Back to blog
Multi-factor authentication solutions: Choosing the best MFA provider for your use case
Auth & identity
Mar 22, 2025
Author: Stytch Team
Multi-factor authentication solutions protect your public and private applications from abuse by adding an extra layer of security to protect against account hijacking.
This guide explains the factors you should consider when choosing a multi-factor authentication provider, explaining the features you may need for your use case or specific project requirements, as well as future-proofing your authentication systems.
What multi-factor authentication solutions protect against
Multi-factor authentication (MFA) is the requirement that users provide multiple methods of authentication to log in to a system, rather than just a username and password. It is most commonly encountered when a two-factor authentication app generates a one-time password and emails or texts it to you.
Multi-factor authentication providers add extra protection for both users’ accounts and the data in them, as well as your organization's internal tools and infrastructure. This includes protecting against attacks including phishing, enumeration attacks and social engineering, password spraying/brute forcing, and credential stuffing using credentials sourced from password leaks and data breaches.
MFA is an essential component for all modern applications, and its absence is often a sign of a poorly secured application that does not respect the importance of its users’ security and privacy and protecting them from fraudulent activity.
Types of multi-factor authentication
With MFA, the weaknesses in each authentication factor are mitigated by the additional layer of security provided by the other additional factors. Some factors are more secure than others, while some offer greater familiarity and convenience to users.
- Knowledge factors: Usernames and passwords, PIN numbers, and security questions — these are all unique secrets that you can memorize to prove your identity. However, knowledge-based factors can be easily defeated if a password is leaked, disclosed, guessed, or brute-forced.
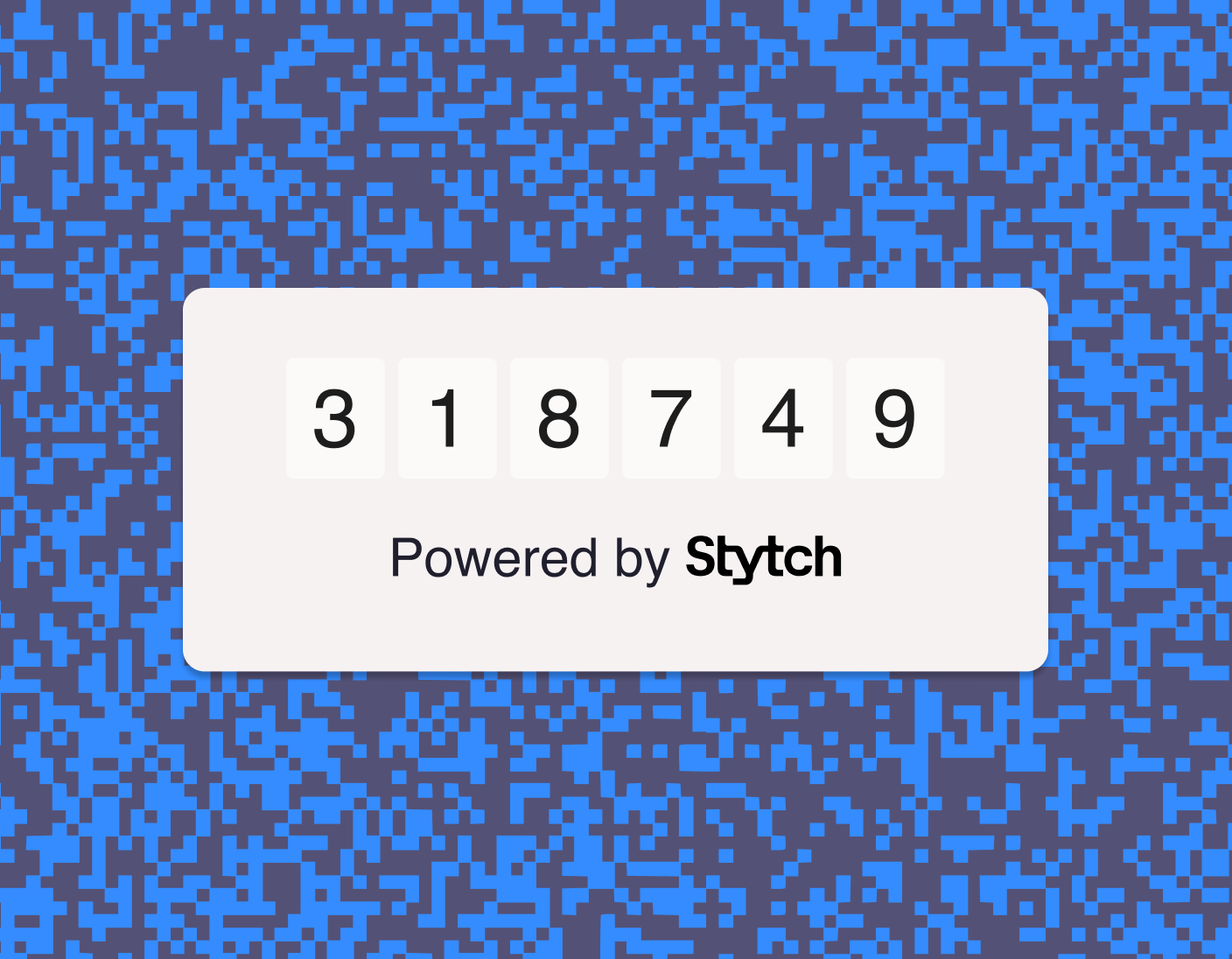
- Possession factors: One-time password (OTP), time-based one-time passwords (TOTP) authenticator apps, SMS/email verification, and hardware tokens (such as smart cards or passkeys like Yubikeys) are based on something you own or have access to that others don't. Combining possession-based factors with a username and password is a popular way to provide users with a familiar MFA method; however, authentication codes provided by SMS and email can be intercepted, and there are sophisticated attacks that can defeat OTP and other possession-based methods.
- Inheritance factors: Biometrics such as your fingerprint, face scan, or voice can be used in inheritance-based authentication. While these measures offer strong protection technologically, inheritance factors are also not infallible (and may be defeated by simply forcing the user to physically interact with a device while under duress). Inheritance factors based on physical characteristics also cannot be altered: if your biometric data is compromised, you cannot easily (or painlessly) change it.
- Location, temporal, and behavioral factors: More common in enterprise authentication solutions, location- and temporal-based factors verify users by their location, the time they are trying to perform actions, and their behavior. Employees attempting to log in from an unexpected IP address or at an unusual hour and then trying to immediately access sensitive information that they do not usually interact with may end the user's session and force them to re-authenticate.
Passwordless authentication can also combine with MFA factors (some that are even transparent to the user) to entirely remove the need for inherently insecure usernames and passwords as part of the authentication process.
What to look for in an MFA provider
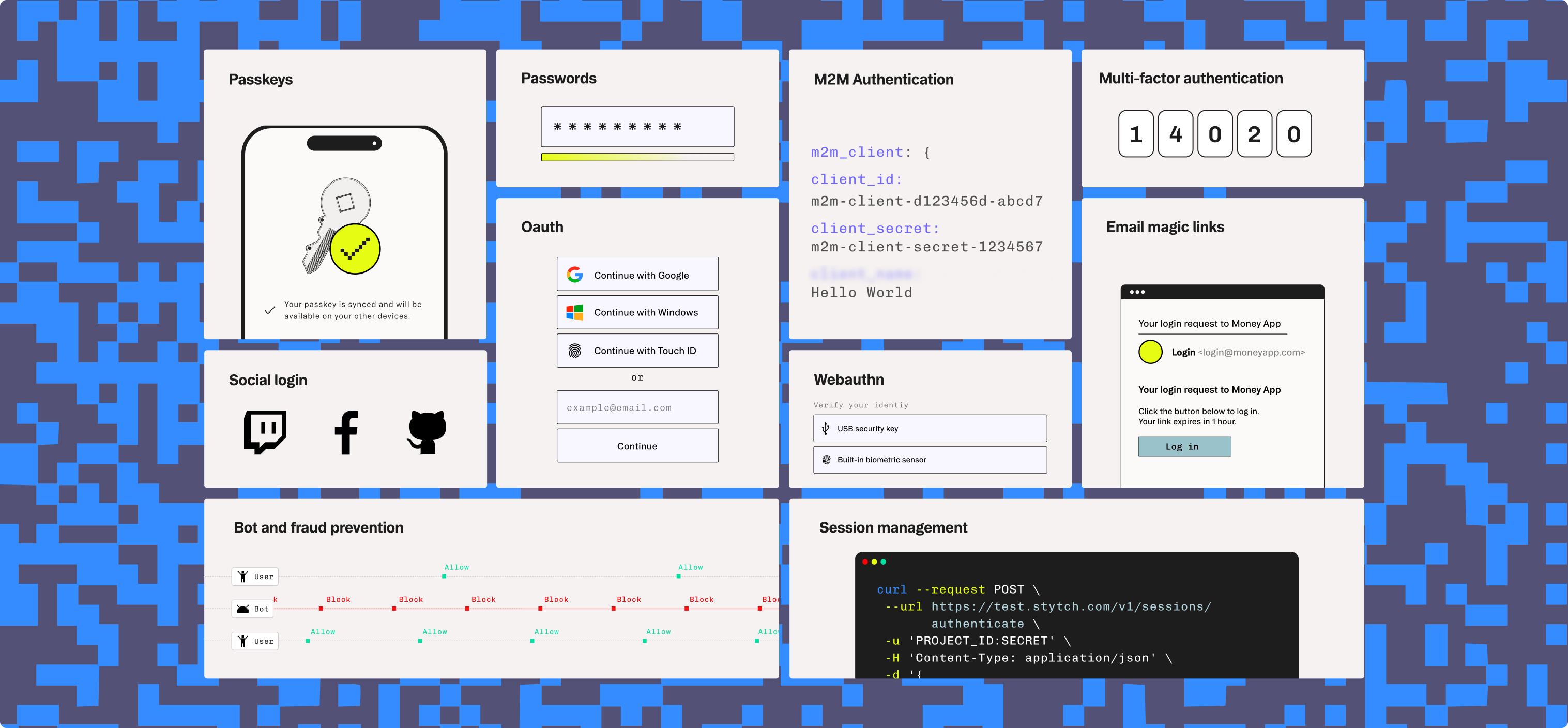
When choosing a multi-factor authentication provider for your application, you should first consider your use case. Do you require a simple login from a popular authentication provider (such as Google or Apple) for a public app, or are you building tools for enterprises that require features such as single sign on and integration with permissions-based access control? Answering this question will help you immediately narrow down your selection of MFA providers based on their advertised features.
From there, you can assess:
- Your users’ needs: The harder your multi-factor authentication is to set up and use, the less effective it will be. Your MFA solution should support the MFA methods your users have ready access to with the devices they already use or that your organization supplies to them.
- Developer features: Your MFA providers APIs/SDKs will need to be compatible with your existing platforms and technologies. Multi-factor authentication platforms should also be reputable, with helpful support resources and extensive documentation.
- Multi-factor authentication technologies: Are the multiple authentication factors you require supported? External factors like company policy or privacy regulations might dictate this.
- Future proofing: Support for standards such as WebAuthn and Passkeys and high customizability ensure that MFA solutions are flexible and able to adapt to evolving use cases and scaling deployments.
- Scalability: A cloud-based multi-factor authentication provider takes care of all of the infrastructure for you, including the security of the platform and ensuring it can scale limitlessly as traffic increases.
- Organization settings: In B2B SaaS applications, you may also require customizable MFA policies by organizations; for example, requiring certain employees or groups that have access to highly sensitive data to log in with MFA every time, while being less restrictive for users who do not have access to privileged resources and need quick access to basic functions. Without the flexibility to enforce MFA policies at both the team and individual user levels, multi-factor authentication can become a source of frustration and a security concern—potentially driving both users and admins to seek workarounds.
MFA provider for consumer and user-driven apps
When building consumer-facing applications, securing accounts without adding unnecessary friction is a delicate balance. Many apps default to letting users log in with just a username and password, which is fraught with security risks and threat vectors like account takeover. Even using OAuth to authenticate with social identity providers like Google, Facebook, or Apple has its drawbacks: users may not want to share data from those accounts, or may not have them at all, especially in regions where certain platforms aren't widely used.
To serve a diverse user base, consumer apps should support multiple sign-in methods—and make multi-factor authentication (MFA) a core part of their security posture. MFA isn't just a best practice; it's increasingly expected by users and often required by regulators. A missing or misconfigured second factor can become a liability in the event of a security breach.
Different use cases call for different approaches to MFA:
- Social or media apps may want a lighter approach like email-based one-time passcodes.
- International audiences benefit from other delivery methods like one-time passcodes using SMS or WhatsApp, since coverage for certain providers may vary by region.
- Financial apps with high fraud risk may require strong device-bound factors like TOTP and authenticator apps or biometric second factors using protocols like WebAuthn or Passkeys.
Stytch offers a comprehensive set of developer-friendly APIs and SDKs that let you implement a variety of MFA strategies—from SMS and email passcodes to biometrics and WebAuthn—tailored to your app’s unique security and user experience needs.
MFA solutions for B2B SaaS applications
In B2B applications, multi-tenancy presents challenges that can change MFA requirements significantly. Authentication needs to adapt not just to individual users but also to the policies of each organization you serve. Unlike consumer apps with a single login experience, B2B SaaS applications and platforms must support multi-tenant environments where each tenant can define and enforce its own security standards.
Multi-factor authentication (MFA) is a core requirement for many organizations, but enforcement often varies:
- Some organizations may mandate MFA for all their members.
- Certain organizations may even restrict which secondary auth factors—like TOTP, WebAuthn, or SMS—are considered acceptable.
- Other organizations may allow members to opt in individually.
And for B2B SaaS applications especially, MFA is usually just the tip of the iceberg.
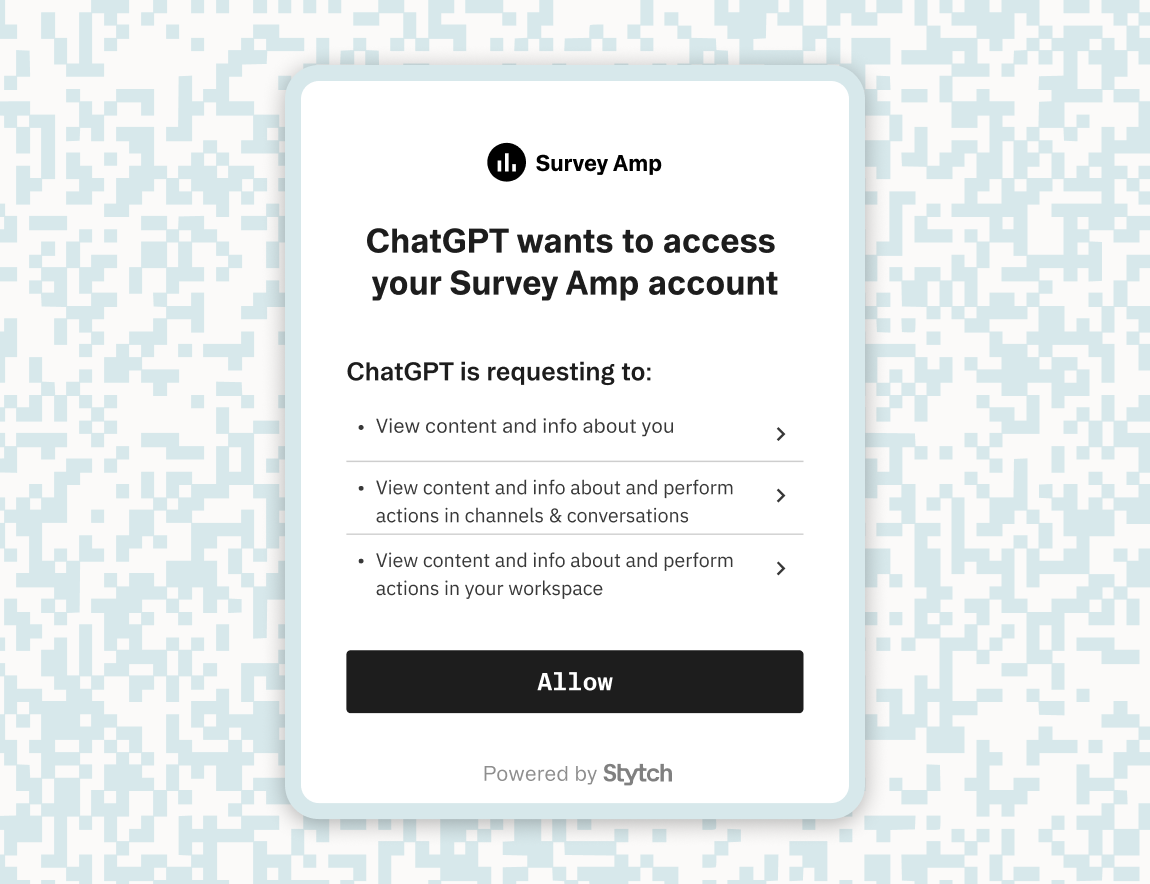
Enterprise organizations will also require that these MFA policies be strictly governed by a robust permissions and authorization framework like role-based access control (RBAC). Combining multi-factor authentication with features like SSO and SCIM is becoming non-negotiable for enterprises that need full coverage and control of their authentication and authorization for compliance reasons.
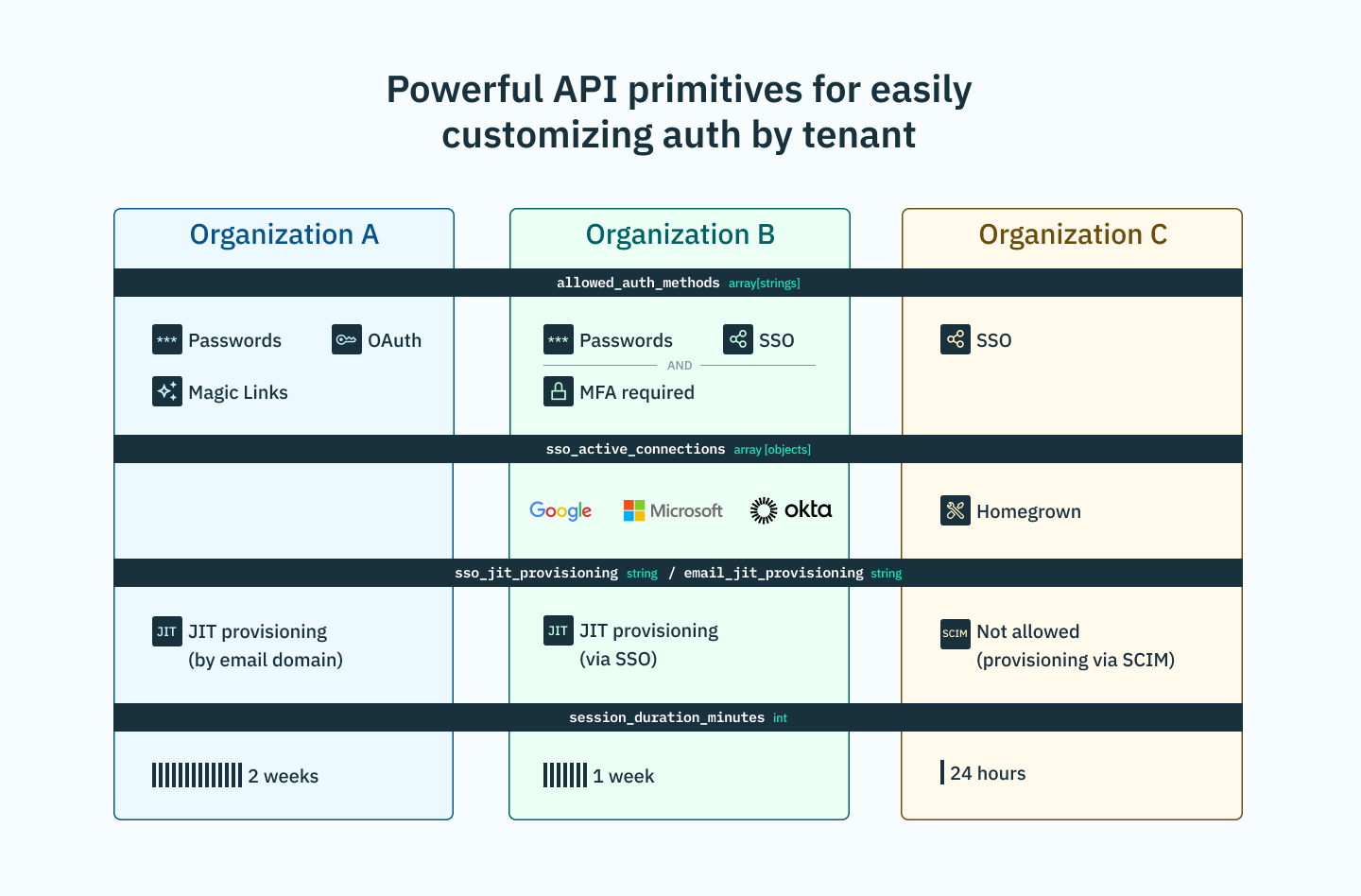
Stytch makes it easy to support these varying requirements with per-tenant MFA configuration in addition to several customizable enterprise auth features. Stytch’s API-driven platform gives each organization control over:
- MFA policies: Enforce that all members perform MFA in order to log into the Organization, and specify which MFA methods are allowed (e.g. TOTP only).
- Approved auth methods: Allows an Organization to specify which primary auth method(s) their members can use to log in (e.g. SSO only, or either Google OAuth and Email Magic Link)
- Just-in-Time (JIT) Provisioning: Optionally allow end users who meet the Organization's JIT Provisioning sources (email domain, SSO, or OAuth tenant) to automatically create an account without being explicitly added
- Invites: Option to allow invites to any email domain, restrict to just Allowed Domains, or to disable entirely
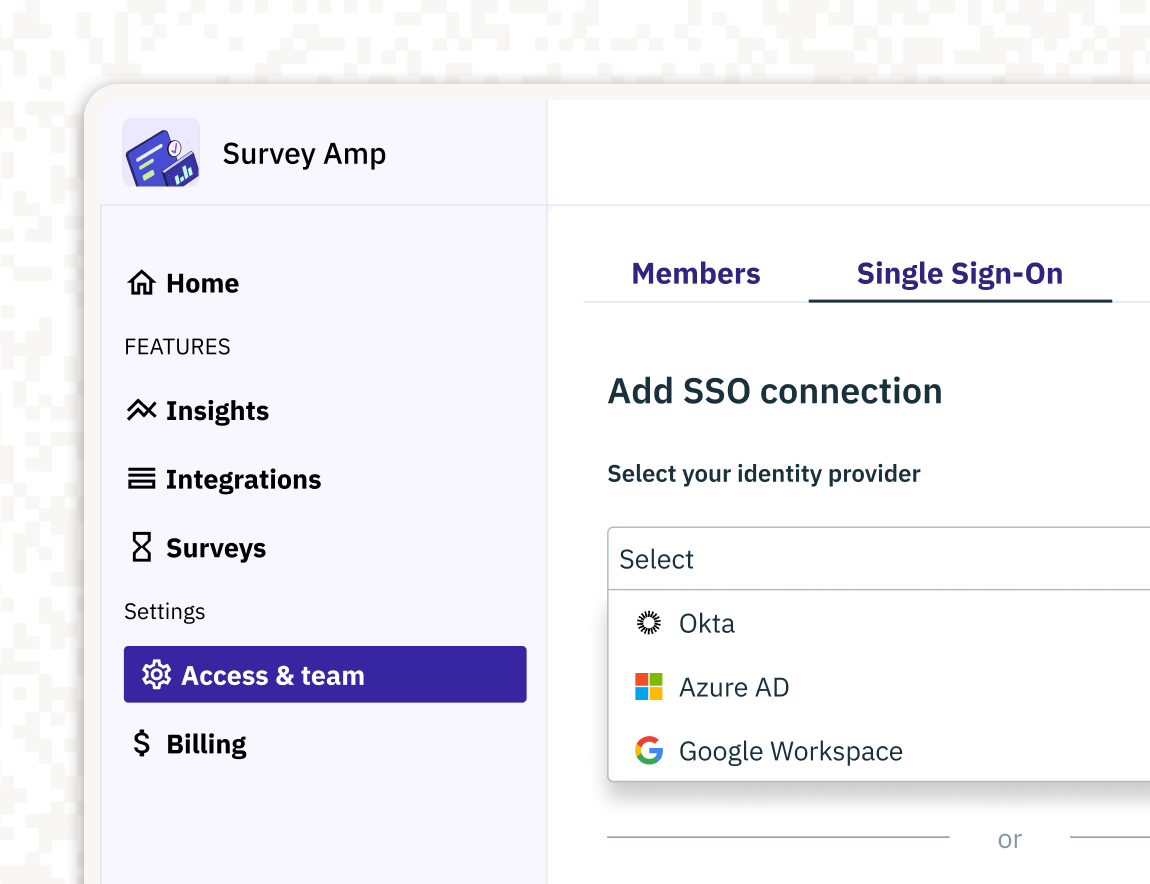
- SSO connections: Configure multiple SSO connections to have members authenticate via their workforce IdPs, with JIT Provisioning and automatic role assignment per-Connection.
- RBAC assignment: Assign roles and permissions to members either directly or automatically, based on SCIM Group membership, SSO Connection, or email domain.
- Custom metadata: Store application or business-specific attributes on the Organization object.
Is multi-factor authentication enough for security?
Multi-factor authentication is essential, but on its own, it’s not always enough.
And in addition to MFA as a security measure, Stytch also provides Fraud & Risk Prevention solutions like bot detection and device fingerprinting to help block malicious traffic and automated attempts to access user accounts. Intelligent monitoring can assess location- and time-based factors for anomalies, to further protect against malicious activity from unexpected sources.
Stytch combines these technologies to create an adaptive multi-factor authentication solution. This adaptive MFA solution uses AI technology to dynamically adjust its requirements based on the context of a login attempt by factoring the source, location, time, and other complex signals including user behavior. This allows trusted users and devices to log in frictionlessly, while users logging in under unusual circumstances will have to provide additional information to prove their identity.
Stytch can integrate with any app, and any enterprise system to provide a single, robust multi-factor authentication solution that spans multiple use cases and projects.
Sign up to get started with MFA and other enterprise auth features.
Build MFA with Stytch
APIs and SDKs for authentication, authorization, security and fraud prevention
Related Articles
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.