Back to blog
The best authentication services in 2025
Auth & identity
Apr 16, 2025
Author: Stytch Team
Authentication services provide a prebuilt set of tools that you can use to secure your websites, apps, and internal tools.
The best platforms today go beyond simple authentication methods — they need to offer multi-factor authentication as well as enterprise-ready features like Single Sign-On (SSO), System for Cross-domain Identity Management (SCIM), OAuth-based third-party app integrations and even fraud prevention technology like bot detection.
This article will cover the key features and qualities to look for in a modern authentication service.
What makes an authentication service the "best"?
The best authentication service will balance developer experience with enterprise features, security, reliability, scalability and usability while meeting the unique requirements of your project. This may include additional enterprise features, integration with your existing tools and platforms, and legal compliance.
Developer experience
The developer experience (DX) of an authentication service can make or break its reputation. Services that are frustrating to use rarely do well when better choices exist.
A good authentication service will provide easy-to-use and well-documented APIs and SDKs, with developer-specific support channels like forums and helpdesks. Multiple integration options should be provided, including:
- API-first architecture with REST endpoints for full control over authentication logic and integration into any stack
- Frontend and backend SDKs for the languages and frameworks you use (e.g. React, Next.js Python, Go, Node.js)
- Headless options for customizing authentication flows
- Pre-built UI components like customizable login forms or ready-made authentication flows
- Infrastructure-as-code support with Terraform
- Event log streaming and integrations with observability tools like DataDog
The more functionality an authentication service provides, the less you have to build, maintain, and audit.
Enterprise features
The best authentication services for enterprise use cases should include:
- Single sign-on (SSO): Typically implemented using SAML (Security Assertion Markup Language).
- Just-in-time (JIT) provisioning: When a user first logs in, a user account gets created on the fly.
- System for cross-domain identity management (SCIM): A central Identity Platform (IdP) manages users. When a user is added or deleted from the IdP, accounts are created or removed/disabled across all applications.
- Organization tenancy: Most enterprises require the ability to set different login methods or security policies for different organizations.
- Machine-to-machine (M2M) authentication: An enterprise-grade authentication service needs to allow different services to communicate and authenticate with each other, not just users. This is usually done using OAuth or API keys.
- Embeddable admin portal: Allow your customer's to self-manage their users auth settings and their roles directly within your application, rather than relying on your engineers to do it.
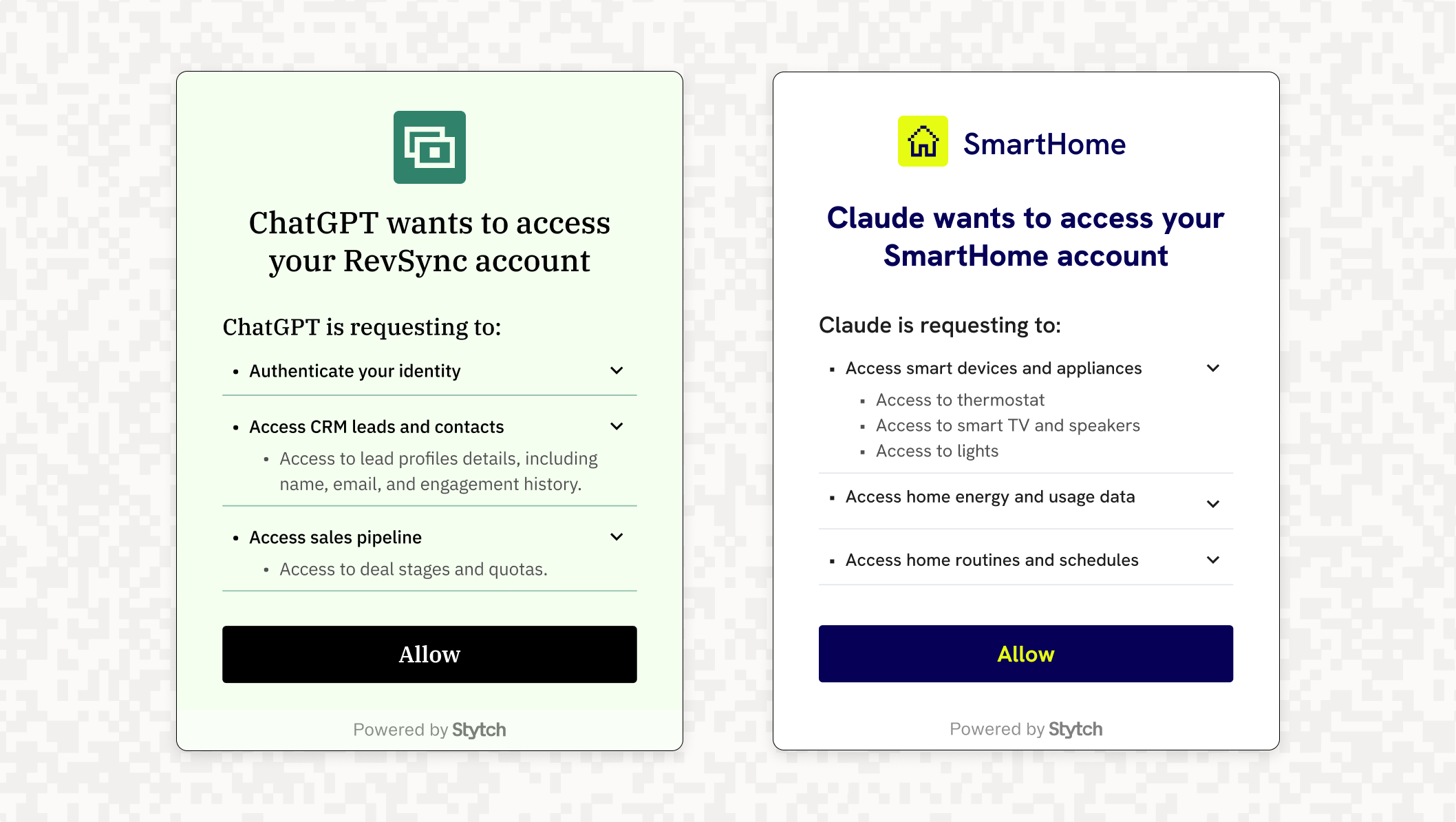
- AI agent authentication: The explosion of AI agents doing tasks on behalf of users means that modern authentication services need to be able to authenticate agents and distinguish them from bots.
- Role-based access control: This can include the ability to assign roles like administrator, user, or viewer, or to set rules based on things like department or region using custom permissions to limit who can access what resources.

Security
A secure authentication service should protect your users and your organization against attacks like brute forcing, man-in-the-middle attacks and social engineering. A secure authentication service should include:
Fraud prevention and bot detection
A secure authentication service will use logging and monitoring to record details on your users (such as common locations and devices), and require extra layers of MFA if the login looks suspicious.
It will also detect potential bots by rate-limiting logins from the same IP addresses or using CAPTCHAs. However, as fraud techniques have become more sophisticated, involving humans and bots working in tandem, basic bot detection is no longer enough to keep your application secure.
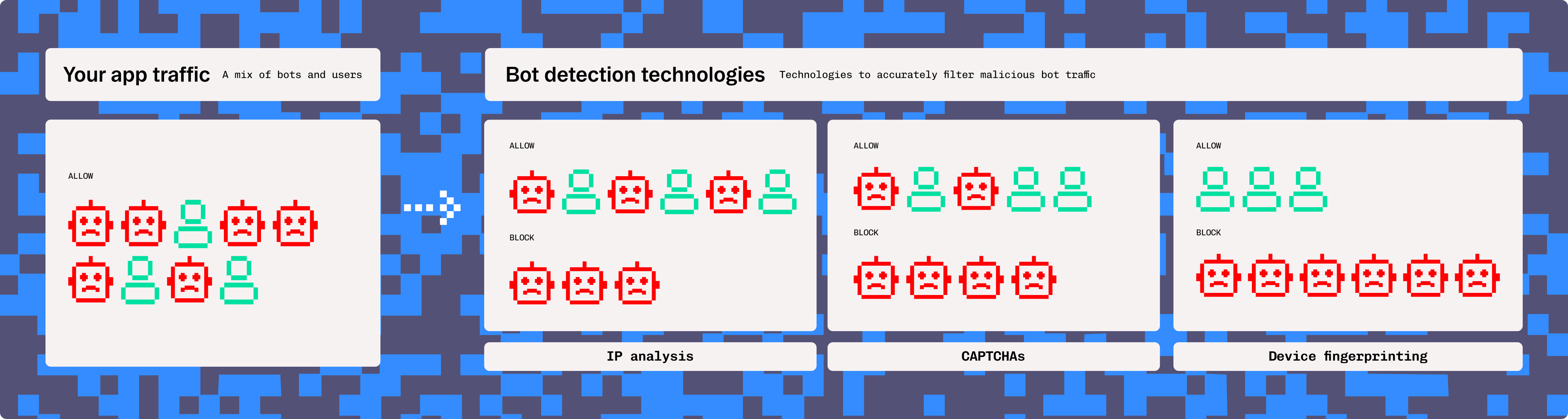
To solve this issue, more advanced techniques such as device fingerprinting are now required, to detect malicious actors who aren't bots. Device fingerprinting means generating a complex identifier for each device that interacts with your application that is stable and can persist across changing sessions and networks.
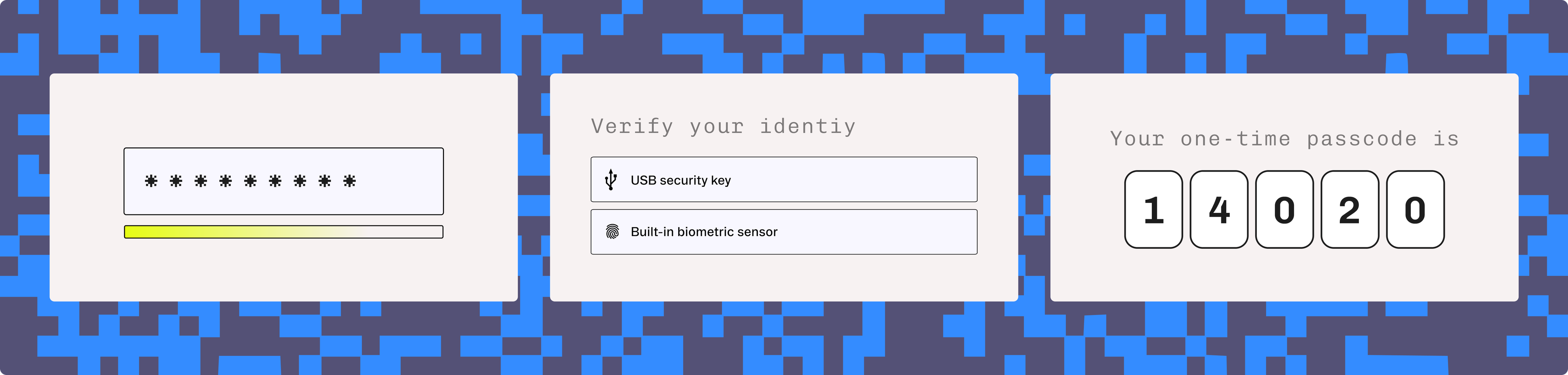
Multi-factor authentication (MFA)
Allows your users to verify themselves using multiple factors. Common examples are a password and a one-time password (OTP) or a time-based one-time password (TOTP) from an authenticator app.
Compliance and regulations
Your chosen authentication solution should also be compliant with regulations like GDPR, HIPAA, or CCPA. Adhering to one of the major cybersecurity frameworks (like ISO 27001 or SOC 2) is also a good way to show your users that you're committed to security and regulatory compliance.
Reliability and scalability
The performance of an authentication service is critical, and any latency it adds should be minimized. The availability of the service is also key, so check out the availability SLAs for each provider that you're considering. It should also be able to meet demand: scalability is a key benefit of adopting SaaS tools rather than hosting and maintaining your own infrastructure.
Many modern providers now offer transparency over their uptime and past incidents with a status page. You should also investigate their level of customer support, how well it can scale (or handle traffic spikes), and its approach to redundancy and failover protection.
User experience
Users may be driven away if your application is not intuitive to use, or if it makes them jump through too many hoops to sign up and log in. Inconvenient authentication can also encourage users to try workarounds. For example, forcing users to create an account for your site rather than using a social login can promote password reuse, or in enterprise environments, frustrated users may turn to account sharing.
Authentication services with good UX should offer:
- Customizable UX and auth flows: A full toolkit of APIs, SDKs, and pre-built UI components will make the process of building the ideal UX or authentication flow much easier.
- Frictionless login options: such as single sign-on, OAuth, and passwordless authentication (including passkeys) makes your apps easier to use while encouraging security best practices from your users.
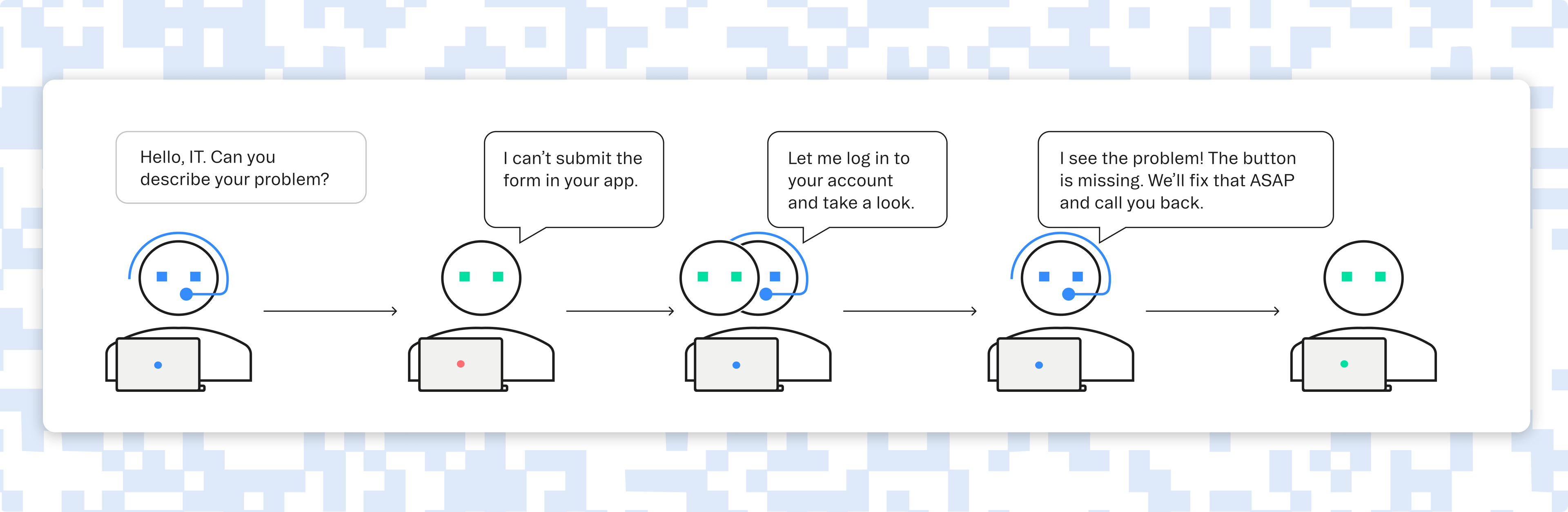
- Seamless troubleshooting: You also want to be able to offer support to your users if they experience issues using your app. An authentication service that allows you or your support staff to securely impersonate a user will make handling any customer issues much smoother.
How to choose the best authentication service
To work out which authentication services will be best for your business or project requirements, you should make the following assessments:
Who are your users and how should your business and technical architecture support their expectations?
In addition to robust security and scalability, when choosing authentication solutions for customer-facing B2C apps, you should focus on features that make it as easy as possible for users to onboard and login. This includes social login methods using accounts your users already have (for example, Facebook and Google) and passwordless authentication.
For B2B and enterprise organizations, multi-tenant applications must support per-organization settings, so you can tailor your authentication policies to each tenant. For example, one customer might require SAML-based single sign-on, while another prefers a combo of passwords and TOTP for MFA, and yet another might want to restrict access by email domain.
An example of how Stytch allows authentication methods to be set on a per organization basis is shown below.
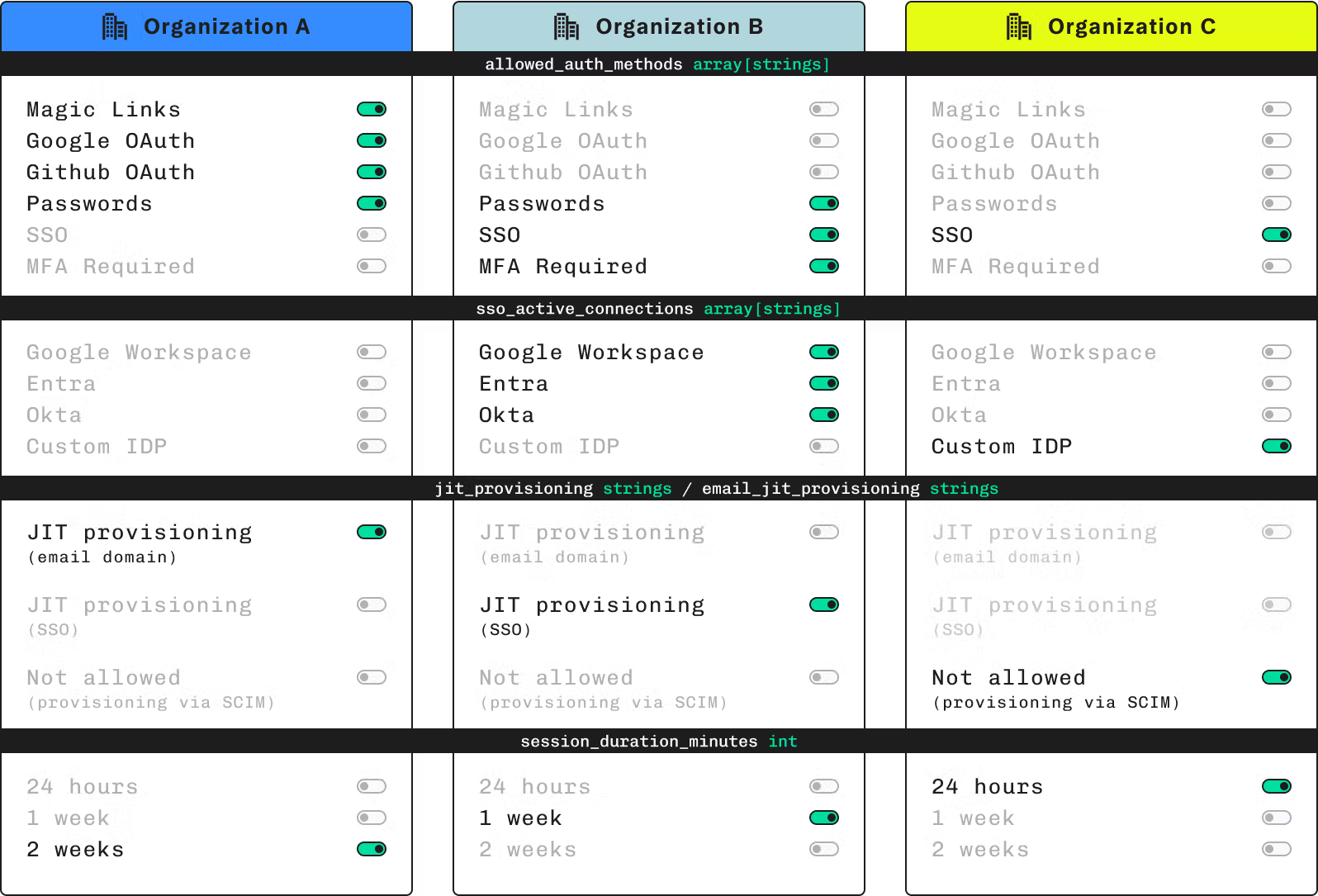
Role-based access control (RBAC) is also vital in enterprise, protecting sensitive resources by granting users and services access to only the data and functions they require to perform their roles. In order to stay compliant with regulations, you'll also need audit logs, and if you're dealing with sensitive data, you may need your authentication provider to offer an on-premises solution.
This should also be paired with fraud and risk prevention strategies. You'll need your authentication service to detect bots and malicious humans, by intelligently detecting devices and applying security rules and rate limits to anything deemed suspicious.
You may have a hybrid use case that spans both B2C and B2B (Slack, Figma, or Notion, for example), in which case your solution will need to provide a versatile feature set that can cover different user segments. If you have both a single-user tier and an enterprise tier, you may need to think about RBAC, or about different accounts for individual users vs organizations, or how a single user can be a member of multiple organizations, as below:
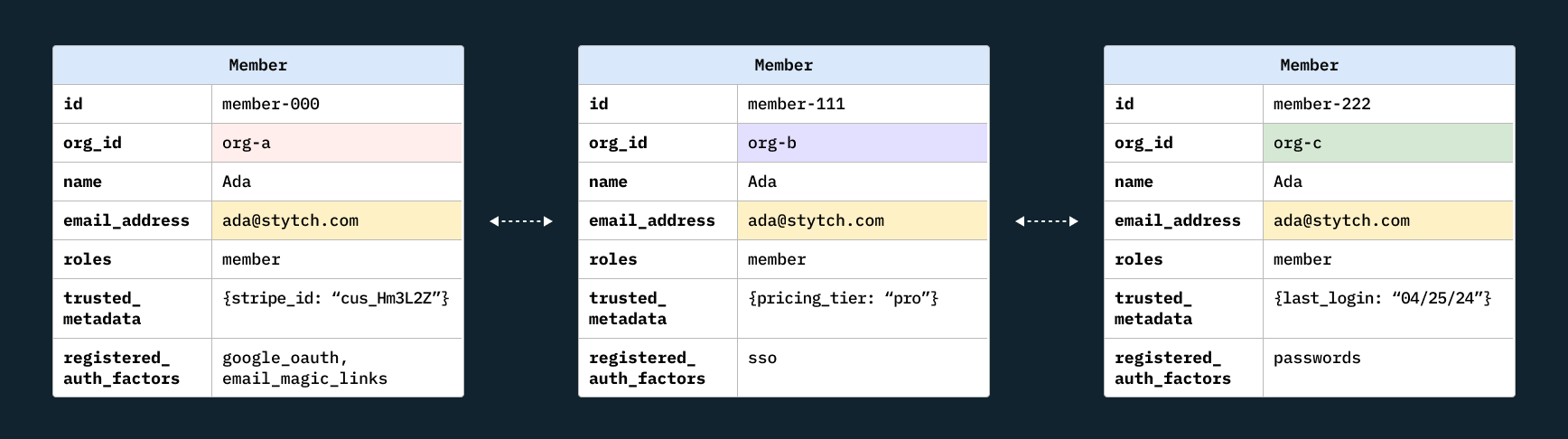
Do you need to comply with GDPR, HIPAA, or other data regulations?
On top of strong security measures such as encryption and MFA, you may need to implement specific security technologies and processes to comply with user privacy regulations such as GDPR, CCPA, and HIPAA. There are also industry-standard certifications that may need to be met, such as ISO 27001 or SOC 2. Some extra features that you may need in order to meet these standards include RBAC, audit logging, and data processing agreements (DPAs). It's worth noting that most major authentication providers offer pre-signed DPAs.
For industries that deal with highly sensitive data, you may need to be able to choose which region your data is hosted in, or be able to self-host your full software stack (either in your own private cloud or on site so that you can remain fully responsible for it). This is especially important with privacy frameworks that give users the rights to redact and correct their data, as you can ensure that their requests are met in full.
Do you need to self-host or do you prefer a solution managed by experts?
When answering this, consider:
- Compliance and responsibility: Does your industry require that certain user data be stored on-premises, or within a specific geographic region?
- Performance: Do you have specific, very low-latency performance needs that you'll need to manage yourself, or will a managed service be good enough?
- Cost: You'll want to compare the infrastructure and maintenance costs that come with self-hosting with the annual subscription cost of a managed authentication service.
How much do you value your developers' time (and sanity)?
An auth service that's easy to integrate with clear documentation (ideally with code examples!) and good customer support channels will be faster and less frustrating for your developers, leading to a more reliable product.
An authentication service will be easier to integrate if it provides the different developer tools and integration methods your team needs. It's worth checking upfront which developer tools each provider offers (e.g., APIs and SDKs for your chosen languages, admin dashboards, or pre-built UI components), and which integration methods they offer (e.g., front-end, back-end, hybrid, mobile, or microservices). That way, you can choose one that covers all your needs.
You should also ask your development team whether they need maximum code control (in which case an API-driven solution with SDKs for their chosen languages will be a must), or whether they prefer to use plug-and-play login widgets (this choice might be more popular for teams with fewer engineers, or that want to release a prototype quickly).
Best authentication services for 2025
When comparing the top authentication services available in 2025, you should consider their target use cases, key features, user experience, and developer-friendliness. Below are some popular authentication services to consider:
Stytch
The Stytch authentication platform provides developers with the tools to build seamless authentication experiences across multiple devices and platforms for any kind of application including B2B and Consumer. It's developer-friendly and was designed with an API-first approach.
Stytch is scalable and quick to implement, and it has comprehensive documentation and examples for the API, including multiple back-end and front-end SDKs. Stytch can be integrated with any IAM solution that supports industry-standard protocols, making it highly flexible.
Key Stytch features
- API-first approach with multiple integration options
- Fraud & Risk Prevention features like bot detection and device fingerptining
- High reliability and uptime
- Purpose-built APIs for both B2B and Consumer auth
- AI agent authentication with OAuth support
- Developer support: First-class developer support with comprehensive documentation, SDKs for multiple languages and developer-focused tooling.
- Auto-deduplication of users
- Provider failover for highly available delivery of SMS and email
Auth0 by Okta
Auth0 by Okta offers pre-built solutions, such as its universal login to assist with implementation, and it offshores all auth flows onto Auth0 servers, meaning you don't have to manage any of it. It's easy to use, is highly configurable, and has a comprehensive dashboard. It also offers enterprise features like SCIM and M2M authentication; however, it can be expensive, and the cost scales rapidly as you add more users and features.
Features such as SSO, social logins, MFA, and M2M authentication are provided out-of-the-box, at the expense of flexibility, as you are unable to completely customize your own authentication logic. However, you do still have some level of control over parts of it (through its actions and other dashboard functions). The pre-built authentication flows can save time for under-resourced teams; however, they can also lead to issues like extra latency or vendor lock-in.
Key Auth0 features
- Universal login across platforms
- Social and enterprise logins
- Single sign-on
- RBAC
- Secure API access using OAuth 2.0
Amazon Cognito
Amazon Cognito integrates well with other AWS services, such as Lambda, API Gateway, and S3. It's also the cheapest authentication service to get started with, being free for up to 50,000 monthly active users. It does, however, require a lot of work to implement, and it is heavily AWS centric, which may promote vendor lock-in.
Key Amazon Cognito features
- User pools to manage users and authentication
- Identity pools for managing authorization or granting temporary IAM roles
- MFA
- Social and enterprise logins
- Customized authentication flows triggered by Lambda
Firebase
Firebase Authentication is great if you want fast integration with mobile/web apps without having to manage authentication logic on the back end. It offers cross-platform support with iOS, Android, and Flutter, and it scales to millions of users since it's backed by Google Cloud's infrastructure. It offers a free tier, which is useful for startups and new projects with a lower initial budget.
However, Firebase Authentication is limited in scope and generally unsuitable for use cases outside of consumer mobile and web apps, such as server-to-server authentication or enterprise authentication, as it doesn't have built-in support for advanced identity management like SAML, or on-site directory sync.
Key Firebase Authentication features
- Tightly integrated with the Firebase ecosystem
- Designed to integrate into front-end projects easily
- Offers multiple authentication methods
- Uses automatic session handling to manage tokens and user state across sessions with minimal back-end setup
Clerk
Clerk is designed to work with Next.js (and includes fully pre-built UI components). It's easy to use with features like session management built-in, which includes robust session handling without any extra setup required. Due to its focus on Next.js and assisting front-end developers, it can be difficult to use with other frameworks (or back-end authentication), and it seems less well-designed for larger enterprise projects, offering fewer enterprise features than some other providers. It can also become quite expensive once you start scaling to larger numbers of users.
Key Clerk features
- Next.js focused
- Pre-built, customizable UI components for sign-up, sign-in, and account management
- User management for consumer apps, including session management, user profiles, and RBAC
- REST API support
Keycloak
Keycloak is a self-hosted, open-source authentication service, and it is highly scalable and customizable, giving you full control over data and configurations. It has Active Directory integration and can also act as an IAM in addition to being an authentication provider. Keycloak's biggest advantage is also its biggest weakness: for organizations that don't need full control of their infrastructure, self-hosting takes more time to implement and requires significant responsibility for the security of the system, as well as ongoing maintenance and hosting overheads.
Key Keycloak features
- Open source
- Self-hosted
- Can act as an IAM, giving SSO, OAuth2, OpenID Connect, and SAML support
- Offers fine-grained RBAC
Comparison of the best authentication services
The below table summarizes the authentication services compared above.
Best auth services for this use case | Reason | |
|---|---|---|
Frictionless login for consumer apps | ||
Frictionless login for consumer apps | Stytch Clerk Firebase Authentication | All support social logins with multiple providers, OTPs, and passkeys. Stytch and Clerk also support magic links. |
Enterprise security and compliance | ||
Enterprise security and compliance | Stytch Auth0 by Okta Keycloak Amazon Cognito | All support single sign-on and multi-tenancy, however Amazon Cognito's multi-tenancy requires more manual work. Stytch and Auth0 support RBAC, whereas Amazon Cognito has more limited RBAC. Stytch, Auth0, and Amazon Cognito are compliant with ISO 27001 and SOC 2, but as Keycloak is self-hosting, this is something you need to organize yourself. |
Self-hosting | ||
Self-hosting | Keycloak | Keycloak is the most commonly used self-hosted authentication service. |
Developer experience | ||
Developer experience | Stytch Clerk | Stytch's API-first approach and multiple SDKs allows flexibility and customized authentication flows. Clerk's pre-built UI components and seamless integration with Next.js make it easy to use, particularly for front-end developers. |
Cost effectiveness | ||
Cost effectiveness | Amazon Cognito Stytch Keycloak | Amazon Cognito is completely free for your first 50,000 monthly active users. Stytch has flexible pricing for consumer apps and also has a free user allowance. Keycloak is self-hosted, so you have some level of control over the price. |
Uptime & support | ||
Uptime & support | Stytch Auth0 Clerk | Stytch has 99.999% uptime SLA, and Auth0 and Clerk have 99.99%. All three also have 24/7 email support and dedicated Slack support channels. Firebase and Amazon Cognito don't offer direct human support (unless you separately pay for a support plan). Firebase has no uptime SLA as standard. |
Ultimately, the best authentication service depends on your requirements, as well as your future requirements!
Future-proof authentication for your application
Stytch offers a developer-friendly, flexible, API-first authentication service that can be used to secure both customer-facing apps and enterprise services in a single platform.
Contact Stytch sales to talk about what kind of authentication is best for your use case, or sign up free and try Stytch now.
Build with Stytch
APIs and SDKs for authentication, authorization, security and fraud prevention
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.