Back to blog
What is passwordless authentication?
Auth & identity
Feb 13, 2023
Author: Stytch Team

On the surface, passwordless authentication is a pretty straightforward concept. It's simply allowing users to access an online account, application, or website without the use of a password.
Under the surface, however, there's a lot going on. There are many different types of passwordless authentication factors, many different ways that passwordless login can be applied in an auth flow, and many different reasons why traditional passwords are no longer a secure or convenient way to verify a user's identity. Let's tackle these topics one by one — starting with the reasons why passwordless authentication is necessary in the first place.
What’s wrong with traditional passwords?
What isn't? Passwords made sense in the 1990s, when the internet first went mainstream. At the time, users had few online accounts, and remembering one or two simple credentials didn't pose a burden. Moreover, most users were not yet using the internet for highly sensitive activities like banking and commerce, so the stakes of a swiped password weren't quite as high as they are now.
Today, though, the average user has 100 passwords — far too many to remember outright. Since less than 23% of users employ a password manager, the vast majority use riskier methods to keep track of their proliferating credentials. According to a recent survey, 65% end up reusing the same password across multiple accounts, and 23 million still use “123456” as their password of choice. That has led to a situation where passwords are neither safe nor practical. Among other issues:
Passwords are easy to breach.
It's estimated that 82% of all online data breaches exploit the “human element” of cybersecurity — in other words, passwords that are easily guessed, stolen, or otherwise compromised. Passwords are considered something-you-know authentication, and anyone who knows one can gain access to every related account. Modern hackers have a variety of methods they can turn to — from malware and phishing scams to brute force attacks and credential stuffing — to intercept or crack a legitimate user's password and capture their sensitive data.
Passwords are frustrating.
On top of having to recall dozens (if not hundreds) of passwords, no one enjoys the drawn-out password recovery and reset processes they must follow if they happen to forget one. In fact, 92% of users report that they'd rather abandon an app or website altogether than undergo a password reset flow.
Passwords have gotten overly complicated.
In an attempt to offset the risks of weak credentials, many apps have imposed increasingly complex password creation rules. Many follow the LUDS formula, which requires a password to contain at least one lowercase letter, uppercase letter, digit, and symbol. In many cases, this leads users to make simple substitutions that are easy for bots to crack (like P@ssword1 or Password1!) or convoluted strings of characters (like I8*&YnFhyg) that are difficult for humans to remember — triggering even more password reset flows.
Passwords are arguably destroying the planet.
You may not think passwords have a big carbon footprint, but we calculated that a year's worth of password usage in the U.S. alone produces the greenhouse gas equivalent of 877,415 cars, due to the time (and energy) it takes to type in and reset credentials. All that said, auth providers like Stytch are improving on antiquated password models to bring them up to speed with modern expectations. More on that later.
How does passwordless authentication work?
Passwordless authentication is not one-size-fits-all. There's a wide variety of passwordless authentication factors, and each involves a different process and results in a different user experience. Some of the most common passwordless authentication methods include:
Magic links

With email magic links, users can sign up for or log in to an app or website with a click. They simply enter their email address when prompted, receive a unique, single-use URL in their inbox, and click on the link to instantly verify their identity. This form of passwordless authentication is considered something-you-have authentication, because the user must prove they have ownership of a specific, registered email address.
With embeddable magic links, these same unique URLs are embedded into marketing materials sent to a user via email, SMS, or other form of communication. Because the user is accessing these materials through their inbox or messaging app, clicking on the link necessarily demonstrates their possession of that email address or phone number.
One-time passcodes
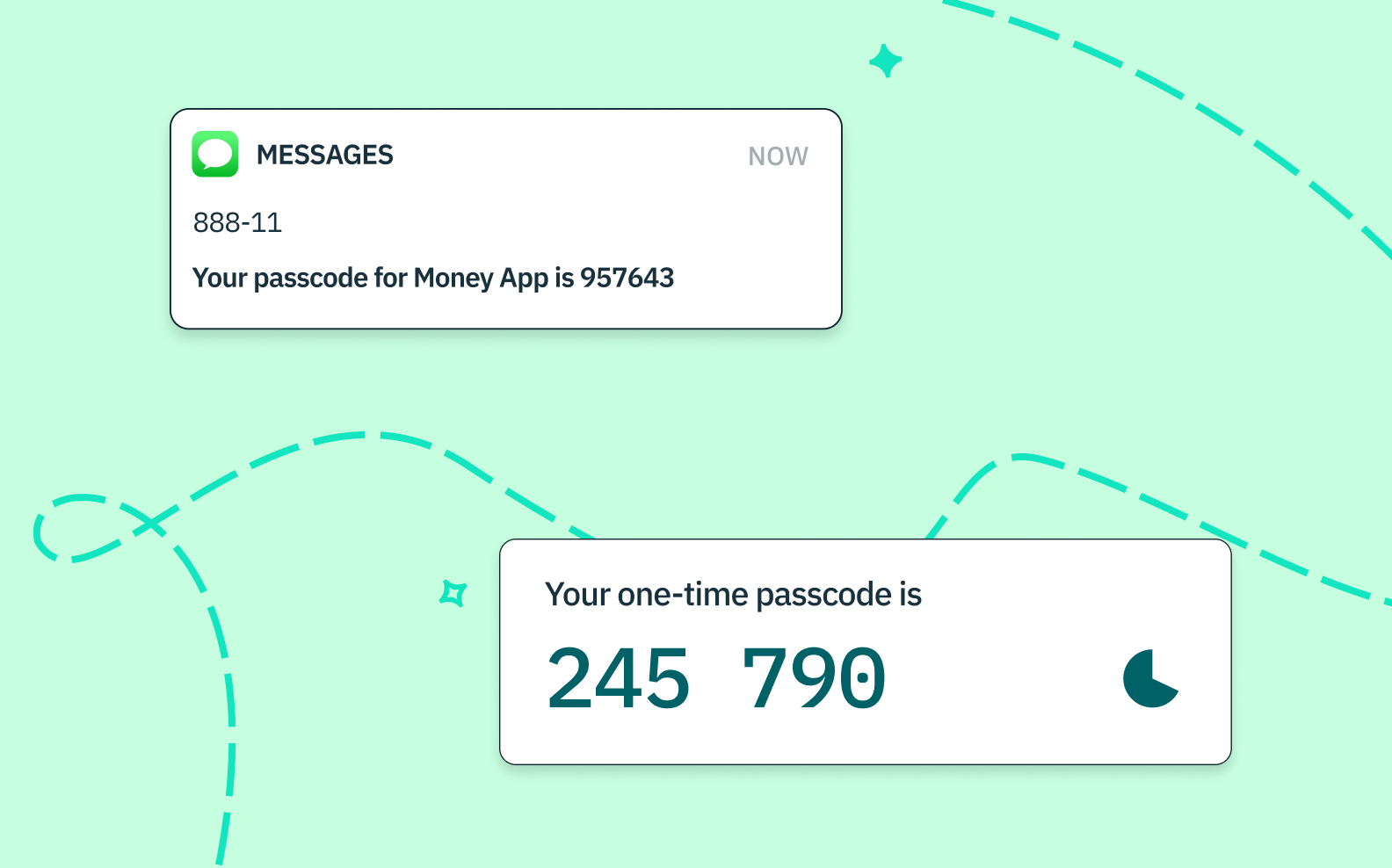
One-time passcodes (OTPs) are randomly generated security codes that are sent to a user's phone number or email address and accessed through an inbox or messaging app. As the name suggests, a one-time passcode can only be used once — or, for a single verification event. After a code is entered, it is invalidated and cannot be used again. Like magic links, OTPs are considered something-you-have type of authentication factor, as users must show they can access a given phone number or email.
Want to go passwordless? Switch to Stytch.
Pricing that scales with you • No feature gating • All of the auth solutions you need plus fraud & risk
Time-based one-time passcodes (TOTPs) offer a stronger version of OTPs for particularly sensitive apps or user activities. They rely on authenticator apps — like Google Authenticator or Authy — to generate passcodes that change every 30 or 60 seconds. That means a hacker has only a very short window to carry out an attack before a code is voided. Additionally, unlike OTPs, authenticator apps are installed on and tied to a specific user device (rather than just a phone number or email), so they can protect users against remote cyberattacks.
OAuth logins
OAuth logins allow users to leverage single sign on capabilities and access an app or website using a pre-existing third-party account. That means, if they have an active social account through Google, Facebook, Apple, or other platform — or an active dev account through Github, GitLab, or BitBucket — they can enter those credentials to verify their identity. Innovative options like Google One Tap take this one step further, detecting an already logged-in Chrome or Gmail session and allowing users to automatically apply those credentials.
Web3 logins

Much like OAuth, Web3 logins allow users to access an app or website using any existing Ethereum- or Solana-based crypt wallet. In addition, forward-thinking providers like Stytch are now offering encrypted, consumer-facing browser extensions — we call ours Vessel — that function like a passport to the internet, empowering users to navigate limitlessly online without ever having to manage another password, private key, or seed phrase.
Biometrics

Biometric authentication is considered something-you-are authentication, as they rely on physical attributes that are inherent to a user's body or behavior. Biometric tools are typically built into a device and are designed to scan, analyze, and recognize distinctive, measurable features — like a user's fingerprint, facial contours, iris/retina patterns, and voice qualities. Many biometric solutions are also equipped with liveness detection tools, so they can distinguish between a legitimate user and a reproduction (like a photograph or voice recording) in order to prevent fraud.
Historically, biometric data has been stored locally on a user's mobile device or laptop, making it impossible to transfer biometric logins across different devices and platforms. Next-generation solutions like passkeys, however, can now back up the cryptographic keys containing a user's biometric data to their cloud account, enabling smooth interoperability.
WebAuthn

Web Authentication API (WebAuthn) is one of the most exciting passwordless technologies on the market, building on advanced public-key cryptography. WebAuthn combines the layered security of multi-factor authentication (MFA) with the physical component of built-in biometrics or external security-key hardware like YubiKey.
This is by no means an exhaustive list, with passwordless authentication methods like push notifications, device fingerprinting, and CAPTCHA solutions also helping to detect bad actors like bots, prevent fraud, and manage legitimate user access.
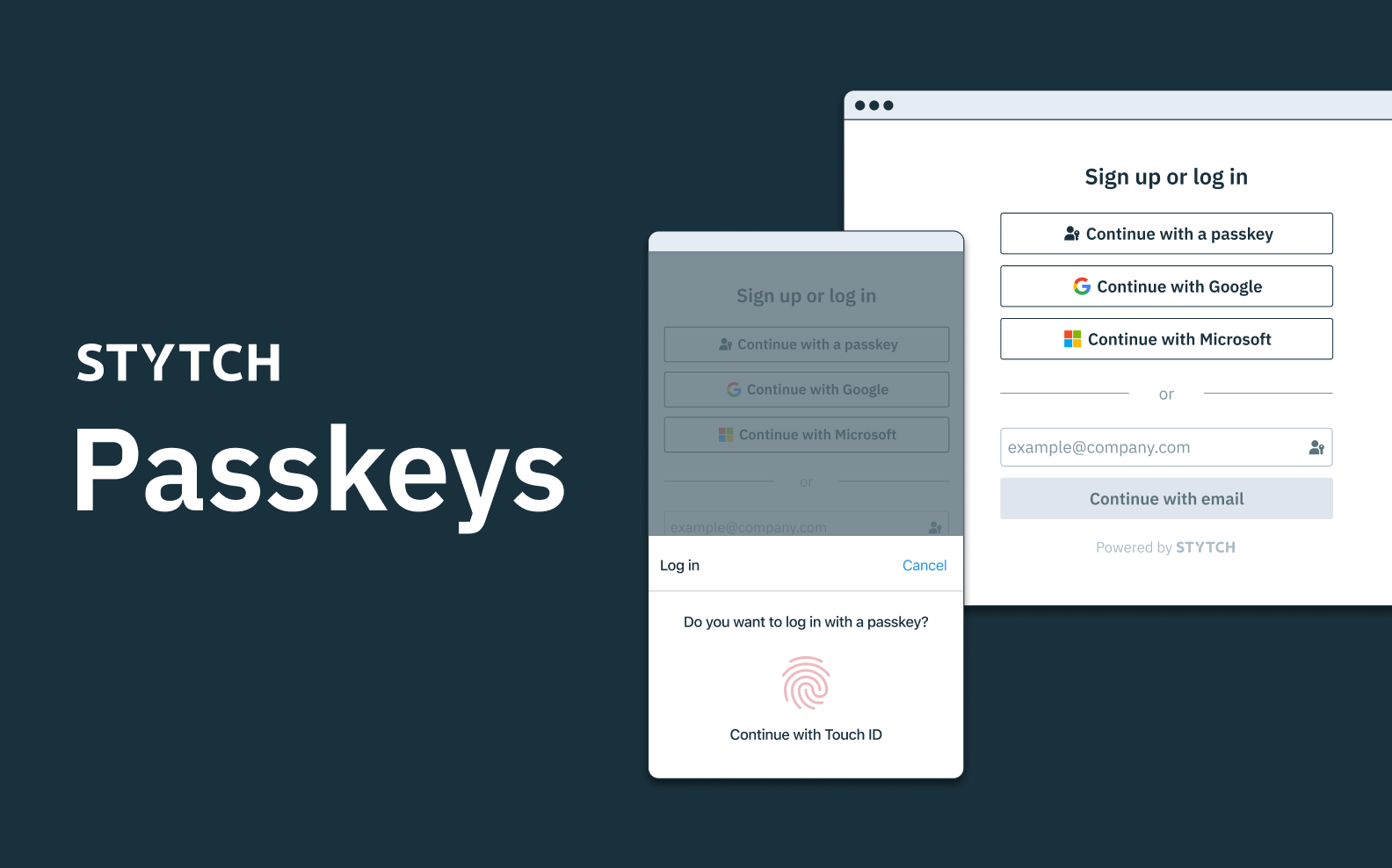
Passkeys
Passkeys are a new evolution built on WebAuthn, with some key improvements. While WebAuthn pioneered the concept of a single-device passkey (i.e. a single hardware key or a biometric validation tied to your mobile device or laptop), “passkeys” as we're discussing here refer to multi-device passkeys and introduce a few major UX and developer improvements:
- They are a drop-in replacement for passwords.
- They are cross-device, cross-platform, and cross-ecosystem.
- Enrollment and login credentials with a passkey leverages UX patterns made familiar by password managers.
- For higher security contexts, passkeys can discern between existing and new devices attempting to access an account.
While passkeys have a couple of infrastructural hurdles to clear before they become widely available, it's Stytch's firm prediction that passkeys will be a tipping point in helping companies and users alike make the full transition into a passwordless future.
What's the role of multi-factor authentication in the world of passwordless?
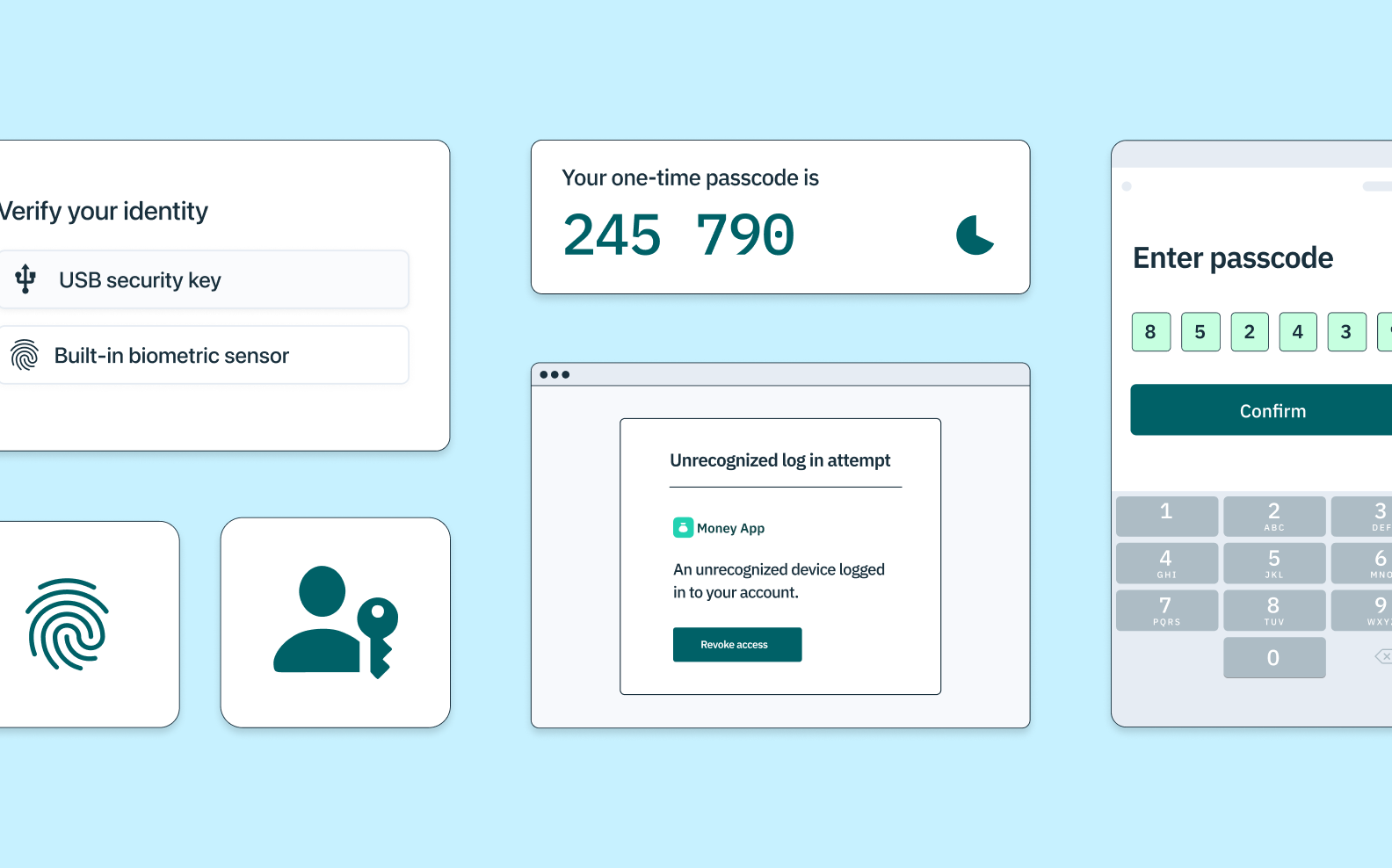
Multi-factor authentication (MFA) is a layered approach to confirming a user's identity when logging into an app or web service. Whereas many authentication flows today only consist of one factor (like a username and password), multi-factor authentication will ask a user to use at least one additional authentication factor – like the answer to a security question, or a one-time passcode.
Though the passwordless authentication methods described above are generally more secure than passwords (can't be reused, harder to steal), each still comes with its own vulnerabilities. That's why at Stytch we not only recommend going passwordless, but also implementing them as part of a multi-factor authentication process. MFA helps ensure that if one authentication method is compromised, your user's accounts are still protected.
The benefits passwordless authentication solutions
There are many advantages to eliminating passwords from your authentication flows. Some of the most notable benefits include:
Passwordless authentication is more secure.
As noted above, passwords are the most common and vulnerable target for capable hackers, and taking them out of the equation bolsters an app's protections exponentially.
Passwordless authentication is more efficient.
Passwordless authentication flows often allow users to log in with a single click — and to avoid lengthy, multi-step password reset processes. For developers, they slash the time it takes to record and respond to log in issues, error tickets, and security risks. Some studies estimate that around 40% of all help desk calls are related to password resets.
Passwordless authentication is more cost-effective.
Similarly, research suggests that each password reset flow costs upwards of $70 in lost productivity and support time. In total, the average organization stands to lose around $5.2 million each year due to the inconveniences of passwords.
Passwordless authentication gives a better user experience.
Passwordless authentication flows are faster and friendlier, ultimately driving better user experiences, engagement rates, and lifetime value. For example, one Web3 mobile wallet platform jumped to 80%+ conversion rates at onboarding after integrating with Stytch's frictionless One-Time Passcodes.
Potential drawbacks of passwordless authentication factors
While passwordless authentication is popular among both users and developers, there can be shortcomings when it comes to implementation, including:
- Access: Many passwordless auth methods require users to verify their identity using a separate account, application, or physical device, which may not be readily available.
- Interoperability: As mentioned, some forms of passwordless authentication — like native, built-in biometrics — aren't able to travel across different platforms or devices.
- Complexity: Many users are still unfamiliar or uncomfortable with the idea of passwordless authentication and may hesitate to install a related application or extension on their device.
- Security: While safer than passwords, passwordless methods aren't 100% foolproof on their own. Any factor that is tied to a user's phone number or email address can be intercepted by a determined hacker through strategic phishing or SIM swapping, and even robust factors like biometrics can be compromised by successful spoofing. That's why experts recommend investing in MFA to keep up with and outsmart the most sophisticated attacks.
Not all apps (or their users) are ready to take the leap into a fully passwordless experience. Nonetheless, adopting passwordless auth isn't an either/or proposition. It's easy to add a passwordless option as a seamless primary or secondary factor in an existing auth flow and still enjoy all of the associated UX and security benefits.
Is it difficult to implement passwordless authentication?
No. The truth is, many companies don't realize that they're already relying on passwordless authentication. They call it a password reset flow. Password resets are really just an overly complicated email verification flow, with a requirement to create a new password tacked on at the end. Remove that, and you're left with an easy email magic link — so why not trim all the excess steps and offer a streamlined (but equally secure) experience?
Not all passwords are bad
It's worth noting that passwords aren't inherently evil, they just haven't been properly updated and upgraded to address the latest cybersecurity threats and user expectations. Stytch offers a modern Passwords solution for companies that (for whatever reason) still need or prefer to offer traditional sign up and log in factors as part of their auth flow. Unlike conventional passwords, however, ours feature next-level breach detection, strength assessment, deduplication measures, and intuitive, human-first reset options to give users the smooth experience they're looking for, plus the peace of mind that comes with stepped-up security.
The bottom line
There are good reasons why traditional passwords are on the way out, and why a completely passwordless internet is the way of the future. Fortunately for today's businesses and developers, there's a variety of advanced passwordless factors and flows that are easy to implement and to use, making them a promising path to stronger security, better user experiences and engagement, and greater overall value.
Discover Stytch's passwordless product suite
Stytch offers a range of frictionless passwordless solutions — including one-click Email Magic Links, instant One-Time Passcodes and seamless OAuth Logins — as part of our integrated product suite, which can be fully customized to your needs. If you want to learn more about how these or other flows work, reach out to one of our auth experts to start a conversation — or sign up for a free account to try our platform out for yourself.
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.