Back to blog
TOTP vs SMS: Which one is better for two-factor authentication (2FA)?
Auth & identity
Feb 1, 2023
Author: Gedney Barclay
With the staggering number of data breaches in recent years - 45% of US companies alone suffered a breach in 2021 – it's become clear that traditional passwords alone are no longer a sufficient form of security for preventing account takeovers. Hackers have stolen over 555 million passwords since just 2017, which is why security professionals now view passwords as "pre-breached" when designing identity and access management policies.
Multi-factor authentication (MFA) is a crucial solution for this problem, but it can be difficult to determine which options are the most secure and user-friendly for a particular application. SMS 2FA (which uses one-time passcodes), for example, are less secure but more widely adopted by consumers, while phishing-resistant options like hardware keys or device-tied biometrics are more secure but less adopted.
In this post, we'll examine the two most popular MFA options today (SMS 2FA and TOTP 2FA) , their relative security levels, and strategies for increasing user adoption.
Pros and cons of SMS and TOTP 2FA
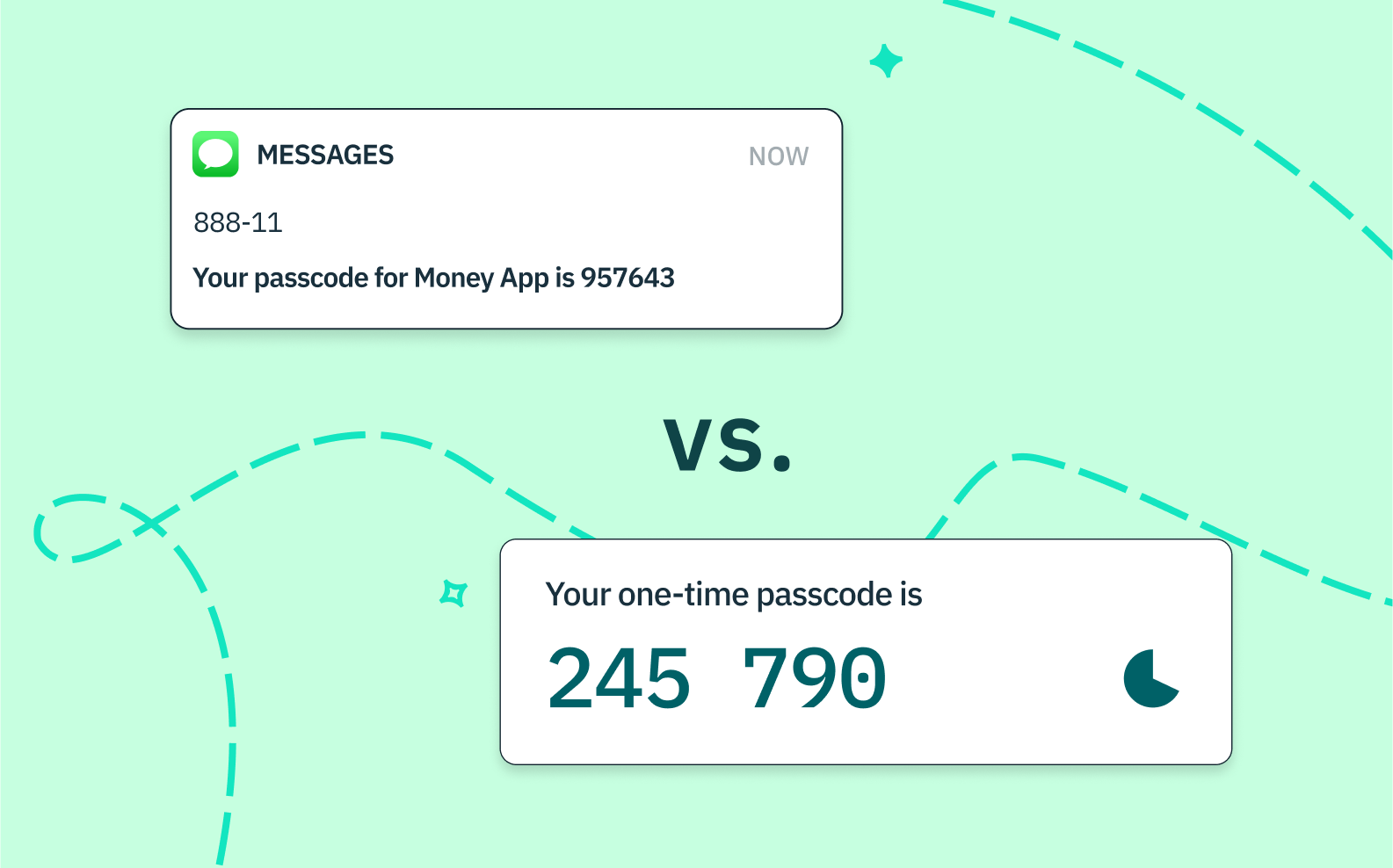
SMS-based 2FA is the most widely used type of 2FA. It works by sending a one-time code to your mobile phone via text message, which you then enter to access your account. This option is familiar and easy for users. It offers a particularly seamless experience on mobile due to the auto-fill capabilities on iOS and Android that allow a user to stay within the application experience when inputting the passcode.
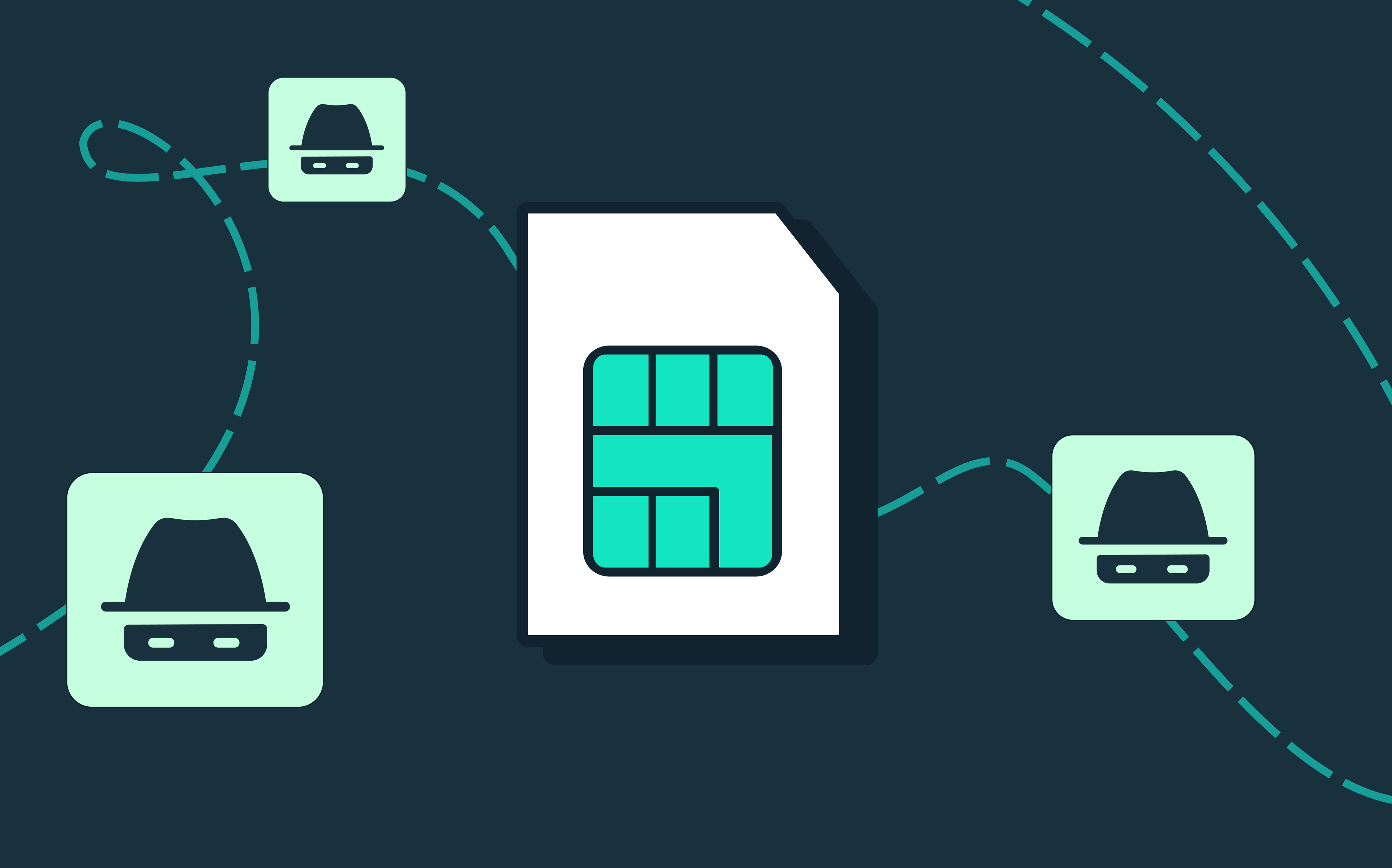
However, SMS 2FA is not considered as secure as TOTP-based 2FA. The major security shortcomings are phishing – where a user is deceived into sharing the passcode with an attacker – and SIM-swap attacks. A SIM-swap attack is a type of cyber attack in which a malicious actor convinces a mobile carrier to reassign a mobile number to a SIM card they control. Once they have control of the number, they can use it to reset the victim's password on any account that uses the phone number as a form of verification and gain access to sensitive information such as bank accounts, emails, and social media profiles. This type of attack is particularly concerning because it can bypass most two-factor authentication systems that rely on text messages. In addition to these security concerns, SMS 2FA also involves reliability risk as you’re dependent on mobile carriers (and a SMS provider’s uptime) for delivery of the authentication code. Provider downtime or poor cell coverage can both complicate reliability of this method.
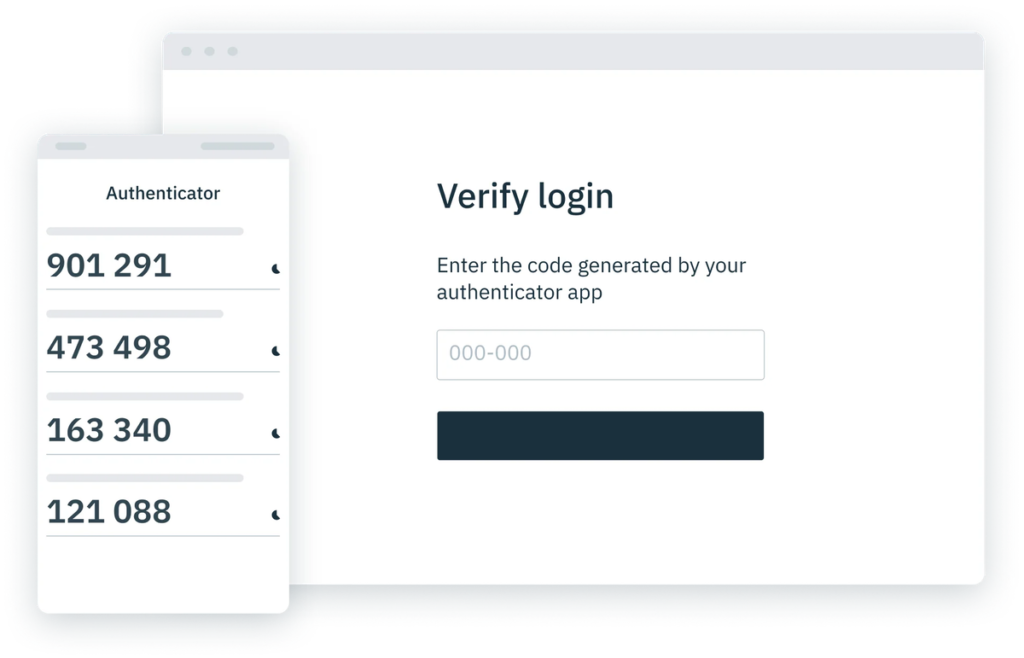
TOTP-based 2FA, on the other hand, uses an app on your smartphone to generate a one-time code that changes every 30 seconds. To access your account, you need to enter the current code displayed in the app. TOTP-based 2FA is considered to be more secure than SMS-based 2FA because it is less susceptible to intercepts and spoofing. Additionally, TOTP-based 2FA does not rely on a phone number, so it can be used with any device that has the app installed.
Want unphishable MFA for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
TOTP vs. SMS: Why Is TOTP more secure than SMS?
Both SMS 2FA as well as TOTP 2FA use unique passwords to secure accounts. With SMS 2FA, the server generates and sends the random code to the phone of the user. Those codes will expire after use. Pending codes remain in effect for the amount of time the application sets (often at least a couple minutes to allow ample time for the user, but the maximum is typically bound at 10 minutes to reduce the attack surface). If the code is intercepted through a SIM-swapping attack, this allows for attackers to break into users' accounts.
In contrast, TOTP token-generated codes generate every 15 to 20 sec and are only available in a device-tied application, which removes the SIM swap attack and reduces the potential time frame of attacks significantly. When the new TOTP code is generated, the previous code will be automatically invalidated. Both TOTP and SMS 2FA are susceptible to phishing attacks though, where a user is tricked into forwarding a code to an attacker.
With SMS, it’s only necessary for the user to manually enter the OTP into the browser. On mobile, the SMS 2FA workflow is considerably easier due to the OS auto-fill capabilities mentioned above.
How TOTP 2FA trumps SMS 2FA
Both SMS and TOTP add another factor to the authentication process to protect users against unauthorized brute-force attacks. SMS 2FA is, however, using static codes which expire once they are used or not reused within ten minutes of sending. A fraudster may already have access to the user’s phone number through a successful SIM swap, or they may be able to convince a user to forward their code (often by acting as a fake support agent) within the valid 10-minute window.
With TOTP, there’s no SIM swap risk because the TOTP application is tied to the user’s device (rather than being tied to their phone number). Additionally, the more ephemeral nature of the generated passcode with TOTP makes phishing attempts materially harder as an attacker has often 1/10th or 1/100th of the time available to them to convince a user to forward a valid code.
The two-factor authentication winner
In summary, SMS-based 2FA is easier to set up and use, but it is not as secure as TOTP-based 2FA. TOTP-based 2FA is more secure but requires an additional app to be installed on your smartphone. Ultimately, the choice between the two will depend on your individual needs and the level of security required for your specific use case.
To ground the differences in real-world data, let’s consider Coinbase’s public data on MFA method popularity and account takeover rates. While only 43% of customers’ funds are protected by SMS 2FA, 95% of successful account takeovers exploit weaker SMS-protected accounts. In contrast, advanced MFA like TOTP protects the majority of Coinbase’s customer funds but only accounts for 4.13% of successful account takeover attacks.
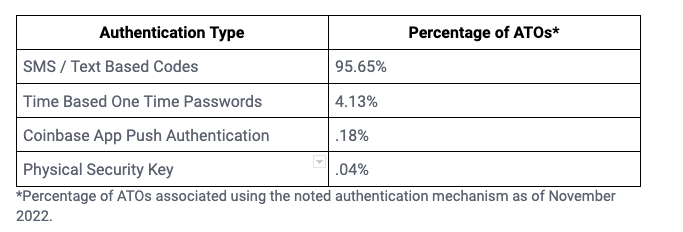
Table from Coinbase shows how often different authentication types are targets for account take overs (ATOs) proportional to each other.
When choosing a 2FA solution for your organization or personal accounts, make sure to evaluate the security and usability requirements and choose the one that best fits your needs. Ultimately, the best MFA strategy is the one in which your users actually enroll in MFA – one approach is to offer both options to users but encourage users to select the more secure method.
FAQs: Two-factor authentication (2FA)
What is the difference between OTP and TOTP?
One-Time Passcodes (OTPs) are unique and temporary codes sent to a user via SMS, WhatsApp, or email, and can be used as the primary auth factor or as a two-factor authentication to strengthen security. Time-Based One-Time Passwords (TOTPs) are unique time-based codes generated by authenticator apps, like Google Authenticator. The app is tied to a user’s device, preventing issues like SIM swapping, which can occur with SMS One-Time Passcodes. TOTPs are typically only used for 2FA.
Is SMS better than an authenticator app?
SMS-based passcodes are a commonly used solution but while it is easily accessible, it isn't the most reliable. Authentication apps are a second-level authentication solution that is safer, more reliable, and fast.
Is TOTP more secure than HOTP and SMS?
Hardware One Time Passscodes (HOTP), otherwise called physical security keys, are more secure than either SMS or TOTP 2FA. BUT, they historically have very low adoption because only extremely tech savvy individuals are willing to buy a hardware security key like a YubiKey.
What is the benefit of TOTP?
Time-based passwords available offline offer streamlined user protection for the second factor in the user experience. Similarly, TOTP can be referred to in applications or as a scalability token. The API for the authentication of applications is based on the TOTP standard.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.