Back to blog
Authentication as a service: Launch faster with stronger security
Auth & identity
Mar 28, 2025
Author: Stytch Team
Secure authentication is essential for any modern user-driven app or B2B SaaS tool. Authentication is difficult to build securely and quickly without putting user data and your infrastructure at risk; and when you start growing and have to factor scalability, the challenges of maintaining authentication developed in-house can become even more complex.
That's where authentication as a service (AaaS) comes in: it's an authentication platform that you can build on, providing an evolving toolkit of industry-standard, best-practices security technologies that are developed, tested, and maintained by teams of authentication, security, and identity management experts.
What is authentication as a service (AaaS)?
Authentication as a service provides identity-related technologies for your applications which includes a whole suite of features like user registration, login methods, session management, user management, authorizations, and more. Many AaaS platforms also provide additional management and security features such abuse and fraud prevention and bot detection to protect your applications and services, further reducing the development overheads required to fully secure your applications.
These solutions are cloud-based, providing highly available and secure login systems for many popular applications. Many AaaS solutions can also be integrated with an organization's identity and access management (IAM) systems like Microsoft Entra ID, Google Workspace, and Okta.
What are the benefits of authentication as a service?
Authentication as a service greatly reduces the development time and effort it takes to implement user registration and login functionality in your applications by providing strong security technologies that are designed, coded, and maintained by experts.
When choosing an AaaS provider, it is important that you assess whether it includes features that benefit both your development team, your business, and your end-users.
A better developer experience
AaaS platforms equip your engineering teams with a comprehensive set of tools to accelerate their development of auth and identity features. With APIs, SDKs, and pre-built UI components, developers can implement best-practices authentication with just a few lines of code.
curl --request PUT \
--url
https://test.stytch.com/v1/b2b/organizations/{ORGANIZATION_ID} \
-d '{
"allowed_auth_methods": ["sso"],
}'This allows you to focus on building the bespoke functionality of your apps, rather than trying to solve sensitive security issues.
Support for a wide variety of auth methods
AaaS platforms integrate with popular identity providers (such as Google, Apple, and Microsoft ), and provide a wide variety of auth methods for login like passwords, magic links, and OAuth — in addition to multi-factor authentication options like using one-time passwords (OTPs), authenticator apps, and biometrics like WebAuthn/passkeys.
This ensures that your users have a convenient, familiar login experience that discourages poor security practices like password sharing and weak passwords, without adding friction to your signup and login flows.
Enterprise features
Enterprise-grade authentication as a service also provide developers with tools and features such as:
- Multi-tenancy, enabling you to securely build SaaS platforms or add authentication to B2B applications with isolated org-level access and configuration.
- Single sign-on (SSO) for seamless authentication across different services and internal business tools
- System for cross-domain identity management (SCIM) for maintaining identity and access information.
- Role-based access control (RBAC) for applying identity and access information to secure data and resources.
- Machine-to-machine (M2M) authentication, to enable secure service-to-service communication without human involvement.
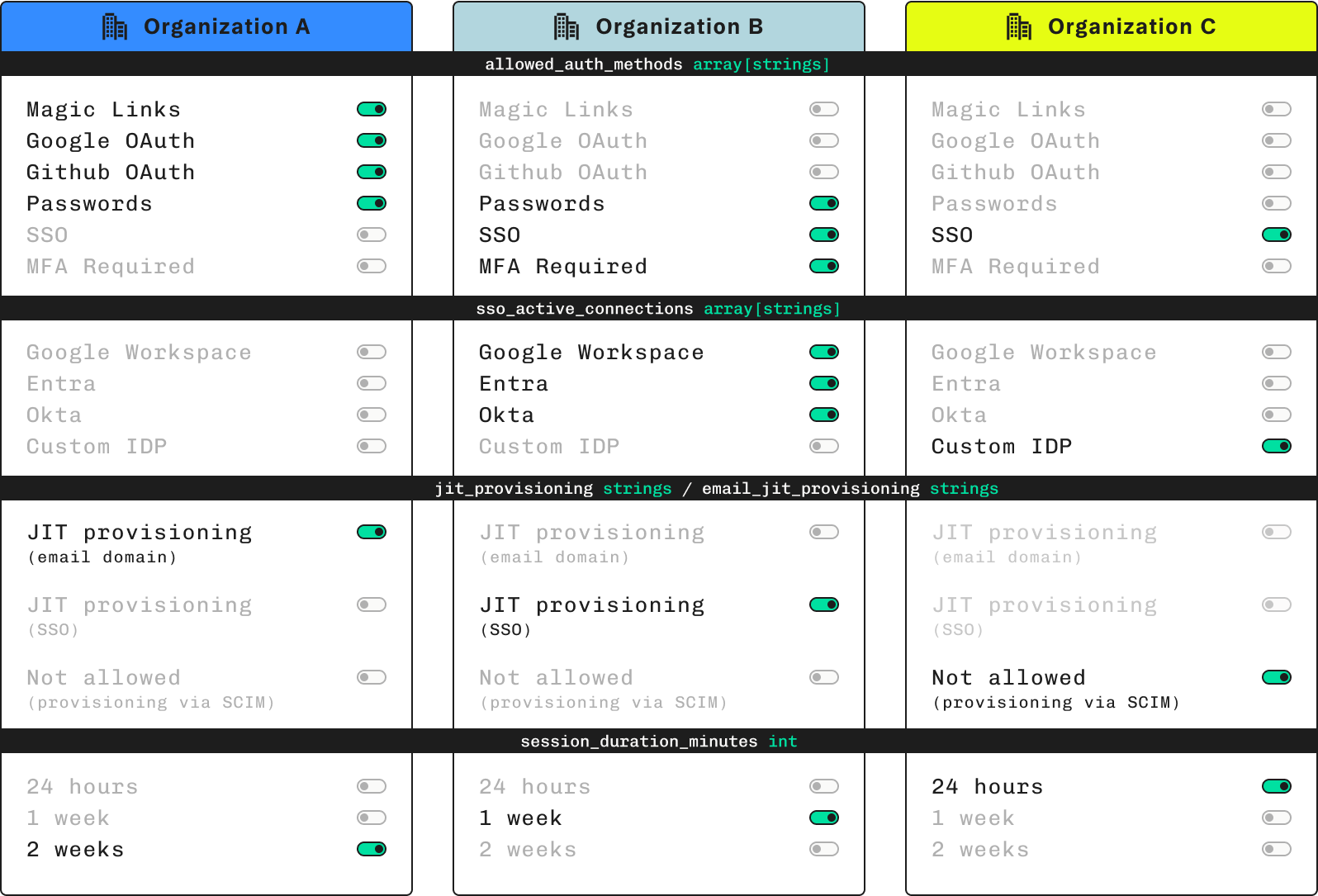
Other essential features such as support for protocols like SAML, OIDC, and JIT provisioning are also often included in enterprise AaaS plans. Enterprise-ready authentication will also have a proven history of security and disclosure, along with additional developer support and service level agreements (SLAs).
Compliance and regulations
Authentication as a service helps you stay compliant with data privacy regulations such as GDPR, CCPA, and HIPAA, as well as more stringent certifications like ISO 27001 and SOC2 for highly sensitive user and financial data.
AaaS platforms that comply with these standards and regulations are critical in enterprise environments, as they are incredibly difficult to implement without dedicated security professionals.
Scalable infrastructure and availability
The reduced infrastructure requirements of AaaS results in lower costs and higher scalability of your applications. When unexpected growth happens, your application won't fall over due to an influx of user registrations or run up your cloud hosting bills
Fraud and risk prevention
Improved security reduces the risk of your apps exposing users to fraudulent activity, maintaining and enhancing your business's reputation for respecting the safety and privacy of your users.
AaaS platforms should provide fraud and risk prevention solutions to detect bots, prevent abuse, and defend against emerging threats—including AI-driven fraud, helping secure your users with new technologies at zero development costs.
How does authentication as a service help developers?
Secure user authentication can no longer rely on basic username and password pairs, and it is becoming increasingly complex to implement security measures that provide adequate security.
Authentication as a service provides an evolving set of developer tools for building scalable, complex identity systems for their products. With AaaS, you can add sophisticated authentication and security protection to your applications without additional development burden to your projects.
The APIs and SDKs provided by AaaS platforms include everything you need to interact with their authentication services, handling everything from front- and back-end implementation to embeddable admin portals, all while following programming and security best practices.
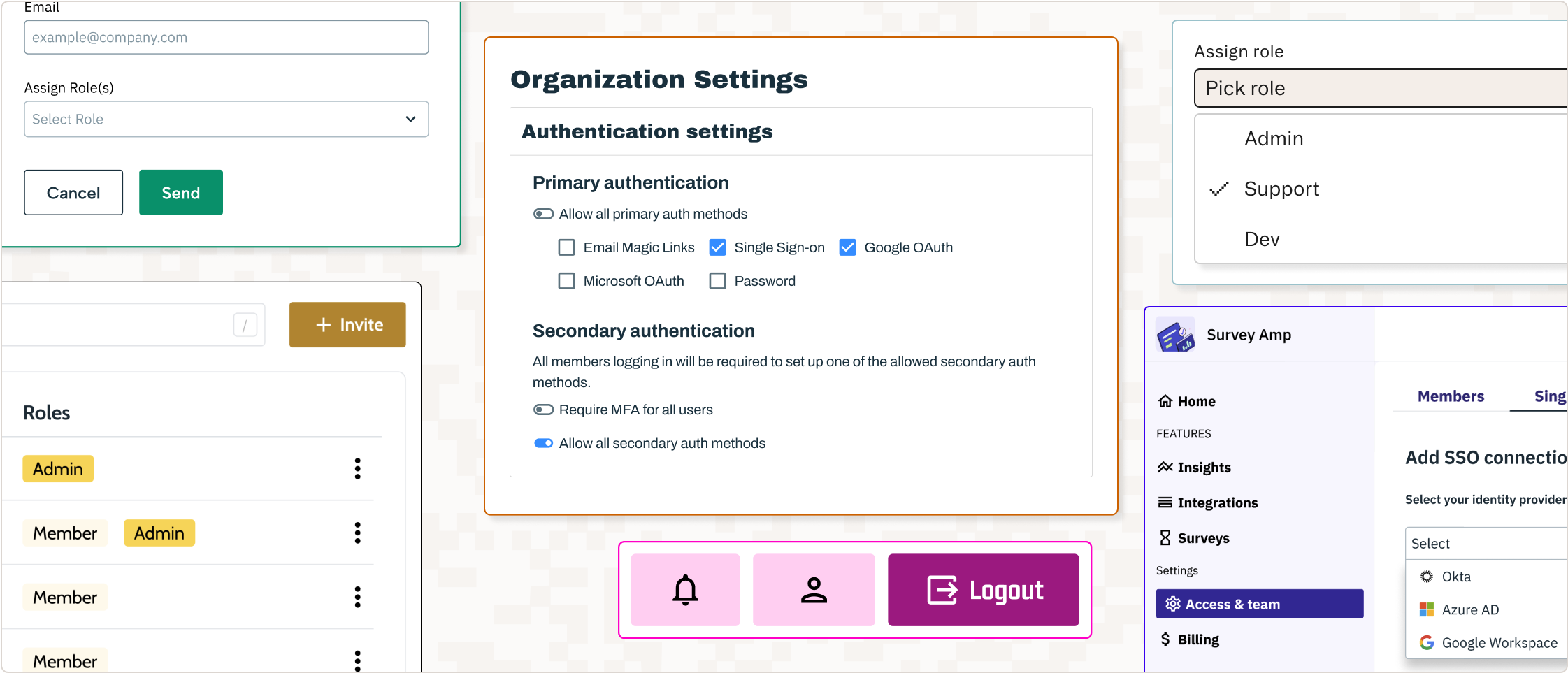
For example, Stytch AaaS integrates with any software project using comprehensive SDKs, as well as directly through APIs and industry standard protocols OAUTH and SAML, immediately adding strong authentication and protection to any app or service.
Case study: Smooth user authentication and app protection with AaaS
AaaS is a proven force multiplier for development teams, increasing efficiency and providing better outcomes.
ClearBit, recently acquired by HubSpot, is a leading B2B AI provider who needed an authentication layer that would provide granular control of enterprise B2B authentication, self-serve onboarding for their growing user-base, and built-in device fingerprinting to combat account and trial abuse. They also required enterprise features like RBAC that would ensure their chosen solution was future-proof as their needs evolved.
We knew we needed to upgrade our in-house auth, and that would be a big undertaking. So having a partner who was thinking through these problems for us and could allow us to be more lean was a lot of the motivation in moving to Stytch.
We knew we needed to upgrade our in-house auth, and that would be a big undertaking. So having a partner who was thinking through these problems for us and could allow us to be more lean was a lot of the motivation in moving to Stytch.
Stytch met (and surpassed) every requirement, reducing the overheads of supporting complex in-house authentication systems and enabling a passwordless self-service onboarding process for their users.
Stytch’s multi-tenant architecture provided Clearbit with the infrastructure to easily build and manage key enterprise auth features such as SAML authentication, integration with OAuth providers, and auto-provisioning. Enabling different auth requirements and settings for different customers was simply an API call away via the Stytch platform.
Adding best-in-class authentication to your app
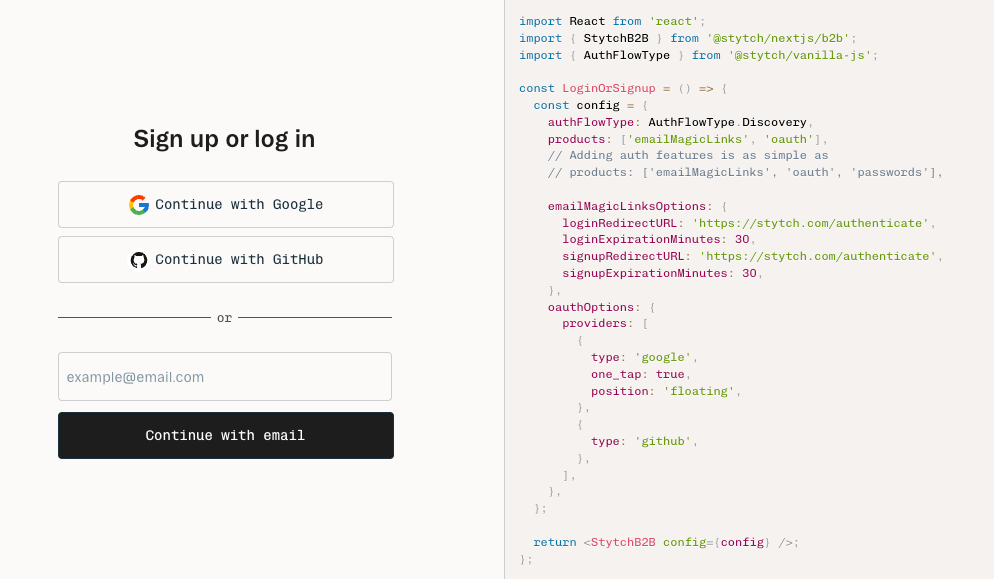
Authentication as a service makes building secure applications easier by abstracting the complexity and dangers of implementing authentication away from your developers, so that they can focus on creating functionality and content for your users.
Adding Stytch authentication and fraud prevention to your app is a straightforward process:
- Sign up with Stytch.
- Configure your identity providers, including popular social login providers like Google and Microsoft, or use your own in-house identity providers like Microsoft Entra ID, Google Workspace, and Okta.
- Add Stytch to your app using our SDK and pre-built UI, or build your own with our headless implementation. Depending on your architecture, you can also implement Stytch using our backend SDKs.
// Adding Stytch authentication to a React app
import React from 'react';
import { StytchB2B } from '@stytch/nextjs/b2b';
import { AuthFlowType } from '@stytch/vanilla-js';
const LoginOrSignup = () => {
const config = {
authFlowType: AuthFlowType.Discovery,
products: ['emailMagicLinks', 'oauth'],
emailMagicLinksOptions: {
loginRedirectURL: 'https://stytch.com/authenticate',
loginExpirationMinutes: 30,
signupRedirectURL: 'https://stytch.com/authenticate',
signupExpirationMinutes: 30,
},
oauthOptions: {
providers: [
{
type: 'google',
one_tap: true,
position: 'floating',
},
{
type: 'github',
},
],
},
};
return <StytchB2B config={config} />;
};
4. Leave the complicated stuff to us and get on with building the rest of your application.
Full, working code examples and Stytch demos are available to help get you up and running quickly, and our thorough documentation is regularly updated as we add new features.
Authentication is hard. Leave it to the experts.
Along with being an ongoing security and privacy responsibility, designing and implementing authentications solutions is a significant undertaking for development teams of any size, distracting you from building your core value for your users.
Integrating Stytch into your consumer and B2B applications gives you immediate access to industry standard multi-factor authentication and compliance functionality, enterprise features such as RBAC and SCIM, as well as innovative technologies such as AI protection and intelligent bot detection.
This can all be achieved using our APIs and SDKs, significantly reducing development time, code complexity, and placing the responsibility for the security and maintenance of your login systems with Stytch cybersecurity experts. Contact Stytch to find out more, or get started yourself now for free.
Build with Stytch
APIs and SDKs for authentication, authorization, security and fraud prevention
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.