Back to blog
Introducing Strong CAPTCHA, Stytch’s answer to CAPTCHA fraud
Product
Oct 12, 2022
Author: Gedney Barclay

Stytch is excited to announce Strong CAPTCHA, the newest addition to our product suite. Our modern take on anti-fraud protection tackles bot fraud at its root: on the backend site architecture. In this article, we'll first cover how CAPTCHA systems work and why they are vulnerable to attack. Then, we'll dive deeper into how we designed Strong Captcha to overcome these vulnerabilities and how it can fit into your auth flow.
Telling bots from humans
Humans are the minority on the internet today. According to a recent report, over 60% of internet traffic is bots, and over 50% of that bot traffic is malicious. This malicious traffic takes many forms, including:
- Fake user account creation: for purposes ranging from buying and reselling concert tickets to influencing elections.
- Spam: deceiving emails that get users to click on malicious links or provide security information to bad actors.
- Account takeovers: in which username / passwords are used to gain access and take over someone’s account, typically for financial gain. This is often enabled by credential stuffing, in which bots attempt a high volume of username/password combinations obtained from a prior data breach.
With the wide variety of threats bot attacks pose to human internet users, it’s no wonder over the past two decades we’ve seen a rise in the use of CAPTCHA, or Completely Automated Public Turing Test to Tell Computers and Humans Apart. We’ve all had to complete these tests at some point, whether it’s selecting images that contain a traffic light, typing in a word displayed in squiggly font, or even just checking a box that asserts we are not a robot. While the challenges appear relatively simple to end users, they are a main line of defense against bot attacks.
CAPTCHA fraud
Unfortunately, CAPTCHA challenges today are engineered more for scale than security. Specifically, CAPTCHAs are vulnerable to a cottage industry called CAPTCHA fraud, in which bad actors outsource solving the test to people on behalf of bots. These companies (also called “CAPTCHA farms”) exploit CAPTCHA’s public key architecture, in which each CAPTCHA instance is identified by a sitekey publicly visible in the web page’s source code. These sitekeys make it easy to get CAPTCHA services up and running with little backend infrastructure. Crucially though, they also make it possible for the person who solves the challenge to be in a different browser from the one used to submit the solution. Like other (albeit more legitimate) SaaS businesses, CAPTCHA farms operate through APIs. Typically, the process looks something like this:
- Get public key: to solve a challenge remotely, all a CAPTCHA farm needs to solve the challenge remotely is this public site key and the URL the CAPTCHA is protecting. So the bot simply scrapes this sitekey value and sends it and the URL as parameters to the CAPTCHA farm’s API endpoint.
- Solve CAPTCHA: using the public site key and the URL, a human CAPTCHA solver receives the CAPTCHA challenge in their queue, solves it, and retrieves the response, also referred to as g-captcha-response. This response code comes in the form of a string, and communicates to the client that the CAPTCHA has been solved (regardless of who solved it or from where).
- Return response: through a separate API call, malicious bots can then retrieve the g-captcha-response code and submit it to whatever page they’re trying to gain access to. Because they have the correct response code, the site in question registers them as a human, and grants them access.
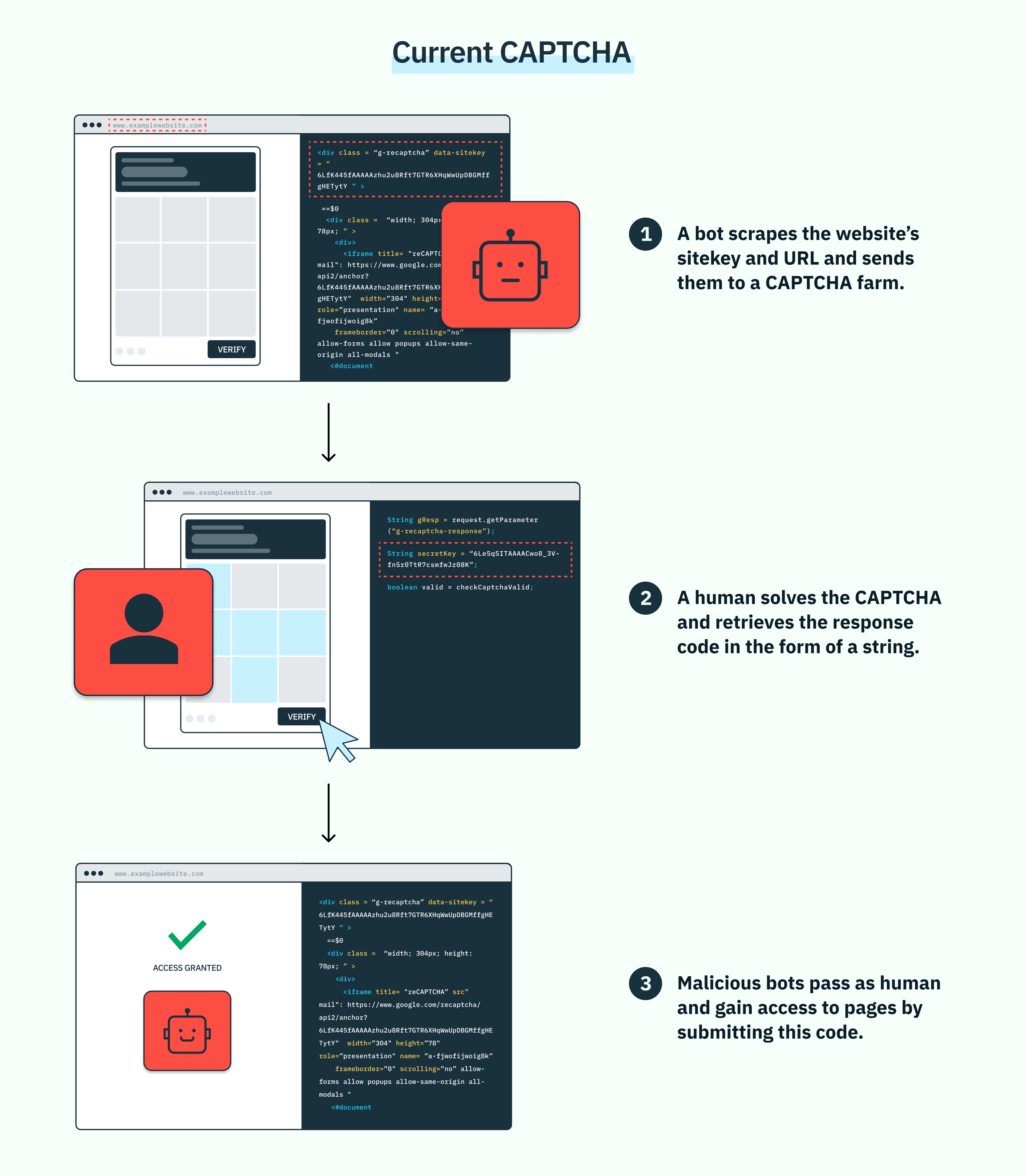
Though CAPTCHA farms employ humans, they typically boast a response time of < 60 seconds. Because of this, hackers can automate the API calls to CAPTCHA farms into their scripts, accelerating the speed and scale of their attacks. This turns CAPTCHA challenges into minor obstacles for bad actors, and opens up scalable attack vectors for bots. The result is added friction and costs on both users and business in the form of fraud, wasted resources, and time.
Protect your app with Strong CAPTCHA
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Strong CAPTCHA: secure and scalable
If CAPTCHA infrastructure is so vulnerable, why do so many people still use the public key architecture? Simply, it’s scalable. For companies who process thousands or millions of authentication attempts, public key architecture offers a fast, affordable way to get CAPTCHA up and running. Fortunately at Stytch, we believe you shouldn’t have to trade scale for security. That’s why we created Strong CAPTCHA. Strong CAPTCHA is functionally incompatible with how most image captcha solver services work today because we have removed the public site key entirely from the end user’s browser environment. With the sitekey unavailable to the end user, we’ve made it architecturally impossible for a CAPTCHA provider service to easily, and directly generate solutions for CAPTCHA-protected sites using attacker preferred, easy-to-use paid API pathways.
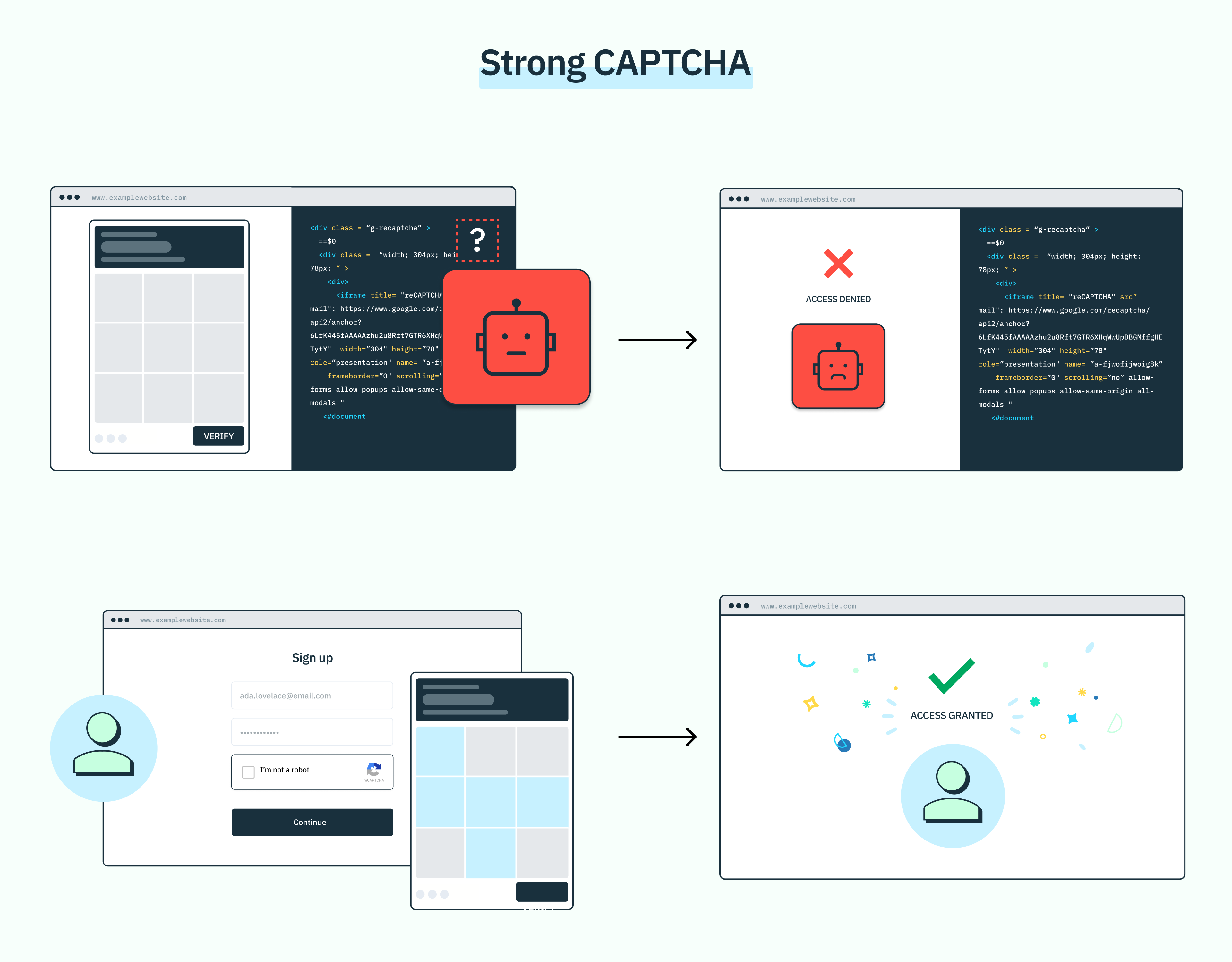
Without direct public-key access, malicious bots can no longer use these services to easily get through CAPTCHA challenges, strengthening the line of defense between a given site and bad actors. The best part? Strong CAPTCHA introduces zero additional friction to the end user’s experience: they get the same familiar CAPTCHA challenge on the frontend, with a more secure infrastructure on the backend.
Use Strong CAPTCHA with your authentication flow
At Stytch, we are laser-focused on helping our customers authenticate their users and verify their identity with minimal friction. By distinguishing bots from humans, Strong CAPTCHA adds another vital solution to our arsenal, and only makes the Stytch suite a more comprehensive auth solution for our customers. While some of our customers may already have a CAPTCHA solution they’re looking to upgrade, we also recognize some companies may still be in the process of understanding where it fits into their authentication flow. You can always chat with an auth expert for more personalized guidance, but there are a couple key junctures where we generally find CAPTCHA to be helpful:
- Account creation: account creation is a prime target for bots because of the volume of traffic and lack of authentication. Because of this, it’s an ideal juncture for using Strong CAPTCHA.
- Just-in-time: many companies use CAPTCHA when they start to notice suspicious behavior, like when a high volume of login attempts come from the same IP address, or if a user’s login behavior is too fast (an indication bots are at work). They might also introduce CAPTCHA if the user is trying to do something involving sensitive or high value information, like change their payment information or account email.
While you can technically introduce CAPTCHA at any point in your login flow, we believe our customers will be most successful if they only use it where it’s most needed. Authentication is a critical growth lever, and you don’t want to create any more hoops for users to jump through than you have to. At the same time, CAPTCHA is just one piece of the authentication puzzle, and it’s important to think about how it fits into your complete customer journey and authentication experience. While we offer more detailed guidance on breach prevention on our blog, it’s safe to say we strongly advise our customers not to rely exclusively on any one given gateway, especially if that gateway is passwords. (For more information on some options to consider, check out our blog on step-up and multi-factor authentication flows). As an example, your Strong CAPTCHA-enhanced authentication flow for account creation might look something like this:
- Provide email.
- Solve Strong CAPTCHA to trigger verification email.
- Verify email with a magic link.
- Account creation success!
Or, you might use it in your login flow like this:
- Provide username and password.
- Strong CAPTCHA is prompted if the user is using an unusual IP or unrecognized device.
- Solve Strong CAPTCHA.
- Login success!
These examples are just the tip of the iceberg for how to configure your authentication flow with Strong CAPTCHA. You can learn more about this solution or other products at stytch.com, or book time with one of our auth experts to see Strong CAPTCHA in action. Whatever your questions or needs, we’d love to help you on your auth journey.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.