Back to blog
What is a passkey?
Auth & identity
Feb 23, 2023
Author: Stytch Team

Of all the innovations in passwordless authentication over recent years, passkeys are arguably the most exciting. Passkeys expand on biometric technology by allowing biometric data to be backed up to (and accessed from) a user’s cloud account, enabling a level of interoperability that has never before been possible.
Given their portability and ease of use, passkeys are a top contender to dethrone the password as the dominant form of passwordless authentication, and we’re here for it. Still, they face several hurdles when it comes to implementation, especially since they require biometric-protected keys to be synced across different platforms and devices. For this reason, we expect that widespread passkey adoption will be slow to take hold — more like a dimmer light gradually turning on than the instant flip of a switch.
In this post, we run through the basics of passkeys: what they are, how they work, the barriers they face, and the steps we’re taking at Stytch to support every stage of their rollout.
What is a passkey?
Passkeys were developed by the Fast Identity Online (or FIDO) alliance, a group of cybersecurity experts dedicated to creating secure, frictionless authentication standards that eliminate the need for passwords. In fact, passkeys were originally introduced as “multi-device FIDO credentials” — “passkeys” is just a catchier term, and it has the added benefit of emphasizing how this new auth solution departs from and improves on the less-secure password.
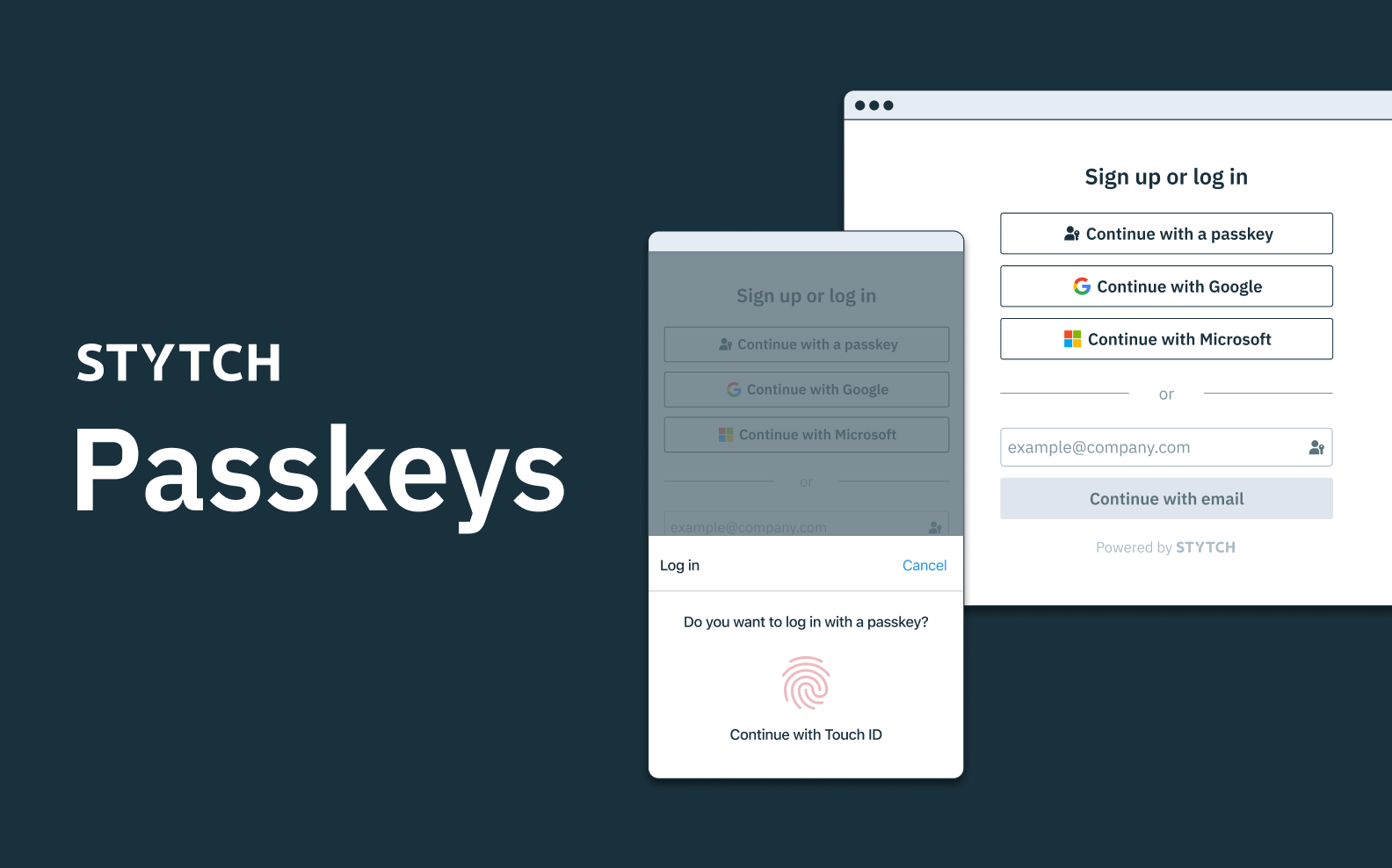
Essentially, passkeys are a phishing-resistant, drop-in replacement for passwords. They rely on biometric verifications like FaceID or TouchID and can be used across different devices, platforms, and ecosystems. Using a passkey is a bit like using a password manager, since a user’s credentials are stored in the cloud and easily accessible from any connected device, just like other cloud-synced features like a user’s photos, contacts, emails, and documents.
Want Passkeys for your app? Switch to Stytch
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
How do passkeys work?
Passkeys rely on pre-existing public key (or asymmetric) cryptography, which creates pairs of public and private cryptographic keys that usually encrypt and decrypt user data, respectively. Typically, the public key is stored on the server, while the private key is stored locally on a user’s device or on hardware like a USB drive or biometric scanner.
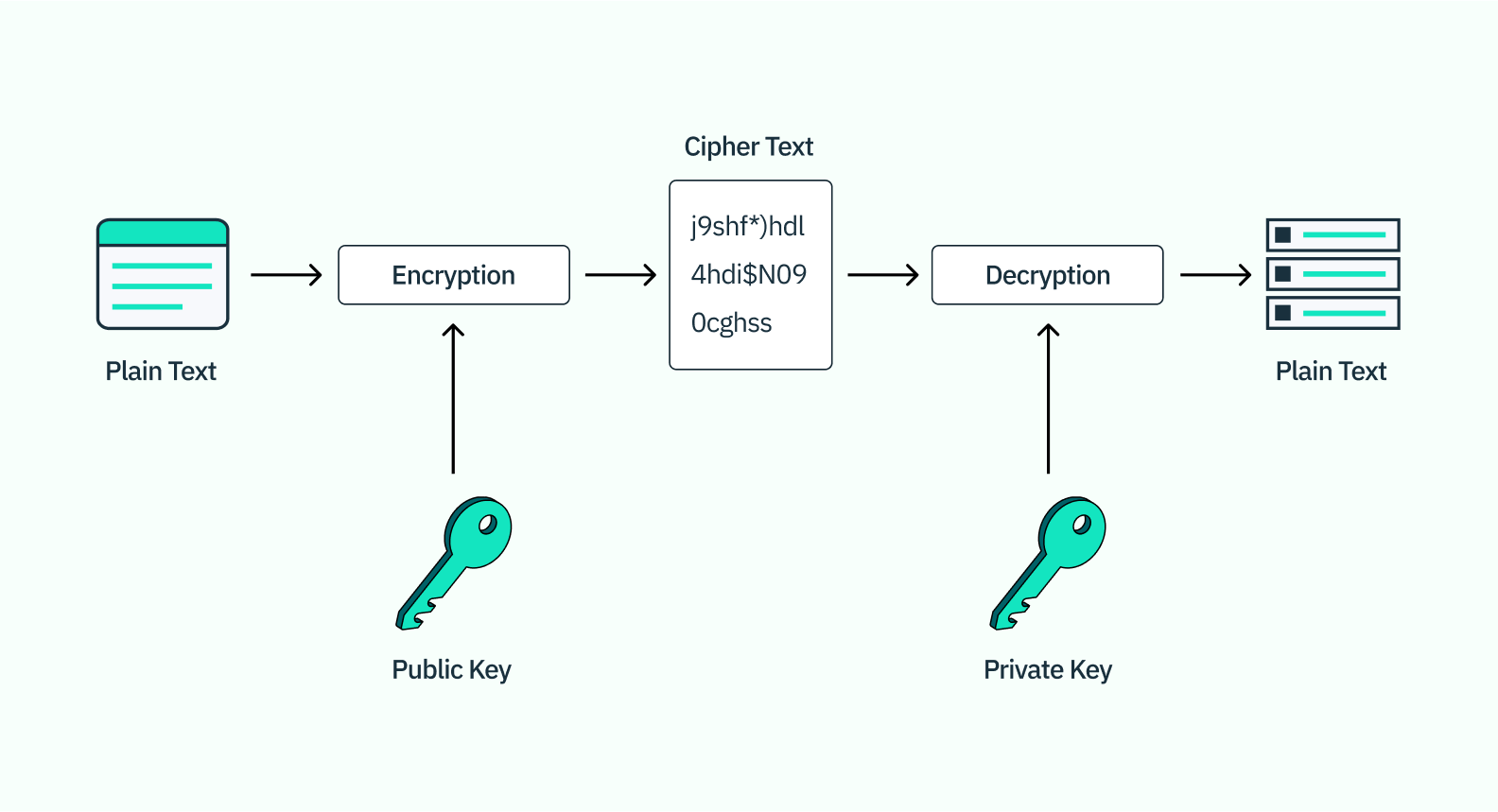
With passkeys, however, the key pair is end-to-end encrypted and backed up to the cloud account on a user’s primary device — that is, iCloud for iPhones and Macs, Google for Androids and Chromebooks, and so on. That means that any device that syncs to this cloud account can use a biometric factor like FaceID or TouchID to verify a user, access the cryptographic key pair, and log the user in.
It is worth noting, too, that the raw data from the biometric authentication itself is not stored in the cloud — just the cryptographic key pair it unlocks — so it cannot be stolen and put to malicious use.
How are passkeys different from native biometrics and WebAuthn?
Passkeys have certain commonalities with other forms of passwordless authentication like biometrics, but there are key technical differences when it comes to how the biometric data is captured and where it is stored. Let's look a little closer.
Native (or on-device) biometrics
Native biometrics leverage a biometric scanner on a user’s laptop or mobile device and ties it to locked storage of either credentials or public/private key pairs. For example, a user might use a fingerprint, faceprint, or voiceprint to unlock the key pair sharing capability with an application in order to log in. This is referred to as native biometrics because the biometric data is only stored on their local phone — never on the app itself.
WebAuthn

WebAuthn is the combination of public key cryptography with either native biometrics or a piece of physical hardware like a YubiKey. As with native biometrics, the identity data from WebAuthn is always tied to a specific device, whether that’s a user’s phone or their YubiKey.
Passkeys
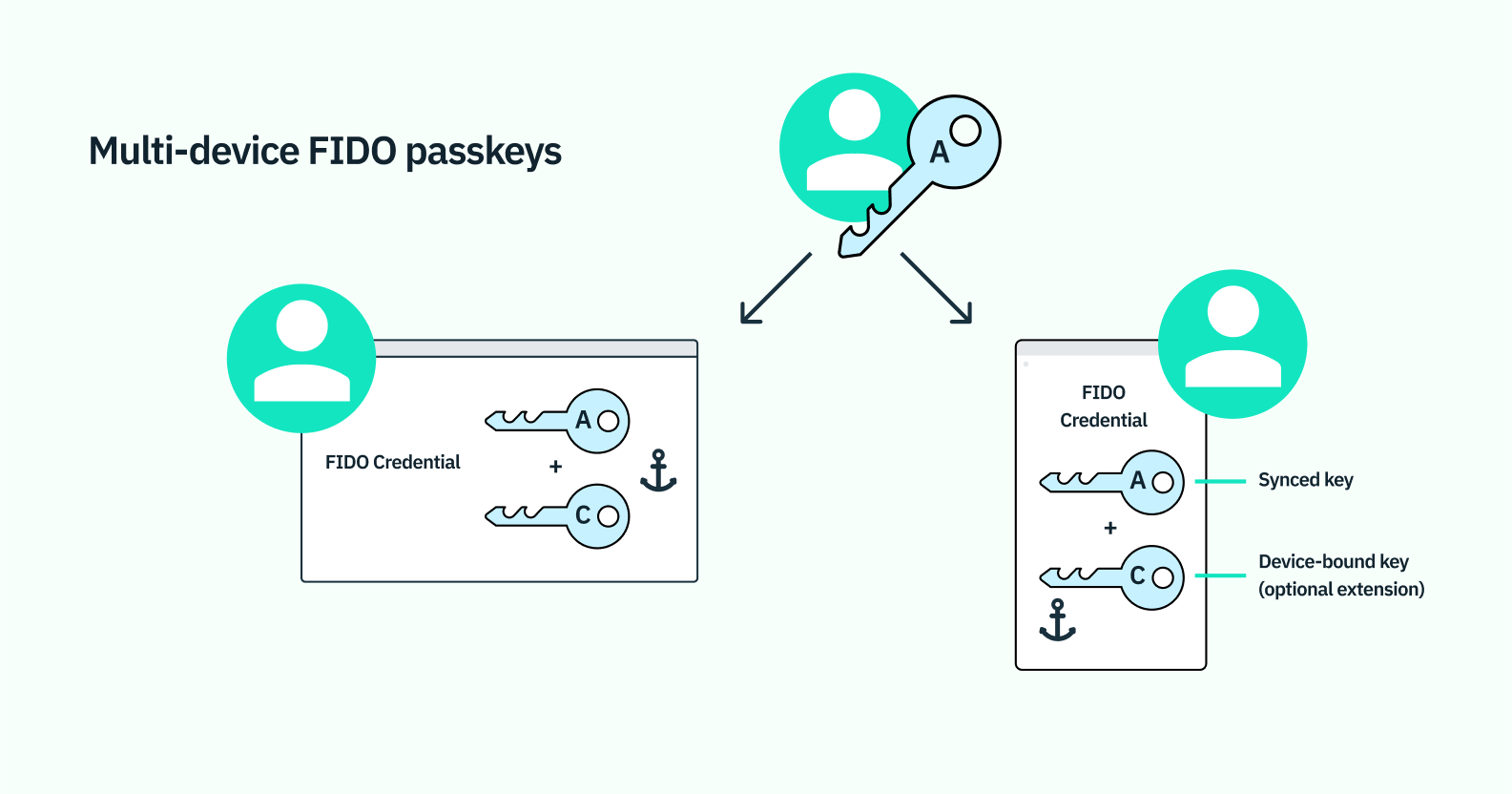
Passkeys as we've covered also combine public key cryptography with native biometrics, but unlike WebAuthn they are not limited to a single device. Using wireless technologies like bluetooth or a QR code, a user can sync passkey data with other devices within the same operating system (like from an iPhone to a MacBook) or even a device on a different operating system (like from an iPhone to a PC).
What are the benefits of passkey login?
Passkeys offer the same advantages as biometric authentication more generally, including one-step account creation, a seamless user experience, and stepped-up security. It comes with three big advantages:
Passkeys make recovery easy
Unlike on-device biometrics or WebAuthn, backed-up biometric data means users have ongoing access to a biometrics-enabled account, even if they lose or break the original device used to create it.
Passkeys optimize access and usability for FIDO authentication
Before, biometrics were restricted to a single device, so a user would need to re-enroll in a new biometric auth flow for each of their devices — on their phone, their tablet, their laptop, etc. — for the same account. With passkeys, the original biometric flow carries over.
Passkeys are as user-friendly as a password, but more secure
As with native biometrics and FIDO's WebAuthn, passkeys rely on unique bodily or behavioral traits to verify a user’s identity, and these attributes cannot be lost, forgotten, guessed, or easily replicated by a hacker. Moreover, passkeys are equally impervious to phishing, because they’re tied to the specific website or application that prompted them and can’t be used on a malicious or fraudulent site instead.
To put it another way, passkeys work just like traditional, interoperable passwords, but without the security risks and the need to remember complex credentials. Like all biometrics, passkeys still fall under the category of “something-you-are” authentication — they just respect the fact that you’re still you, regardless of where you go or which device you use.
What are the challenges to using passkeys?
Various platforms have already begun implementing passkeys, including Apple, Google, and Microsoft, and their future looks bright. However, there are still a few obstacles to face in terms of usability, security, and implementation.
From a usability standpoint, passkeys share some of the same drawbacks as other forms of biometrics. These include occasional false rejections, which can occur with everyday variations to a user’s physical features — for example, if they’re wearing a mask or their voice is altered due to illness. Biometrics are also imbued with society’s systemic biases, exhibiting higher error rates for AI-underrepresented groups like women and people of color.
Furthermore, passkeys are only as secure as the cloud accounts they’re stored on. And the fact that users’ biometric credentials are automatically synced across all cloud connections means their data may end up on devices where it was not intended to be.
In terms of implementation, passkeys are currently somewhat limited in scope, since biometric-protected keys are still incompatible with the cloud-syncing function in many cases. For this reason, their large-scale adoption will be a slow burn as auth providers and other cybersecurity platforms learn to integrate their syncing features securely and effectively.
How Stytch is supporting passkeys
Stytch is committed to providing phishing-resistant FIDO credentials as part of our suite of passwordless authentication products.
We’ve already launched a set of robust native biometrics, including fingerprint and facial recognition tools powered by our flexible API, as well as frictionless WebAuthn solutions. Today, we support multi-device passkeys as a secondary authentication factor for 2FA, but we're also excited to extend support for passkeys as a primary authentication factor in the near future, too.
Check out our biometric solutions
To learn more about our approach to biometrics — and how we’re opening the door to multi-device, phishing-resistant passkeys — get in touch with one of our auth experts. You can also sign up for a free account to try our solutions out for yourself.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.