance in the market and limits fair competition for both businesses and consumers.
This disparity raises concerns about market fairness and the accessibility of products and events to the general public. It also brings into question the responsibility of companies and organizations to protect their customers from such activities.
Strategies for combating scalping bots
As with all bots, certain signs can indicate bot activity vs. real users, such as an unusually high volume of traffic from similar IP addresses, rapid and repetitive access patterns, or the simultaneous creation of numerous new accounts. Employing advanced software tools and algorithms as part of your bot mitigation solution can help detect these patterns and reduce the impact of scalper bots on a website or online platform. But there are several more advanced and nuanced ways of stopping scalper bots that could save you a lot of time and investment.
Advanced detection methods
Behavioral analysis, machine learning, and device fingerprinting are increasingly used to differentiate bots from real users. By analyzing patterns such as mouse movements, typing speed, and navigation patterns, advanced detection systems can identify inconsistencies typical of scalper bots.
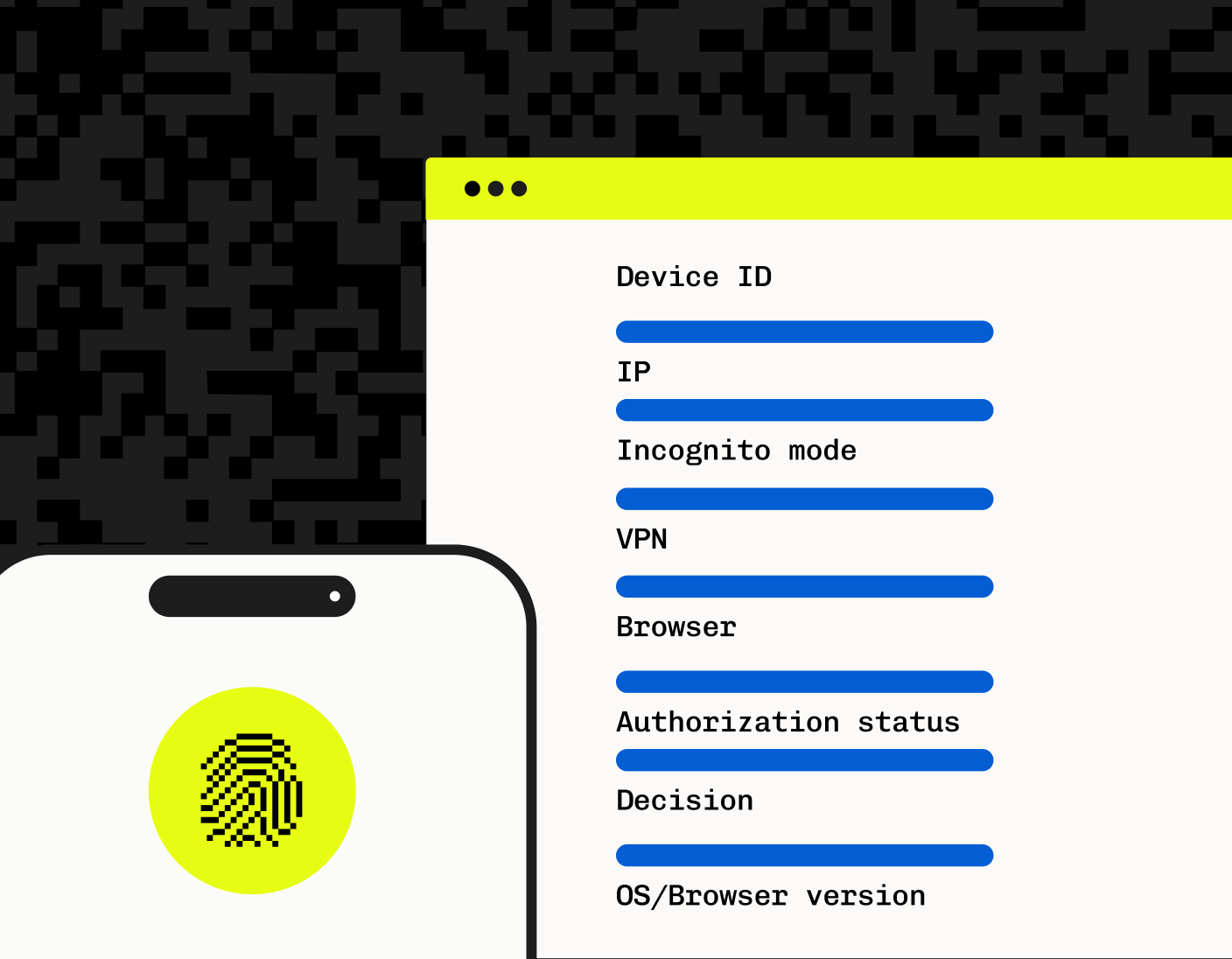
Scrutinizing device parameters and user agents provides further insight into the nature of incoming connections, helping to distinguish between genuine customers and bots. With device fingerprinting, the use of attributes like browser type, screen size, operating system, and timezone – combined into a single identifier – provides a unique ‘fingerprint’ for each device, effectively detecting and blocking bad bot traffic.
How to stop scalper bots at the door
To stop scalper bots, businesses often turn to bot mitigation via stronger authentication tools. These solutions include deploying CAPTCHAs, requiring multi-factor authentication, and implementing rate limiting on their websites. By adding these layers of security and bot protection, websites can make it more difficult for bots to execute their automated scripts successfully.
It’s important to remember that with authentication, you must hit the right balance between security and usability so as not to inconvenience legitimate users. This is where Stytch can help.
How Stytch can help
Stytch’s Device Fingerprinting (DFP) can protect against scalper bots, ticket bots, and automated attacks by aggregating various attributes of a user’s device into a unique identifier, ensuring a high degree of accuracy in distinguishing legitimate users from fraudulent actors. The use of attributes like browser type, screen size, operating system, and timezone, combined into a single identifier, provides a unique ‘fingerprint’ for each device, effectively detecting and blocking bad bot traffic.
A step beyond traditional CAPTCHA, Stytch’s Strong CAPTCHA uses complex challenges that are easy for humans but difficult for bots to solve, effectively distinguishing between legitimate users and automated systems.
Stytch also offers ‘unphishable’ multi-factor authentication (MFA) that require users to authenticate their identities using multiple factors, including something they know (like a password), something they have (like a hardware token or a registered device), and something they are (like a fingerprint or other biometric data) — making it challenging for bots and cybercriminals to gain access.
To learn more about how these or other solutions work, reach out to an auth expert to start a conversation, or get started on our platform for free today.
Prevent fraud with Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.