Back to blog
Why email verification is crucial for B2B applications
Auth & identity
Jan 4, 2025
Author: Basia Sudol
Author: Stytch Team
In the dynamic world of B2B and multi-tenant applications, email verification during signup is not just a best practice—it’s a cornerstone of secure application design. It’s one of the simplest and most proactive steps any engineering team can take to prevent fraud.
Some may worry that introducing up-front verification could impact sign-up conversion rates. However, the benefits of email verification far outweigh the manageable UX challenges. Email verification protects businesses, their customers, and their sensitive data from a myriad of potential security threats.
We will explore those threats and key considerations on how to verify email addresses in this article.
Why email verification matters for B2B apps
For B2B applications, where users often represent entire organizations, the stakes are even higher. A compromised account or an unchecked fraud attempt could impact multiple users not only within the same tenant but also across tenants.
B2B applications often deal with highly sensitive company data. In multi-tenant environments, where multiple companies share the same infrastructure, email verification becomes vital. Without it, unauthorized users could exploit vulnerabilities in tenant segregation, potentially leading to data leaks or unauthorized access to another tenant's environment.
For example, imagine a SaaS platform like Workday, Gusto, or Rippling, where multiple companies manage their payroll and HR data. Without email verification, an attacker could register using a domain they don't own (e.g., tim@gusto.com) to impersonate a legitimate user from Gusto. This could allow bad actors to manipulate or steal data intended for actual employees.
Non-verification will also result in an influx of fake signups, trial repeaters, spammers from disposable emails and bots—polluting the integrity of your user base and business. The downside of not verifying emails is costly.
Preventing account takeovers, breaches and, abuse
If your application doesn’t require email verification, malicious actors can exploit this gap to register accounts with email addresses they don’t control, opening the door to several risks. Here are several attack vectors you should be aware of.
Pre-hijacking accounts and invites
Without email verification, a bad actor can preemptively create an account under another user's email address ahead of time. Once the real owner of the email signs up or logs into the site using a passwordless method, the attacker now retains backdoor access to the account with a password they previously set up.
Attackers might create thousands of accounts using legitimate email addresses, and then wait for the real owners of these emails to sign up or log into these apps using alternative authentication methods.
This also creates the risk of app invitations being hijacked through spoofed email addresses. For example, if your application allows user invitations via email, an attacker could preemptively register with the email before the legitimate employee does.
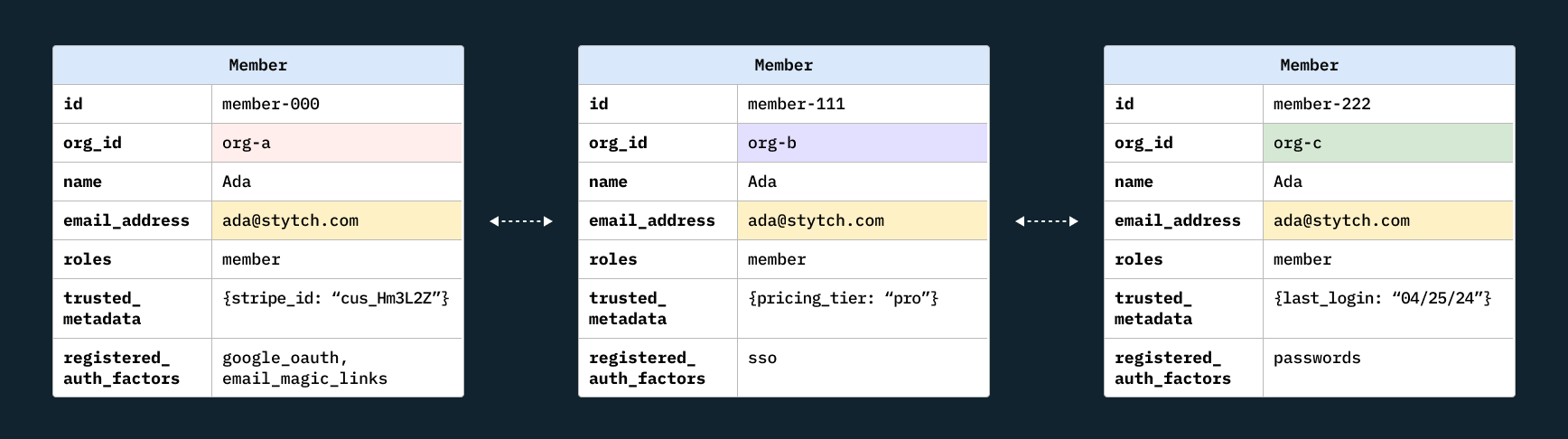
These types of attacks could have severe consequences for both B2C and B2B applications, particularly if your authentication provider or service deduplicates accounts based on different auth methods rather than intelligently linking legitimate profiles. With Stytch, however, all authentication methods, regardless of the method a user initially signs up with, point to the same user profile because we strictly enforce email verification as early as possible.
Honeypot organizations
Honeypot Organizations or organization spoofing occurs when an attacker impersonates a legitimate company to gain unauthorized access. Attackers may create fake organizations using convincing but illegitimate email domains (e.g., hr@realcompany.com) to trick employees of the real organization into joining.
If your B2B app doesn’t enforce email verification, attackers can easily trick employees into joining fraudulent organizations, either by sending deceptive user invitations or sophisticated social engineering scams. Once infiltrated, attackers could steal confidential information, manipulate internal workflows, or even launch phishing attacks within the organization.
Slack faced a huge surge of invite spam, where attackers exploited its user invitation flow to impersonate organizations and send deceptive user invites.
Free tier and trial abuse
One of the most common methods of free trial abuse is using temporary or disposable email addresses to set up fake user accounts on SaaS apps that don’t verify email ownership. For companies that offer free trials or credits as part of a PLG strategy, attackers may sign up for infinite accounts in order to continuously abuse free resources.
Fraudulent users often use these fake accounts to exhaust system or compute resources (like AI compute, storage space, processing speed, API calls, etc.) which are typically capped for legitimate free users.
Aside: At Stytch, we’ve seen how combining email verification with intelligent and advanced device fingerprinting creates a strong defense against free trial and freemium abuse. By using our fingerprint APIs and SDKs to detect and block fraudulent authentication attempts from the same device or network, you can significantly limit resource abuse for any app.
Email verification is still the industry standard
The importance of verifying email addresses upfront isn’t just a best practice—it’s the standard among leading companies. An analysis of the AI Auth Landscape reveals that top companies in the space require email verification during signup:

These companies handle highly sensitive data, making email verification a critical security measure. The takeaway? Email verification isn’t just a security enhancement—it’s an expected part of interacting with your application.
Implementing email verification
Robust email verification doesn’t have to disrupt the user experience. By implementing user-friendly, secure methods, applications can achieve a balance between security and convenience.
Fortunately, there are now multiple auth conventions and methods that engineering teams can rely on to verify email ownership without disrupting the standard user experience, and Stytch supports them all.
Email Magic Links and One-Time Passcodes (OTP)
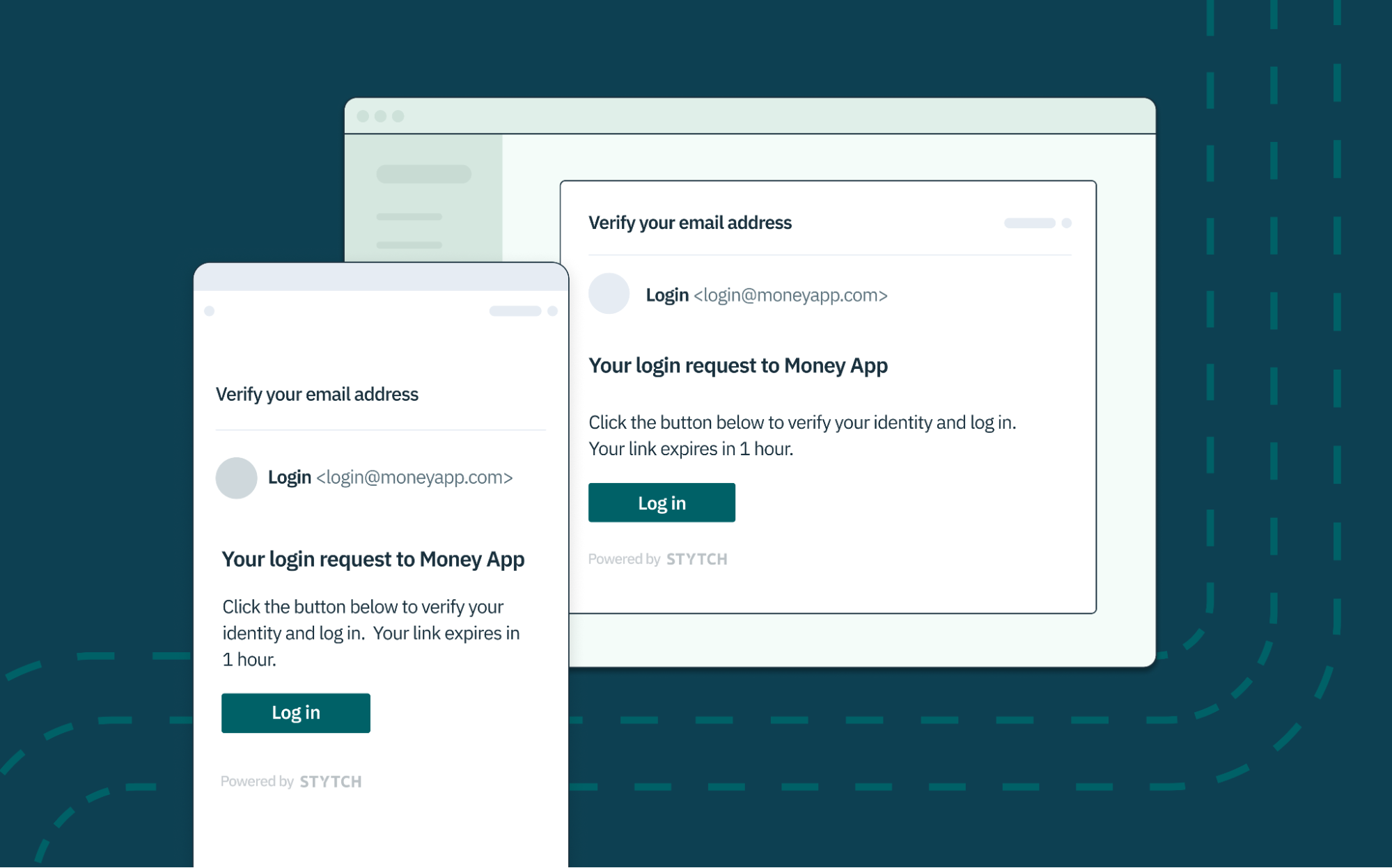
In traditional email + password authentication flows, the easiest way to verify that a user owns a particular email address is to send a unique magic link or one-time passcode (OTP) to the email they must have provided. At Stytch, we’ve built our email verification products to provide an even more seamless auth experience, so much so that your users may not need to store or remember any passwords.
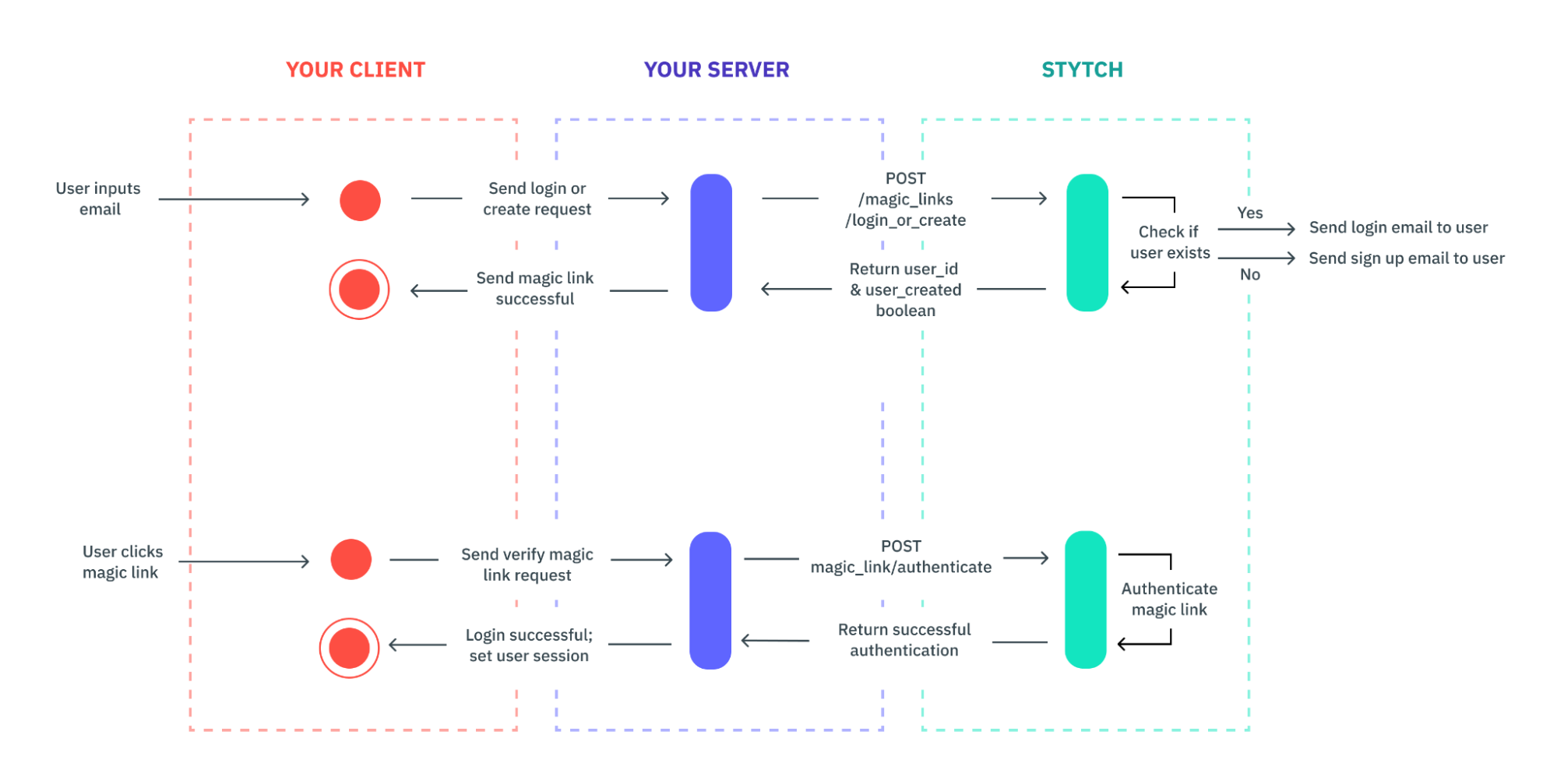
Stytch handles the delivery of all your Email Magic Links and OTPs. With Stytch's APIs, you can also build out your sign-up, sign-in, and password reset flows using OTPs across email, SMS, and WhatsApp, ultimately relieving your engineering team from the overhead cost of building and managing these messaging services.
OAuth with reputable providers
Another reliable method for verifying user identity and email ownership is OAuth and OpenID Connect (OIDC). By allowing users to sign up or sign in through trusted third-party identity providers like Google and Microsoft, your app offloads the burden of identity verification to established industry providers.

Regardless of whether you’re a B2B or B2C app, Stytch offers out-of-the-box OIDC support for over 14 identity providers, including GitHub, Salesforce, Slack, Hubspot, Apple, Facebook (Meta), and more.
Single Sign-On (SSO) for Enterprise Clients
For enterprise-focused B2B applications, SSO is a must-have authentication method for integrating with identity providers that house and manage corporate email addresses.
Identity providers (IdPs) such as Google, Okta, and Microsoft Entra ID, OneLogin often manage their identity profiles for corporate users in XML format. These can only be accessed by building intricate configurations and assertion flows according to complex identity protocols (SAML or OIDC).
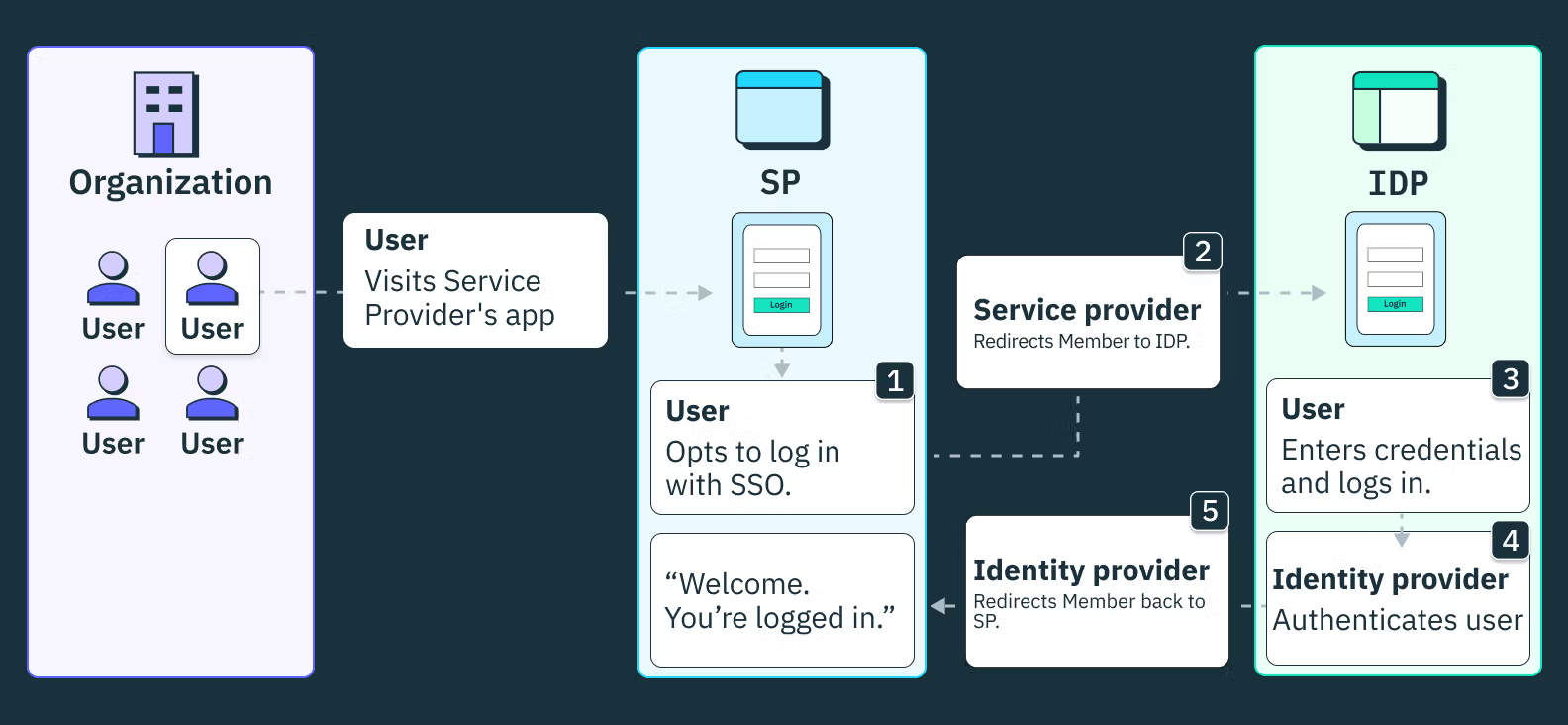
With Stytch, you don’t need to build support for the SSO from scratch. Instead, you can easily configure SSO for your enterprise customers, regardless of the IdP where their user identity data is stored. Stytch facilitates the exchange of SAML and OIDC requests and assertions between the IdPs and your B2B app.
Stytch: seamless and secure B2B auth
When it comes to B2B authentication, balancing security and user experience is crucial. Here's more detail on how Stytch leverages email verification to deliver a modern, frictionless approach to B2B authentication:
- Stytch’s B2B platform always requires email verification through a trusted factor (OAuth, Email magic links, Email OTPs, or Enterprise SSO) in order to sign up for an account in any organization.
- Stytch’s Discovery Flow allows users to see and accept pending invites, or Just In Time Provision into their team’s workspaces based on email domain after verifying their email address

- Stytch supports Google One Tap, a very popular, low-friction implementation of login with Google that enables end users to select their account and login/signup with a single tap.
- Stytch has built in ergonomics to ensure that conversion remains high with email based methods, such as built in failover email providers and protection against email security scanners.
- Stytch automatically deduplicates accounts safely on email address to provide a seamless experience where users can log in through any method and gain access to the same account. We address the pre-hijacking vulnerability in our B2B product by always requiring email address validation on sign up.
Product and engineering considerations
Introducing email verification into applications is often a decision driven by product teams. While engineering may hesitate to advocate for changes due to concerns about added complexity, product teams typically focus on the broader impact on user activation and security.
Here's how to align the teams:
- Highlight UX Benefits: Alternative login options like Google OAuth, email magic links, or one-time passwords (OTPs) can actually improve activation rates rather than slow them down (one example: 7% uplift with Google One Tap for Zapier) while ensuring security. See more literature on how passwordless login methods impact user conversion here.
- Mitigate Engineering Concerns: Many teams will opt to migrate to a provider like Stytch as opposed to investing the engineering resources to build solutions to these problems in-house. Teams like Orb have successfully migrated millions of users to Stytch in just one week and were able to implement these security and UX improvements very quickly thereafter.
- Emphasize the high cost of skipping verification: Skipping email verification may seem like a shortcut to streamline the signup process, but the risks far outweigh the temporary benefits:
- Data Breaches: Unauthorized access to sensitive data can result in costly breaches, regulatory fines, and customer loss.
- Free Usage Costs: Increased cost associated with free credit usage, ultimately increasing your total COGS.
- Reputation Damage: Security incidents undermine user trust, potentially leading to churn and lost business opportunities.
- Legal Liabilities: Regulations like GDPR, HIPAA, and CCPA require businesses to take adequate measures to protect user data. Failure to verify email addresses could result in non-compliance and steep penalties.
By winning over cross functional teams with this framing, you’ll make it easier to secure buy-in for email verification initiatives.
Conclusion
In B2B and multi-tenant application landscapes, email verification is not optional—it’s a fundamental requirement for security, reliability, and user trust. By implementing robust verification methods, you protect your users, their organizations, and your own platform from a wide range of threats.
Ready to implement enterprise-grade auth? Stytch offers a comprehensive suite of auth and fraud preventions methods, whether it's email magic links, email OTPs, OIDC SSO, SAML SSO, or even our device fingerprinting product.
If you have questions about our features, pricing, customer support, or anything at all, feel free to schedule a call with an auth expert.
Build B2B Auth
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.