Back to blog
What is fraud prevention?
Auth & identity
Nov 3, 2023
Author: Stytch Team
As we navigate the complexities of the digital age, the importance of fraud prevention for businesses has only increased. But what is fraud prevention and detection in the context of today’s complex, high-stakes environment, and how has it evolved?
Today, artificial intelligence (AI) and machine learning are not only tools for growth but also instruments for fraudsters’ sophisticated schemes, posing new threats. And while not every threat is a Walter White to an organization’s reputation, it pays serious dividends to set some guardrails.
Let’s delve into fraud prevention and the various types of fraud, highlighting how businesses can arm themselves against an ever-evolving risk landscape.
Table of contents
- What is fraud prevention and detection, and why should it matter to businesses?
- Foundational fraud prevention and risk management considerations
- Breaking bad actors: fraud prevention tools to consider for the AI era
What is fraud prevention and detection, and why should it matter to businesses?
Fraud prevention: anticipating threats
At its core, fraud prevention refers to strategies and solutions put in place to avoid fraudulent activities before they occur. In an age where online transactions have become the norm, the need for advanced fraud prevention is more critical than ever. Cybercriminals are constantly finding new ways to commit fraud – from identity theft to credit card fraud, and now fraud both enabled by and targeting AI applications – making it imperative for businesses to stay one step ahead.
At a high level, fraud prevention for organizations encompasses various measures, tools, and best practices designed to identify and reduce the risk of fraudulent transactions. This involves not just technical solutions but also policies and procedures that help prevent fraud from infiltrating business operations. The ultimate goal is to protect the financial assets, personal information, and trustworthiness of businesses and their clients.
Fraud detection: mitigating risks in real time
Fraud detection plays an additional critical role in combating cyber threats, working hand-in-hand with fraud prevention measures to strengthen overall security. While fraud prevention focuses on preempting fraudulent activities, fraud detection aims to identify these activities as they occur or even after they’ve taken place. Advanced fraud detection systems use complex algorithms and machine learning to recognize patterns of behavior that are indicative of fraud.
Implementing timely and effective fraud detection and prevention together is vital to minimizing the potential damage caused by fraudulent transactions. While fraud prevention and fraud detection serve different purposes, their integrated applications form a robust defense against the multifaceted challenges of cybersecurity.
Recognizing types of fraud

Recognizing various types of fraud is the first step in building an effective fraud prevention strategy. Common forms include:
- Identity theft: This occurs when fraudsters obtain and use someone’s personal information for gain. From securing loans to purchasing items online, the repercussions for victims can be far-reaching.
- Credit card fraud: Criminals make unauthorized transactions using stolen credit card details. The ease of online shopping has only exacerbated this issue, calling for more stringent fraud detection mechanisms to secure credit card transactions.
- Bank fraud and money laundering: These sophisticated schemes can involve multiple parties and obscure money trails, often requiring significant investigative resources to unravel.
- Business email compromise (BEC): A high-impact scam, BEC involves fraudsters impersonating company executives or business contacts to mislead employees or customers into transferring funds or revealing sensitive information such as personal information.
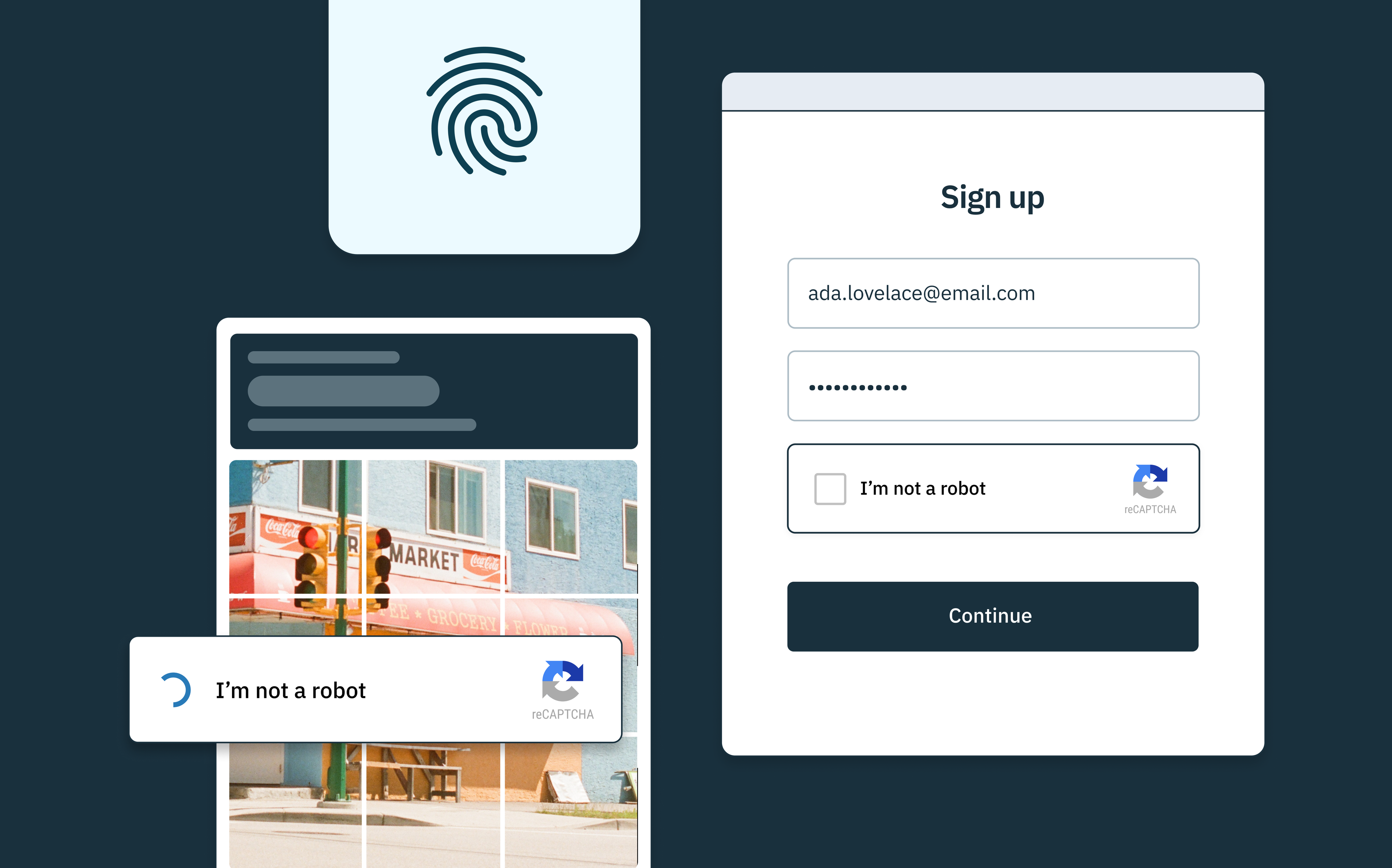
- Phishing: Criminals use phishing schemes to deceive users into revealing their personal and financial information. Strong authentication methods are needed to protect against these kinds of scams. To combat reverse engineering and increasingly potent phishing attacks in the AI era, businesses should consider advanced security technologies with stronger user access controls and more phishing-resistant forms of authentication.
- AI bot attacks: Increasingly common in the AI era, bot attacks are challenging AI companies (or companies relying heavily on AI) to implement effective bot detection and blocking mechanisms. They also need to monitor and protect against bot detection evasion techniques. For more on AI bot attacks, check out “Securing AI against bot attacks.“
These types of fraud underscore the need for a multifaceted approach to fraud prevention in the digital age, demanding collaboration across various business units and sometimes third-party services.
Want to stop fraud? Get Device Fingerprinting from Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Implementing effective fraud detection not only protects businesses from financial losses but also safeguards their reputation and customer trust. By proactively identifying and preventing fraudulent activities, businesses can maintain a secure environment for their customers to conduct transactions in – table stakes for any serious organization.
AI and the evolving threat landscape
Those stakes are undoubtedly higher in the current digital milieu. Fraudsters can create fake accounts, engage in business email compromise, and even utilize AI to mimic user behavior, blurring the line between bot and human, and complicating the process of detecting fraud.
Furthermore, companies increasingly need bot detection that protects APIs – often the secure barrier between sensitive data and malicious actors – from exposure to unauthorized bots.
In response to these emerging threats, businesses must continuously update their fraud detection and prevention strategies to stay ahead of the evolving tactics used by cybercriminals.
In addition to traditional methods of fraud detection, such as manual review and rule-based systems, businesses are increasingly turning to advanced technologies like artificial intelligence (AI) and predictive analytics. These tools enable businesses to analyze large volumes of data in real-time to detect fraud quickly and accurately. They also continuously adapt and learn from new information, making them highly effective at detecting emerging fraud patterns and techniques.
Foundational fraud prevention and risk management considerations
So where to begin in this multifaceted fight against fraud? While at Stytch we’re focused on equipping businesses with the right tech tools to combat fraud, it’s beneficial to begin with some strategic groundwork before you make any new technology investments to set your organization on the right path to effective adoption and utilization of such tools.
Five core areas of a defensive strategy
A comprehensive fraud prevention program is essential for any business seeking to safeguard its operations. At a high level, this might involve:
- Risk management strategies: Regular, comprehensive assessments to identify vulnerabilities within the system and determine the company’s risk appetite.
- Policies and procedures: Clear guidelines on handling sensitive information and financial transactions, as well as protocols for responding to suspected fraud.
- Internal controls: Checks and balances, such as segregating duties and setting up approval processes for transactions.
- Employee training: Regular sessions to educate staff on the latest fraud trends and the role they play in preventing fraud.
- Customer due diligence: Procedures to verify the identity of customers and assess the risk of potential fraud.
By implementing these elements, businesses can establish a solid foundation to combat the multifaceted threat of cyber fraud. But in addition to internal controls, organizations must comply and collaborate with regulatory bodies – and perhaps consider insuring themselves – to create an environment where inevitable security missteps won’t prove destructive.
The need for regulatory compliance

Consistent adherence to regulatory compliance plays a crucial role in fraud prevention. It’s not just as a legal obligation – it’s a strategic tool for business growth and sustainability.
Businesses need to be keenly aware of the regulations related to data security and fraud in their specific industry. Compliance with these regulations not only helps in reducing the risk of fraud but also protects the business from potential legal implications. Moreover, regulatory bodies often provide guidelines on best practices for fraud detection and prevention, which can serve as a valuable resource for businesses.
Failing to adhere to regulatory compliance can have disastrous consequences for businesses. Penalties can range from hefty fines to loss of licenses, and in severe cases, they may face lawsuits or criminal charges.
Additionally, non-compliance can severely tarnish a business’s reputation, eroding customer trust and loyalty. Businesses may also lose their competitive edge as regulatory compliance often means adopting the latest security technologies and practices, which can enhance overall business efficiency and performance.
Cyber insurance policies
Businesses should consider investing in cyber insurance policies as an added layer of protection against financial loss in the event of a security breach. These policies can help cover expenses such as legal fees, public relations costs, and lost revenue.
In the case of a security breach, businesses should have protocols in place for notifying affected customers and addressing their concerns. Transparency and effective communication are crucial in maintaining customer trust, risk management, and mitigating potential damage to the business’s reputation.
Institutional collaboration: joining forces against fraud
Combating cyber fraud isn't a solo endeavor. Collaboration between businesses, financial institutions, and government agencies can enhance fraud prevention and detection efforts. Sharing information about emerging threats, known fraudsters, and effective prevention techniques can fortify individual defenses, creating a united front against cyber fraud.
Furthermore, working together can help identify patterns and trends across industries, leading to more comprehensive and effective fraud prevention strategies. By pooling resources and knowledge, organizations can better protect themselves and their customers from fraudulent activities.
Breaking bad actors: fraud prevention tools to consider for the AI era
With the rise of emerging technologies such as blockchain and biometrics, businesses must stay current on these technologies and incorporate them into their fraud prevention arsenal. By being proactive in adopting them, organizations can future-proof themselves against fraudulent activities.
Unphishable authentication solutions
Unphishable authentication solutions aim to counteract phishing attempts that trick individuals into revealing sensitive information like passwords. By removing the traditional password element or adding extra layers of security, these methods greatly reduce the risk of account breaches due to phishing.
Some prominent strategies of unphishable authentication solutions include passwordless methods like biometric verification and magic links, which eliminate the traditional password vulnerability; Multi-Factor Authentication (MFA) that enhances security by requiring additional verification elements, ranging from physical devices to biometric confirmations; and passkeys and Single Sign-On (SSO) solutions that provide secure, centralized access to multiple platforms, reducing the reliance on multiple vulnerable password points and simplifying user experience while maintaining a high security level.
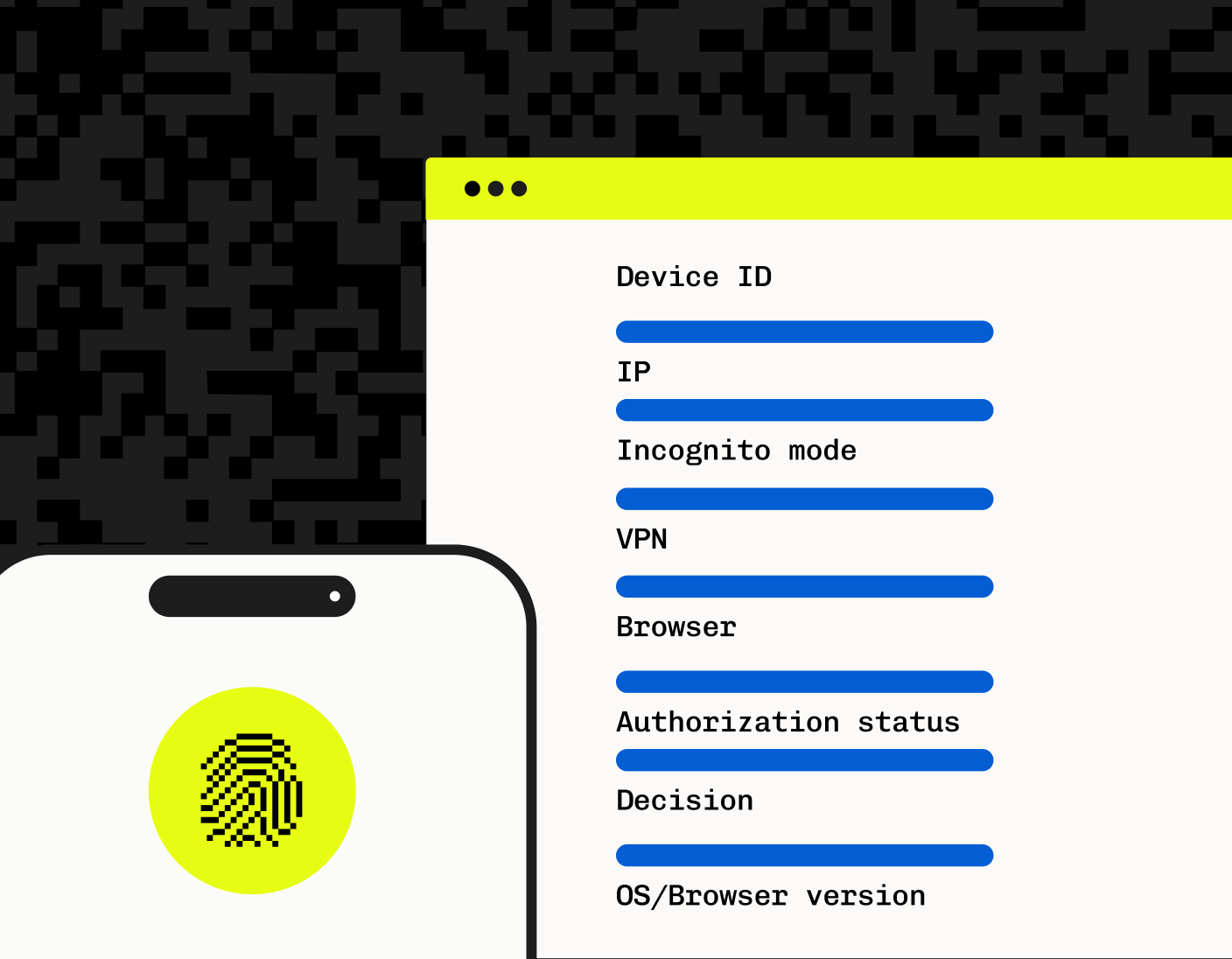
Device fingerprinting
Device fingerprinting is a technique for identifying individual devices based on a combination of information, such as browser type and version, operating system, IP address, installed fonts, and more. This unique fingerprint enables organizations to pinpoint authentic users from malicious actors and detect suspicious activities, even if fraudsters change their IP addresses or use VPNs.
Stytch’s Device Fingerprinting provides a set of customizable tools for your business to accurately identify devices. Stytch’s device fingerprints remain stable across incognito browsing, webviews, VPNs, changes to user agent or IP addresses, and more.
Stronger access controls
Closing the door to unauthorized access can be challenging, but Time-based One-Time Passcodes (TOTP) that involve short-lived, automatically generated codes and offer temporary access can significantly reduce the risk of unauthorized access. They are one of the most commonly deployed and effective methods.
Additionally, a more complex CAPTCHA – the challenges users must solve to prevent bots from accessing websites and applications – can be another powerful layer of security. Unlike conventional CAPTCHAs which can often be bypassed by bots, StrongCAPTCHA by Stytch employs complex problem-solving tasks that are easy for humans but challenging for bots.
All these solutions and tools are ideal ways to tackle some of the most common emerging threats depending on the level of threat risk and sophistication your organization is confronting.
For more insights on enhancing your fraud prevention strategies, explore the wealth of resources available on the Stytch blog, or talk with an auth expert at Stytch today.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.