Back to blog
Top SCIM Tools to Streamline B2B Identity Management in 2025
Auth & identity
Jul 16, 2025
Author: Stytch Team
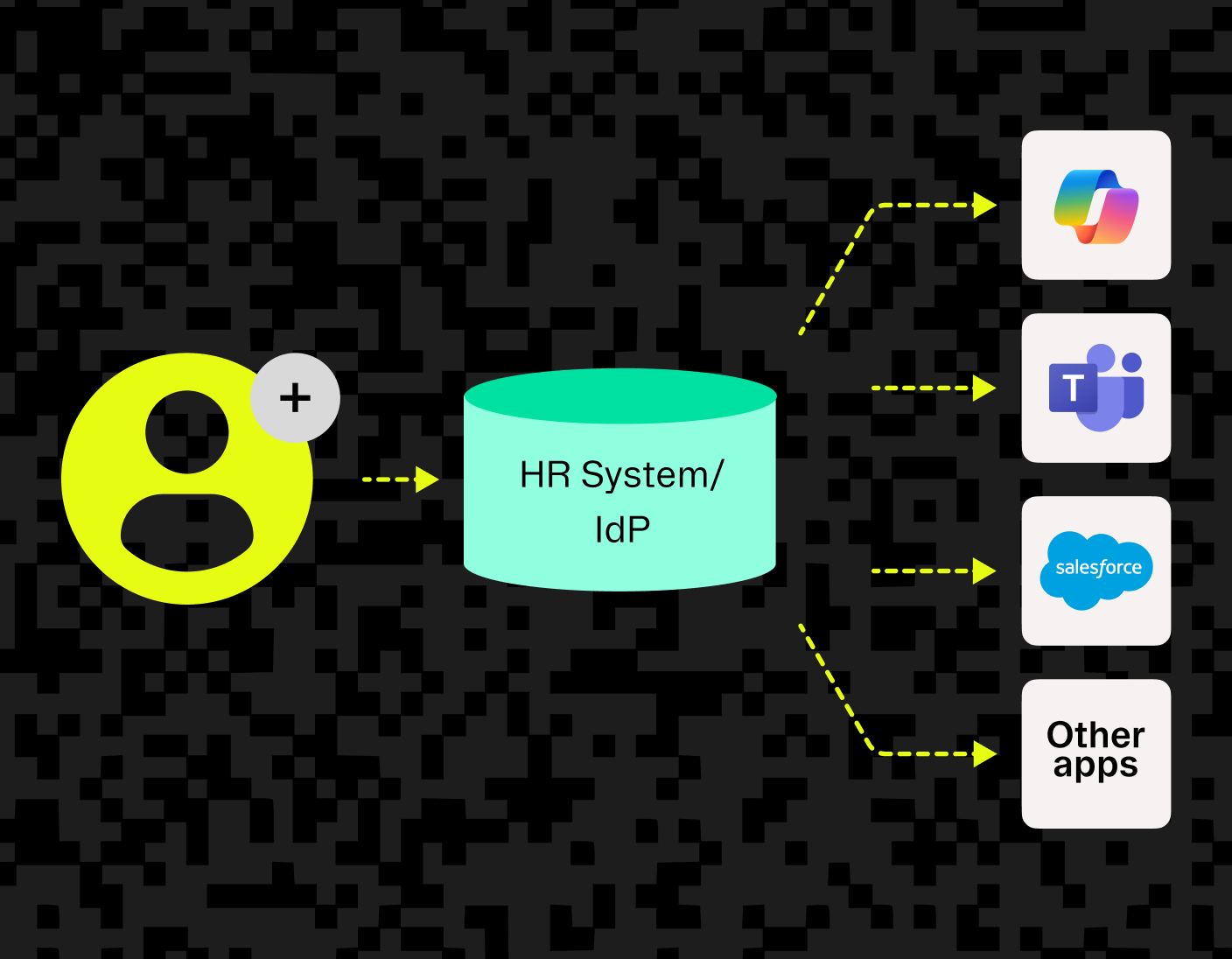
System for Cross-domain Identity Management (SCIM) is an open standard that automates user provisioning and deprovisioning across multiple applications and services.
Without automated provisioning, IT teams face significant operational overhead: manually onboarding employees, updating permissions when roles change, and ensuring immediate access removal when an employee leaves.
For B2B SaaS companies, SCIM support has become essential to making enterprise sales. Customers expect seamless integration with their existing identity infrastructure to be able to manage employee access at scale.
What are SCIM tools?
The term "SCIM tools" encompasses software solutions that help you implement SCIM. While some might simply call these "SCIM-enabled solutions" or "SCIM implementations," we use "SCIM tools" here as a convenient umbrella term that includes:
SCIM clients are providers (IdPs) like Okta, Microsoft Entra ID and JumpCloud that have built-in SCIM support. These initiate user provisioning requests when users are added, modified, or removed from the IdP. While they're primarily identity management platforms, their SCIM capabilities make them relevant tools for implementing automated provisioning.
SCIM service providers are applications (like Salesforce, Microsoft teams, or your own SaaS app) that have implemented SCIM APIs to allow their customers to automatically create, update, or deactivate users in their instance. Again, these aren't exclusively SCIM tools, but their SCIM support makes them part of the SCIM ecosystem.
SCIM libraries help you add a SCIM REST API to your own SaaS app by offering reusable code for things like parsing SCIM requests, validating SCIM schemas, and formatting the responses. However, the real complexity lies in what happens after parsing - determining how to map SCIM operations to your application's user model, handling edge cases like deactivating users and revoking their sessions, managing group memberships, and ensuring data consistency across your system.
Third-party SCIM providers (like Stytch, Auth0, or Frontegg) offer managed SCIM service provider functionality, handling the entire protocol implementation.
Rather than building and hosting your own SCIM API, these platforms act as the integration layer. They receive provisioning requests from your customers’ IdPs, translate those into user operations for your app, and send them via webhook or API. This way you get complete SCIM functionality and full control without actually owning the protocol surface.
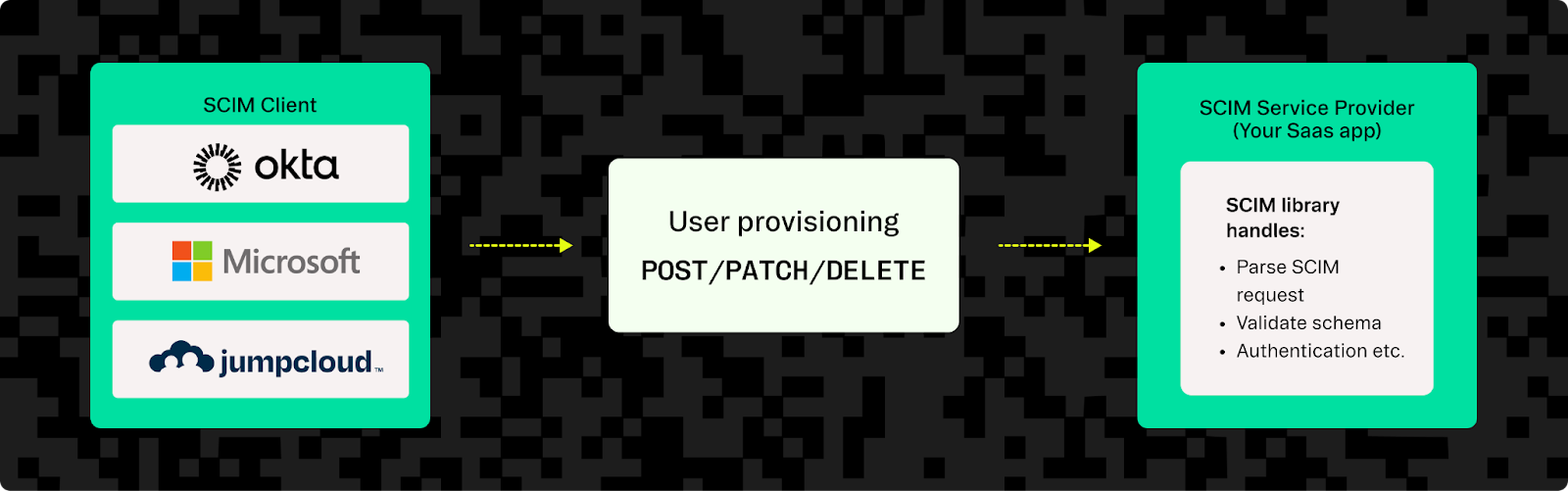
Most B2B applications need to become SCIM service providers to receive provisioning requests from their customers' IdPs. While libraries can help build this capability in-house, specialized SCIM providers like Stytch offer pre-built infrastructure that handles IdP-specific logic, eliminating the need to implement and maintain provisioning workflows yourself.
How SCIM automates identity lifecycle management
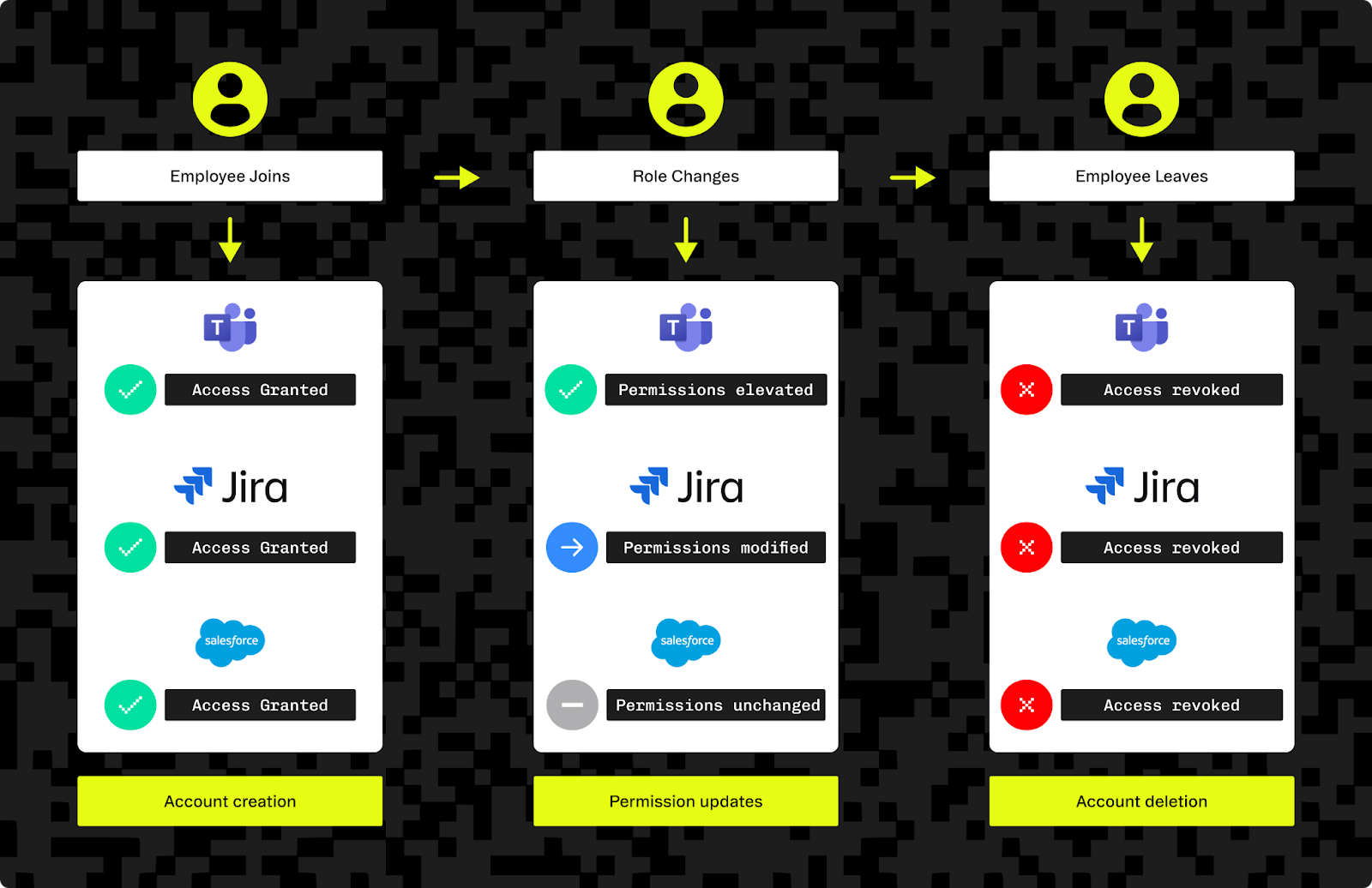
SCIM creates a synchronized pipeline between your customers’ identity systems and your SaaS application. When an employee joins, changes roles, or leaves the company, their IdP automatically sends SCIM requests to the SCIM REST API or all connected applications to update access. This happens in real time without manual intervention. New hires gain immediate access to necessary tools, role changes trigger appropriate permission updates, and departing employees instantly lose access across all systems.
This has a few major benefits:
- Reduced IT workload: eliminates manual account management across multiple systems
- Enhanced security: automatic deprovisioning prevents orphaned accounts and reduces access-related security risks
- Improved compliance: centralized audit trails and consistent access policies simplify regulatory reporting and reviews
- Better user experience: employees gain immediate access to tools they need without having to wait around
SCIM vs. SAML
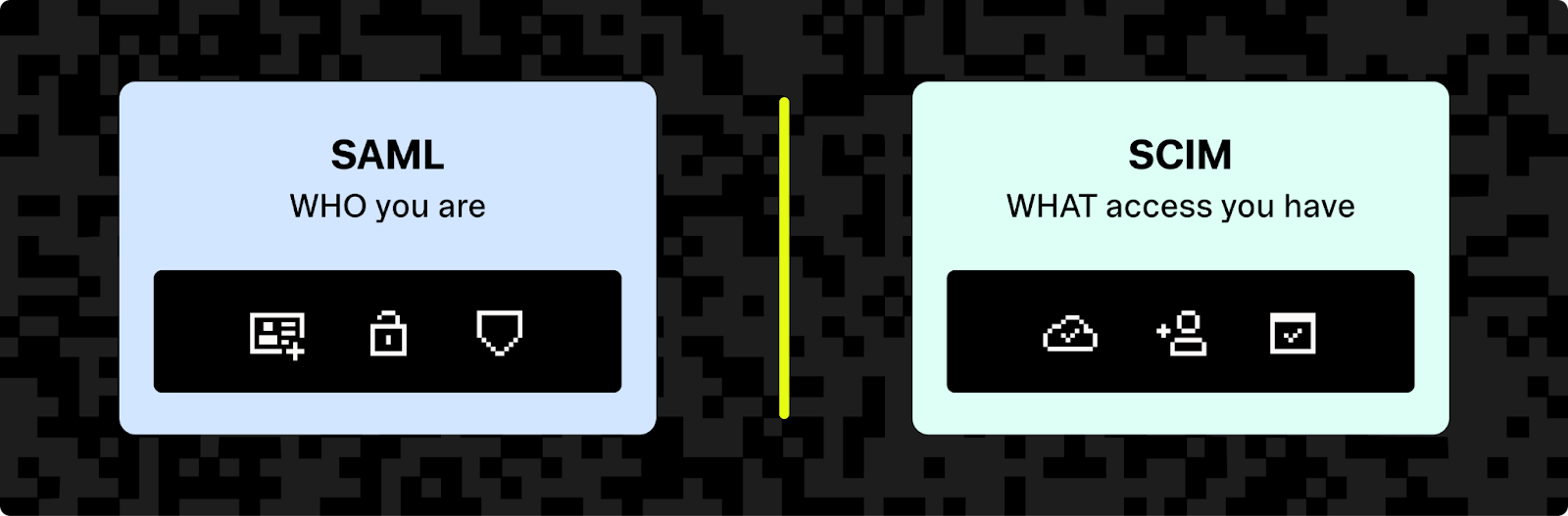
While SAML handles authentication (which proves who you are), SCIM focuses on provisioning (managing access). SCIM often works alongside this protocol — SAML for single sign-on, and SCIM for automated account lifecycle management — creating a complete identity management solution.
Essential features to look for in SCIM solutions
When evaluating SCIM implementation options for your B2B SaaS application, focus on the following capabilities. Whether you're choosing a third-party SCIM service, evaluating libraries, or selecting an IdP for internal use, these features determine implementation success and long-term viability.
Full SCIM 2.0 compliance
Whether you're choosing a SCIM client, provider, or library, you should look for one with full SCIM 2.0 compliance — that is, one that follows all the major SCIM specifications (RFC 7642, 7643 and 7644). This includes full CRUD capability for users and groups. A common frustration when implementing SCIM can be to get started and then find that your SCIM tools don't support PATCH and DELETE operations, so choose carefully. Choosing standards-compliant tools ensures compatibility with major IdPs and helps future-proof your applications against protocol changes. Avoid any proprietary solutions that lock you into vendor-specific implementations or that require additional custom integration work.
Group and role management
Look for SCIM tools with robust group synchronization capabilities that enable automatic role-based access control (RBAC). The tool should seamlessly map IdP groups to application roles without manual configuration, simplifying permission management across your user base. This feature eliminates the need to manually assign roles and ensures users automatically receive appropriate permissions based on their group membership.
Security and compliance requirements
Look for robust token-based authentication, encrypted data transmission, and compliance certifications like SOC 2 and ISO 27001.
Essential capabilities include audit logging, rate limiting protection, and support for industry-specific regulations like GDPR or HIPAA.
Developer experience and APIs
Well-documented APIs, comprehensive SDKs, and developer-friendly tooling enable your team to deliver SCIM support faster.
Sandbox environments and webhook support are must-haves, as is responsive technical support for your developer team during implementation.
Scalability and bulk provisioning support
As well as the standard requirement that any solutions should be able to handle enterprise-scale user volumes, it's also worth considering the need to support bulk user-provisioning operations. Large scale mergers, organization restructures, or new application go-live dates can all require large amounts of user provisioning to be done at once, and bulk operations support can be hugely beneficial in these cases.
Deployment options and data residency
If your organization has strict on-premises or geographic data residency requirements, you'll need to check that any third-party SCIM tools offer the options you need to keep your data secure.
Customer onboarding and admin experience
Look for SCIM tools that offer embeddable admin portals or SDK components for your customers. These allow your end users to configure IdP integrations, group-role mapping, and SCIM provisioning flows directly in your application, dramatically reducing support load and accelerating onboarding.
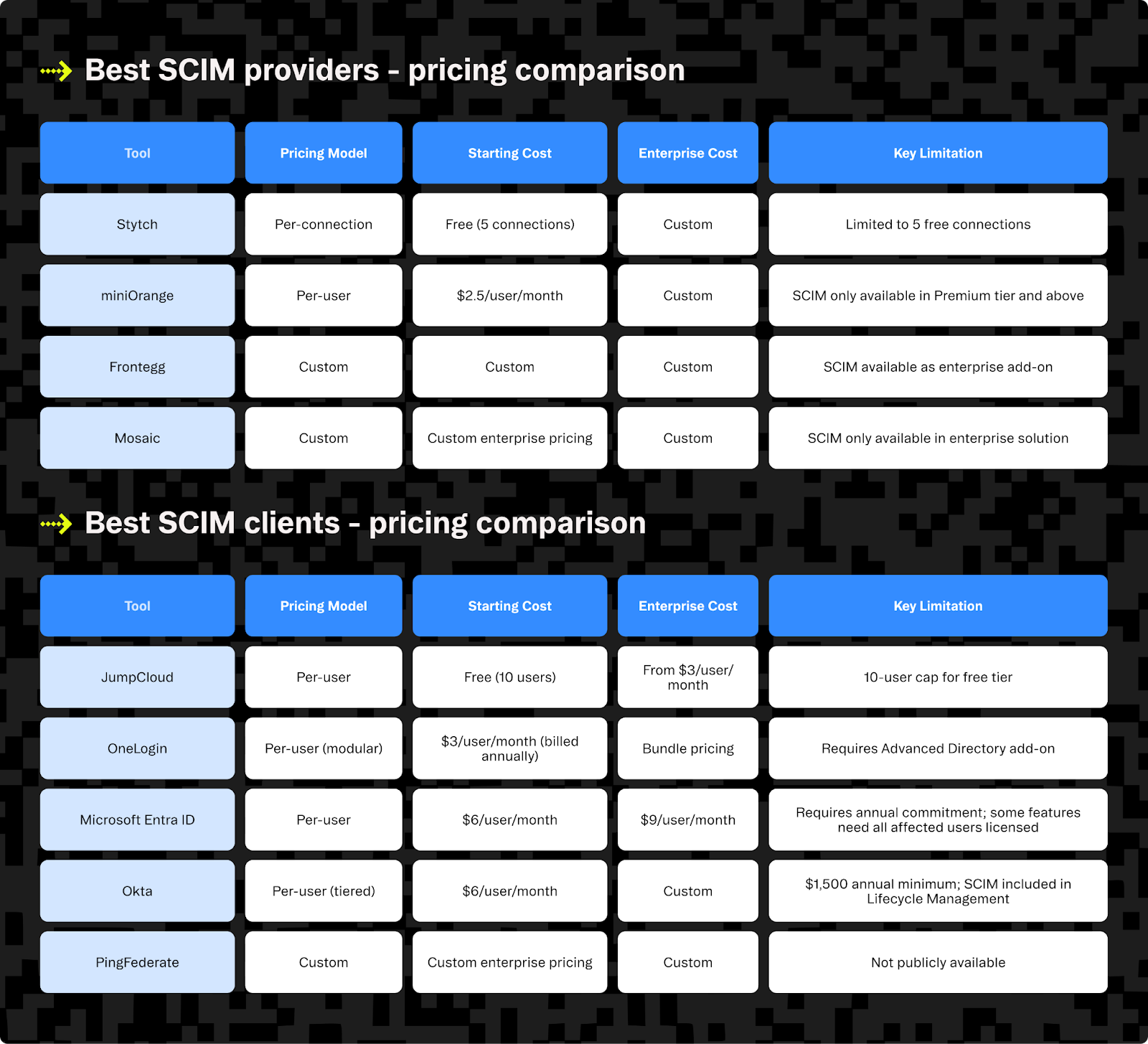
Best SCIM providers and clients
The SCIM landscape is divided into two primary categories: SCIM providers that receive provisioning requests (what most B2B applications need) and SCIM clients that send provisioning requests (typically identity providers). Some solutions, such as miniOrange, offer both capabilities.
Understanding the different pricing models is crucial for decision-making. Per-connection pricing charges based on the number of SCIM integrations, making costs predictable for B2B SaaS companies. Per-user pricing charges for each user account managed, which works well for internal identity management. Custom enterprise pricing typically involves annual contracts with professional services for complex implementations.
Looking for a quick pricing comparison? The tables below show at-a-glance pricing and key limitations across major SCIM providers and clients. For a detailed feature analysis or to explore the best open-source libraries, jump to the next section.
Note that while many CIAM platforms like Auth0, Amazon Cognito, and Firebase Authentication offer some user provisioning capabilities, they are generally optimized for B2C authentication flows and do not natively support SCIM 2.0 as a service provider. Implementing SCIM with these tools typically requires significant custom development or third-party middleware.
Best SCIM providers
Stytch
Stytch stands out among SCIM providers with its transparent pricing and developer-first approach. Unlike competitors that require sales consultations, Stytch offers predictable costs that scale naturally with business growth.
Key features:
- Full SCIM 2.0 implementation with real-time synchronization
- Production-hardened handling of IdP edge cases and token rotation
- Embeddable admin portal for customer self-service configuration
- Webhook integration for downstream system synchronization
- IdP-agnostic design supporting Okta, Microsoft Entra ID, Google Workspace
- Embeddable Admin UI and SDKs for self-service SCIM setup with automatic group-to-role mapping
Pricing:
- Free tier: 10,000 MAUs with 5 SCIM connections included
- Additional connections: $125 per connection
- Enterprise: custom pricing with 99.999% SLA
Total cost example: A company with ten enterprise customers would pay $625/month ($125 × 5 additional connections) after using the five free connections.
Frontegg
Frontegg is a SCIM provider that targets enterprise B2B SaaS with strong security compliance and multi-tenant architecture designed for B2B applications.
Key features:
- SCIM 2.0 standard support with self-service configuration
- Advanced RBAC with subscription and feature flag permissions
- SOC 2 Type II and ISO 27001 compliance
- Pre-configured support for Microsoft Entra ID, Okta, and Google Workspace
Pricing:
- Requires sales engagement for pricing details
Best SCIM clients
Microsoft Entra ID
Microsoft Entra ID is the logical choice for Microsoft-centric organizations, offering deep Microsoft 365 integration and extensive application support.
Key features:
- Full SCIM 2.0 protocol support and integration with 3,000+ pre-configured gallery applications
- Hybrid provisioning for cloud and on-premises applications
- Advanced attribute mapping with expression-based transformations
- Enterprise certifications including SOC 2, ISO 27001, FedRAMP
Pricing:
- Free tier: only basic SCIM provisioning included
- P1 License: ~$6/user/month (group assignments, on-premises agent)
- P2 License: ~$9/user/month (advanced governance features)
- Note: Partial licensing is not allowed. A per-user license is required for every user provisioned to your applications via SCIM.
Okta Identity Cloud
Okta Identity Cloud is the market leader with extensive pre-built integrations and comprehensive governance capabilities for cloud-forward enterprises.
Key features:
- 7,000+ pre-built integrations
- Advanced governance capabilities in Identity Governance suite
- 99.9%+ uptime SLA with global availability
Pricing:
- Suite-based pricing: Essentials, Professional, Enterprise tiers
- Custom pricing requires sales consultation
OneLogin
OneLogin offers modular pricing and strong security certifications, making it well suited for security-conscious mid-market organizations.
Key features:
- Full SCIM 2.0 compliance
- 5,000 API calls/hour rate limit per account
- Comprehensive security certifications: SOC 2, ISO 27001, 27017, 27018
- Advanced rule engine with regex support
Pricing:
- $3/user/month (billed annually, includes SSO + Advanced Directory + MFA)
Total cost example: a 200-user organization needs $600/month for basic SCIM functionality.
JumpCloud
JumpCloud provides a cloud-native solution that includes SCIM functionality in its base pricing without requiring add-on purchases or higher-tier plans, making it ideal for unified device and identity management.
Key features:
- Full SCIM 2.0 compliance
- Extensive pre-built connectors (Slack, AWS, GitHub)
- MSP multi-tenant capabilities
Pricing:
- Free tier: 10 users (SCIM only)
- Paid tiers start at $3/user/month (billed annually)
- Enterprise Platform & Platform Prime: custom pricing
PingFederate
PingFederate is an enterprise-focused federation solution offering both SCIM client and limited server capabilities.
Key features:
- Dual role functionality: both SCIM client and server
- Enterprise security certifications: SOC 2, ISO 27001
- Extensive connector library including GitHub EMU, ServiceNow
- Advanced attribute mapping
Pricing:
- Custom enterprise pricing: not publicly available
- Requires direct consultation for pricing details
Best SCIM tools for different business sizes
When selecting SCIM clients or providers, your organization's size and growth trajectory directly impact which pricing model and feature set will deliver the best value.
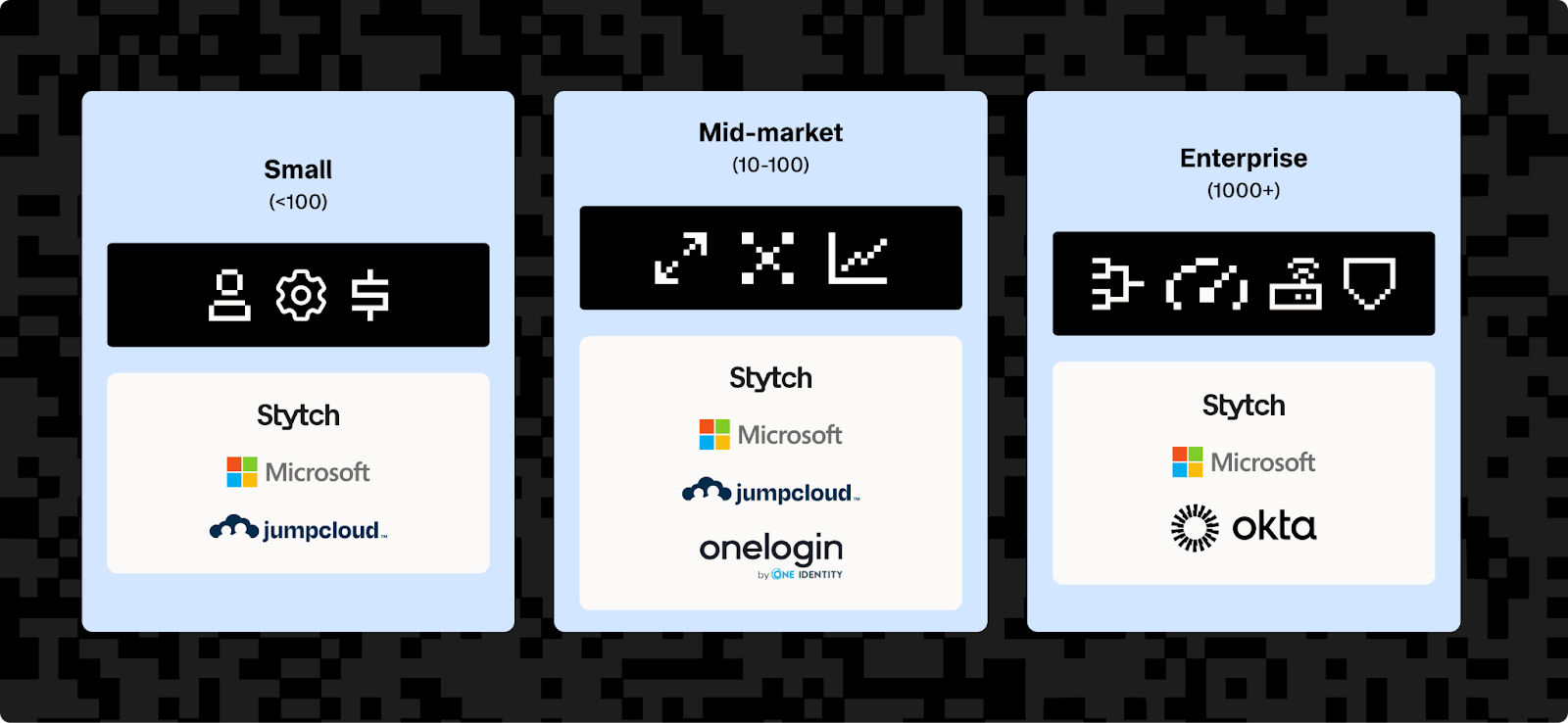
Alt: Identity providers are categorized by company size from small to enterprise with different feature requirements.
Enterprise solutions (1000+ employees)
Organizations at enterprise scale need SCIM tools with extensive governance features, complex organizational hierarchy support, and comprehensive compliance capabilities. Custom enterprise pricing typically provides the best value at this scale, with annual contracts offering budget predictability and included professional services.
For cloud-first enterprises needing extensive third-party application support, Okta Identity Cloud leads with its 7,000+ integrations. Microsoft Entra ID works best for Microsoft-centric organizations requiring hybrid cloud and on-premises provisioning. B2B SaaS companies often prefer Stytch Enterprise for its transparent pricing and fast procurement without lengthy sales cycles.
Mid-market solutions (100–1000 employees)
Mid-market organizations benefit from SCIM tools that balance enterprise features with transparent pricing and reduced implementation complexity. The key decision comes down to your growth trajectory. Per-connection pricing scales with your customer base, while per-user pricing scales with your employee count. Self-service setup and predictable costs without enterprise minimums make implementation feasible without dedicated IT resources.
Stytch stands out for B2B SaaS companies with its per-connection model that scales with customers rather than employees. JumpCloud offers unique value by including SCIM in its base SSO pricing, making it excellent for unified device and identity management. Security-conscious organizations often choose OneLogin for its modular approach that lets them add only the features they need.
Small business solutions (<100 employees)
Smaller organizations need cost-effective SCIM tools with minimal administrative overhead and easy setup processes. Free tiers provide the perfect entry point, letting you implement SCIM before revenue justifies paid solutions. The best options offer seamless migration paths to paid tiers as you grow, avoiding painful platform switches later.
JumpCloud's free tier supports up to 10 users with full SCIM capabilities, which is perfect for small teams testing enterprise identity management. Stytch offers 10,000 MAUs with 5 SCIM connections free, ideal for B2B startups preparing for their first enterprise customers. For teams already using Microsoft 365, Microsoft Entra ID includes basic SCIM provisioning in existing subscriptions, making it the natural choice.
Best open-source SCIM tools
For organizations with specific requirements, strong development resources, or budget constraints, open-source SCIM solutions offer flexibility and customization opportunities. These are good choices when you have dedicated development teams, unique customization requirements, or specific compliance needs that commercial solutions can't address. However, they require significant development resources and ongoing maintenance compared to managed services, including long-term security update responsibilities.
i2scim
i2scim is a Kubernetes-deployable SCIM server implementation that functions as a generalized SCIM engine. Unlike fixed implementations, it supports configurable endpoints and schemas defined in JSON, with custom resource types and attributes for specialized use cases.
Scimmy (Node.js library)
The SCIMMY library provides a comprehensive SCIM 2.0 implementation for Node.js applications, handling protocol compliance, schema validation, and resource management with minimal configuration required for basic setups.
.NET and Java options
The UnboundID SCIM 2.0 SDK for Java by PingIndentity and SCIM Client for .NET provide production-ready implementations with extensive documentation. WSO2 Charon is another open-source modular Java-based SCIM 2.0 implementation with separate core API, utilities, and reference implementation components for flexible integration.
Testing tools (SCIM.dev)
SCIM.dev offers a learning platform in the form of compliance testing and validation tools that help developers verify their SCIM implementations against standard specifications, reducing integration issues with major identity providers during development phases.
Limitations of building your own SCIM service provider
While open source libraries provide a foundation, building custom SCIM implementations introduces significant challenges that organizations often underestimate during initial planning phases.
Implementation challenges and development overhead
SCIM compliance requires handling complex edge cases like IdP-specific token formats, pagination quirks, and race conditions during rapid provisioning changes. Nested organizational hierarchies and custom attribute mapping demand sophisticated data modeling that extends far beyond basic CRUD operations for user accounts.
Scalability problems for complex organizations
Generic SCIM implementations struggle with enterprise organizational structures involving multiple subsidiaries, cross-functional teams, and dynamic role assignments. Supporting bulk operations, real-time synchronization, and complex group memberships requires architectural decisions that aren't apparent during initial development phases.
Resource requirements for maintenance
SCIM implementations require ongoing updates for new IdP versions, security patches, and protocol enhancements. Developer time allocated to SCIM maintenance diverts resources from core product features and customer-facing improvements.
Security considerations
Custom implementations must handle secure token storage, rate limiting, audit logging, and encryption properly. Security vulnerabilities in identity provisioning systems create company-wide access risks that extend far beyond individual application compromises.
How Stytch streamlines SCIM development
While the challenges of custom SCIM implementation are significant, Stytch addresses these pain points with a comprehensive platform designed specifically for B2B SaaS companies.
Superior organization data model architecture
Stytch's native multi-org architecture ensures complete isolation between organizations, with each having dedicated user bases and SCIM configurations. Unlike retrofitted B2C solutions, this org-first design prevents identity leakage risks and enables org-specific email updates, which is critical for enterprise SCIM deployments where cross-organization access poses security vulnerabilities.
Enhanced enterprise control capabilities
The platform includes embeddable Admin Portal components that handle SCIM provisioning setup, group-role mapping, and member management out of the box. Customers can configure SCIM integrations directly through the Admin Portal or API with automatic RBAC role assignment based on SCIM group membership, email domains, or SSO connections, which eliminates custom middleware requirements.
Developer-friendly APIs and implementation
Stytch handles IdP-specific nuances for Okta and Microsoft Entra ID without requiring custom logic for each provider. The platform automatically supports SCIM filtering, PATCH operations, and schema extensions while providing webhook events for downstream synchronization and production-hardened handling of race conditions, token rotation, and pagination issues.
Transparent pricing and procurement
Unlike enterprise-only competitors, Stytch offers SCIM support on free and self-serve paid plans with clear per-connection pricing. This eliminates lengthy procurement cycles and makes SCIM implementation predictable from both cost and timeline perspectives, enabling faster enterprise sales cycles.
Let Stytch implement SCIM for you
Stytch stands out with transparent per-connection pricing, comprehensive SCIM 2.0 implementation, and production-hardened IdP compatibility. The embeddable admin portal enables customer self-service while native multi-org architecture ensures enterprise-grade security without lengthy procurement cycles or complex licensing negotiations.
Ready to streamline your SCIM implementation? Explore Stytch's identity management solutions with a free tier supporting 10,000 MAUs and 5 SCIM connections.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.