Back to blog
Auth0 reviews: Why developers migrate from Auth0 to Stytch
Auth & identity
Mar 21, 2025
Author: Stytch Team
Across forums, blogs, and community threads, developers regularly share their experiences with authentication—what works, what breaks, and what drives them to switch solutions. One authentication provider that frequently comes up in these conversations? Auth0.
At Stytch, we’ve listened closely to developers migrating from Auth0, and we’ve noticed a set of recurring themes behind their decisions.
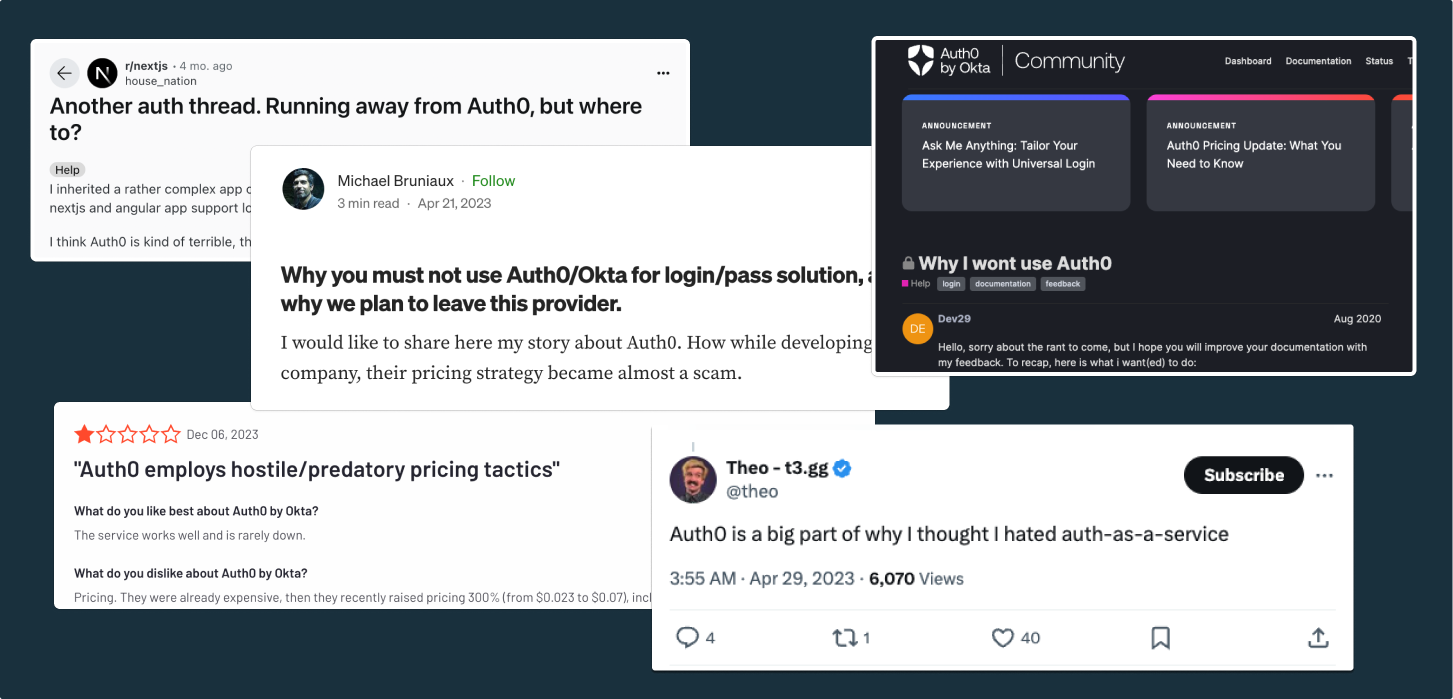
In this article, we’ve compiled some of the most common reasons why developers migrate from Auth0 to Stytch for authentication. We’ve collected and cited comments from blog posts, Reddit, Twitter, Hacker News, G2, StackOverflow, and Auth0’s community forum to bring you unfiltered opinions from actual Auth0 developers on why they made the switch—in their own words.
Let’s dive in.
Auth0 pricing: You shouldn’t have to pay a fortune for auth
What drives an engineer to be frustrated enough to write an entire article warning other devs away from a vendor? Not a quick angry tweet. Not a comment. But an entire article!
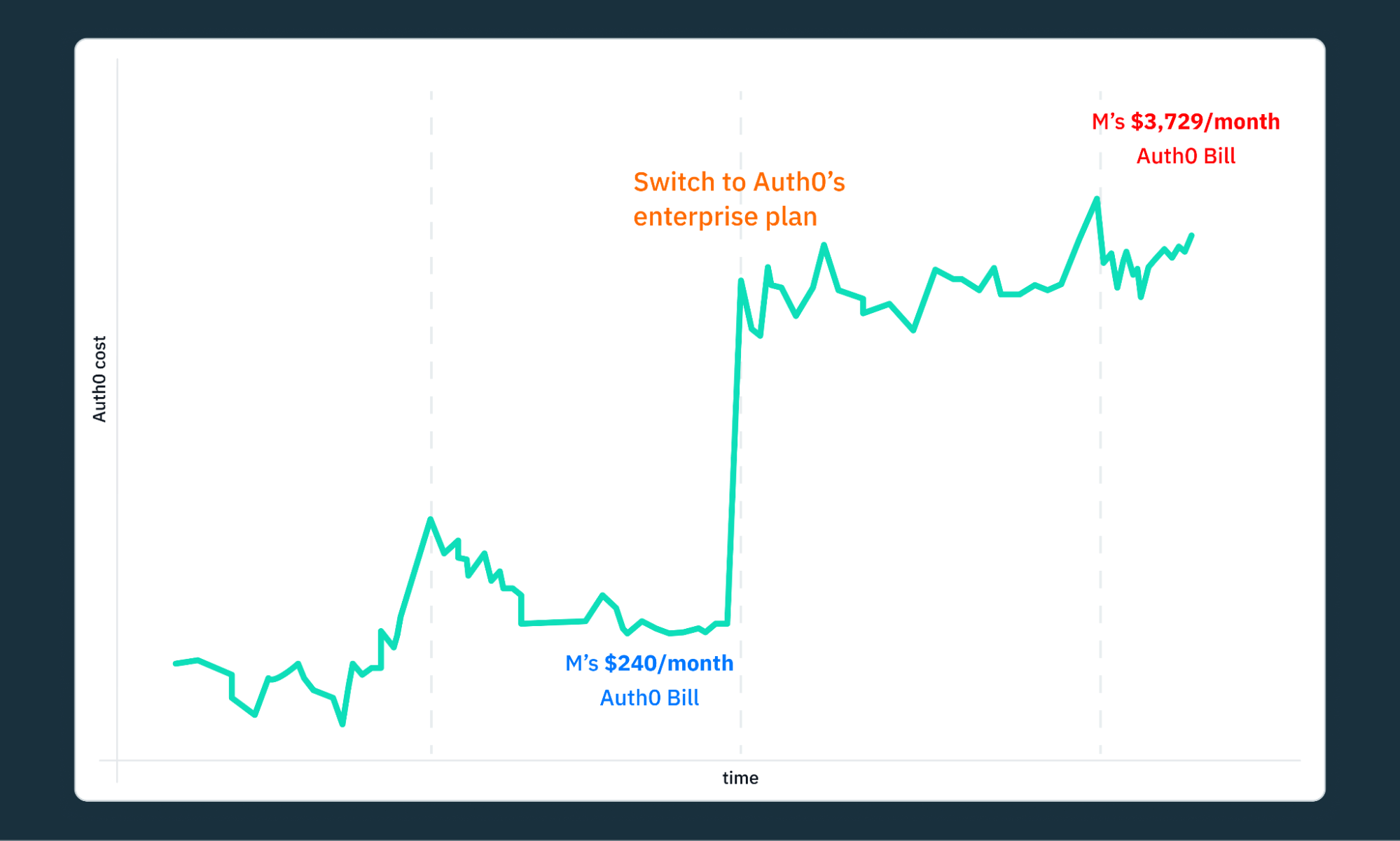
Michael Bruniaux’s story is unfortunately a common one. Their company’s Auth0 bill exploded by 15.54x (from $240/month to $3,729/month) despite modest user growth and no new feature usage. In his article he details how Auth0’s pricing felt like a scheme to trap their company into a costly enterprise plan.
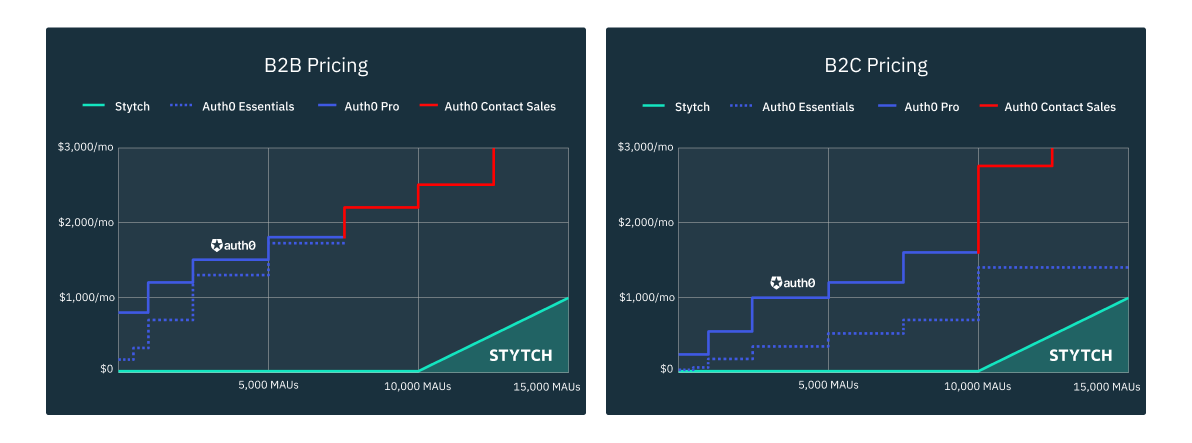
Auth0 pricing has always been one of their most unpopular qualities as an auth provider. Every day we see online comments complaining about the same pain points: feature restrictions, unexpected caps, and hidden fees that force costly upgrades.
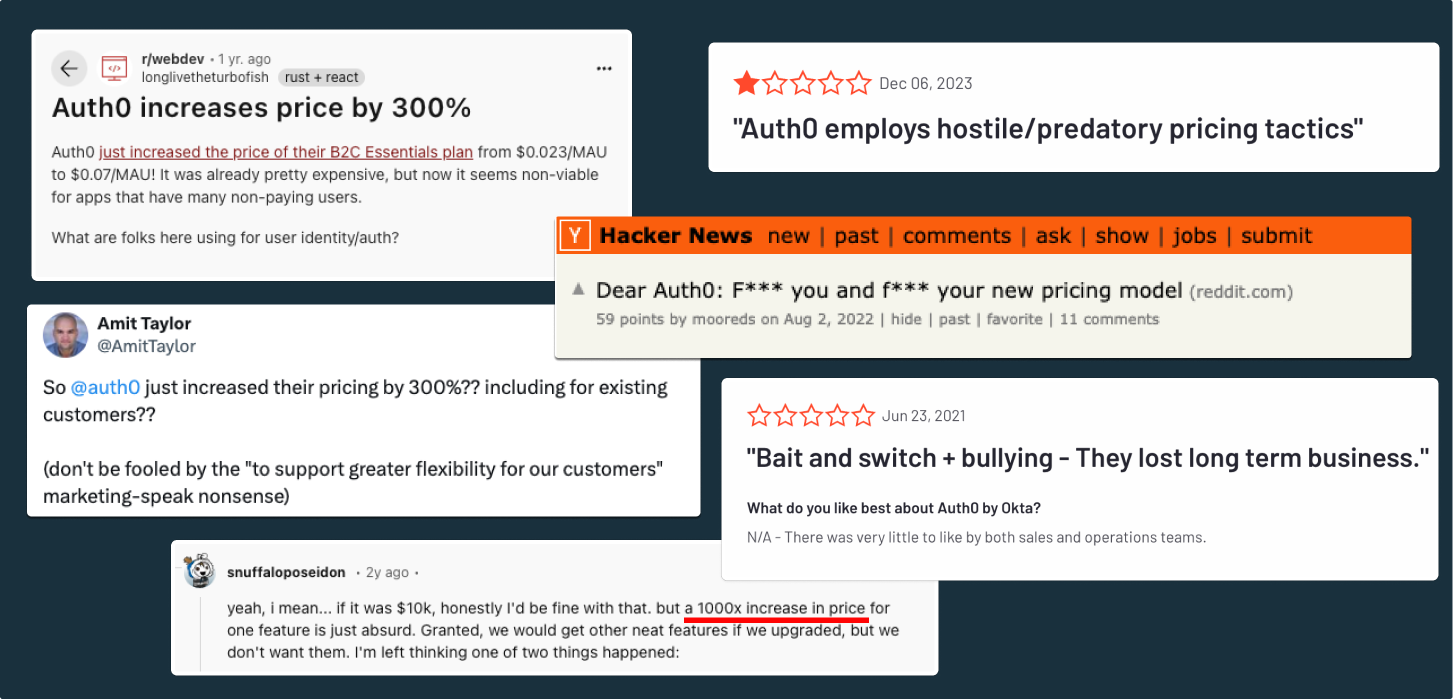
As you can see from the reviews above, one of the major frustrations many companies face once they’re locked in with Auth0 is the unpredictable price increases. It’s clear that their customers don’t want surprises or restrictions from their authentication provider that punishes growth with unreasonably high bills.
And despite their most recent pricing update to their free plan, Auth0’s pricing is still designed to feel like a classic bait-and-switch once applications outgrow the free plan’s limits.
Auth0 customer support: Can we get some help?
For many developers, effective customer support is just as critical as the product itself. Unfortunately, Auth0's customer support has often left developers feeling frustrated and unsupported with reports of unresponsiveness and unresolved issues piling up. Authentication is a critical part of infrastructure, and poor support from an auth provider can quickly become a dealbreaker.
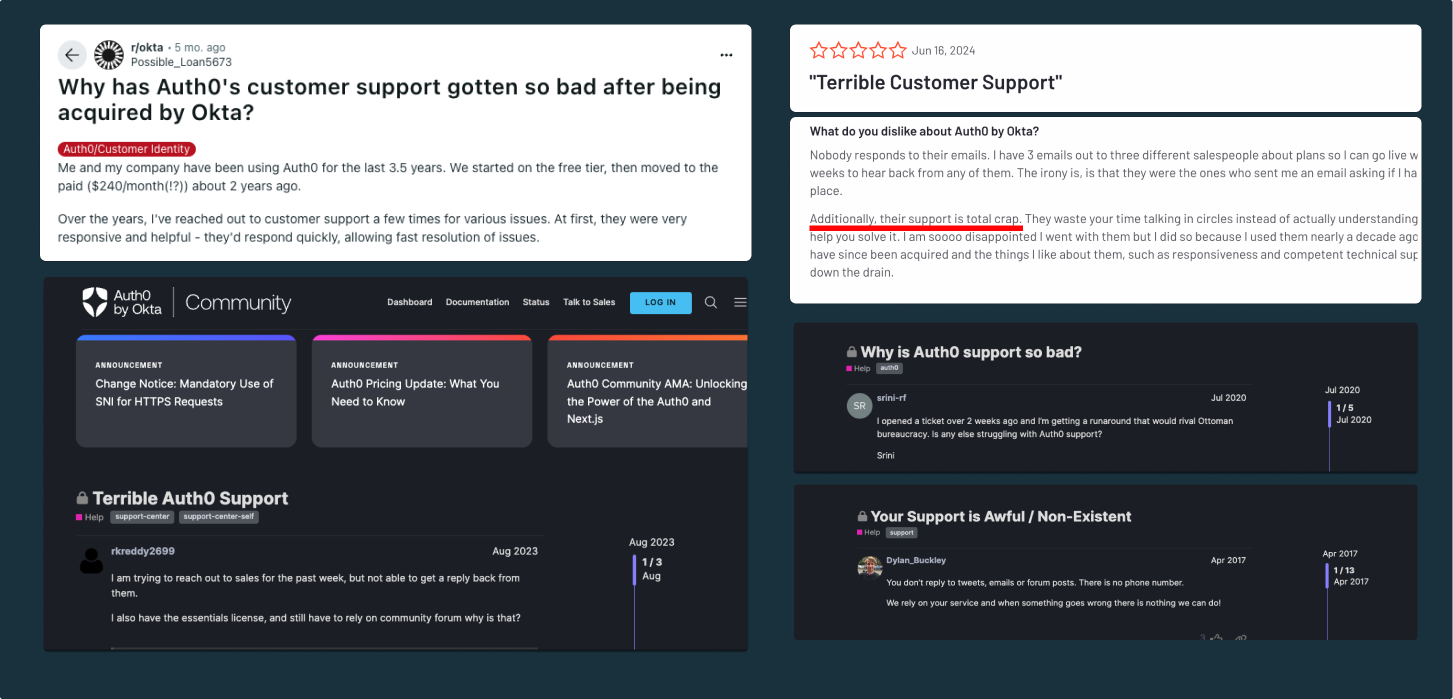
Developers describe waiting multiple weeks for a reply only to receive a generic templated response that didn’t address their specific issue. Some even claim unresolved issues are being closed and then ignored for several months.
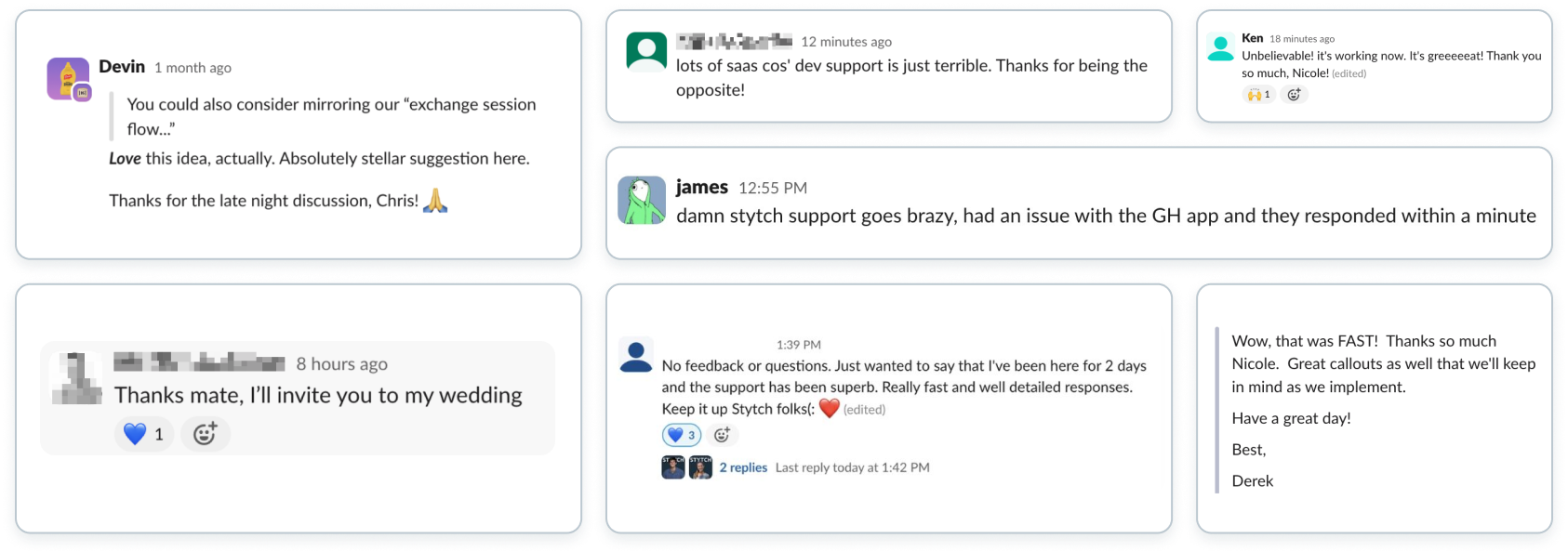
Unlike Auth0, Stytch offers direct support starting even with the free plan, available through our official developer Slack, forum, and email. Our commitment is to be your trusted authentication partner for the long haul.
Auth0 developer experience: Falling short where it matters most
The heart of a dev-focused tool is in the quality of development experience it provides, and this is what has been slowly declining with Auth0, especially since it was acquired by Okta.
Spending weeks building around deliberate restrictions and wrestling with an authentication platform that’s supposed to save you time is a losing battle. Wasting engineering hours to workarounds, manual processes, and support tickets isn’t just an inconvenience—its a direct hit to your team’s productivity and codebase quality.
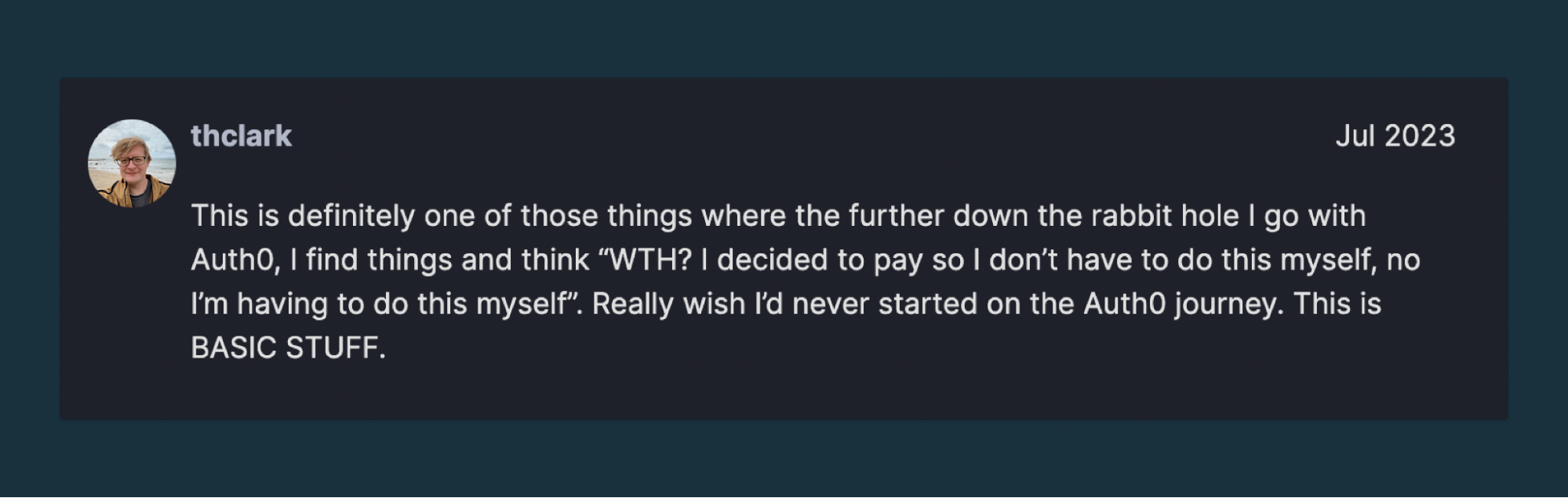
We stumbled upon several developers and engineering teams voicing their concerns about the Auth0’s usability (both APIs and SDKs) and highlighted key sticking points with their Auth0 integrations.
Auth0’s uncustomizable Universal Login
Auth0’s Universal Login is their “out-of-the-box” login product that developers are compelled to use, whether it’s SAML, OIDC, Passwords, Passwordless, or even multi-tenant organization flows.
The problem? Auth0’s Universal Login is a one-size-fits-all approach that fits almost no one perfectly. The most enforced pain point with Auth0’s Universal Login is the mandatory redirect during authentication: your users will be redirected away from your app to an Auth0-hosted domain before they’re sent back to your app.
Universal login sacrifices user and developer experience by design since it effectively strips developers of any native in-app code control over the auth flow. Customization options are limited and restrictive, and the auth experience almost always feels separate from your app rather than part of it.
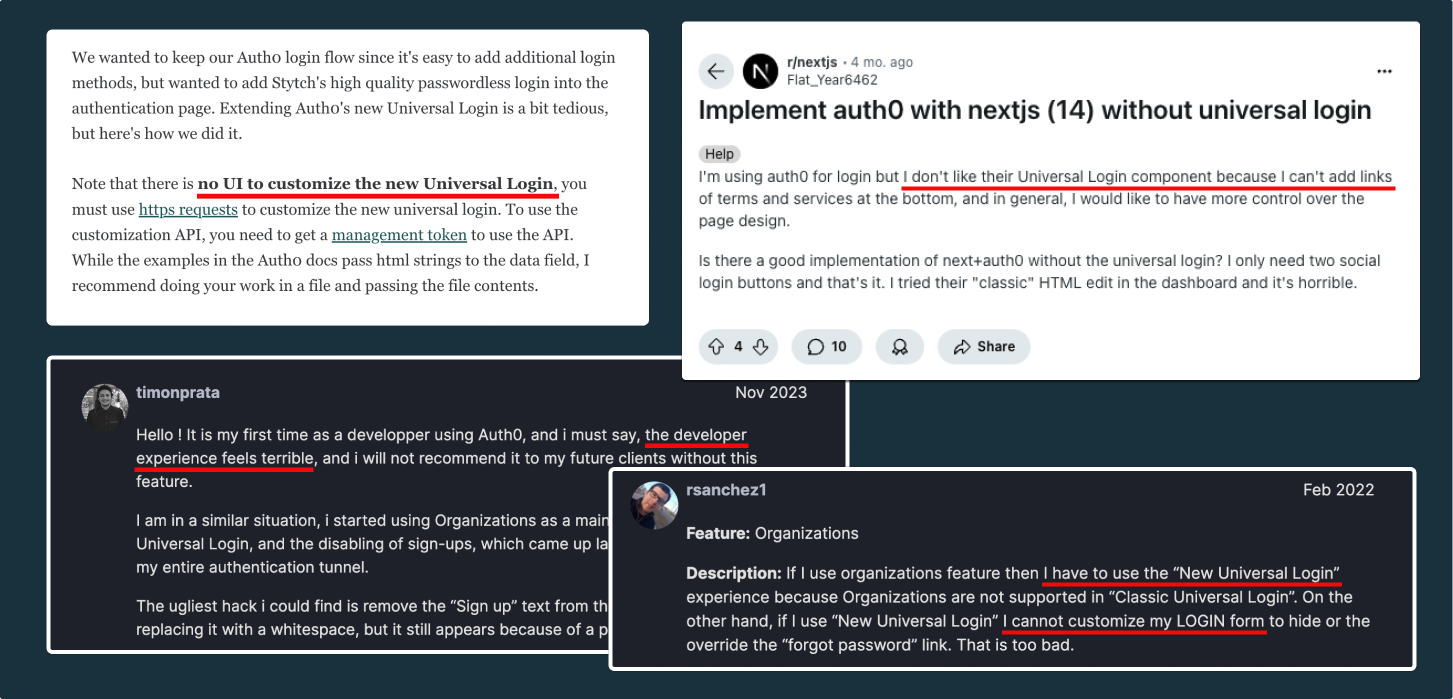
Take passwordless authentication, for example. You’d naturally expect Auth0’s Universal Login to support email magic links or OTP during signup or sign-in without requiring Auth0’s Actions/Rules, which are similar to lambdas or edge functions. With so many workarounds, implementing basic auth capabilities feels like building from scratch.
But as Frederick points out, shouldn’t Universal Login handle everything?
Stytch takes a completely different integration approach with embedded authentication, keeping users entirely within your application’s domain. Unlike universal login, embedded authentication gives developers maximum control over the entire UX by keeping the auth code and logic natively within your app.
Learn more about the differences between Stytch Embedded Auth vs. Auth0 Universal Login.
Auth0’s multi-tenancy is tightly coupled with Universal Login
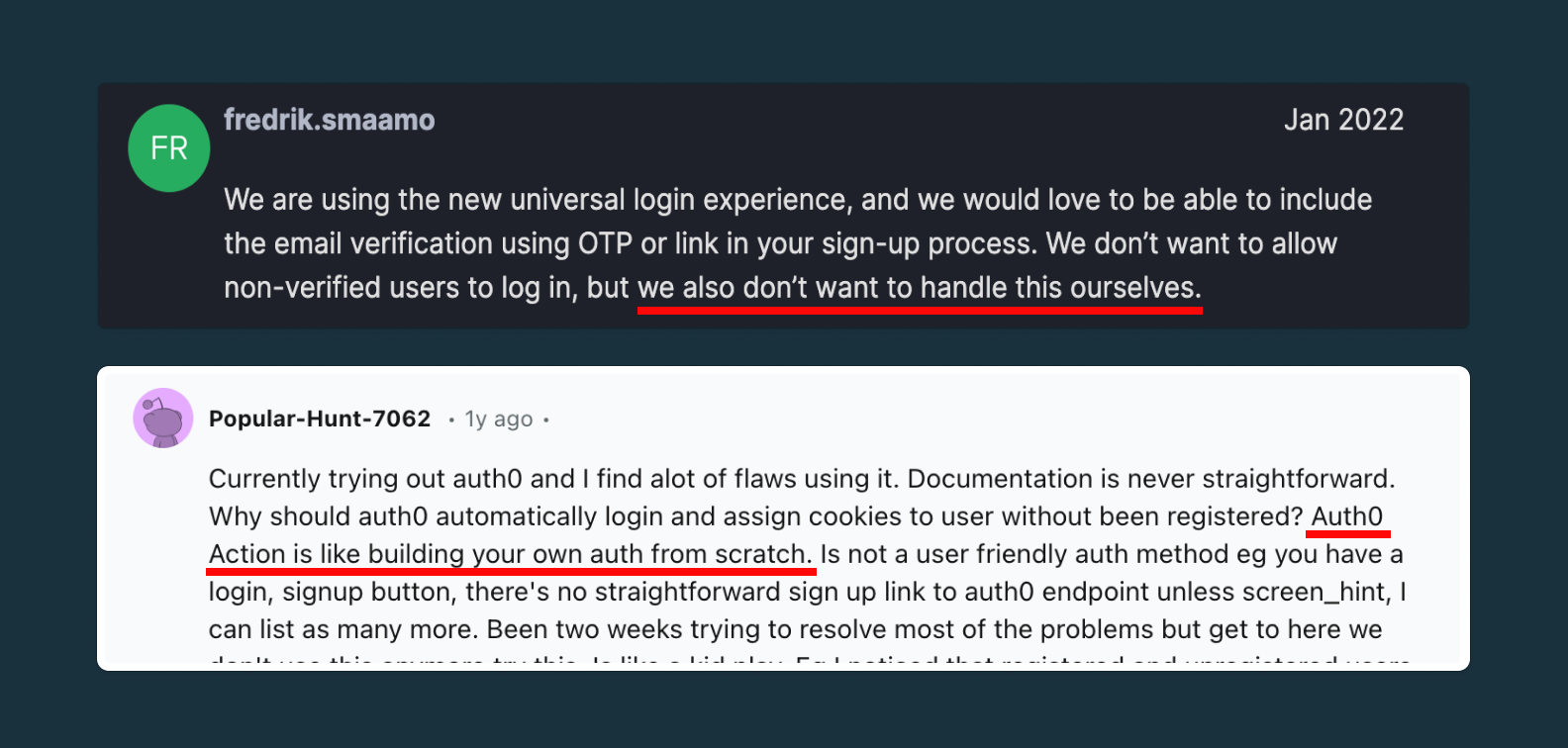
To manage multi-tenant auth in your B2B SaaS, you’re once again forced to use Auth0’s Universal Login.
Imagine building a multi-tenant SaaS app where new users can’t create accounts under their tenants because they signed up via an invitation link instead of directly through Universal Login. This is just one of the side effects of Auth0’s Universal Login controlling everything. Others include clunky multi-factor authentication policies, no switching between organizations, and a lack of flexibility where it matters most.
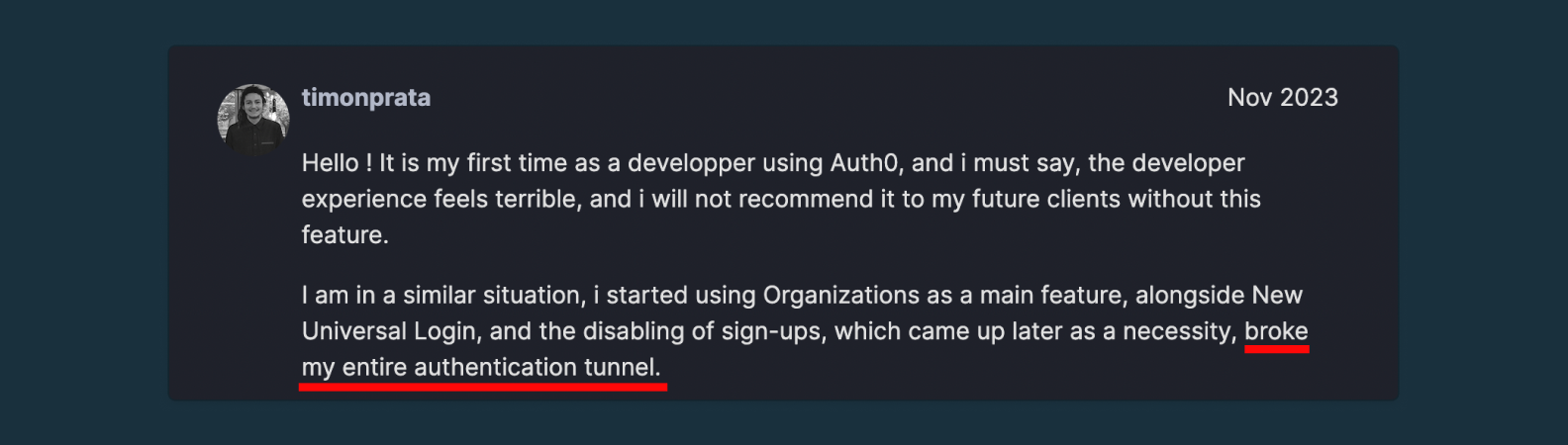
Auth0 users like Timon have run into this exact issue.
Stytch takes a fundamentally different multi-tenant approach by making organizations the foundation of our B2B data model. This org-first architecture makes it possible for your enterprise customers to be able to customize everything—member invitations, organization-specific auth factors, approved domains, SSO, JIT provisioning —without building temporary hooks or refactoring their auth systems.
Duplicate Auth0 users
Another major flaw in in Auth0's authentication is its handling of data duplication and user management.
When a user authenticates through OAuth (e.g. Google or Microsoft) and later logs in with email and password, Auth0 creates two separate user records, even if both accounts share the same email and belong to the same person. With Auth0, simply offering multiple options for login and signup creates significant problems for your app.
This data duplication forces engineering teams to write middleware or scripts to clean up to merge user accounts, and, in the worst cases, users may need to reset passwords or re-authenticate based on the auth method they initially used. The founder of Syften, a popular social monitoring tool, wrote a blog post detailing how Auth0 wasted two weeks of development due to user duplication before deciding to migrate.
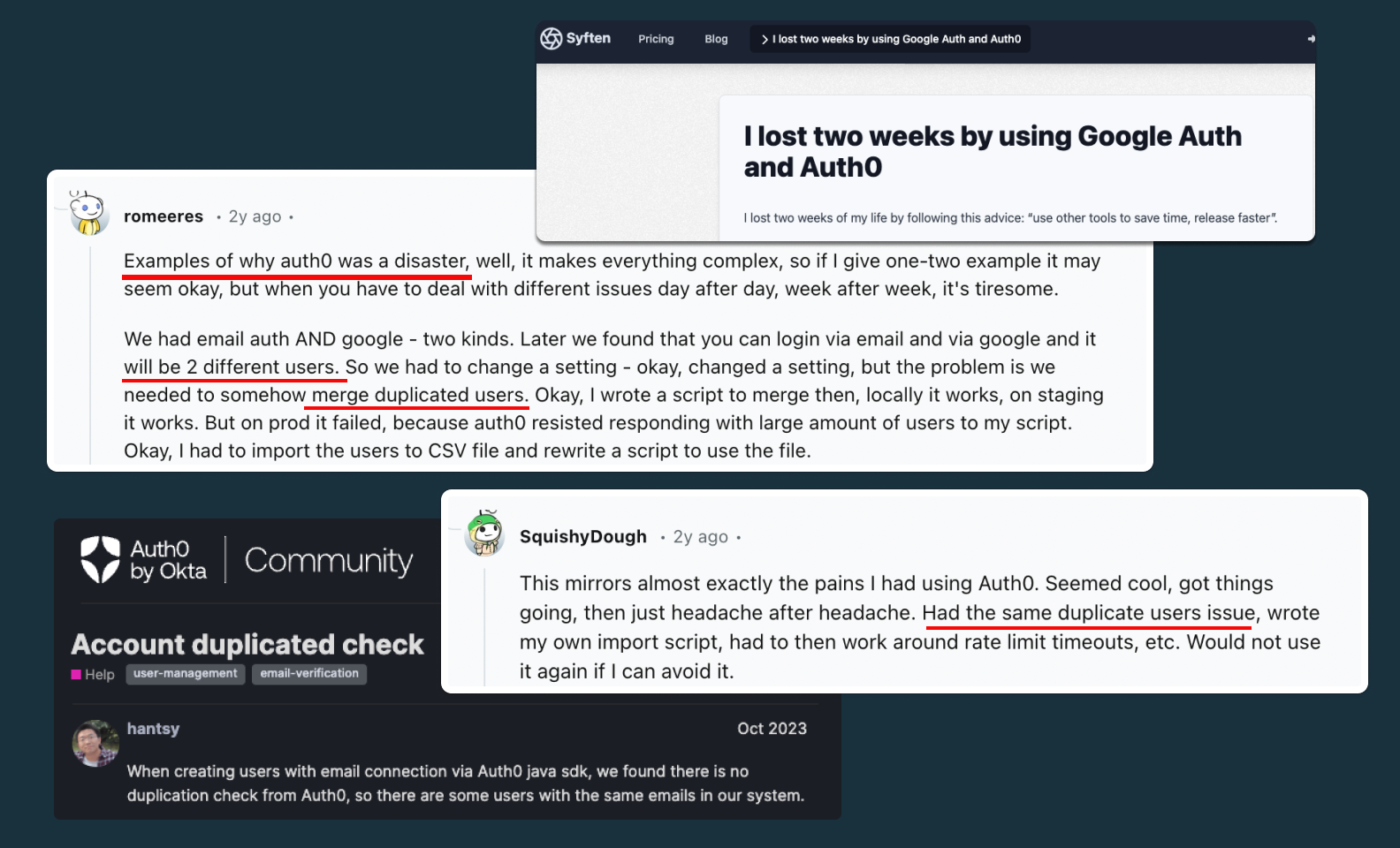
With Stytch, user records are automatically deduplicated if they share an email address. If a user signs up with an email and password, and then later logs in through Google OAuth, we securely verify their identity and link the two accounts on your behalf. We ensure one unified account for every user, regardless of the authentication method they use at any time.
Searching for an Auth0 alternative
When developers feel compelled to publicly voice their frustrations, it’s usually a sign of widespread, prolonged issues with the tool they’re using. Posting on forums, blogs, and social media is an effective outlet to ensure feedback is taken seriously. But Auth0’s continued harsh pricing, unresponsive customer support, and restrictive developer experience has left developers looking for alternatives for authentication.
At Stytch, we’ve listened to these frustrations and built our platform to address them directly. Transparent pricing, flexible embedded authentication, and dedicated developer support are core to what we offer. Engineering teams at companies like Orb, Clearbit, and Mintlify, are picking Stytch over Auth0, so they can deliver a smoother auth experience for their developers and users.
If you’re ready to leave the headaches of Auth0 behind, we’re here to help every step of the way. Schedule a call with an auth expert or join our developer Slack community to see how Stytch can transform authentication for your team.
Build with Stytch
The most powerful alternative to Auth0
Citations
[1] https://www.reddit.com/r/nextjs/comments/1dfme38/another_auth_thread_running_away_from_auth0_but/
[2] https://medium.com/@michael_93843/draft-wip-ff4366a63658
[3] https://community.auth0.com/t/why-i-wont-use-auth0/48879
[4] https://www.g2.com/products/auth0-by-okta/reviews/auth0-by-okta-review-8975677
[5] https://twitter.com/theo/status/1652220166460276737
[6] https://www.reddit.com/r/webdev/comments/18d6hcd/auth0_increases_price_by_300/
[7] https://news.ycombinator.com/item?id=32320571
[8] https://x.com/AmitTaylor/status/1732530584524615995
[9] https://www.g2.com/products/auth0-by-okta/reviews/auth0-by-okta-review-8975677
[10] https://www.reddit.com/r/webdev/comments/wdqqq0/comment/iijwv45/
[11] https://community.auth0.com/t/why-is-auth0-support-so-bad/46861
[12] https://community.auth0.com/t/your-support-is-awful-non-existent/6363
[13] https://community.auth0.com/t/terrible-auth0-support/113015
[14] https://www.g2.com/products/auth0-by-okta/reviews/auth0-by-okta-review-9795599
[15] https://www.g2.com/products/auth0-by-okta/reviews/auth0-by-okta-review-5438992
[16] https://www.reddit.com/r/okta/comments/1cuso7d/why_has_auth0s_customer_support_gotten_so_bad/
[18] https://blog.publiccomps.com/adding-stytch-to-our-login/
[20] https://community.auth0.com/t/organizations-feature-missing-lots-of-functionalities/77504
[21] https://www.reddit.com/r/nextjs/comments/1eifqs8/implement_auth0_with_nextjs_14_without_universal/
[23] https://www.reddit.com/r/reactjs/comments/12du21l/comment/k54a4vv/
[24] https://syften.com/blog/how_not_to_do_auth/
[25] https://www.reddit.com/r/reactjs/comments/12du21l/comment/jf8g4an/
[26] https://www.reddit.com/r/reactjs/comments/12du21l/comment/k5whr9s/
[27] https://community.auth0.com/t/account-duplicated-check/118260
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.