Back to blog
Stytch vs Auth0: Bot detection
Auth & identity
Apr 3, 2025
Author: Stytch Team
Several auth providers like Auth0 provide a generic bot detection feature that aims to detect automated traffic or activity. But assuming that fraud is exclusively perpetrated by bots ignores the more complex reality where both humans and bots are capable of executing sophisticated schemes.
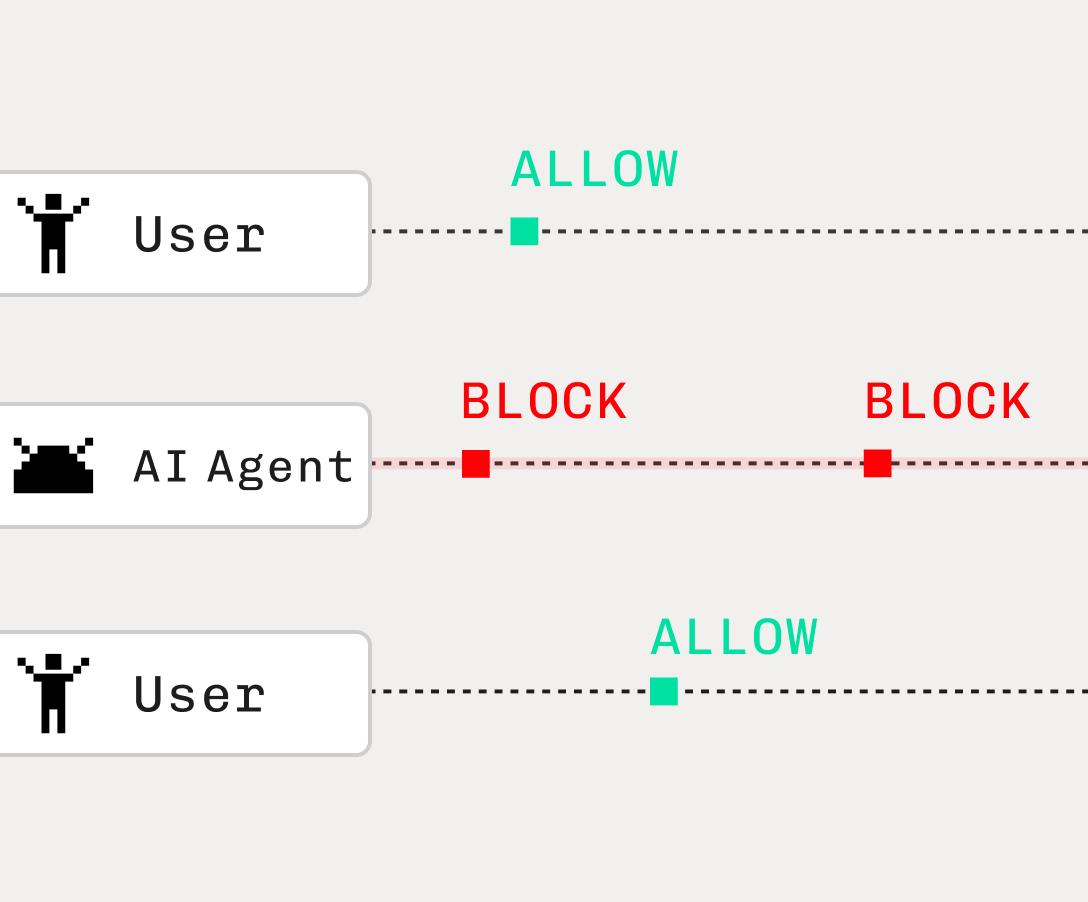
Traditional bot detection focuses on identifying and blocking automated traffic, which might work for stopping spam bots, credential stuffing scripts, or DDoS attacks. However, modern fraud prevention needs to go further than a simple yes/no on automation. Your application should also be capable of:
- Recognizing AI agent use and abuse.
- Persistently identifying a fraudster who switches devices or uses spoofing tactics.
- Distinguishing between legitimate users and malicious actors who aren’t bots.
- Preventing fraud like fake signups, account takeovers, payment fraud, and more.
Bot detection is no longer about blocking “just bots.” It’s about understanding behavioral context, usage patterns, and low-level signals from devices and networks. And that requires much more than what traditional bot detection solutions can deliver.
In this article, we’ll explore how Stytch’s Fraud & Risk Prevention solution—specifically our advanced Device Fingerprinting feature—goes far beyond basic offerings like Auth0 bot detection.
Auth0 bot detection: Limitations and challenges
Auth0 offers a bot detection feature, but its approach has significant limitations when it comes to comprehensive fraud prevention. This means it can flag obvious automated attacks like high-volume IPs, serve CAPTCHAs, and recognize simple automation patterns. But Auth0’s approach lacks the persistence, depth, and flexibility needed to detect more sophisticated fraud schemes.
Here are the main limitations when working with Auth0 bot detection.
A toggle, not a toolkit
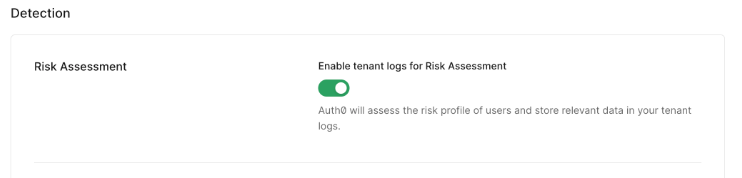
One of the most critical shortcomings of Auth0’s bot detection feature is how rigid and opaque it is. At its core, it’s just a simple toggle—an on/off switch in the dashboard. You flip it on, and Auth0 begins applying generic detection logic behind the scenes.
The only additional control is an opaque slider of the level of bot detection.
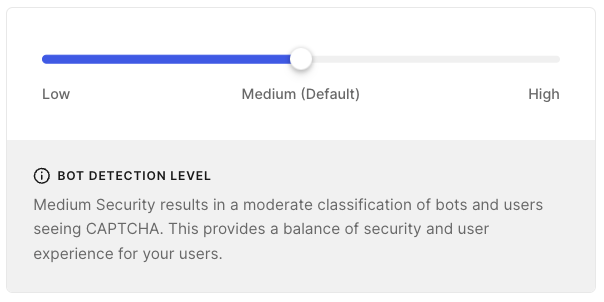
This kind of one-size-fits-all logic might catch a noisy bot, but it’s not equipped for real-world threats and complexity. By contrast, platforms like Stytch provide a fully configurable API, customizable Security Rules Engine, and rich device telemetry so your team can design risk-based authentication flows that respond in real time to evolving threats.
Session-based detection
Auth0 bot detection relies on ephemeral signals like IP addresses, user agents, and browser headers to evaluate traffic. These attributes reset at the end of each session and can be easily spoofed. Without persistent identifiers, Auth0 can’t track returning fraudsters or connect fraudulent behavior across sessions, devices, or networks—leaving serious blind spots in your security posture.
Basic rate limiting
Auth0’s rate limiting is largely tied to IP addresses. It can throttle requests from a specific IP, but attackers can easily rotate IPs to bypass this check. Worse, this blunt approach can backfire—blocking legitimate users on shared IPs, such as those behind corporate networks or mobile carriers.
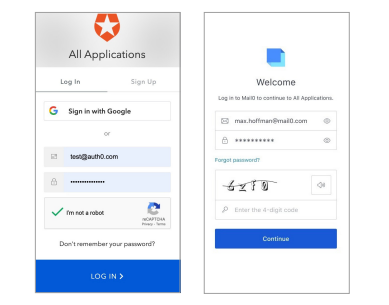
Outdated CAPTCHA challenges
When Auth0 bot detection can’t confidently assess risk, it defaults to CAPTCHA challenges. In fact, CAPTCHAs form the backbone of Auth0’s bot mitigation strategy. But CAPTCHA-solving farms and automated solvers make this defense easy to bypass, while simultaneously adding friction and frustration for legitimate users.
Bots only, no human fraud detection
Auth0 bot detection models are designed to catch non-human behavior. If a fraudster mimics legitimate user actions—or if a real user simply behaves in an unusual way—Auth0 struggles to tell the difference. This binary lens means manual account takeovers, human-in-the-loop attacks, and social engineering tactics often go undetected.
Limited to Universal Login & no customizations
Auth0’s bot detection features are only fully supported in its Universal Login product. If your app uses custom authentication flows or embeds login directly into the UI, you will only have limited support unless you migrate to Universal Login—which comes with major drawbacks. That’s a significant integration constraint for modern applications seeking customizations and flexibility.
If you're serious about defending against today’s fraud landscape, you need more than point-in-time detection and CAPTCHAs. You need persistent identifiers, telemetry, and device-level intelligence—the kind that Auth0 bot detection doesn't provide.
Stytch Device Fingerprinting: A persistent, intelligent defense
Stytch takes a fundamentally different approach to fraud prevention—one that goes far beyond session-based bot detection. Instead of relying on ephemeral signals like IPs or headers, Stytch uses advanced device fingerprinting to uniquely and reliably identify users across sessions, devices, and behaviors.
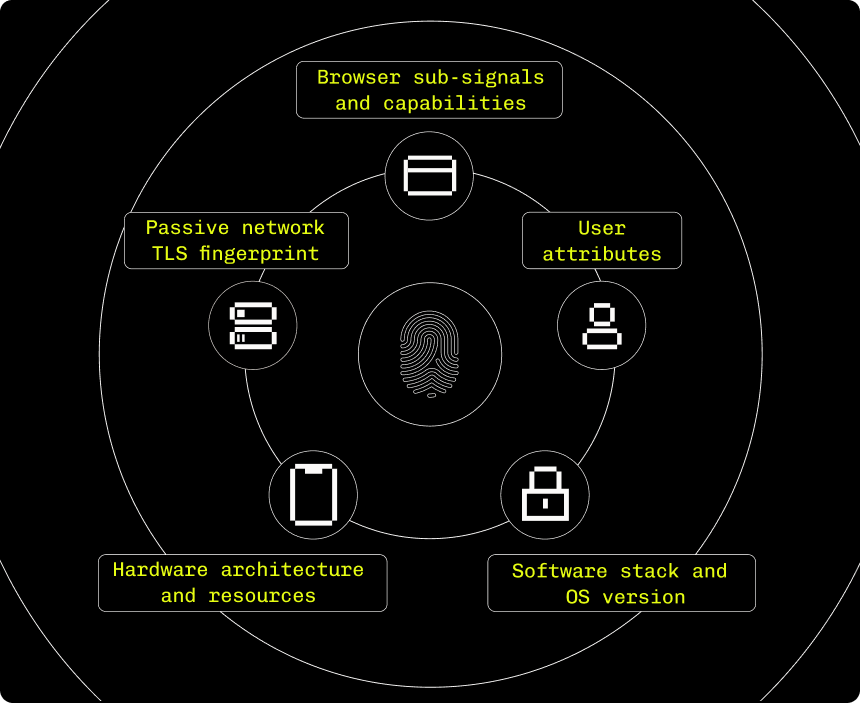
Here are the core reasons why our approach to bot detection enables companies across high-risk industries like B2B SaaS, fintech, and e-commerce to use Stytch Device Fingerprinting to uncover sophisticated fraud patterns.
Flexible dev tools and integration
Stytch provides an API and multiple SDKs (Node, Go, Python, Ruby, Swift, Kotlin, etc.) that make it simple to embed device fingerprinting into any application architecture. Whether you use Stytch for authentication or not, our Device Fingerprinting platform is modular by design. You can integrate it:
- As a standalone fraud prevention layer for any custom-built application
- As part of Stytch’s auth flows (e.g. login, signup, session refresh)
- With your existing security stack via our API and SDKs
Setup is fast. Just drop in the Stytch telemetry script or SDK, and start receiving telemetry-based verdicts in a matter of minutes.
Persistent identity, deep device intelligence
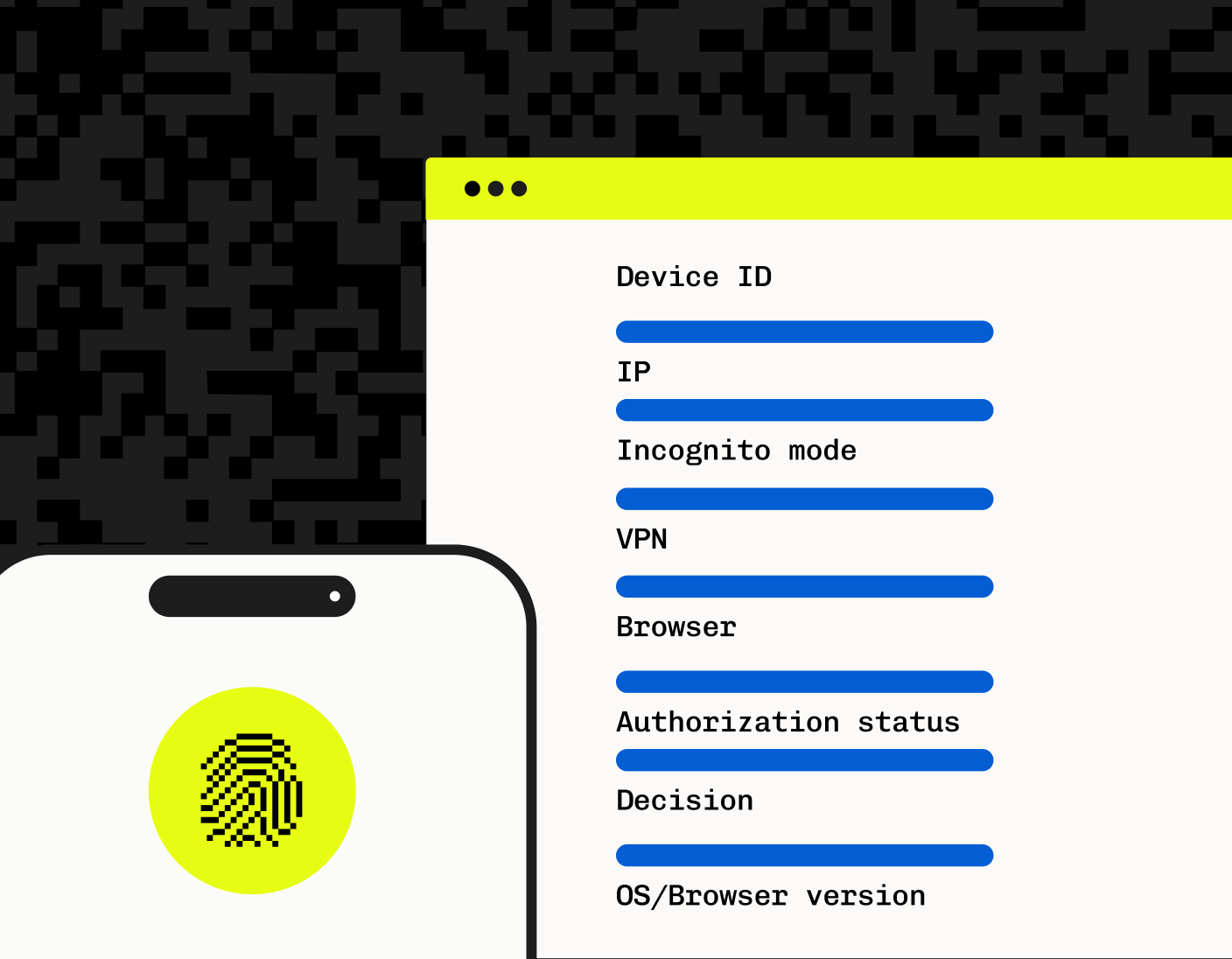
Stytch’s device fingerprinting engine creates stable, high-entropy identifiers for every user device, combining standard and proprietary telemetry across:
- Browser sub-signals and rendering behavior
- Passive TLS and network fingerprinting
- Hardware architecture and OS resources
- And more
The result is a unique and powerful set of fingerprint identifiers that’s persistent across sessions, and incredibly difficult to spoof—even with network switching, incognito mode, or user agent deception. These identifiers provide deep, context-aware device intelligence that gives you the power to make smarter, more targeted security decisions.
// For each device, Stytch will create a unique set of persistent fingerpint identifers to return in the API
...
"telemetry_id": "026ac93b-8cdf-4fcb-bfa6-36a31cfecac1",
"fingerprints": {
"browser_fingerprint": "browser-fingerprint-0b535a...",
"browser_id": "browser-id-99cff...",
"hardware_fingerprint": "hardware-fingerprint-4af7a0...",
"network_fingerprint": "network-fingerprint-b5060...",
"visitor_fingerprint": "visitor-fingerprint-6ecf57...",
"visitor_id": "visitor-6139c..."
},
"verdict": {
"action": "ALLOW",
"detected_device_type": "...",
"is_authentic_device": true,
"reasons": [...],
...
}
...For example, our visitor_fingerprint is a cookie-less way to uniquely identify users across sessions, which is perfect for enforcing paywalls, because it remains consistent even in incognito mode. On the other hand, our hardware_fingerprint can be used to identify the operating system and architecture of a device, which is useful for detecting proxy or location spoofing.
These, along with the other fingerprints we provide, can be found in the table below.
Definition | Use Case | |
|---|---|---|
Visitor ID | ||
Visitor ID | The cookie stored on a user’s device that uniquely identifies them. | Provides a consistent identifier for each user. |
Browser ID | ||
Browser ID | A combination of Visitor ID and Network Fingerprint to create a unique browser identifier. | Can be used to detect stolen sessions, since the Browser ID should only be tied to a single browser fingerprint. |
Visitor Fingerprint | ||
Visitor Fingerprint | A highly unique, cookie-less identifier based on a diverse set of signals. | Can be used to enforce paywalls or ban users in a cookie-less manner, since the visitor fingerprint remains consistent even in incognito mode. |
Browser Fingerprint | ||
Browser Fingerprint | A combination of signals that uniquely identifies a browser and its version on a specific device. | Useful in banning a specific browser version across multiple user accounts on the same machine. |
Hardware Fingerprint | ||
Hardware Fingerprint | A combination of signals identifying an operating system and architecture. | Detecting proxy or location spoofing since the Hardware fingerprint will be stable across different locations. |
Network Fingerprint | ||
Network Fingerprint | A combination of signals associated with a specific network. | Blocking known data centers or specific block of IP addresses. |
Fraud Prevention beyond bots
Because each fingerprint is persistent and highly unique, Stytch can recognize when a device reappears under different identities—not just bots. This makes Stytch uniquely capable of identifying:
- Phishing-based takeovers from unfamiliar devices
- Subscription fraud, referral gaming, and toll fraud
- Fake account generation from cloaked environments
- Bypass attempts via incognito, VPNs, or TOR nodes
Stytch stops fraud: bots and humans alike.
Actions and reasons
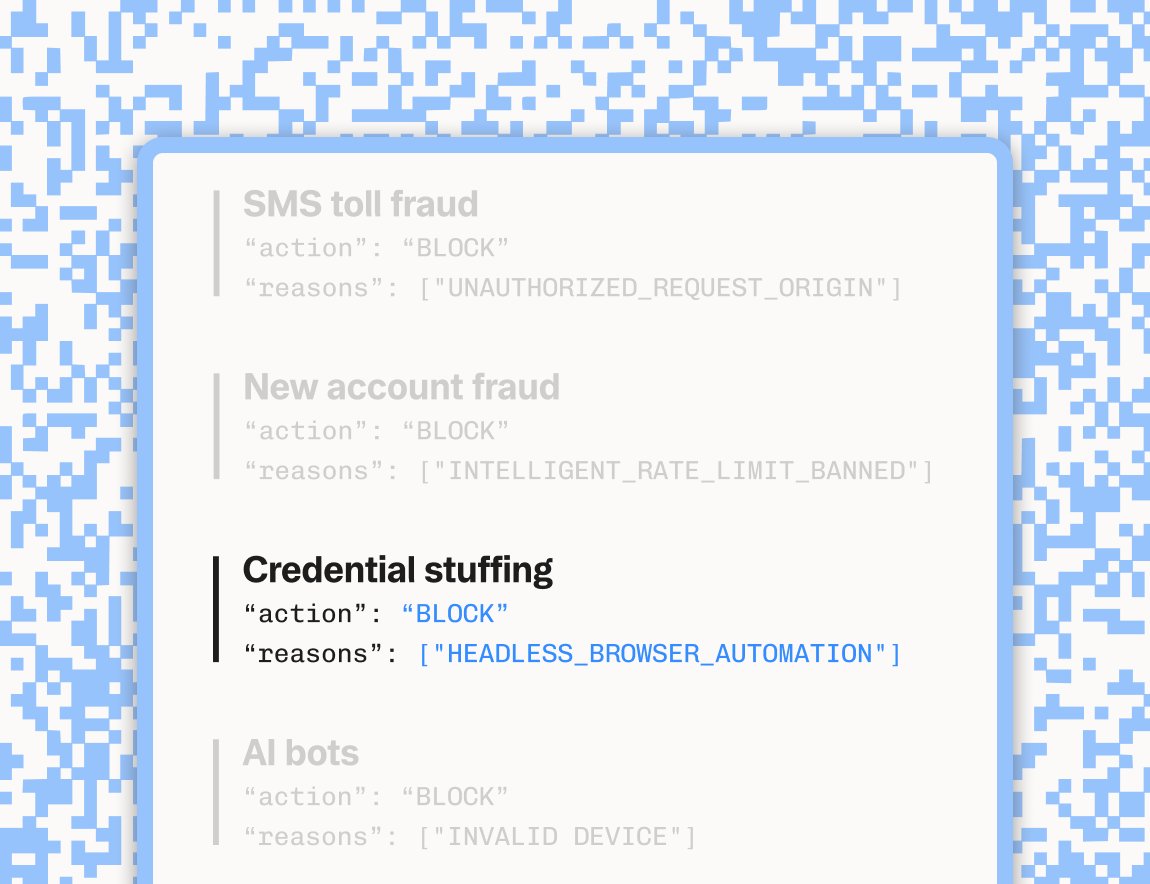
Stytch’s Device Fingerprinting doesn’t just identify devices—it provides a robust actions and reasons framework that enables you to respond intelligently in real time. For every fingerprinted request, Stytch returns:
- A clear verdict (
ALLOW,CHALLENGE, orBLOCK) - A set of reasons explaining why the decision was made (e.g., new device, fingerprint mismatch, abnormal velocity, known fraudulent pattern)
This structure empowers you to tailor your fraud response strategy with precision. You can:
- Trigger step-up authentication (like MFA) for suspicious but not confirmed threats
- Introduce friction (CAPTCHA, rate limiting, re-verification) based on context
- Block access outright when the fingerprint is known to be malicious or risky
- Maintain a seamless experience for trusted, low-risk devices
Security rules engine

Stytch also provides a Security Rules Engine that gives you full control over how you programmatically respond to certain fingerprints and identifiers. You can configure rules:
- Directly via the Stytch Dashboard
- Programmatically via API
- On a per-device, per-fingerprint basis
This gives you the control to trigger fraud prevention measures only where it’s needed.
Intelligent Rate Limiting
Instead of throttling broad IP ranges, Stytch uses granular, device-level rate limiting to pinpoint abuse. When our system detects anomalous velocity or behavior, it can:
- Challenge or block specific offending devices
- Return graduated verdicts (
RATE_LIMIT_WARNING,RATE_LIMIT_EXCEEDED,RATE_LIMIT_BANNED) - Avoid false positives that punish legitimate users on shared networks (e.g. corporate or mobile carriers)
Stytch's Intelligent Rate Limiting feature is dynamically powered by real-time telemetry and reinforced by our fingerprinting data.
A side-by-side comparison
Auth0 | Stytch | |
|---|---|---|
Bot detection | ||
Bot detection | ✅ Basic bot detection using IP, headers, and request patterns | ✅ Detects bots using telemetry and device signals |
Persistent identifiers | ||
Persistent identifiers | ❌ None – session-based only | ✅ Persistent identifiers across sessions/devices |
Human + bot fraud detection | ||
Human + bot fraud detection | ❌ Limited – focused on bots only | ✅ Detects bots, AI agents, and human-driven fraud attempts |
Device spoofing & cloaking detection | ||
Device spoofing & cloaking detection | ❌ Easily evaded by IP rotation or user agent spoofing | ✅ Identifies spoofed or cloaked devices via hardware + software signals |
Rate limiting | ||
Rate limiting | ⚠️ Basic IP-based throttling | ✅ Intelligent Rate Limiting (IntRL) across telemetry dimensions |
Browser or device fingerprinting | ||
Browser or device fingerprinting | ❌ Not supported out of the box | ✅ Multiple fingerprint types: Visitor, Hardware, Browser, Network, etc. |
Fraud visibility & control | ||
Fraud visibility & control | ❌ No telemetry or risk scoring surfaced | ✅ /lookup API exposes fingerprints + recommended actions and reasons |
Integration complexity | ||
Integration complexity | ⚠️ Requires Universal Login | ✅ API support, lightweight SDK + script integration |
Getting started with Stytch’s Device Fingerprinting
Our DFP product suite is compatible with all web and native mobile authentication experiences, whether it’s built with another provider, in-house, or Stytch. The best part? You don’t need to write any custom code or actions for any of Stytch’s device fingerprinting features to work, and the setup process can have you up and running in just a few minutes.
Once you install Stytch’s telemetry script by including the <script> tag in the <head> section of your page, you just need to call the GetTelemetryID function to get a unique identifier for each user.
<html>
<HEAD>
<script src="https://elements.stytch.com/telemetry.js"></script>
</HEAD>
<body>
<button id="login" onclick="login()">Click here to log in!</button>
<script>
function login() {
var publicToken = "public-token-test-1a582244-8834-424c-92ce-71b5f7bbcf02"; // public token from Stytch Dashboard
GetTelemetryID({
publicToken: publicToken
}).then((telemetry_id) => {
var request = new XMLHttpRequest();
request.open('POST', 'https://www.customer.com/login', true);
request.setRequestHeader('X-Telemetry-ID', telemetry_id);
request.send(null);
});
}
</script>
</body>
</html>The telemetry ID serves as the foundation for calling our Fingerprint Lookup API, which provides unique insights into device activity and suggests actions for handling further interactions with that device.
curl --request GET \
--url 'https://telemetry.stytch.com/v1/fingerprint/lookup?telemetry_id={TELEMETRY_ID}' \
-u 'PROJECT_ID:SECRET'
Ready to talk to an auth expert about Stytch’s Fraud & Risk Prevention product suite?
Feel free to schedule a chat with one of our experts.
Fraud & Risk Prevention
Beyond WAF and CAPTCHA: 99.99% bot detection, intelligent rate limiting, and reverse engineering protection.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.