Back to blog
The age of agent experience
Auth & identity
Feb 8, 2025
Author: Julianna Lamb

Designing for the agent experience
AI agents—from ChatGPT Operator to coding tools like Devin and Lovable, are transforming how we interact with apps. Agents are capable of navigating interfaces, making requests, and executing tasks on behalf of users, and they’re taking over navigating the web for humans. It’s time to start building for a new persona: the autonomous agent. Instead of just designing experiences for human users, we need to think carefully about how machines will access data and perform actions securely, with transparency and user consent.
At a high level:
- Agents need the ability to “log in” or otherwise prove they have permission to act on a user’s behalf.
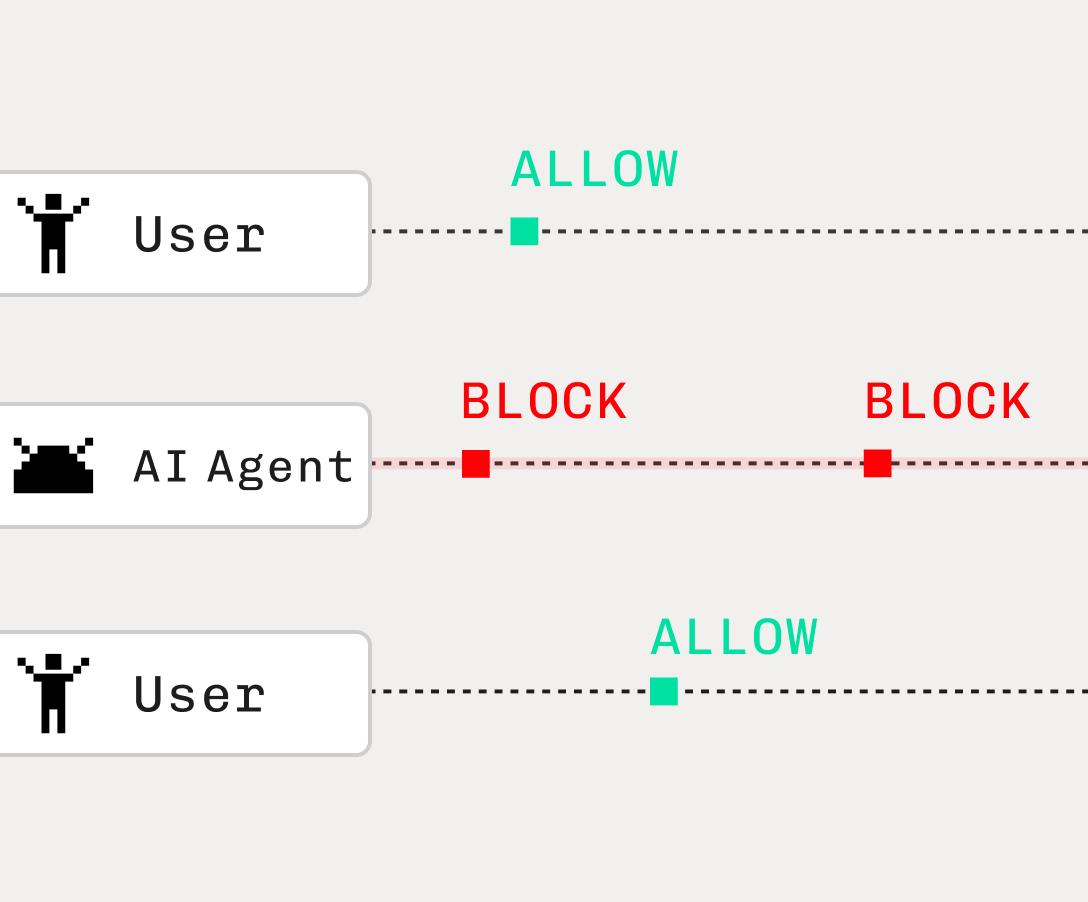
- Users need confidence that these agents are only doing what they explicitly allow (and have a way to revoke access if something changes).
- Service providers need robust ways to authenticate and authorize agents, confirm user consent, and manage risk.
The good news is that we already have a robust standard for delegating secure, scoped, and revocable access: OAuth. Rather than giving your password to every new application or agent, OAuth is designed to give the right party the right permissions in a safe, standardized way.
AX: The next frontier after UX and DX
In a recent post, Introducing AX: Why Agent Experience Matters, Netlify Co-Founder and CEO Mathias Biilmann argues that agent experience (AX) will be as big a deal as user experience (UX) and developer experience (DX) once were. Historically:
- UX (coined by Don Norman in 1993) transformed how we think about the human interface—covering everything from visuals to workflows to how a product “feels” for real people.
- DX (popularized in 2011) recognized that developers were an equally important audience. Platforms that offered better docs, better APIs, and less friction saw massive growth and adoption.
Now, we have agents—powered by large language models, multi-modal inputs, and the ability to handle tasks in an “autonomous” way. According to Biilmann, “we need to start focusing on AX or ‘agent experience’—the holistic experience AI agents will have as the user of a product or platform.”
Agents as a driving force
Investing in agent experience will be table stakes as more and more companies launch agents and users shift to using other products via those agents instead of directly interfacing with the UI.
- Agents are more than generative—they have “agency,” meaning they can initiate actions and transactions rather than simply responding to user queries.
- Tools or platforms poorly suited for LLMs will quickly fall behind, because humans will lean on the AI that best orchestrates their tasks.
- Open Ecosystems will likely outperform closed “vertical” integrations in the long run. If you welcome any agent a user prefers—complete with easy onboarding, open APIs, and secure authentication flows—your product becomes more powerful and “agent-friendly.”
As we’ll discuss later, making your system accessible via OAuth is one of the biggest steps you can take to ensure a high-quality agent experience.
Building a great agent experience
Many of the principles that have been foundational to UX and DX will apply to AX as well, but some things won’t carry over. We have UIs because humans are incredible at deriving meaning from icons and visuals; humans communicated with pictures long before we invented written language.
In contrast, AI’s native language is numerical embeddings – both text and images need to be translated, but images don’t have the same “natural” tokenization that text does, and can be far more computationally expensive. Therefore, we should orient AX around methods of communication that computers are best at and optimized for their consumption – browsers are slow, client code takes time to render. Key principles for great AX include:
- Clean, Well-Defined API: An API originally designed with good DX in mind is a solid starting point for agents. Many apps that have never needed APIs before will need to invest in building them or investing in more comprehensive APIs to ensure agents have access to complete functionality. Focus on clear documentation, well-structured data, and stable endpoints to give agents a reliable way to interact with your product.
- Easy User Onboarding: Ideally, both the human user and the agent can get started with minimal friction. Providing a streamlined flow—like a single command or a concise OAuth handshake—ensures that agents can operate quickly while users stay in control.
- Frictionless Agent Operations: Once granted the right permissions, agents should be able to do their work without cumbersome manual steps. Whether it’s spinning up a new instance, managing resources, or analyzing data, the experience should be as automated and efficient as possible—maximizing both agent productivity.
- Step-Up Authentication: There will be some scenarios where an agent shouldn’t be able to continue without a human in the loop approval. For example, when moving large amounts of money, executing on a write action that impacts your production code, or similar, there should be an approval workflow that requires the human user’s input.
When you take these steps—offering secure APIs, simplifying onboarding, and removing bottlenecks in the agent workflow—you ensure a better experience not only for AI-driven agents but also for your human users. In many cases, the same design choices that improve AX end up improving user satisfaction and adoption overall.
Why OAuth is perfect for agent auth
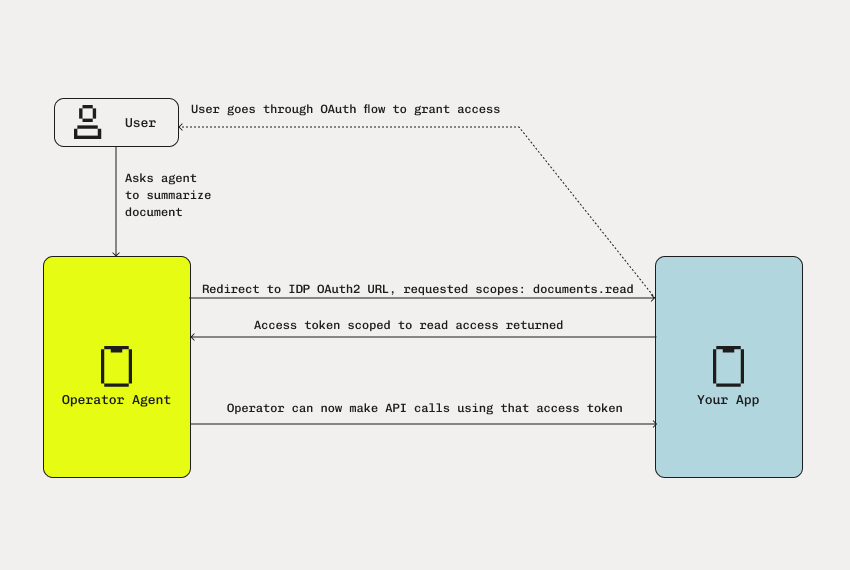
For years, OAuth has let you “Log In with [provider]” and then give an application or service permission to access your data. This typically involves short-lived access tokens, refresh tokens, and specific scopes that define exactly what the third party can do.
When an AI agent is your third party, the underlying security needs aren’t all that different:
- Secure User Consent: Don’t give your agent your username and password. OAuth provides a secure flow ensuring the user explicitly approves which data or actions the agent can access.
- Token-Based Authorization: The agent receives tokens that can be scoped and revoked. This protects your core credentials and allows granular permissioning.
- Long-Term Agent Use with Revocation: Agents might need ongoing access to your account. With OAuth, you can revoke their access at any time without resetting your main password.
- Step-Up Authentication for Extra Security: For sensitive actions, agents will need to require a human in the loop approval to proceed.
There’s no need to reinvent the wheel here, OAuth is a battle tested standard that brings a familiar experience to this new world of agents. But this does mean that all applications will need to become OAuth providers in order to allow for easy and secure access for agents.
Leveraging existing OAuth flows for agents

When you think “OAuth,” you might picture a user in a browser clicking a “Consent” button. In some cases, this will be practical for agent auth as well. But for some agent scenarios—where the AI may not have a graphical interface—there are specialized flows that handle these interactions elegantly:
- Device Authorization Grant (Device Flow): Often used when the application is running on a separate device from the user’s smartphone or laptop, like a TV. The agent notifies the user and shares a link to visit, the user follows the link to consent on their main device, and the agent obtains an OAuth token.
- CIBA (Client-Initiated Backchannel Authentication): This OpenID Connect flow is handy for high-risk actions (e.g., making large stock trades) because it ensures the user must explicitly confirm. The service (e.g., a brokerage) can notify the user directly, rather than relying on the agent to ask permission.
Choosing which flow to use depends on how you want to handle user notifications, scope approvals, and risk. But the bottom line is the same: OAuth has already solved the core delegation problem for third-party actors—human or agent.
Everyone needs to be an OAuth provider
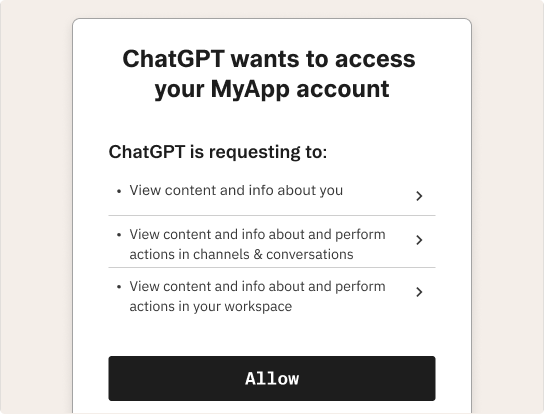
If your product doesn’t work seamlessly with other agents that your users might be leveraging, eventually, you risk losing out to competitor platforms that welcome every agent and provide a smooth AX.
Being an OAuth provider is part of building that open ecosystem. With OAuth, your app can:
- Offer standardized flows for token-based authentication.
- Empower users to pick whichever AI agent they trust.
- Define scopes for read-only vs. read-write, normal actions vs. high-stakes actions.
- Provide revocation or additional user checks for truly sensitive operations.
In short, everyone needs to become an OAuth provider if they want to attract or even allow AI agents to operate in their ecosystem and maintain a competitive advantage.
Don’t reinvent OAuth
There are a lot of ideas out there about what the future of agents might look like. Many agent demos are basically letting an AI browse your site like a slow, not-so-smart human—and ignoring that OAuth flows already exist for secure, user-centric delegation. Here are a few takeaways on why we shouldn’t be trying to reinvent the wheel with agent auth:
- On agent authentication: Don’t give the agent a username and password, it’s annoying for users and a security risk.
- On frictionless interactions: If your product is friendly to bots (i.e., it has an API and an OAuth flow), you don’t need complex RPA to simulate a human user.
- On tightly scoped access: Agents won’t necessarily need access to everything a human user can do, and in many cases, it might be a non-starter to give them that kind of unscoped permission. That’s the whole point of scopes.
- On user consent: For big actions, require device flow or something that ensures the human is in the loop. Making human-in-the-loop approval a core product flow will make it easier for users to trust agents with your application.
Ultimately, adopting these OAuth-driven best practices is how you deliver a top-notch agent experience and avoid reinventing the wheel every time a new AI tool emerges.
Architecting for agent experience
Moving from an app built “just for humans” to an agent-friendly design doesn’t need to be a huge overhaul. Consider these recommendations:
- Expose Clear, Machine-Friendly APIs: As Biilmann notes, “Platforms or frameworks that are hard for LLMs and agents to use will start feeling less powerful.” Provide stable endpoints, well-structured data, and documentation that an agent can parse.
- Scope Your Permissions Thoughtfully: Don’t rely on a single monolithic permission that grants total control. Break it down: “read account data,” “post new content,” “initiate high-value transactions.”
- Plan for Token Storage and Rotation: Agents may store tokens long-term. Make sure these are limited in scope, easily refreshed, and promptly revocable.
- Have a Strategy for High-Risk Actions: For big or irreversible actions, consider a second layer of user confirmation. This can be a device flow or a backchannel (CIBA).
- Aim for an Open AX Ecosystem: Follow the principle that your users might bring any agent. Offer a standard OAuth interface that any agent can plug into, without a ton of custom code or guesswork.
The future of agent auth
Designing your systems to be agent-friendly might sound futuristic, but as Mathias Biilmann’s post outlines, AX is already here, just like UX and DX once were. Platforms that invite AI agents, empower them with secure APIs, and let users choose (and limit) agent permissions will likely outcompete those stuck in closed or manual approaches.
At Stytch, we’re excited about this agent-driven future and are committed to making it simple for everyone to implement secure agent access. By leveraging OAuth flows, we can make it simple for you to power best-in-class authentication and authorization experiences that scale from human users to the agents they trust.
That's why we built Connected Apps—a powerful feature that makes it easy for your application to be integrated with AI agents, third-party apps, and multi-app ecosystems. With Connected Apps, your application can become an OAuth 2.0 identity provider, delegating access and permissions to build seamless integrations with other first-party and third-party applications.
Check out our step-by-step guide in the developer docs.
Become an OAuth provider
AI agent workflows, cross-app logins, secure data-sharing workflows and more—Connected Apps makes it all possible without the engineering lift.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.