Engineering
May 21, 2025
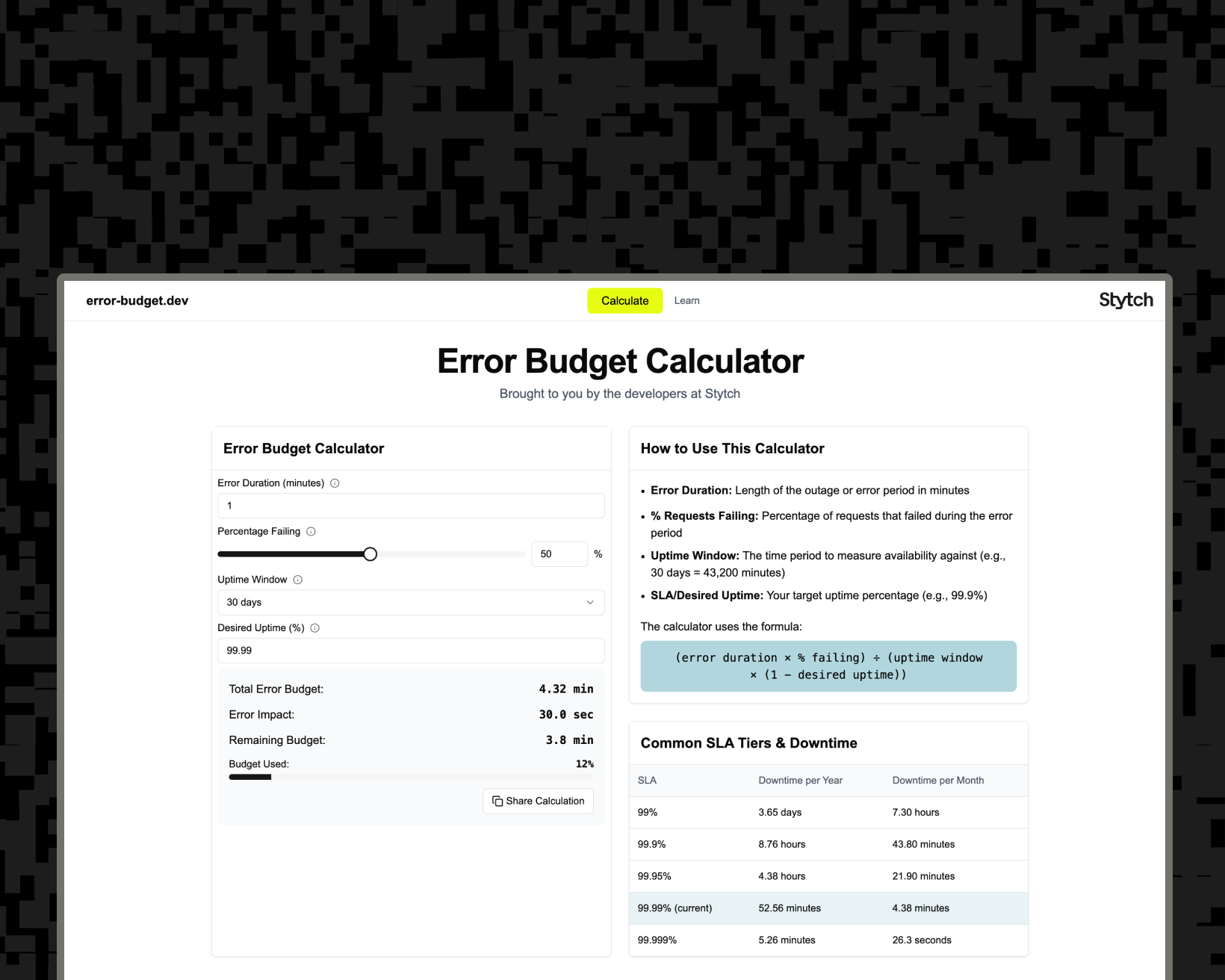
Understanding SLAs, SLOs, SLIs and Error Budgets
Engineering
May 20, 2025
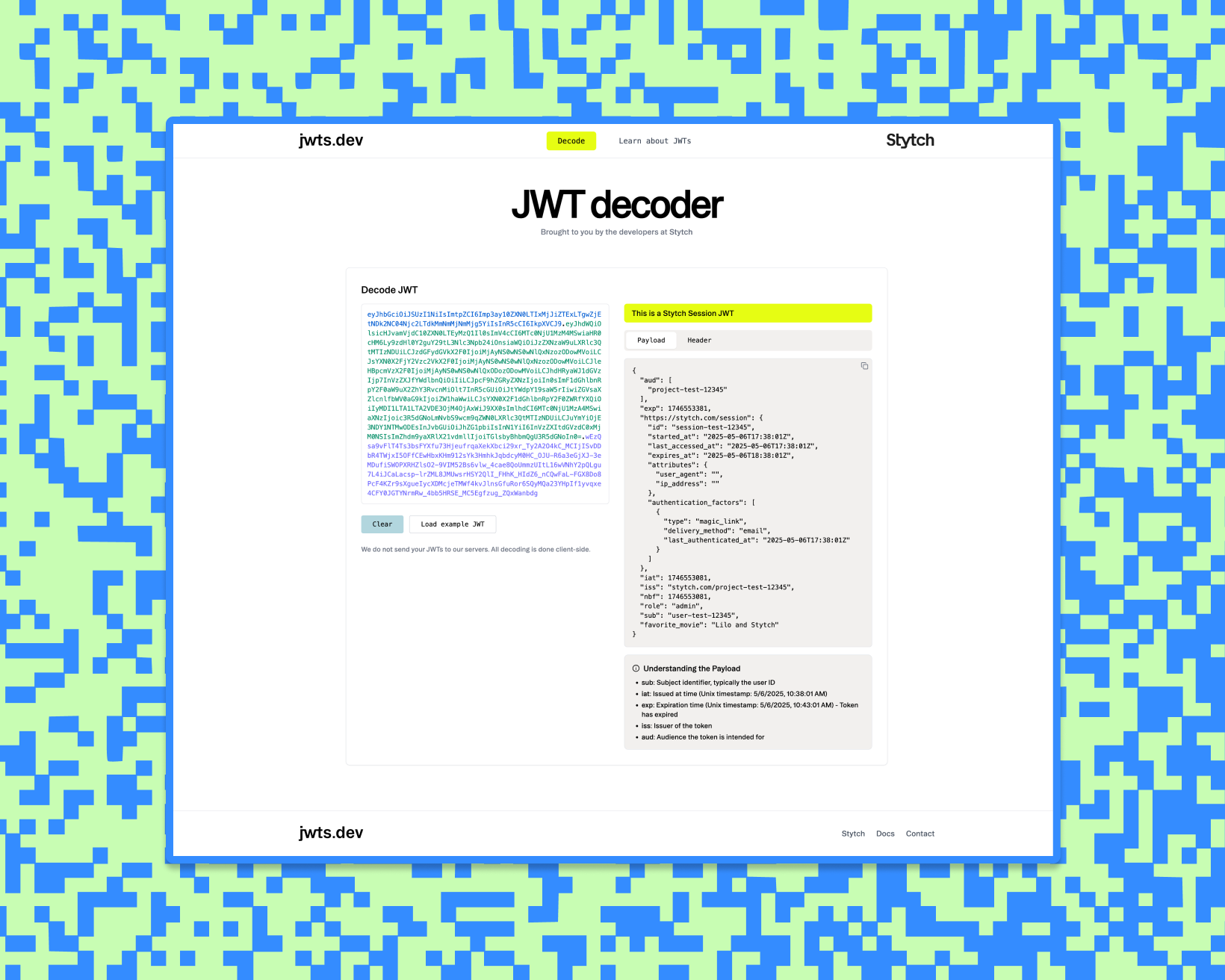
jwts.dev: decode and learn about JWTs in one place
Engineering
Mar 15, 2025
How to create a closed source Objective-C++ framework for Swift Package Manager
Auth & identity
Engineering
Jun 28, 2024
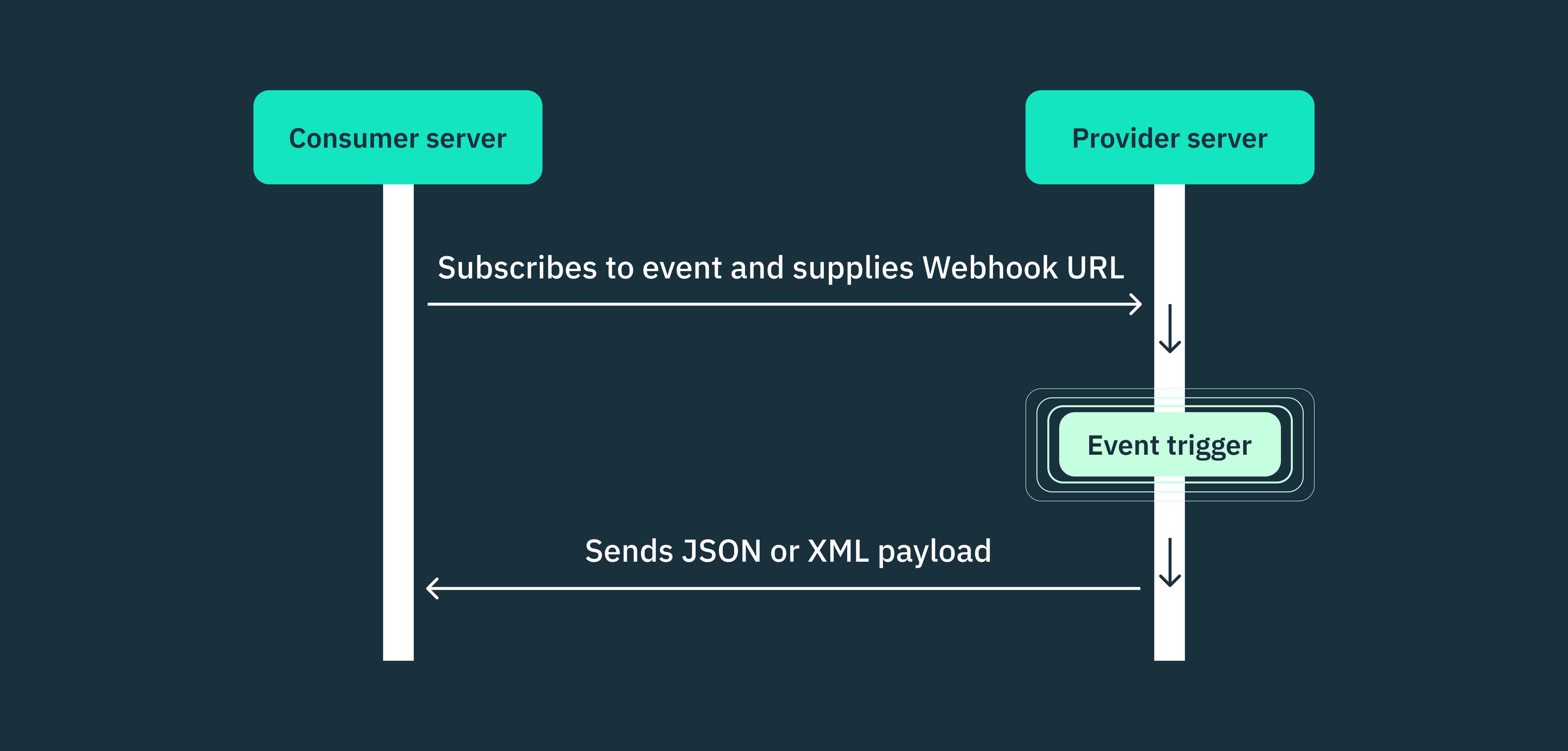
Webhooks security best practices
Auth & identity
Engineering
Jan 12, 2024
How to securely implement M2M authentication and authorization in Node.js using Stytch
Company
Engineering
Dec 29, 2023
Apply by API: Making job applications developer-focused
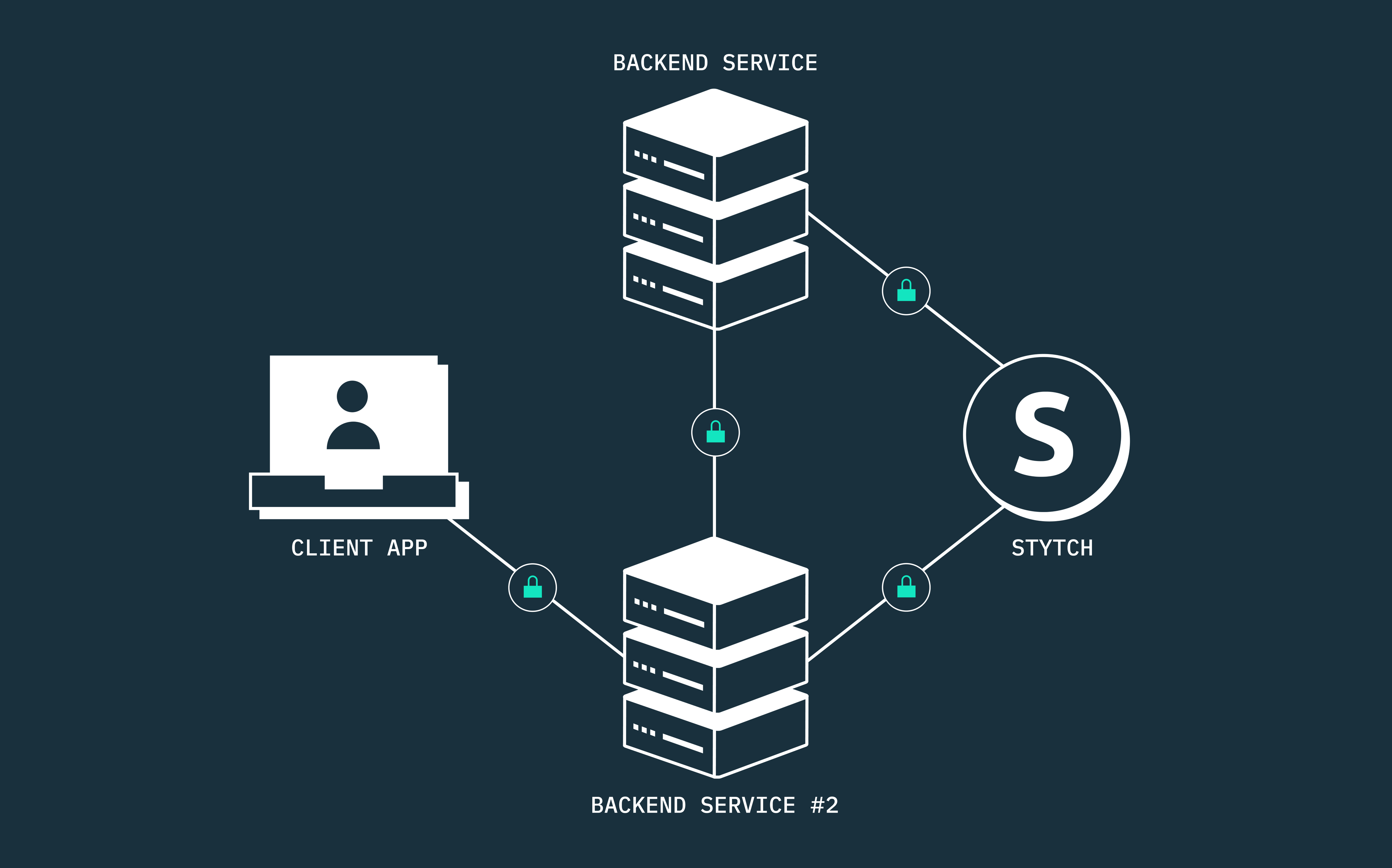
Auth & identity
Engineering
Dec 26, 2023
The complete guide to machine-to-machine (M2M) authentication and authorization
Engineering
Dec 21, 2023
Optimizing DBs at scale: how we reduced writes by 1000x for one of our most accessed tables
Engineering
Product
Dec 5, 2023
Log in with Passkeys: an example app using React and Stytch’s frontend SDK

Engineering
Oct 20, 2023
Upleveling our SQL models to manage DBT query speeds

Engineering
Sep 1, 2023
Open-sourcing SQX, a way to build flexible database models in Go
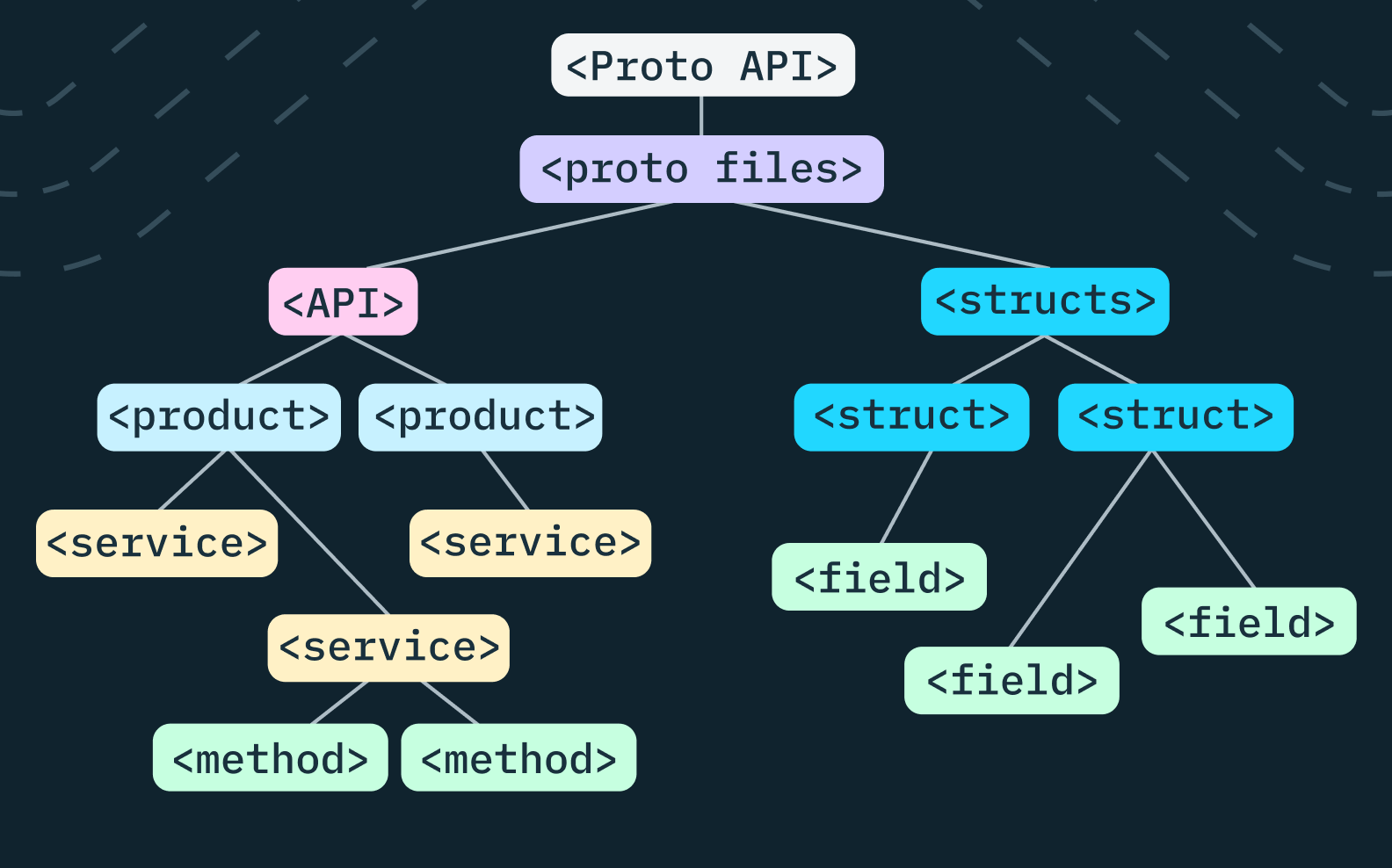
Engineering
Jul 18, 2023
Generating "humanlike" code for our backend SDKs
Engineering
Jul 12, 2023
What does compiler theory have to do with auth?
Engineering
Jul 10, 2023
An engineer’s guide to mobile biometrics: Android Keystore pitfalls and best practices

Engineering
May 3, 2023
An engineer's guide to mobile biometrics: event- vs result-based
Engineering
May 3, 2023
An engineer's guide to mobile biometrics: step-by-step

Engineering
Mar 17, 2023
Stytch postmortem 2023-02-23

Auth & identity
Engineering
Jan 20, 2023
Choosing a B2B auth provider
Auth & identity
Engineering
Jan 10, 2023
What is Security Assertion Markup Language (SAML) and how does it work?

Auth & identity
Engineering
Dec 16, 2022
What is OpenID Connect (OIDC)?
Auth & identity
Engineering
Dec 9, 2022
SSO protocols: SAML vs. OIDC
Company
Engineering
Dec 3, 2022
Engineering the engineering team
Auth & identity
Engineering
Nov 22, 2022
What is single sign on (SSO) and how does it work?
Auth & identity
Engineering
Nov 17, 2022
Organization tenancy: the foundation of SSO and B2B data models
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.