Back to blog
What are one-time passcodes (OTPs)?
Auth & identity
Feb 10, 2023
Author: Stytch Team
As developers step up security measures to evade the latest cyber threats, they’re adding a range of innovative authentication and identity management solutions to their sign up and log in flows.
One of the strongest tools in their modern arsenal is the one-time passcode (OTP), also sometimes referred to as a one-time password.
Below, we explain what OTPs are, how they work, and why they best traditional passwords when it comes to offering a more robust security profile with a smoother user experience.
What are OTPs, exactly?
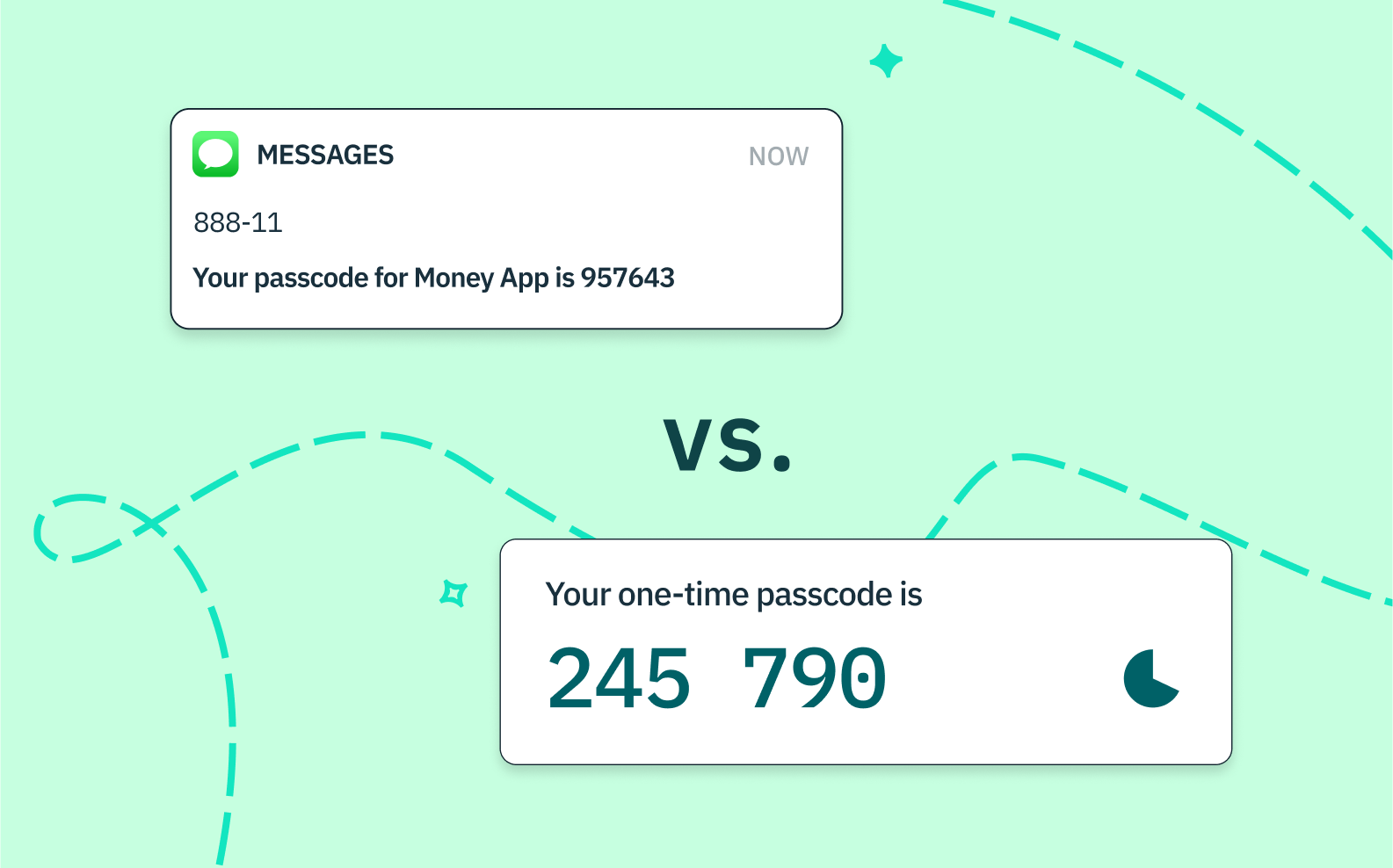
OTPs are security codes that are automatically sent to a user’s phone number or email address upon a sign up or log in attempt. They typically contain a randomly generated string of numeric or alphanumeric characters that a user must input to verify their identity and gain access to or carry out sensitive actions within an app or website.
As the name suggests, a one-time passcode can only be used once — that is, for a single authentication event. After a given code is entered, it is invalidated and cannot be used again.
What are different types of OTPs?
There are several different categories of OTPs, which are defined by the communication method involved. The most common forms include:
Email one-time passcodes
Email OTPs are sent to a user’s registered email address and can be accessed via their inbox on a desktop or mobile device.
SMS one-time passcodes
SMS OTPs are sent via text to a user’s registered phone number. While typically received through a mobile device, they can also be accessed on a computer using a messaging app like iMessage.
WhatsApp one-time passcodes
WhatsApp OTPs are sent through the WhatsApp messaging service, an app used by over 3 billion people worldwide. They’re a popular option for developers and platforms with a global user base, as they avoid the deliverability issues that can arise when sending text messages internationally.
How do OTPs work?
OTPs are considered something-you-have authentication, because codes are sent to a specific phone number or email address and must be accessed via a messaging app or inbox that is in the user’s possession.
In practice, OTPs generally follow a simple progression:
- A user attempts to sign up for or log in to an app or website, initiating a verification request.
- The back-end server generates a unique, random code, which is sent to the user’s registered phone number or email address.
- The user accesses this code and enters it within the app or website to gain access.
- If correct, the server validates the code, and the user is granted access.
- The code is invalidated, preventing its future use.
Using OTPs in an MFA flow
Because of their ease and flexibility, OTPs can be used as a primary authentication factor or as a secondary factor in a two-factor authentication (2FA) or multi-factor authentication (MFA) flow. That means they can stand on their own or be combined with one or more other authentication methods, like OAuth logins, biometrics, or even traditional passwords.
MFA takes a layered approach to verifying a user’s identity and role-based permissions, boosting an app’s overall security. Auth factors can be grouped together and front-loaded at the initial login or dispersed throughout the user journey in a process known as route-based (or just-in-time) authentication.
With this approach, additional auth factors are only required when a user wants to perform a particularly sensitive task — like changing payment details or making a purchase — introducing extra friction only when it’s needed.
Want secure OTPs for your app? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
How are OTPs different from traditional passwords?
While one-time passcodes are sometimes referred to as “one-time passwords,” one of the most distinguishing (and advantageous) qualities of OTPs is that they are completely passwordless.
In fact, OTPs differ from traditional, static passwords in two key ways that boost both their safety and their usability. Let’s explore them one by one.
Stronger security
Passwords are the single most dangerous element in cybersecurity today. According to one recent report, 82% of all online data breaches involved the “human element” of authentication — in other words, weak, shared, or stolen passwords.
Unlike traditional passwords, however, OTPs:
- Cannot be predicted: With OTPs, each new string of characters is randomly generated, so it’s unlikely to contain easily guessable information like a user’s birthday or pet name. It’s also impossible to guess what the next passcode will be based on past examples.
- Cannot be reused: A static password remains fixed until it is changed by the user — so if a hacker intercepts it, they can enjoy ongoing access to that user’s account. But each one-time passcode is unique and can’t be used beyond a single login session.
- Cannot be repeated: 85% of users admit to repeating the same password across multiple sites and apps, putting all accounts at risk if a password is intercepted. OTPs, on the other hand, are generated for a specific platform and can’t be applied across accounts.
That makes OTPs more resistant to common cyber attacks that target password-based authentication, like credential-stuffing, password spraying>, and account takeovers.
Frictionless UX
On top of security concerns, passwords are just plain stressful. In a recent study, 75% of users reported feeling anxious about the number of passwords they’re expected to remember across many online accounts.
What’s more, passwords are bad for business. 65% of consumers say they’ve abandoned a website or app because the process of creating credentials was too complex — and 92% would rather give up than have to recover or reset a forgotten password.
The user experience of OTPs is comparatively frictionless. Unlike traditional passwords, OTPs:
- Are accessible: OTPs often come in the form of 6- or 8-digit codes, so they’re easy to remember. Besides, they’re typically right in front of a user in a readable text or email.
- Are automatically fillable: Auth providers like Stytch offer auto-fill capabilities for OTPs sent to Android or iOS devices, so a user doesn’t even have to navigate away from an app to enter them.
- Are flexible: OTPs can be seamlessly inserted anywhere in an authentication flow or user journey as a secondary factor, adding extra security without extra hassle.
Thanks to their ease of use, OTPs promise not only greater protections, but greater conversion rates, as well.
Potential drawbacks of OTPs
Like many authentication methods, OTPs aren’t absolutely foolproof, even when used as a secondary factor in an MFA flow.
Why? The short explanation is that any auth factor tied to a user’s phone number or email address can be compromised by a skilled hacker. For one thing, OTPs are sent as unencrypted plain text, so any communication that can be intercepted and read by a malicious actor — through rare but viable tactics like SIM swapping> — potentially puts a passcode at risk.
Moreover, OTPs are also subject to phishing attacks. These are social engineering schemes, in which hackers send fraudulent emails or text messages that manipulate users into clicking on a bad link or unwittingly sharing a passcode.
That’s why auth experts recommend fortifying all MFA flows with unphishable factors to ensure top-notch security and outmaneuver even the most determined hackers.
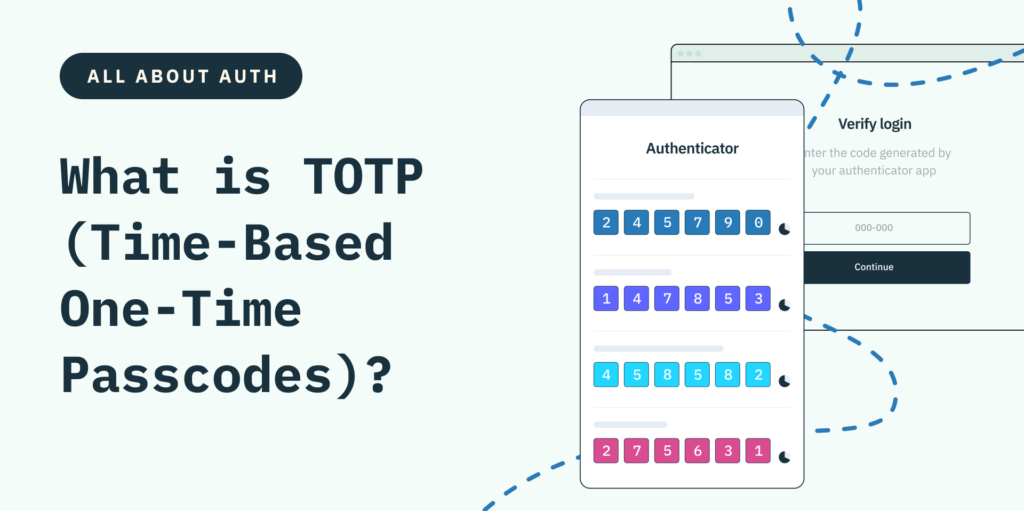
What are TOTPs?
Time-based one-time passcodes (TOTPs) are a newer, more advanced form of OTP often included as part of an MFA flow. They rely on authenticator apps — like Google Authenticator, Microsoft Authenticator, or Authy — to generate a random passcode that automatically changes every 30 or 60 seconds. That means a potential hacker has only a very short window to carry out an attack before a code is invalidated.
Additionally, unlike with original OTPs, authenticator apps are installed on and tied to a specific user device (rather than just their phone number). That means TOTPs can protect users against more sophisticated attacks like SIM swapping, while original OTPs cannot.
While TOTP provides stepped-up security, the time limitations means users need to be able to move fast to verify their identity and gain access to their desired app. Otherwise, they risk adding extra steps and friction to the login process. As a result, TOTP flows are typically reserved for highly risky actions or sensitive data — like moving money across fintech platforms or accessing a company’s payroll records.
Key takeaway
OTPs are a great option for modern developers who want to reinforce the security of their app or website without the inconveniences of passwords, and they work well as primary or secondary factors in a sign up or login flow.
Discover Stytch’s OTPs and TOTPs
Stytch offers flexible, frictionless One-Time Passcodes and advanced TOTP Authenticator Apps/a> as part of our comprehensive product suite.
If you want to learn more about how these or other solutions work, reach out to an auth expert to start a conversation — or sign up for a free account to try them out for yourself.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.