Back to blog
One-Time Password (OTP) bots: what they are and how to stop them
Auth & identity
Nov 8, 2023
Author: Alex Lawrence
OTP bots are a relatively new and sophisticated threat in the increasingly wide world of Multi-Factor-Authentication (MFA) scams. In short, they’re automated software – or bots – that bypass two-factor authentication, causing a security nightmare for users and online services.
As they challenge many conventional security measures, understanding and neutralizing OTP bots has become a priority for many organizations.
But before we dive into prevention strategies, let’s first understand the anatomy of two-factor and multi-factor authentication to see how these bad actors work their dark and deceptive magic.
The lay of the auth land: OTPs and 2FA
What are One-Time Passwords (OTPs)?
One-Time Passwords (OTPs) are unique, short-lived passcodes sent to a person’s phone number to be used as an additional layer of security for online transactions or logins. Typically sent to a user’s registered phone number or email, an OTP must be entered within a specified time period to confirm the user’s identity.
Unlike traditional static passwords, OTPs are much harder to compromise because they are dynamic and expire after a single use or short duration, making them a popular choice for two-factor and multi-factor authentication processes.
Understanding Two-Factor Authentication
Two-factor authentication (2FA) enhances security by requiring two separate verification methods. Usually, after entering a password, users receive a one-time password (OTP) to their phone number via SMS, providing a second layer of security. However, OTP bots have emerged as a tool for intercepting these crucial OTP codes, creating a pressing security issue.
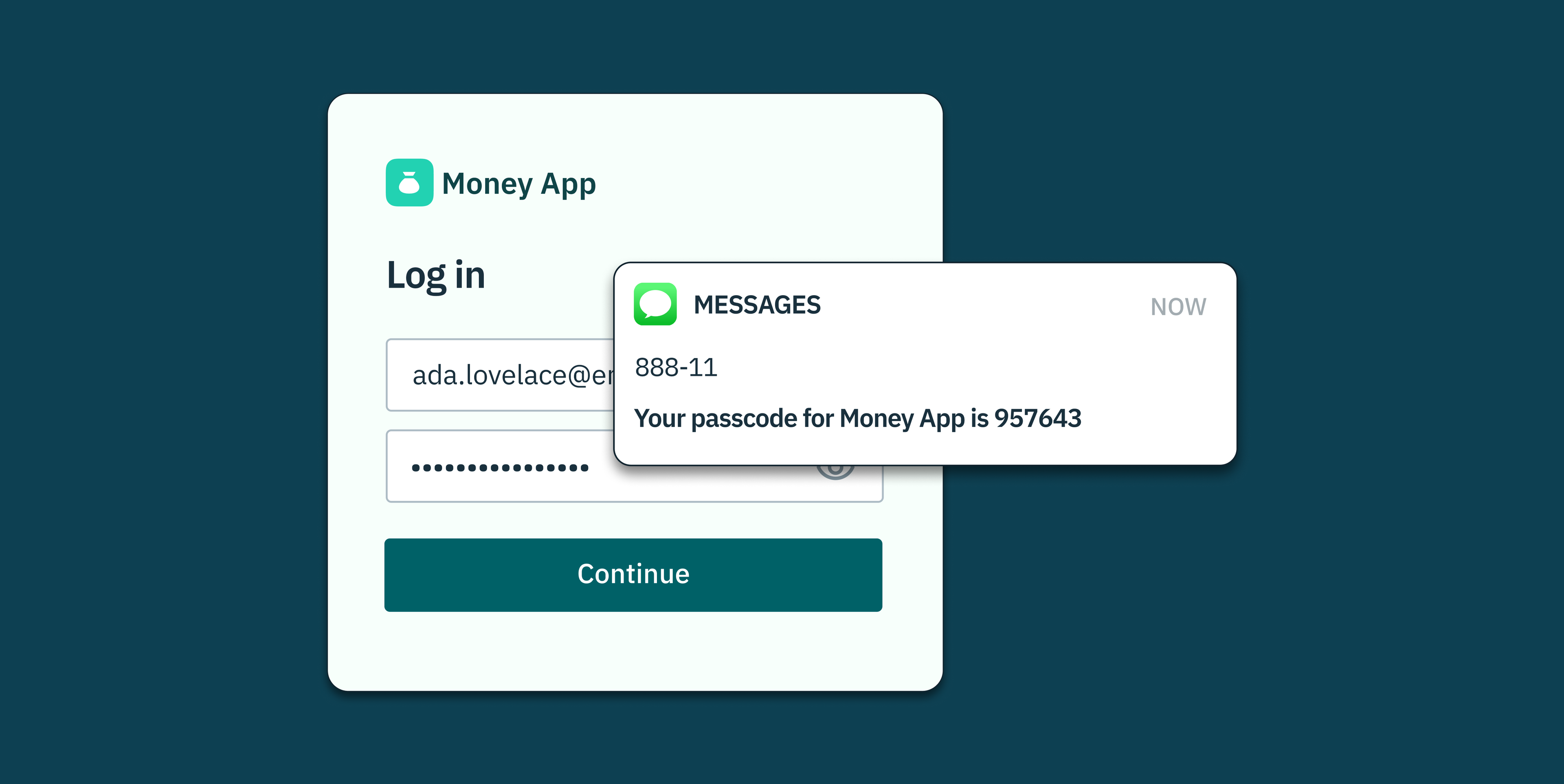
The process of 2FA involves a combination of two different factors: something you know (like a password), something you have (like your phone), or something you are (like your fingerprint). This means that even if an attacker knows your password, they’ll still need the second factor—usually a temporary verification code sent to your mobile device phone number —to access your account.
With OTP bots now being able to intercept these codes, 2FA’s effectiveness is somewhat compromised, pushing for the development of more advanced and secure authentication methods.
What are OTP Bots?
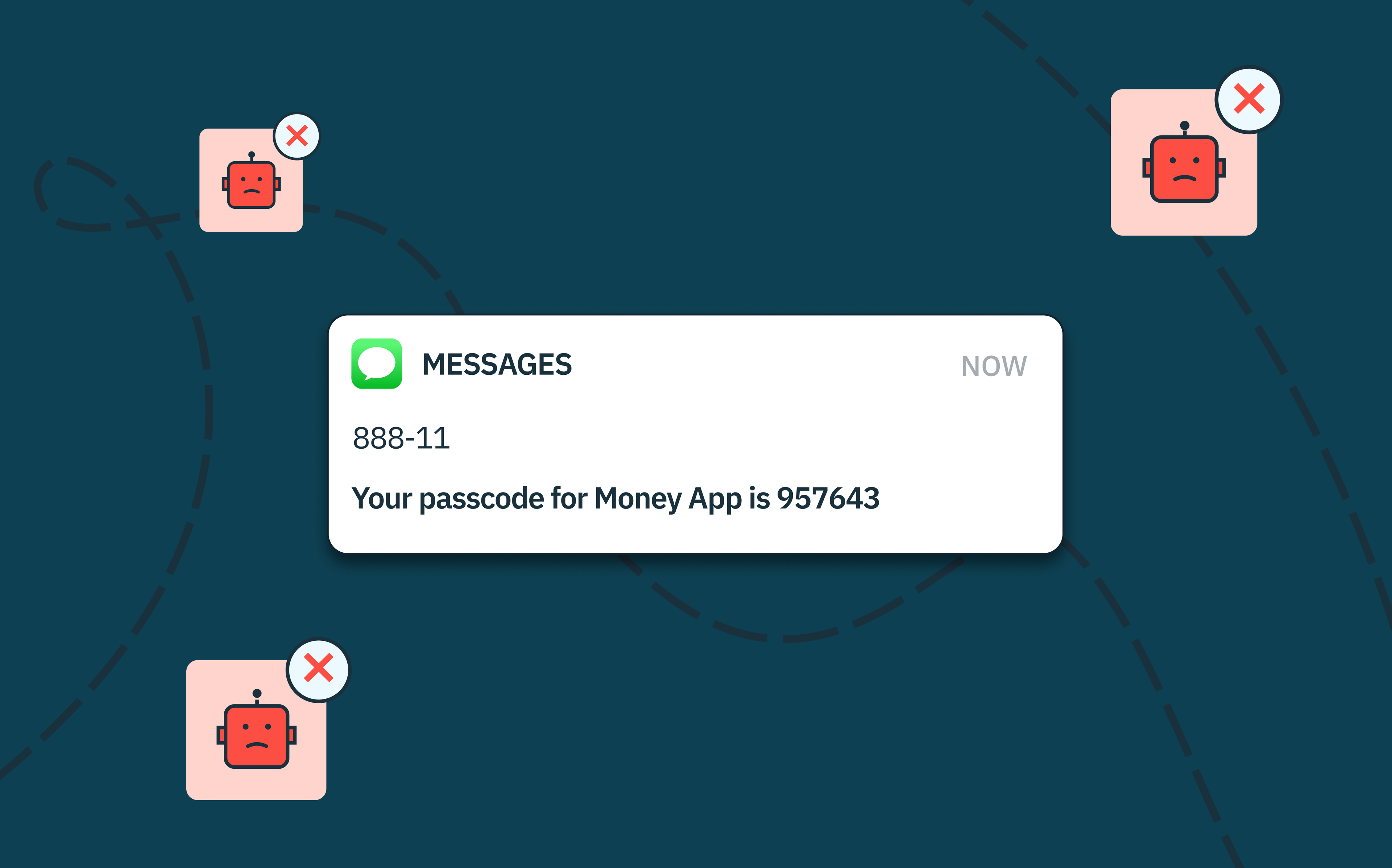
OTP bots are automated software programs that are designed to bypass two-factor authentication (2FA) systems. OTP bots are typically used for financial gain, such as accessing and draining bank accounts or making fraudulent transactions.
As more and more online services have implemented 2FA as an extra layer of security, OTP bots have become a more significant threat with their ability to bypass traditional authentication methods, making it easier for hackers to gain access to sensitive information using a victim’s phone number and other methods. The rise of OTP bots can also be attributed to the increasing availability and affordability of automated software tools.
Understanding OTP bot attacks and their impact
While OTP bots are not essential for OTP scams to work, they can massively scale and improve scam success rates through automation and an extra layer of credibility. There are two common scam types where OTP bots can make a massive impact:
Phishing
In a phishing attack, the potential victim usually receives a text message or an email claiming that something is wrong with their bank account with a plausible looking URL / link to click on. The scam usually goes down as follows:
- The victim clicks the link, taking them to a fraudulent site mimicking the bank’s login page, and enters their credentials which the attacker then uses to access the actual bank site.
- At this stage, direct bank account access is blocked due to the unfamiliar IP address of the attacker, so a Two-Factor Authentication (2FA) OTP challenge is initiated.
- The scammer’s site prompts the victim to select a 2FA method, forwarding the choice to the bank.
- The bank sends an OTP to the victim, who enters it on the phishing site. The attacker uses the OTP to gain full access to the bank account.
- To avoid suspicion, the scammer may allow transparent access to the bank or display a fake error message.
- The scammer can then conduct fraudulent transactions or collect financial information from the victim.
Malware
As mentioned, OTP bots are automated software which we’ll categorize as malware given the malicious nature of their design. In a malware attack, the attacker will trick the victim into installing the OTP bot (malware) on their device. This is often accomplished through exploiting password reset flows for sites that use only OTP pin validation as a challenge to resetting the password. Once the OTP bot (malware) is on the victim’s device, it can monitor the device’s activities as follows:
- OTPs for authentication, like bank logins, are sent to the user’s phone.
- Malware on the user’s device detects and secretly forwards the OTP to the attacker.
- Advanced malware automates the process: initiating login, intercepting OTP, and completing authentication.
- Attackers gain unauthorized access to perform malicious actions (funds transfer, data theft).
- The malware may erase the OTP message to avoid detection by the user.
- Additional malware or backdoors may be installed for sustained access.
By automating the OTP interception process, these bots can conduct widespread attacks, compromising numerous accounts swiftly and often going undetected until the damage unfolds.
Let’s dig a bit deeper into why they’ve been so successful.
The problem with 2FA
One of the main reasons why OTP bot attacks have become so prevalent is due to the popularity of 2FA as an added security measure. With the increasing popularity, new methods of circumventing this popular authentication method have sprung up. 2FA is now a lucrative target for cybercriminals looking for ways to exploit vulnerabilities and steal sensitive information.
Once attackers obtain an OTP, they can bypass the 2FA, leading to account takeover. With this unauthorized access, scammers can engage in malicious activities, including stealing financial resources, personal data, or using the account for other fraudulent schemes. This poses a significant risk to individuals and can also result in substantial financial losses for organizations and institutions.
Want to stop fraud? Get Device Fingerprinting from Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
LLMs and Modern Social Engineering
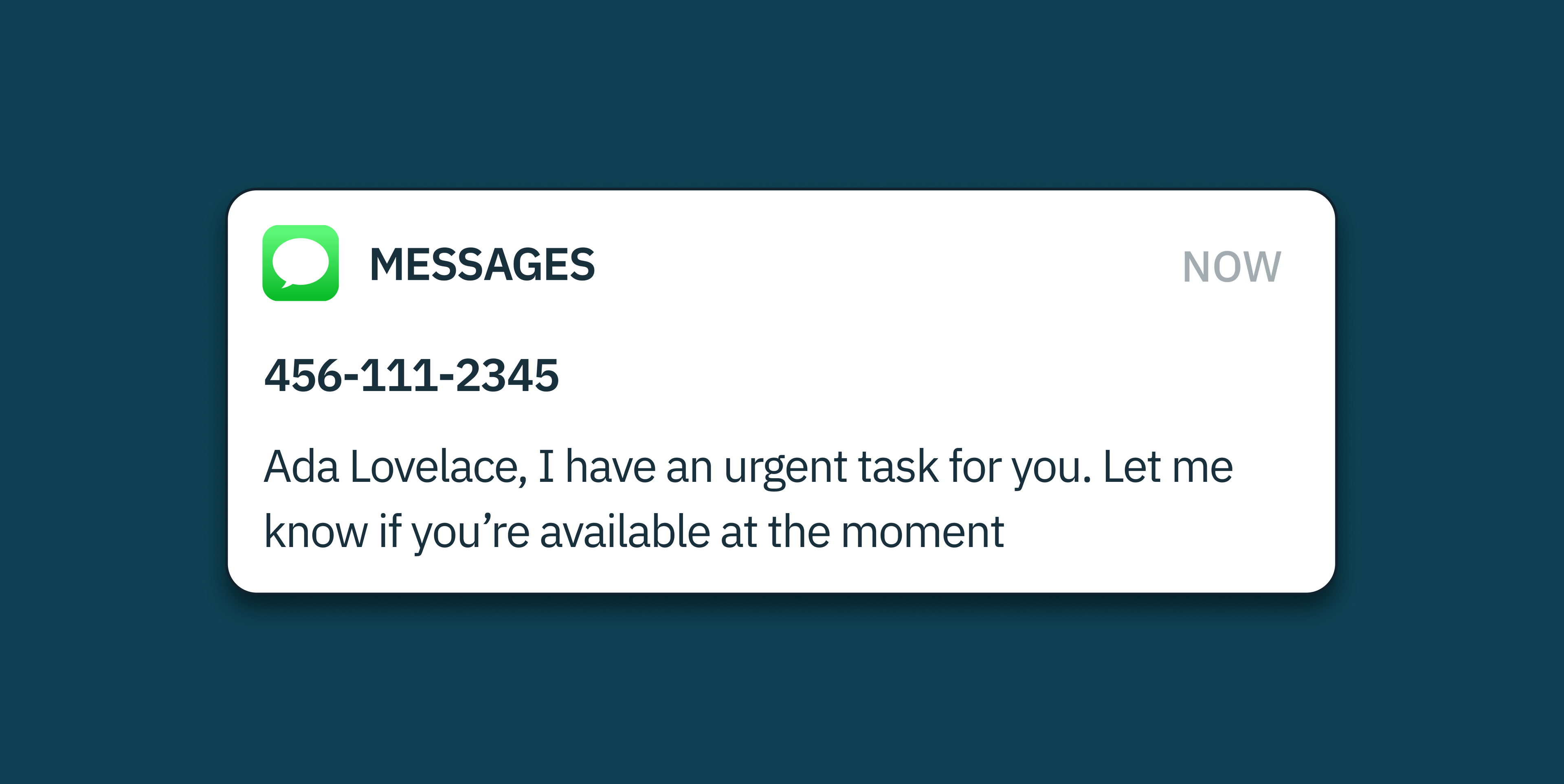
With modern generative AI-platforms such as ChatGPT 4, automated responses can feel so human it often feels like there’s a real person behind the ‘curtain.’ Modern social engineering seeks to exploit this incredibly promising – and daunting – technological advancement in the world of fraud.
In traditional social engineering, attackers use deceptive messages, e.g. posing as a company’s CEO and requesting urgent information, or pretending to be a reputable service requesting a verification code, to trick victims into a scam. By ‘engineering’ their responses in their favor, unsuspecting victims believe they’re securing their accounts and will provide the OTP or verification code, inadvertently granting attackers access to their information.
Scammers are increasingly experimenting with advanced Large Language Models (LLMs) – the machine learning powering generative AI – to create sophisticated automated systems capable of executing social engineering attacks. These fraud bots are being designed to mimic human interaction more compellingly than ever. LLMs build on ‘traditional’ fraud techniques and can vastly expand the creativity and adaptability of fraudsters.
LLM-powered bots can engage in conversations in multiple languages, and could even be programmed to perform Open Source Intelligence (OSINT) to gather publicly available data about their targets. This would enable them to craft highly personalized and convincing messages that take social engineering to the next level of believability.
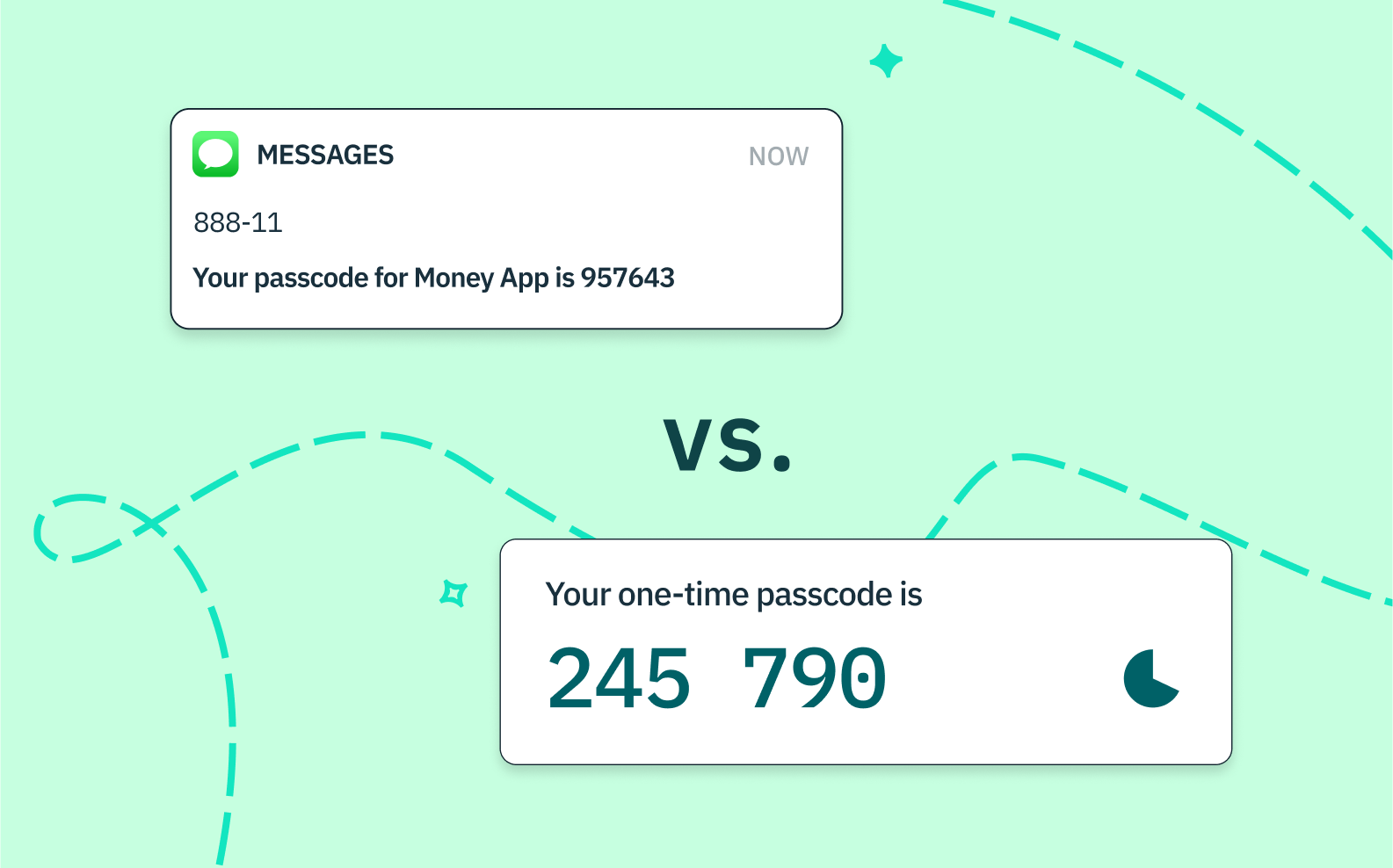
The Flaws of SMS-Based OTPs
Despite their encryption, SMS text messages can be intercepted either by technical means (such as OTP bots) or by deceiving telecom service representatives, exploiting the weakest security link: human error.
Moreover, attackers can hijack a victim’s SIM card by using social engineering techniques to impersonate the user and obtain a new SIM with the same number (a rather nefarious technique called SIM-swapping). They then receive all incoming SMS messages, including OTPs, essentially bypassing 2FA measures to compromise victim accounts.
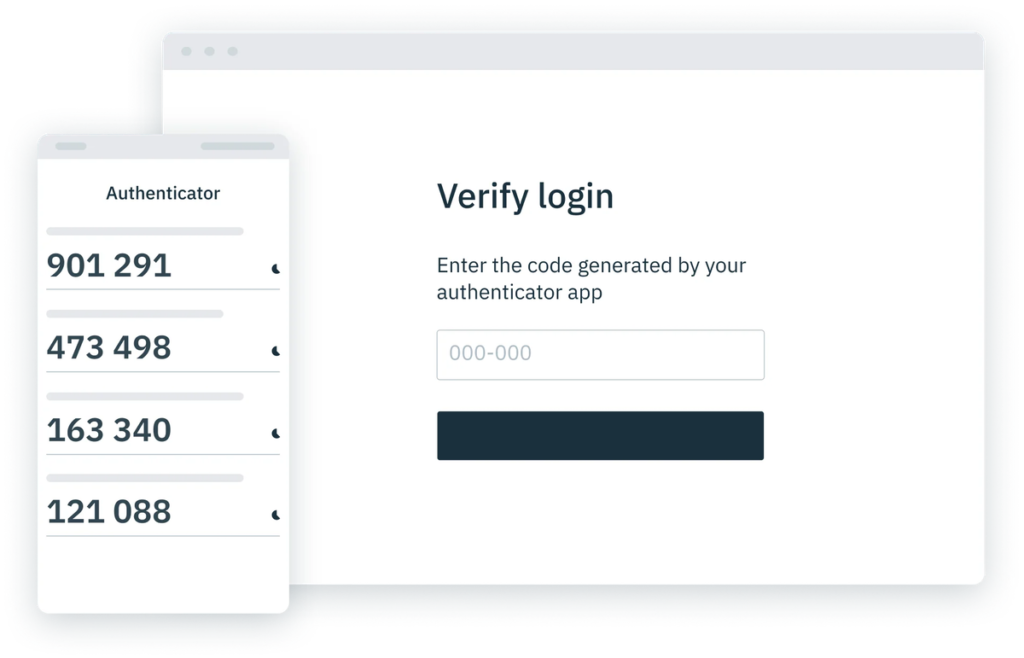
To mitigate vulnerabilities associated with SMS-based OTPs, organizations are increasingly turning towards app-based OTP solutions. Instead of receiving one-time codes through text messages, users generate them within a designated mobile application or hardware token.
The ‘SMS Buster’
Some attackers have broadened their market to offer OTP bot services to other would-be fraudsters, like the infamous ‘SMS Buster,’ for a subscription fee. These OTP bot services allow even low-skilled individuals to launch attacks, making them even more prevalent.
‘SMS Busters’ can read OTPs from text messages, parsing them for OTPs and automatically inputting them into the targeted application. These bots can also bypass CAPTCHA challenges by using Optical Character Recognition (OCR) technology.
The impact on organizations and networks
Financial institutions are prime targets for OTP bots. Attackers exploit these bots to perform unauthorized transactions, transferring funds without consent. The automation and scale of these attacks amplify the risks and potential losses for both banks and customers, who may be unable to access their funds or suffer losses – not to mention face reputational damage and regulatory sanctions.
Services like Google, PayPal, and Instagram are common victims of OTP bot assaults. Users often link financial details with these platforms, making them attractive targets. The bots’ ability to bypass security protocols creates vulnerabilities around user funds and sensitive data. It’s no wonder why Elon Musk’s somewhat messy rollout of X, the app formerly known as Twitter, is facing such strong fintech industry pushback for throwing itself into the payments game.
Prevention strategies
To combat OTP bots, businesses and online services must implement strong security measures that go beyond traditional 2FA methods. These include biometric authentication methods, such as fingerprint or facial recognition, which are more difficult for bots to bypass. Additionally, businesses and services should regularly review and update their security protocols to stay ahead of evolving bot tactics.
Individual users can also take steps to protect themselves, including regularly changing passwords and using unique and complex login credentials for each online account.
Stronger 2FA factors
Adding stronger security layers can make it harder for OTP bots to gain access to user accounts. Incorporating methods like biometric verification or cross-platform hardware tokens fortify and diversify checkpoints leading to account access. This makes it difficult for bots to bypass security protocols and gain unauthorized access.
Behavioral biometrics
Behavioral biometrics, also known as passive biometrics, is an emerging authentication method that analyzes user behavior patterns to identify and verify individuals. These include keystroke dynamics, mouse movements, swipe patterns, and other unique behaviors that are difficult for bots to replicate. By continuously monitoring these behavioral patterns, online services can detect suspicious activity and block OTP bot attacks before they compromise sensitive information.
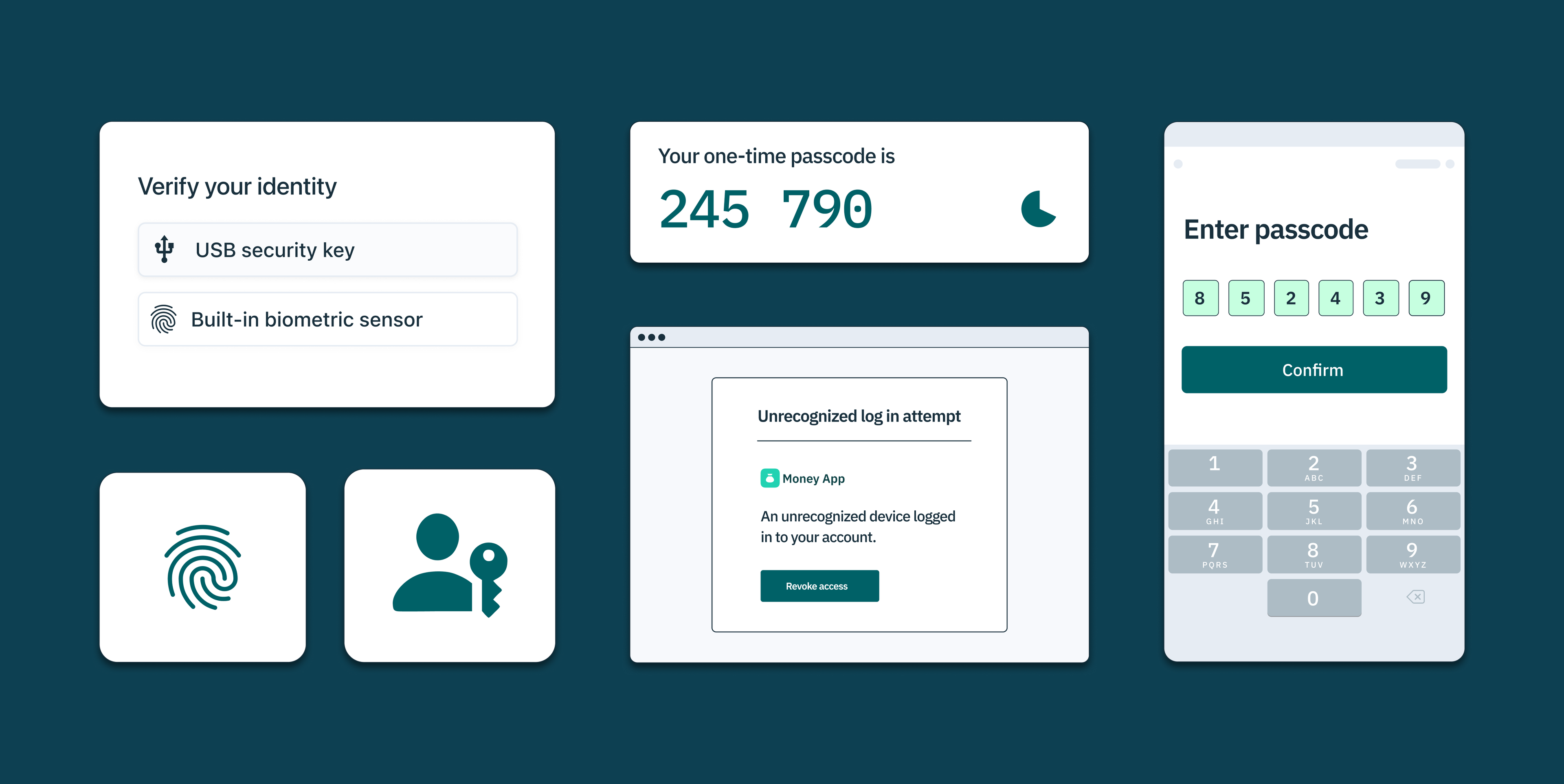
Web authentication and hardware tokens
Web authentication works by using public key cryptography and secure hardware tokens or biometrics stored on the user’s device, effectively preventing OTP bot attacks. When a user registers an account, the server creates a public-private key pair, with the private key, or hardware token, securely stored on the user’s device, and the public key stored on the server.
During login, the server sends a challenge to the user’s device, which the device signs with the private key. The server can then verify the signature with the stored public key, ensuring that the user, and not a bot, is attempting to access the account. This procedure significantly raises the bar for attackers, as they must now gain access to the user’s physical device or biometric data to bypass authentication – no easy feat.
Tools that can help
In light of the availability of newer authentication methods such as TOTPs (authenticator apps) and passkeys, now is the perfect time to steer users away from less secure methods like passwords and SMS OTP as OTP bots continue to rise.
Stytch can help developers and organizations prepare their defenses using both physical and API-powered device security measures, such as our WebAuthn solutions.
Device fingerprinting identifies unique characteristics of a user’s device, such as the operating system, browser version, screen resolution, and even unique identifiers like IP address, helping safeguard against OTP bot attacks and other potential breaches.
Step-up authentication allows for more rigorous authentication processes like additional verification steps if a user logs in from a new location or attempts to conduct a high-risk transaction. By leveraging real-time risk assessment, step-up authentication ensures that stronger security measures kick in only when they’re most needed – without adding friction or compromising on user experience.
Stytch also offers ‘unphishable’ multi-factor authentication (MFA) that require users to authenticate their identities using multiple factors, including something they know (like a password), something they have (like a hardware token or a registered device), and something they are (like a fingerprint or other biometric data) — making it challenging for cybercriminals to gain access.
To learn more about how these or other solutions work, reach out to an auth expert to start a conversation, or get started on our platform for free today.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.