Back to blog
Stytch Fraud & Risk Prevention: Intelligent Rate Limiting, real-time monitoring, and more
Product
Feb 19, 2025
Author: Stytch Team
Author: Griffin Solot-Kehl
To kick off Launch Week, we’re excited to announce several major enhancements to Stytch’s Fraud and Risk Prevention solution, providing even stronger security for your app and users while making the platform easier to use. These new features improve on what is already the most accurate and sophisticated fraud and risk prevention platform available.
New features include:
- Intelligent Rate Limiting: Adaptively protect against automated threats using dynamically weighted traffic signals.
- Enhanced data visualization: Gain deeper insights and monitor real-time fraud patterns.
- Event log filtering: Analyze traffic trends in your dashboard.
- Streamlined rule creation: Create an authorization rule from an existing fingerprint directly from the dashboard.
- Backend SDK support: Integrate across more languages.
- External metadata support: Link fingerprints to your identifiers for better risk assessment.
The Most Reliable Way to Stop Attacks and Detect AI Abuse
With AI driving a surge in bot-driven fraud and abuse—from account takeover to phishing and compute abuse—Stytch’s Fraud and Risk Prevention gives you a powerful, proactive defense. That’s why teams from Replit to Calendly already trust Stytch to keep their applications secure.
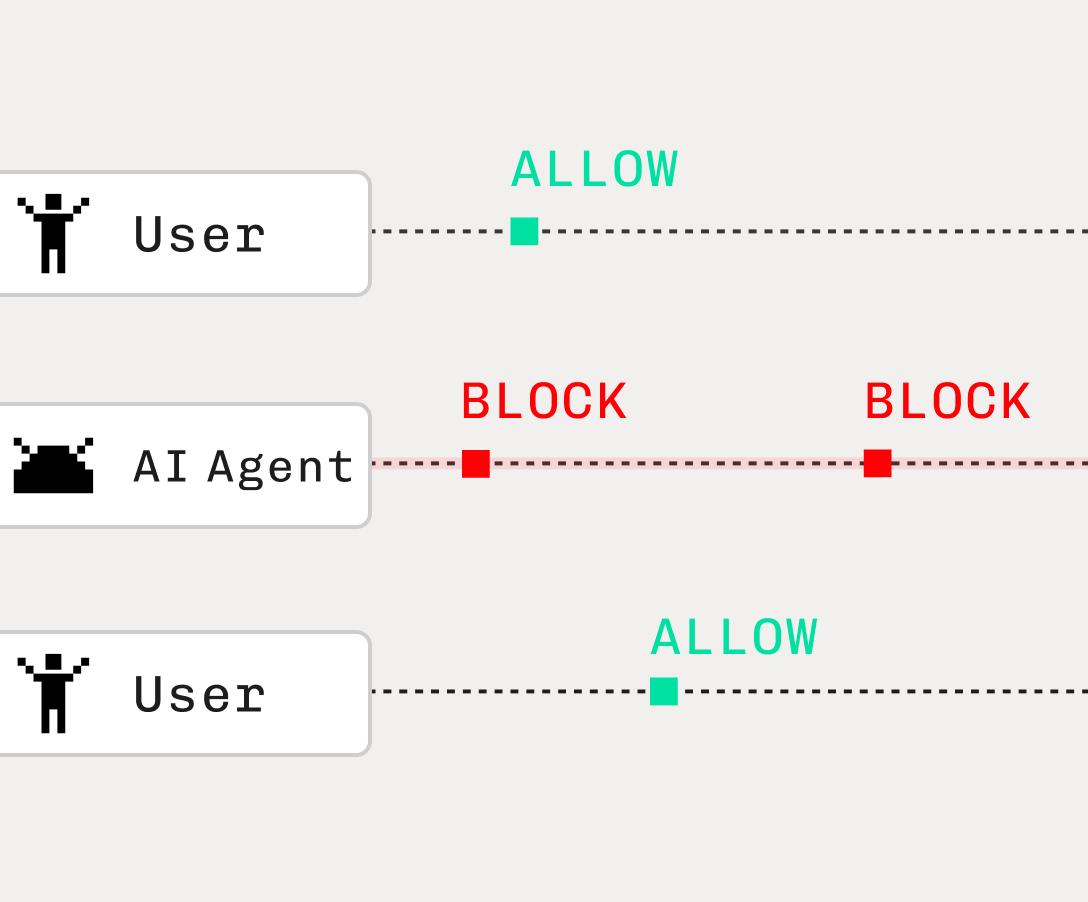
Our solution combines deterministic identifiers with supervised machine learning for a highly accurate and immutable fingerprint that identifies every visitor to your application, while preserving user privacy and resisting reverse engineering. With new features like Intelligent Rate Limiting, our platform can evaluate the security risk in real time and return an authorization verdict that recommends you ALLOW, BLOCK, or CHALLENGE any visitor device, ensuring bad actors are kept out while real users face zero friction.
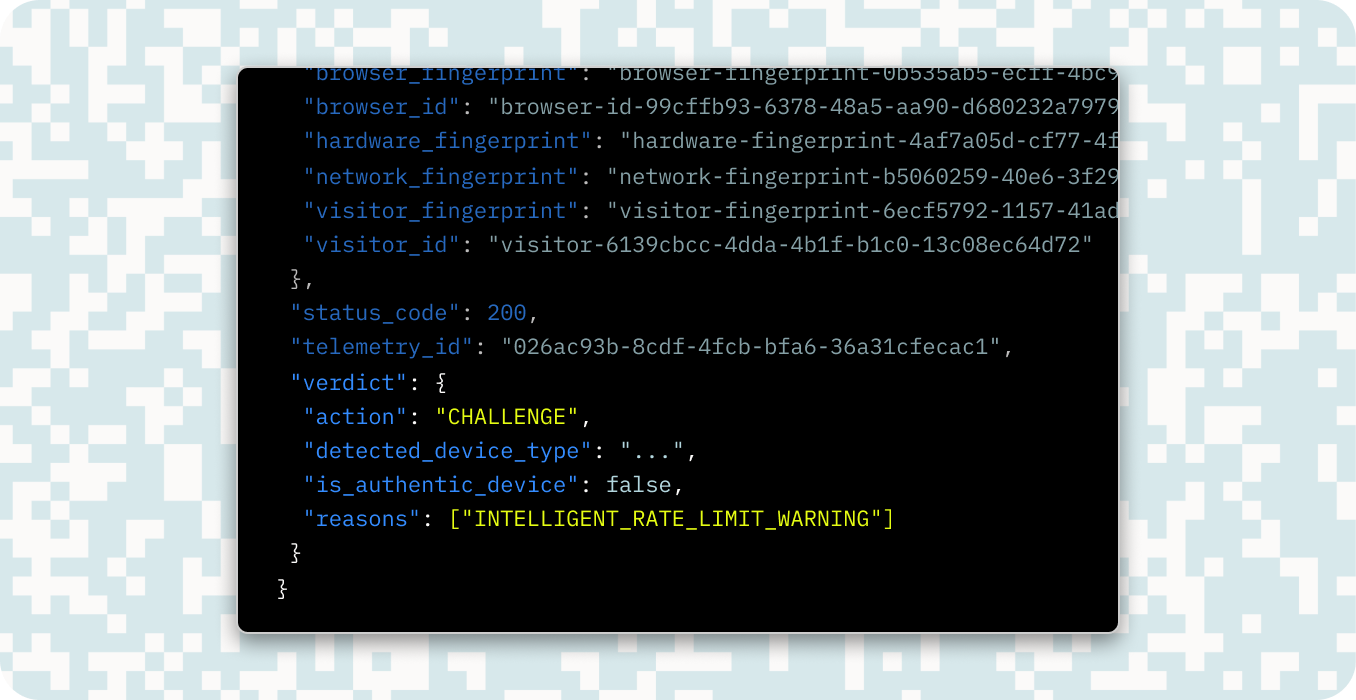
Stytch’s advanced fingerprinting technology has proven uniquely effective at detecting AI agent use from emerging tools like OpenAI's Operator and Anthropic's Computer Computer Use API. As AI agents gain more access and permissions to perform actions on digital platforms, they pose new security risks and challenges. Stytch helps your application stay ahead of the fraud curve by identifying any bot-driven or AI-driven traffic with precision.
Fraud and Risk Dashboard Upgrades
The first changes you’ll notice are the ones we've made to improve your dashboard experience. These upgrades were designed to help make the dashboard easier to navigate and use for workflows such as pulse checks on traffic shaping and investigations into false positives/negatives. A large part of fraud prevention is analysis of past data, so we wanted to make that experience even more powerful.
Enhanced Data Visualization
The first key dashboard improvement is added data visualization for dashboard activity. Most notably, a new live chart view gives you a quick understanding of traffic health.
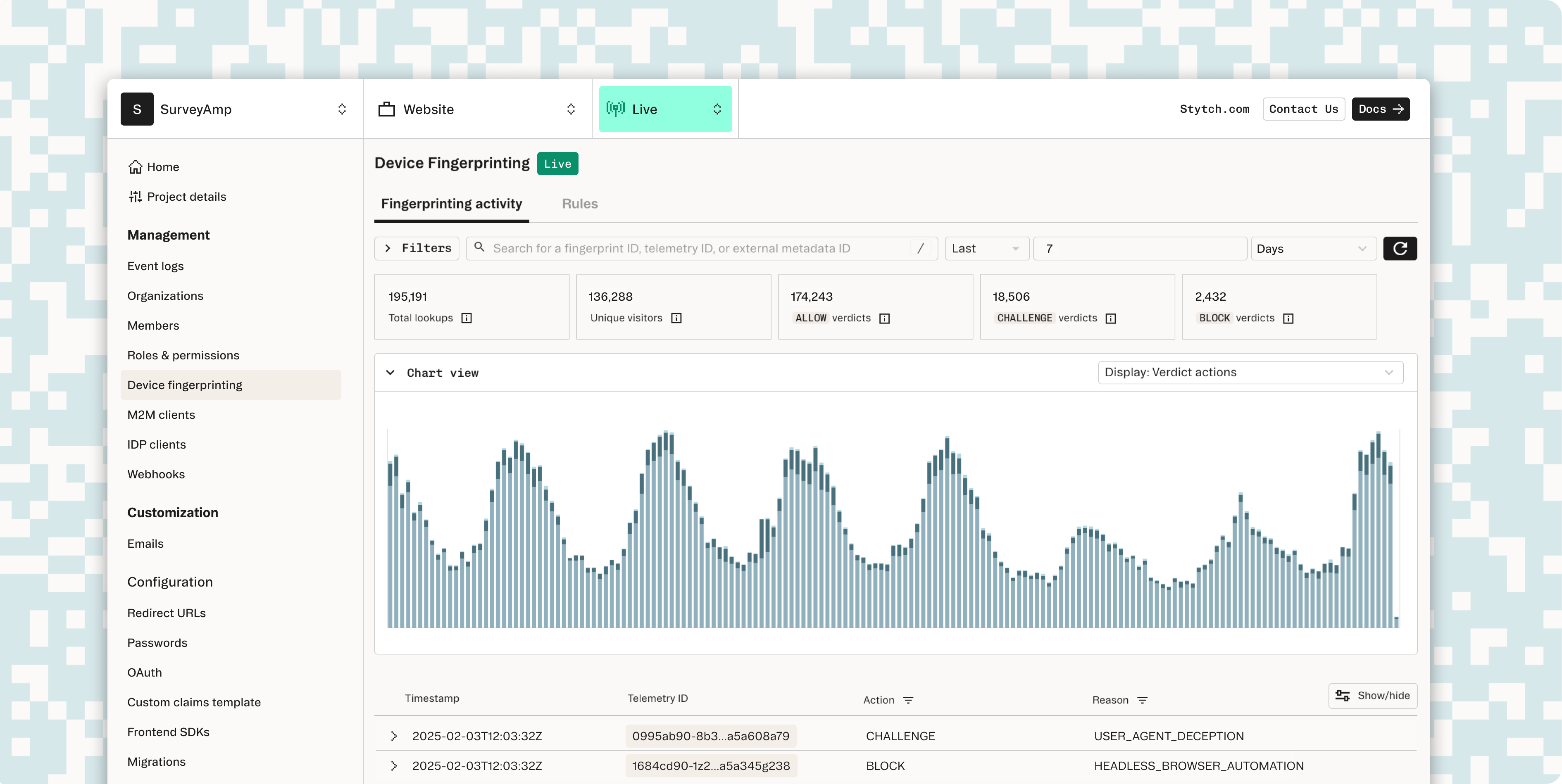
Filters can be applied based on a range of parameters to get insight into traffic trends. The dashboard can display verdict actions, reasons, and detected device types for filtered sets of traffic. This will help you find trends on attack vectors based on characteristics such as common browser fingerprints, network fingerprints, and hardware fingerprints.
Being able to see common attributes of traffic can inform you about events like bot attacks that can be easily correlated with potential abuse and other useful insights for account safety. These new features make it easier to get a quick snapshot of your traffic shaping and drill down quickly into specific fingerprints to identify and prevent abuse.
Event Log Filtering
We have upgraded our device fingerprinting logs to be easier to navigate and filter by time frame or other parameters. This makes it so you no longer have to know the specific telemetry ID to view a particular verdict.
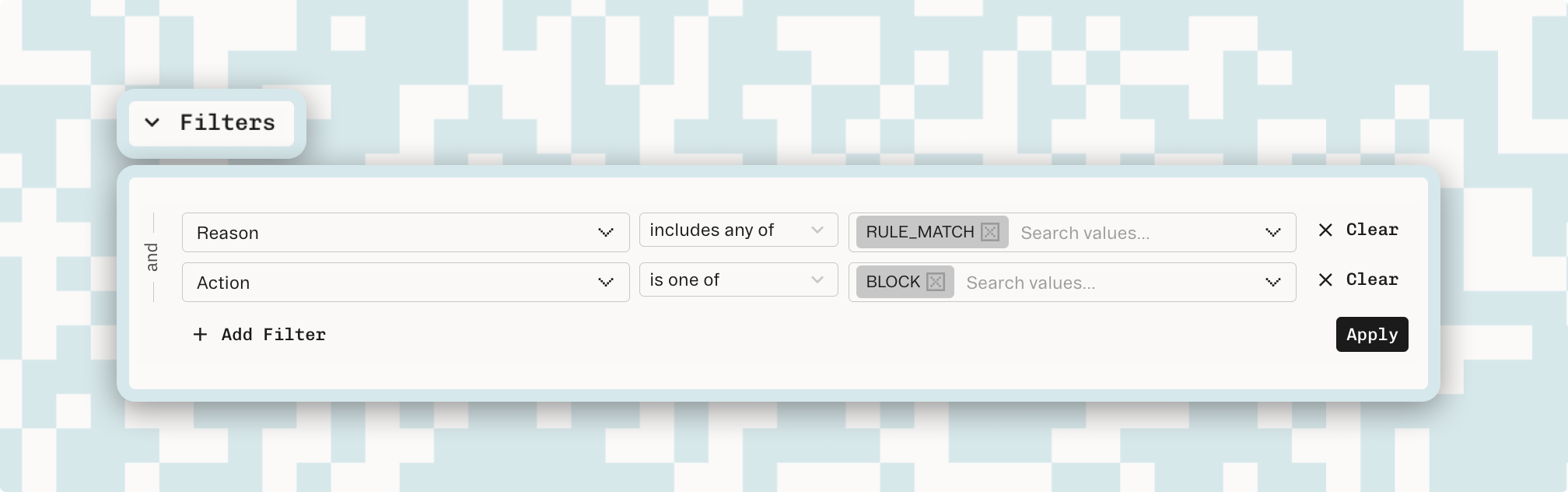
This is also improved by the inclusion of additional filterable parameters: “ExternalID”, “OrganizationID”, and “UserAction”, that can be synced from your own logging systems,letting you better associate external identifiers to the existing Device Fingerprinting logs.
All of these improvements are designed to improve your ability to investigate and associate your logs between different sources, giving you the tools to handle data and own your entire flow.
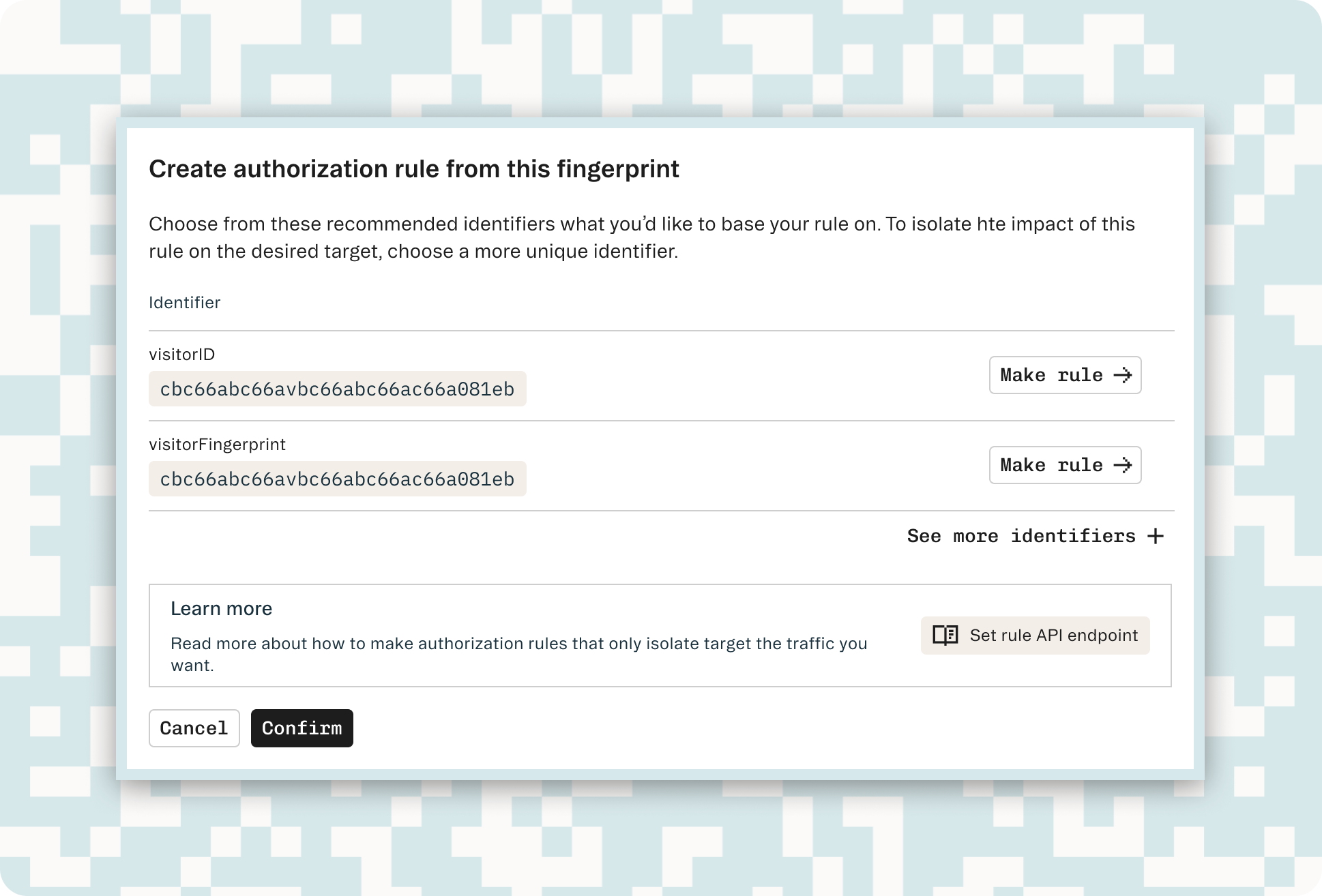
Streamlined Rule Creation
We’ve also made creating custom rules easier and more intuitive. You can now use an existing fingerprint to easily create an authorization rule. You can initiate the rule creation process directly from the dashboard, selecting an action and expiration for the targeted parameter without losing context.
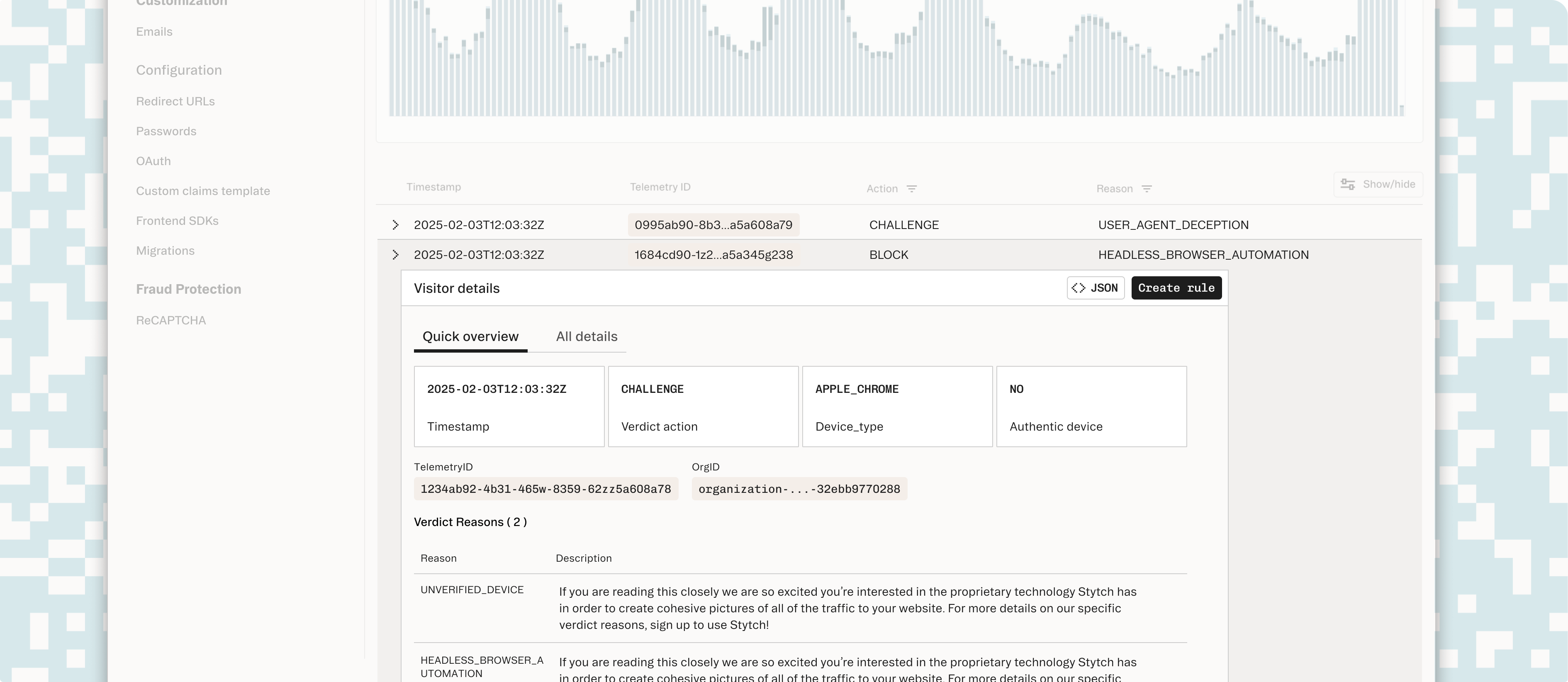
The rules will then apply for all future fingerprints within the selected duration, clearly visible in the response payload. This addition makes it easier and faster to fix any false positives or negatives that may occur with a quick rule override.
Dynamically Weighted Intelligent Rate Limiting
Intelligent Rate Limiting (IntRL) has been improved under the hood to provide better accuracy on detecting low-volume traffic. As a quick overview, Intelligent Rate Limiting is a feature that automatically rate limits attacks on applications by leveraging a dynamic set of device and traffic sub-signals that more accurately predicts fraudulent traffic than traditional rate limiting strategies like IP addresses.
By refining our internal parameters used to determine when and who to rate limit, we've improved precision in detecting low-profile fraudulent activity, not just high-velocity attacks. This helps defend against more sophisticated attacks that are more targeted, which is common for bad actors who are attempting to take over specific accounts or deploy a small number of advanced bots.
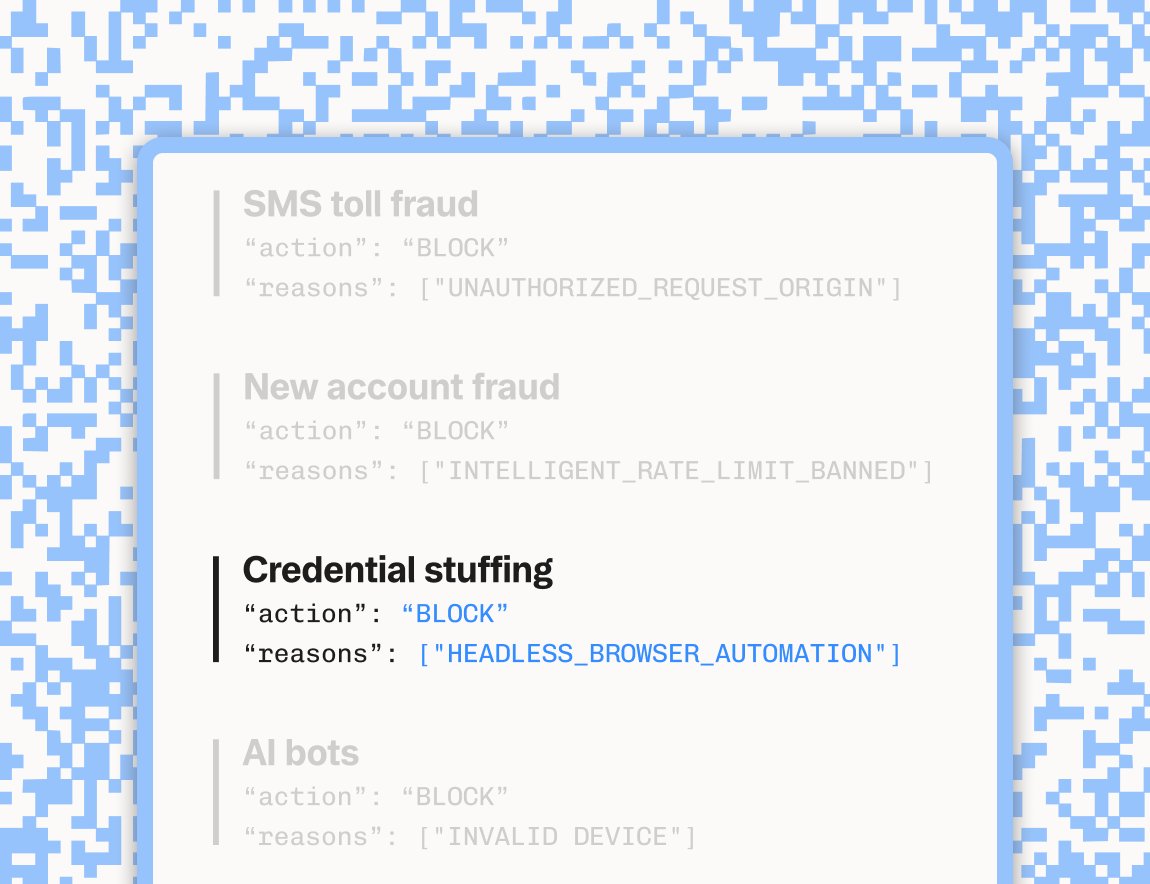
This feature also excels at detecting and limiting automated browser activity by leveraging the full breadth of our device fingerprinting capabilities combined with our Intelligent Rate Limiting system. Our solution identifies common tools like Puppeteer, Selenium, Anthropic’s Computer Use API, and OpenAI’s Operator, even as they rotate through new IPs or known proxy providers.
Intelligent Rate Limiting applies an extra layer of defense, preventing abuse before it reaches critical volumes. Crucially, our approach doesn’t rely on blanket IP bans; instead, we can block on more granular attributes, like the browser version, preserving legitimate traffic while thwarting high-volume scraping and account generation attempts.
Other Notable Improvements
- CNAME Support for Telemetry.js has been added, making it harder to detect Stytch is being used and block scripts.
- IPGEO decisioning is in closed beta, which allows you to set rules to make BLOCK/ALLOW decisions based on IP addresses, ASNs, and country codes.
- Proxy and VPN Information are now included in fingerprint lookups as is_proxy and is_vpn in the API response.
Getting Started
Our Fraud and Risk Prevention improvements and endpoints are now available in all of our backend SDKs, including Node, Go, Python, Ruby, Kotlin, Java and Rust, and can be used with both the B2C and B2B clients. Visit our docs for more details.
We are hard at work to ensure that Stytch Fraud and Risk Prevention is the most robust and accurate tool in the world to keep your product and users secure. Ensuring the best user experience and ease of access to data remains a priority, and we invite you to try it out for yourself.
Tell us how you want to use Stytch Fraud and Risk Prevention, and our team will help you start building!
Stay tuned tomorrow for the next product in Launch Week. And follow us on X for daily product announcements.
Fraud & Risk Prevention
Beyond WAF and CAPTCHA: 99.99% bot detection, intelligent rate limiting, and reverse engineering protection.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.