What are Passkeys exactly
Passkeys are FIDO credentials that utilize local biometric verifications like FaceID or TouchID to generate asymmetric public-private keys for authentication. The public key is registered and stored with the application, or relying party, the end user is authenticating into. The private key is stored on the device, or client, that was used for biometric verification.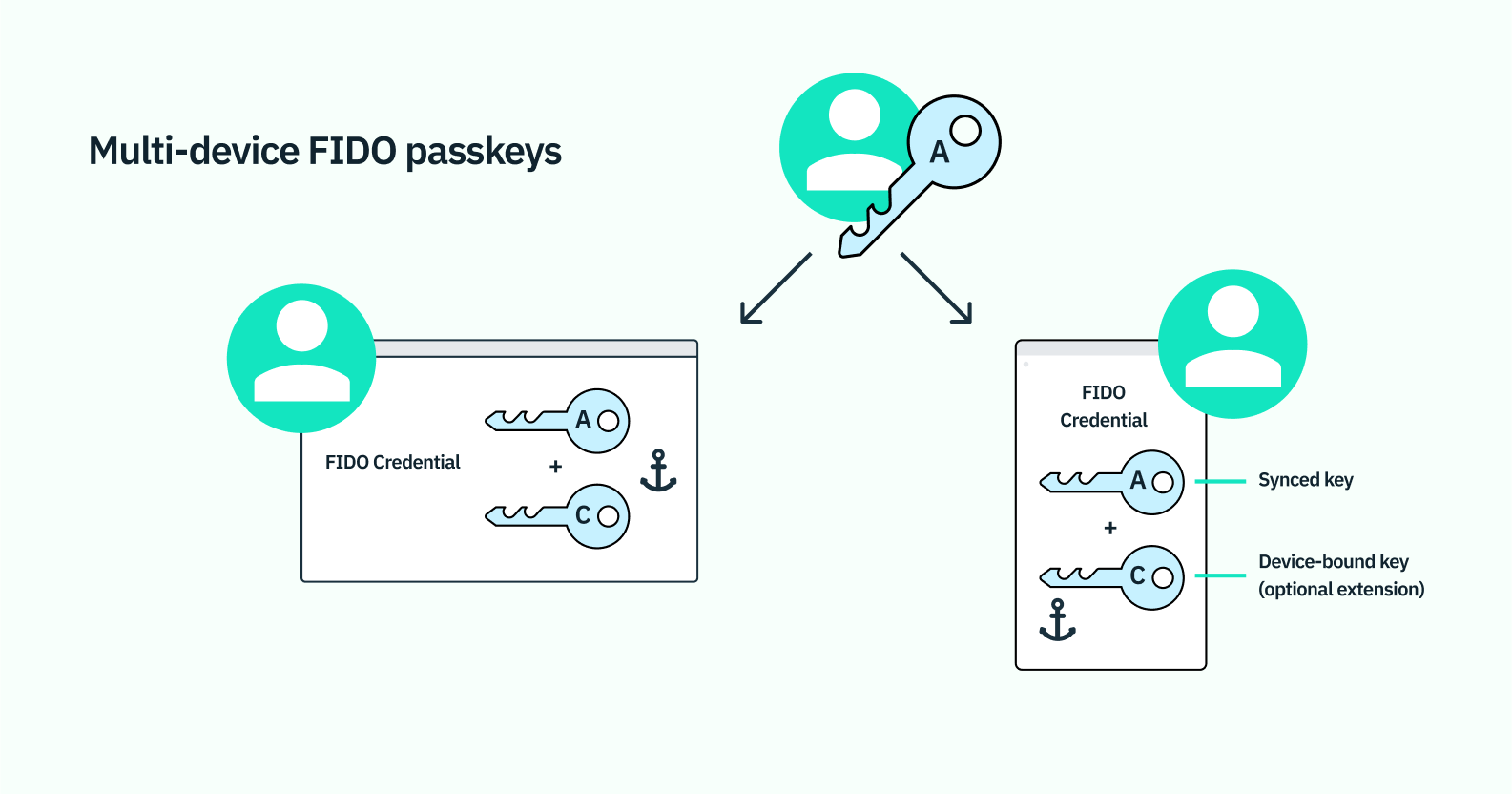
Passkeys are multi-device
Passkeys are stored in primarily two ways:- A passkey can be device-bound to a mobile device, computer, or an external device like a Yubikey.
- A passkey can be synced in the cloud by a provider and easily accessible from any connected device.
Passkeys and WebAuthn
The two technologies are inherently related. Passkeys are built on top of the WebAuthn standard, a web specification that defines the use of strong, attested, scoped, public key credentials by web applications. The term Passkeys refers to the multi-device usage of FIDO credentials, rather than the restricting of the private key to a single device. In other words, Passkeys are multi-device credentials created by the WebAuthn standard.Stytch Passkeys
Stytch enables developers to implement Passkeys while conveniently using the same WebAuthn endpoints. By integrating atop the WebAuthn API, developers have full flexibility and control when creating FIDO credentials. Set thereturn_passkey_credential_options field to true when calling the Start WebAuthn Registration endpoint or Start WebAuthn Authentication endpoint.

