Back to blog
Stytch supports Web Bot Auth for agent and bot verification
Latest
Auth & identity
Product
Sep 23, 2025
Author: Bobbie Chen

We are excited to announce our support for Web Bot Auth, the emerging standard for bots and AI agents to identify themselves. We’re partnering with Browserbase, Anchor Browser, Cloudflare, Akamai, as well as the wider Web Bot Auth community, to bring a more trustworthy web.
What we'll cover:
- What is Web Bot Auth and why should anyone use it?
- The importance of open standards
- Get started today with Stytch
Here's the quick summary:
- User-Agent is broken because it is spoofable - and other alternatives have their flaws as well.
- Web Bot Auth is an emerging open standard that gives good bots a way to cryptographically identify themselves, so sites can deliver better Agent Experience (AX).
- Stytch now supports Web Bot Auth, featuring:
- a lightweight JavaScript-based integration via IsAgent or Device Fingerprinting, and
- no agent registration required with us.
We’re launching alongside Browserbase, Anchor Browser, Cloudflare, and Akamai to help build a better web for humans and agents.
What is Web Bot Auth and why should anyone use it?
The problem with User-Agent
You can think of Web Bot Auth as a better version of the User-Agent header.
The User-Agent header allows browsers and other web clients to declare their own identity. But it’s easily spoofed, and that makes it really difficult to use. In the words of Aaron Andersen’s 2008 blog post:
…the user agent string was a complete mess, and near useless, and everyone pretended to be everyone else, and confusion abounded.
This is a bad situation for good bots. Most website operators welcome search engine crawlers like Googlebot, which is a well-behaved and robots.txt-respecting service. But bad bots constantly impersonate Googlebot since User-Agent is just a string; that means that the recommended approach to identify Googlebot is to do a reverse DNS lookup or keep track of thousands of IP addresses.
And that’s just for one service! Then you can go after Bingbot, Common Crawl, Applebot, Meta’s bots, …and those are just the traditional ones. We are now in a Cambrian explosion of agentic traffic, and it’s not easy to keep up with the new companies spinning up AI agents, fetchers, and other new bots.
User-Agent doesn’t work for bots to identify themselves, and that’s unfortunate.
The value of self-identification
When well-behaved bots identify themselves accurately, it opens the door to better experiences. We launched IsAgent, the AI agent detection SDK, specifically because website operators didn’t know exactly what kind of traffic they had.
Every day, we benefit from self-identification on the web. When I open a website on my phone, it serves me a mobile-friendly version. When I visit a multi-national company’s website, it serves me content in my preferred language. But when I use an AI agent, I currently get a site optimized for humans.
AI agents prefer formats like LLMs.txt or MCP servers. You probably don’t want an AI agent to impersonate you by logging in with all those dangerous permissions; agents should get scoped permissions through consent flows. Web Bot Auth gives AI agents (and other bots) the ability to identify themselves, securely.
When Browserbase announced our support for Web Bot Auth, we saw hundreds of companies reach out within weeks. This tells us something important: the bottleneck to scaling agentic AI is trust at the identity layer. Stytch and Browserbase already have a strong partnership and we’re excited to work with Stytch to bring Web Bot Auth to the web.
– Peyton Casper, Product - Identity & Trust at Browserbase
How does Web Bot Auth enable self-identification?
Web Bot Auth is a standards-based approach for automated agents to sign HTTP requests so servers can verify identity and apply clear policy.
It’s a lot like User-Agent, but cryptographically signed with a specific private key using HTTP Message Signatures (RFC 9421). That private key is controlled by the bot operator, so that means that no one else can impersonate a particular bot (without breaking modern cryptography, which would be very bad for other reasons).
That’s great! Now good bots can identify themselves in an unspoofable way, and website operators can detect them and offer better experiences.
Anchor Browser is proud to partner with Stytch as a native supporter of the Web Bot Auth specification. By lowering the barrier to adoption, Stytch is helping democratize agent verification and making WBA easier than ever for developers to implement.
– Idan Raman, CEO and Co-founder at Anchor Browser
The importance of open standards
Fostering an open ecosystem
When Cloudflare first announced their support for Web Bot Auth, they were met with controversy over the risks of centralized gatekeeping. I think these worries are misplaced.
There is widespread interest and input from the industry on bot authentication. I’m involved in the IETF Working Group for Web Bot Auth, and each discussion involves participation from internet giants, smaller companies, and concerned individuals. For example, Akamai is involved with Web Bot Auth:
Akamai is deeply invested in making the internet safe for business and ready for what’s next. Supporting Web Bot Auth as an open standard reflects our ongoing work on content, browser, and interoperability standards to deliver, optimize, and secure the web.
– Eric Graham, VP of Product, Application Security, Akamai
At its core, Web Bot Auth is an emerging open standard, and that’s valuable for all of us. Just as Stytch supports OAuth and invests in its ongoing development (like supporting OAuth for MCP Connected Apps for AI and MCP integrations), we support Web Bot Auth and the young ecosystem that is developing around it.
Why we believe in Web Bot Auth
Web Bot Auth is an open standard without proprietary lock-in. Anyone can implement the spec to send Web Bot Auth headers, and anyone can implement the spec to verify the resulting signatures.
I think the spec is a great starting point. It uses standard web technologies, building on top of HTTP Message Signatures and Structured Fields. It’s easy to roll out incrementally; no big-bang migrations required. And there is plenty of room for extension through richer claims like capabilities or other attestations.
As an emerging standard, there aren’t many implementations of Web Bot Auth yet. It is much easier to build a healthy ecosystem by agreeing to communicate in a structured way - that is the core requirement of interoperability, and we need it to reap the benefits.
Today, Stytch is adding a new implementation of Web Bot Auth verification through IsAgent and Device Fingerprinting. We’ve also published a guide to signing for AI agent and bot developers: How to implement Web Bot Auth for your AI agent, bot, or crawler (and why you should). We hope to help build a healthy ecosystem for responsible bots and AI agents.
When it comes to open Internet protocols, real-world implementations are invaluable in helping us learn how they work at scale, and where they need to be improved. That’s why at Cloudflare, we’re supportive of Stytch’s implementation of the Web Bot Auth proposals, and their participation in the standardization process at the IETF!
– Thibault Meunier, Research Engineer at Cloudflare
How Stytch supports Web Bot Auth
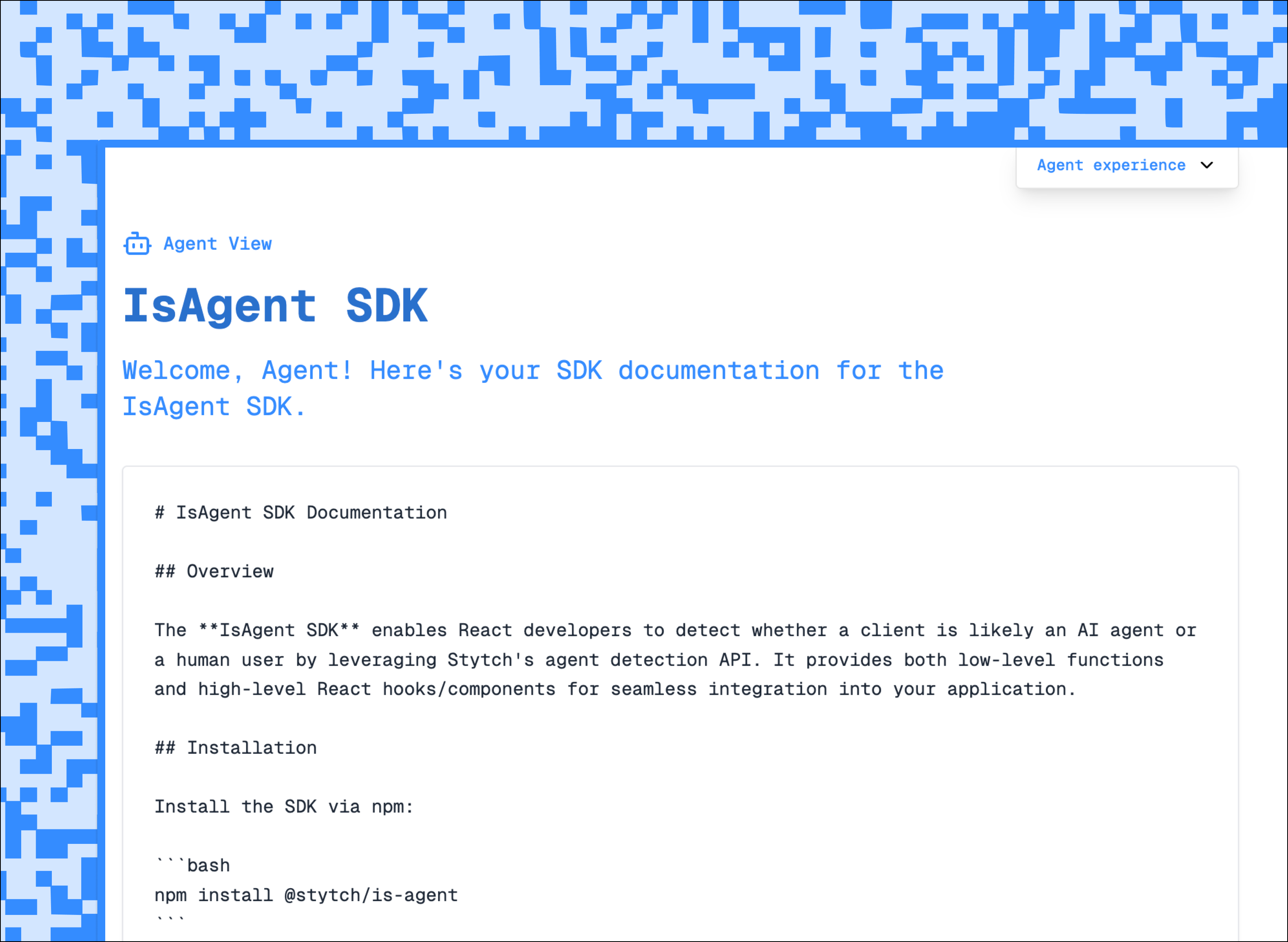
Today, you can verify agents using Web Bot Auth using our agent identification SDK, IsAgent, or our fraud prevention solution, Device Fingerprinting.
With a lightweight Javascript integration, you’ll get verifiable identity based on the latest proposal for Web Bot Auth. This is what it looks like when an agent supporting Web Bot Auth, like ChatGPT Agent, is detected:
As a bot or agent operator, you don’t need to register with Stytch. We support the Signature-Agent header, which enables decentralized discoverability of agents; as long as you send an appropriate URL with your public key directory, we can verify your identity (see the implementation guide for details).
As a website operator, you can nudge bots and agents towards agent-friendly interfaces like LLMs.txt, or simply log the result so that you can plan for future development.
Get started today
If you're a website operator and want to detect good bots:
- Sign up for IsAgent (free and lightweight) or Stytch Device Fingerprinting (hardened for enterprise usage).
- If you're already using IsAgent or Device Fingerprinting, no action is needed - you'll see information about Web Bot Auth verification in your API responses already.
If you're an agent or bot operator interested in implementing Web Bot Auth signing:
- Check out our implementation guide: How to implement Web Bot Auth for your AI agent, bot, or crawler (and why you should)
And for everyone:
- Learn more about our launch partners for Web Bot Auth:
- Consider reading the proposals for Web Bot Auth and joining the IETF Working Group to contribute to an open, standards-based web.
Related Articles
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.