Auth & identity
Nov 10, 2025
AI agent authentication methods

Auth & identity
Oct 8, 2025
Guide to authentication for the OpenAI Apps SDK
Auth & identity
Sep 29, 2025
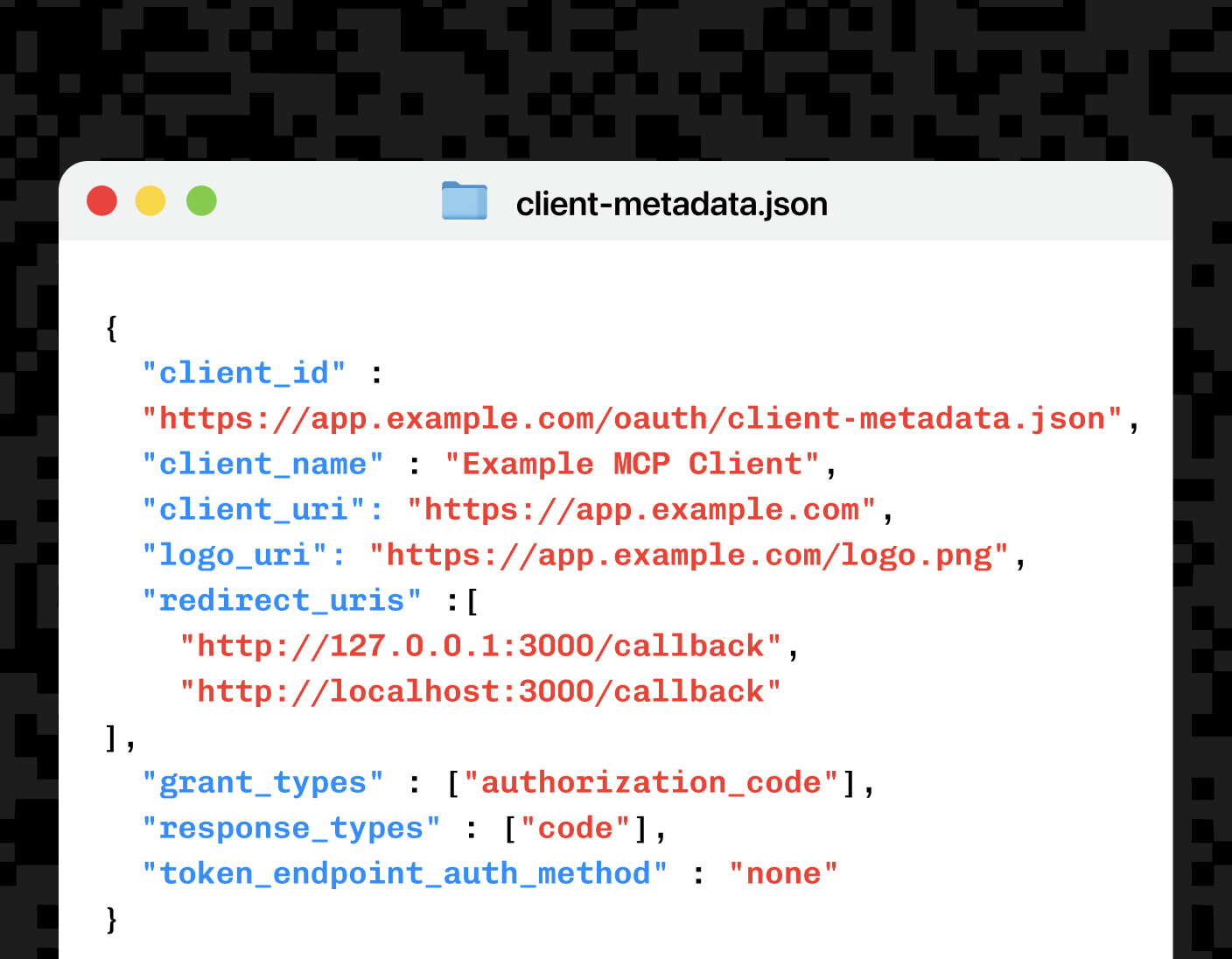
Building MCP with OAuth Client ID Metadata (CIMD)
Auth & identity
Sep 29, 2025
AI agent authentication: securing your app for autonomous agent access

Auth & identity
Sep 24, 2025
Agent ready episode 8 with Anthropic, Cloudflare, and Arcade: evolving architectures for AI agents

Latest
Auth & identity
Product
Sep 23, 2025
Stytch supports Web Bot Auth for agent and bot verification

Latest
Auth & identity
Engineering
Sep 23, 2025
How to implement Web Bot Auth for your AI agent, bot, or crawler (and why you should)

Auth & identity
Sep 16, 2025
Agent ready episode 7 with Stytch: AI agent fraud and threat prevention

Auth & identity
Sep 4, 2025
Agent ready episode 6 with Honeycomb: observability & SLOs with AI agent workloads

Auth & identity
Sep 3, 2025
Agent ready episode 5 with Arcade: tool calling, orchestration, & agent development

Auth & identity
Aug 28, 2025
Agent ready episode 4 with Stytch: identity, auth + consent for AI agents

Auth & identity
Aug 26, 2025
Agent ready episode 3 with Cloudflare: deploying remote MCP at the edge
Auth & identity
Aug 21, 2025
Agent ready episode 2 with Stainless: auto-generating an MCP server & client

Auth & identity
Aug 19, 2025
Agent ready episode 1 with Langflow: RAG workflows & agent development
Auth & identity
Aug 18, 2025
Agent-to-agent OAuth: a guide for secure AI agent connectivity with MCP
Auth & identity
Aug 15, 2025
The top 7 passwordless authentication solutions for developers
Auth & identity
Aug 14, 2025
SCIM API explained: how it works and how to integrate with identity providers

Auth & identity
Aug 13, 2025
Sam Altman was wrong: AI didn’t defeat auth. Single factors did.
Auth & identity
Aug 12, 2025
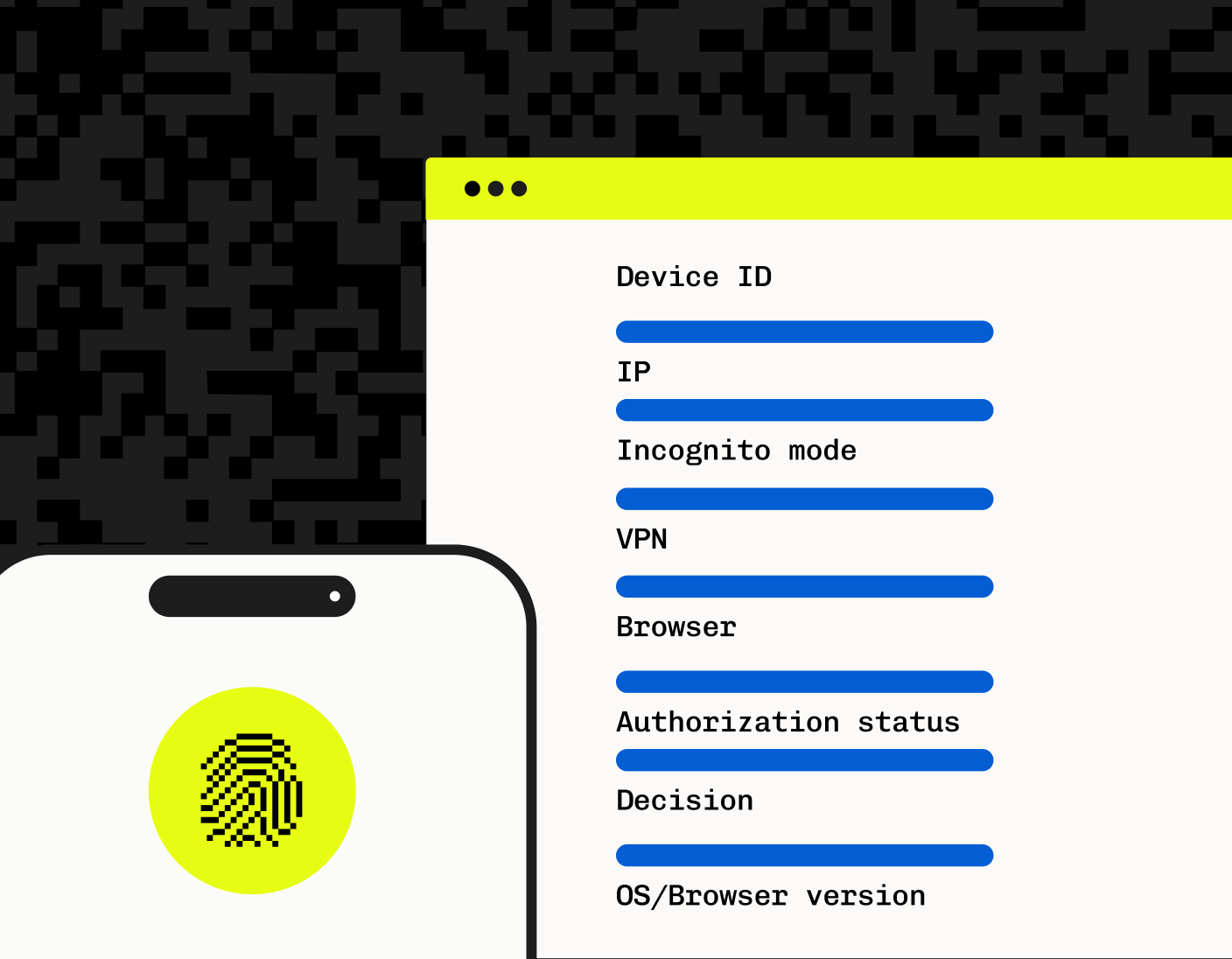
What Is device fingerprinting? Guide and implementation techniques

Auth & identity
Aug 11, 2025
SCIM protocol: how it works, what it solves, and why it matters
Auth & identity
Jul 23, 2025
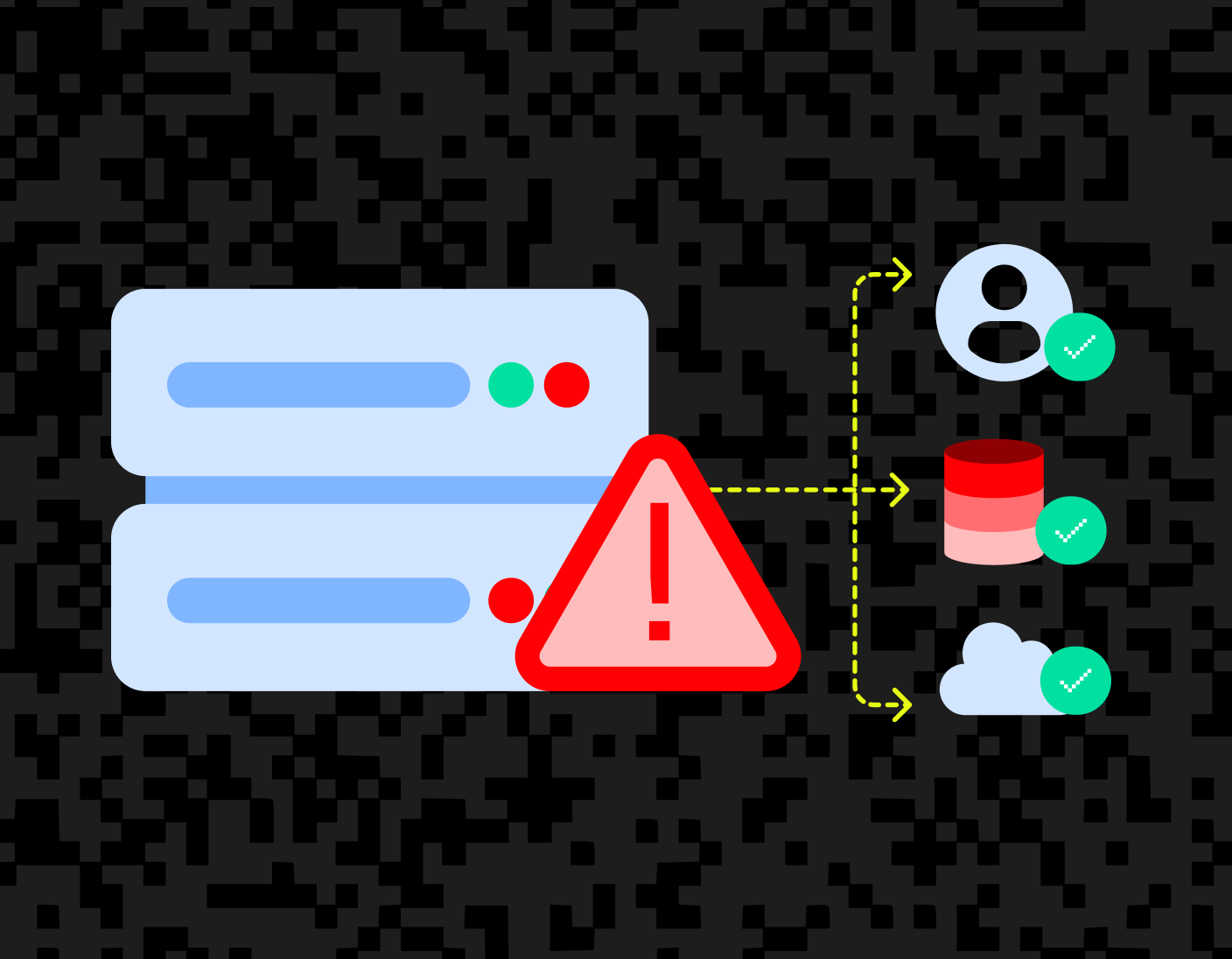
Securing identity APIs against server-side request forgery (SSRF) at Stytch
Auth & identity
Jul 21, 2025
MCP authentication and authorization implementation guide

Auth & identity
Jul 16, 2025
Browser fingerprinting: implementing fraud detection techniques in the era of AI
Auth & identity
Jul 16, 2025
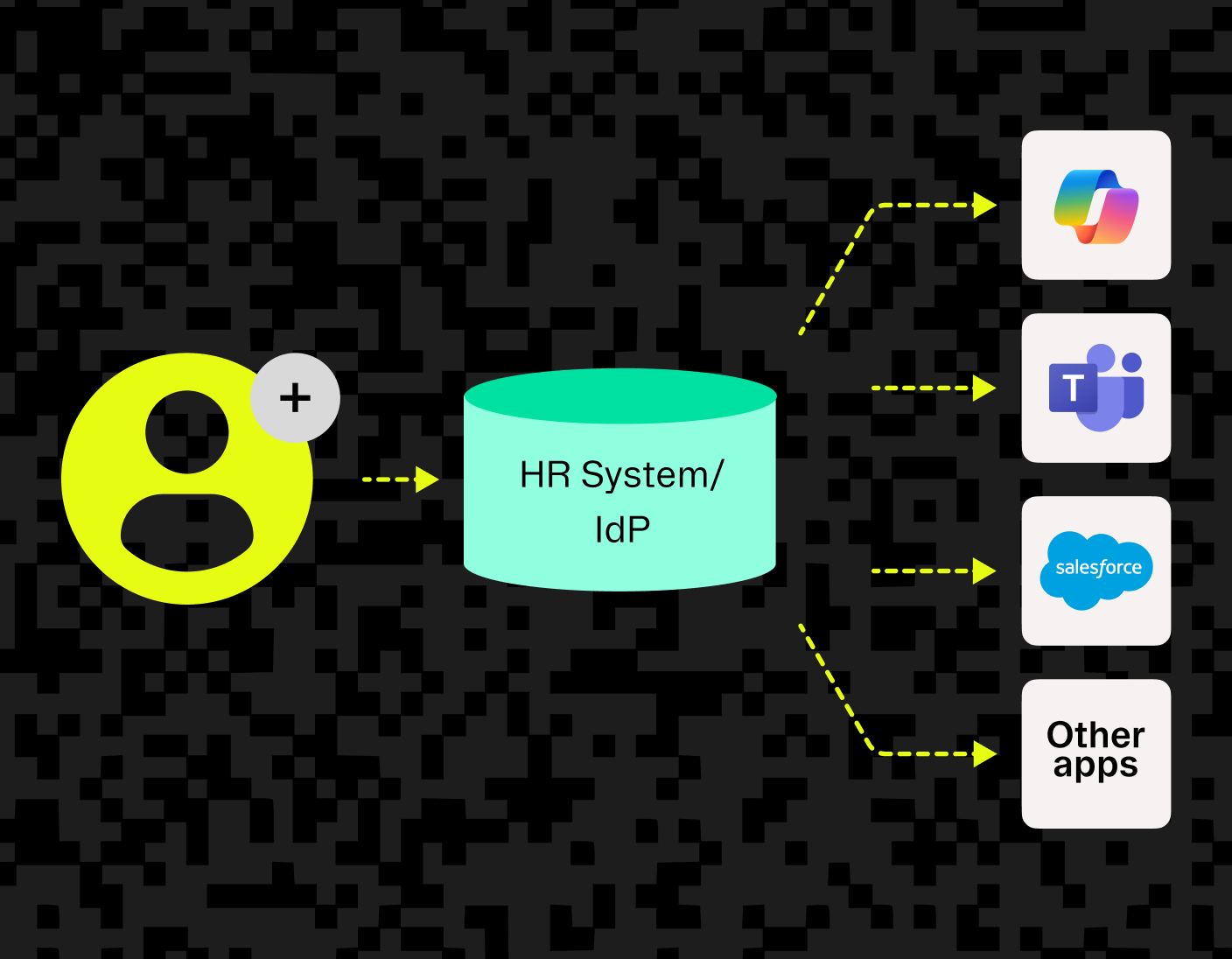
Top SCIM Tools to Streamline B2B Identity Management in 2025
Auth & identity
Jun 30, 2025
How to secure model-agent interactions against MCP vulnerabilities

Auth & identity
Jun 11, 2025
OAuth for MCP explained with a real-world example
Auth & identity
Jun 4, 2025
The age of agent experience: now with MCP servers
Auth & identity
Jun 4, 2025
How to secure MCP: threats and defenses

Auth & identity
Jun 4, 2025
Bears, mice, and moles aren’t enough: a better approach for preventing fraud
Auth & identity
SAML Shield
May 21, 2025
SAML example: what is SAML and how do you use It?
Auth & identity
May 21, 2025
AI agent fraud: key attack vectors and how to defend against them
Auth & identity
May 21, 2025
How to block AI web crawlers: challenges and solutions

Auth & identity
May 19, 2025
If an AI agent can’t figure out how your API works, neither can your users

Auth & identity
May 2, 2025
npm-audit for MCP security: A deep-dive on mcp-scan
Auth & identity
Apr 25, 2025
Single Sign-On example

Auth & identity
Apr 19, 2025
Building an MCP server with OAuth and Cloudflare Workers

Auth & identity
Apr 17, 2025
What is a SAML service provider? How to integrate your app with enterprise Single Sign-On
Auth & identity
Apr 16, 2025
The best authentication services in 2025
Auth & identity
Apr 12, 2025
MCP and OAuth Dynamic Client Registration
Auth & identity
Apr 11, 2025
MCP authentication and authorization servers
Auth & identity
Apr 4, 2025
Handling AI agent permissions
Auth & identity
Apr 3, 2025
Stytch vs Auth0: Bot detection

Auth & identity
Apr 2, 2025
OAuth 2.1 vs 2.0: What developers need to know
Auth & identity
Mar 29, 2025
AI agent security explained

Auth & identity
Mar 28, 2025
Model Context Protocol (MCP): A comprehensive introduction for developers

Auth & identity
Mar 28, 2025
A developer’s guide to RFC 7519, part 1: JWT structure and claims
Auth & identity
Mar 28, 2025
Authentication as a service: Launch faster with stronger security
Auth & identity
Mar 22, 2025
Multi-factor authentication solutions: Choosing the best MFA provider for your use case
Auth & identity
Mar 21, 2025
Auth0 reviews: Why developers migrate from Auth0 to Stytch
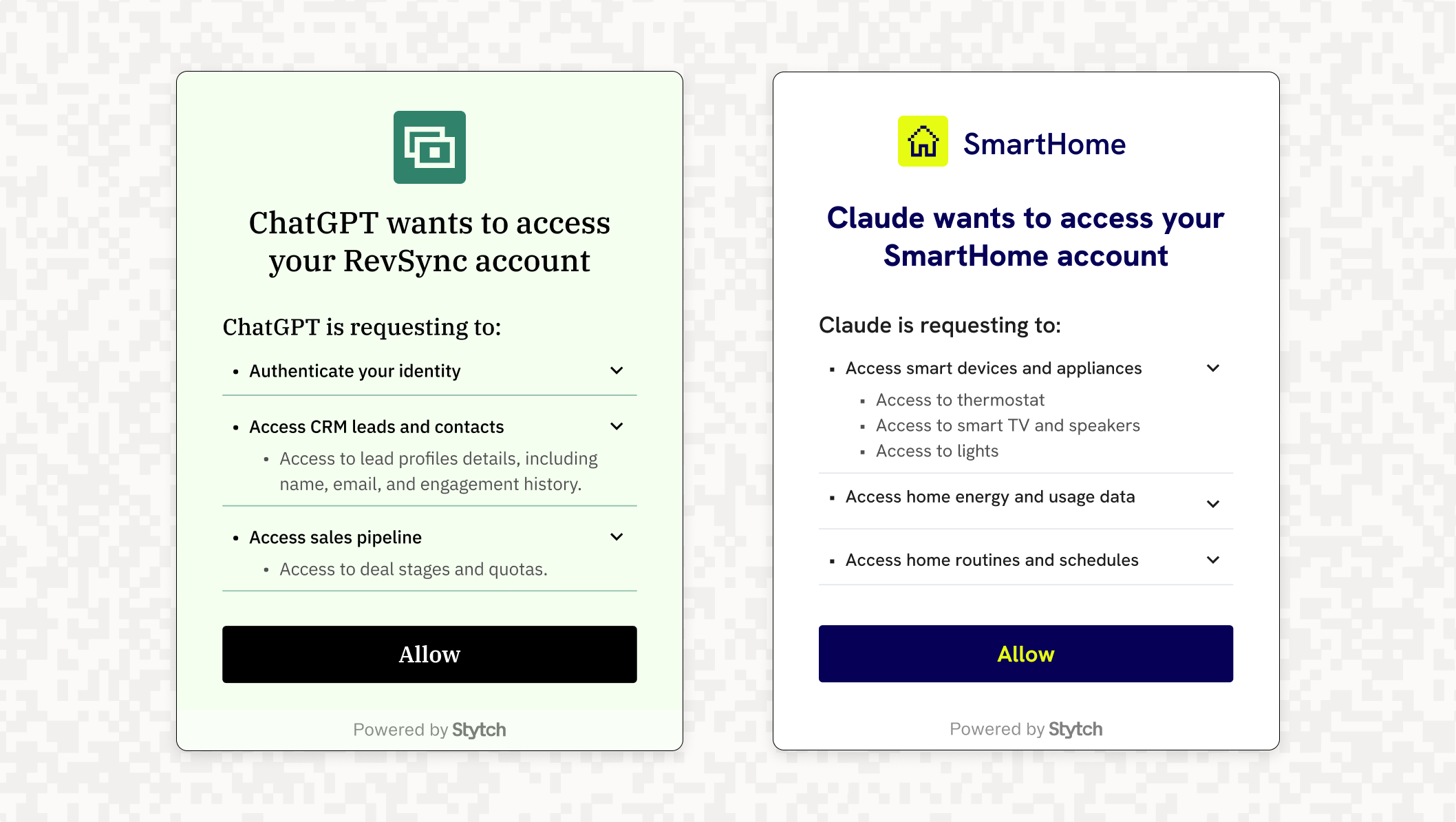
Auth & identity
Mar 8, 2025
Connecting AI agents to every app
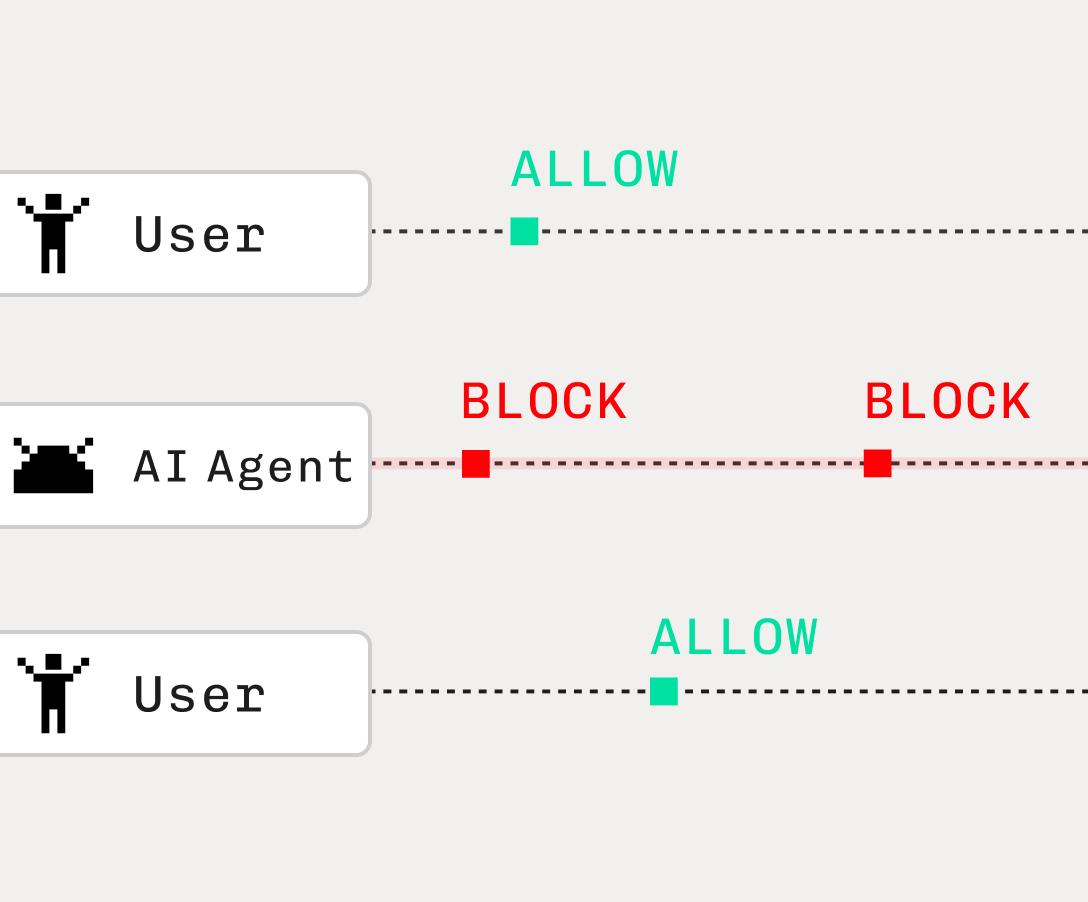
Auth & identity
Feb 15, 2025
Detecting AI agent use & abuse

Auth & identity
Feb 8, 2025
The age of agent experience
Auth & identity
Jan 4, 2025
Why email verification is crucial for B2B applications
Auth & identity
Jan 3, 2025
Bot Detection 101: How to Detect (and Beat) Bot Traffic

Auth & identity
Dec 3, 2024
What Is Anonymous Visitor Identification? How to Identify Visitors to your Website or App
Auth & identity
Nov 15, 2024
Canvas fingerprinting: Explained and illustrated

Auth & identity
Nov 1, 2024
Stytch Embedded Auth vs. Auth0 Universal Login
Auth & identity
Oct 31, 2024
Auth0's Security Incidents: How JWT Vulnerabilities Have Repeatedly Impacted the Platform
Auth & identity
Oct 24, 2024
Top techniques for effective API rate limiting

Auth & identity
Oct 17, 2024
Anti-spoofing tools and techniques

Auth & identity
Oct 2, 2024
Top strategies to prevent web scraping and protect your data

Auth & identity
Sep 25, 2024
Auth0 2024 Pricing Update: What They’re Hiding About the Real Cost

Auth & identity
Sep 25, 2024
Adaptive MFA: A smarter approach to authentication security

Auth & identity
SAML Shield
Sep 4, 2024
SAML certificates explained

Auth & identity
Aug 28, 2024
Spotting the spoof: User agent spoofing unmasked
Auth & identity
SAML Shield
Aug 22, 2024
What are SAML assertions?
Auth & identity
Aug 8, 2024
SAML vs LDAP: What's the difference?

Auth & identity
Aug 1, 2024
SAML vs OAuth: Key Differences Explained
Auth & identity
Jul 25, 2024
Integrating SAML Single Sign-On with Python, Okta, and Stytch

Auth & identity
Jul 23, 2024
Stopping an account takeover before it takes a toll
Auth & identity
Jul 9, 2024
SCIM API: Your comprehensive guide and introduction
Auth & identity
Engineering
Jun 28, 2024
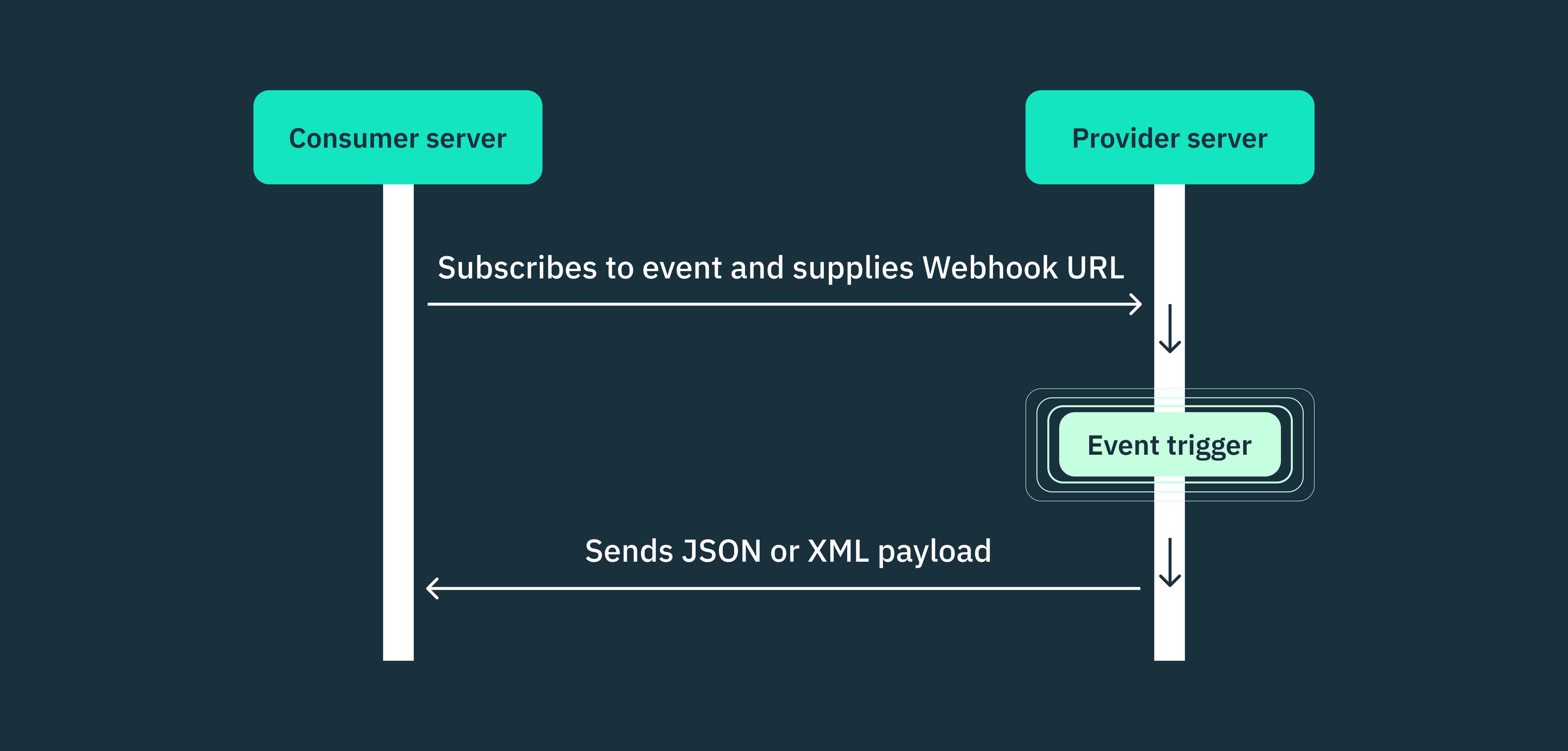
Webhooks security best practices
Auth & identity
Jun 25, 2024
Application security in the age of artificial intelligence: adapting to new challenges and opportunities
Auth & identity
Jun 12, 2024
What is SCIM and how does it work?

Auth & identity
Jun 11, 2024
CAPTCHA vs. reCAPTCHA: What’s the difference?
Auth & identity
May 30, 2024
How to Enforce Multi-Factor Authentication with Node.js and Stytch

Auth & identity
May 24, 2024
Webhooks vs APIs
Auth & identity
May 22, 2024
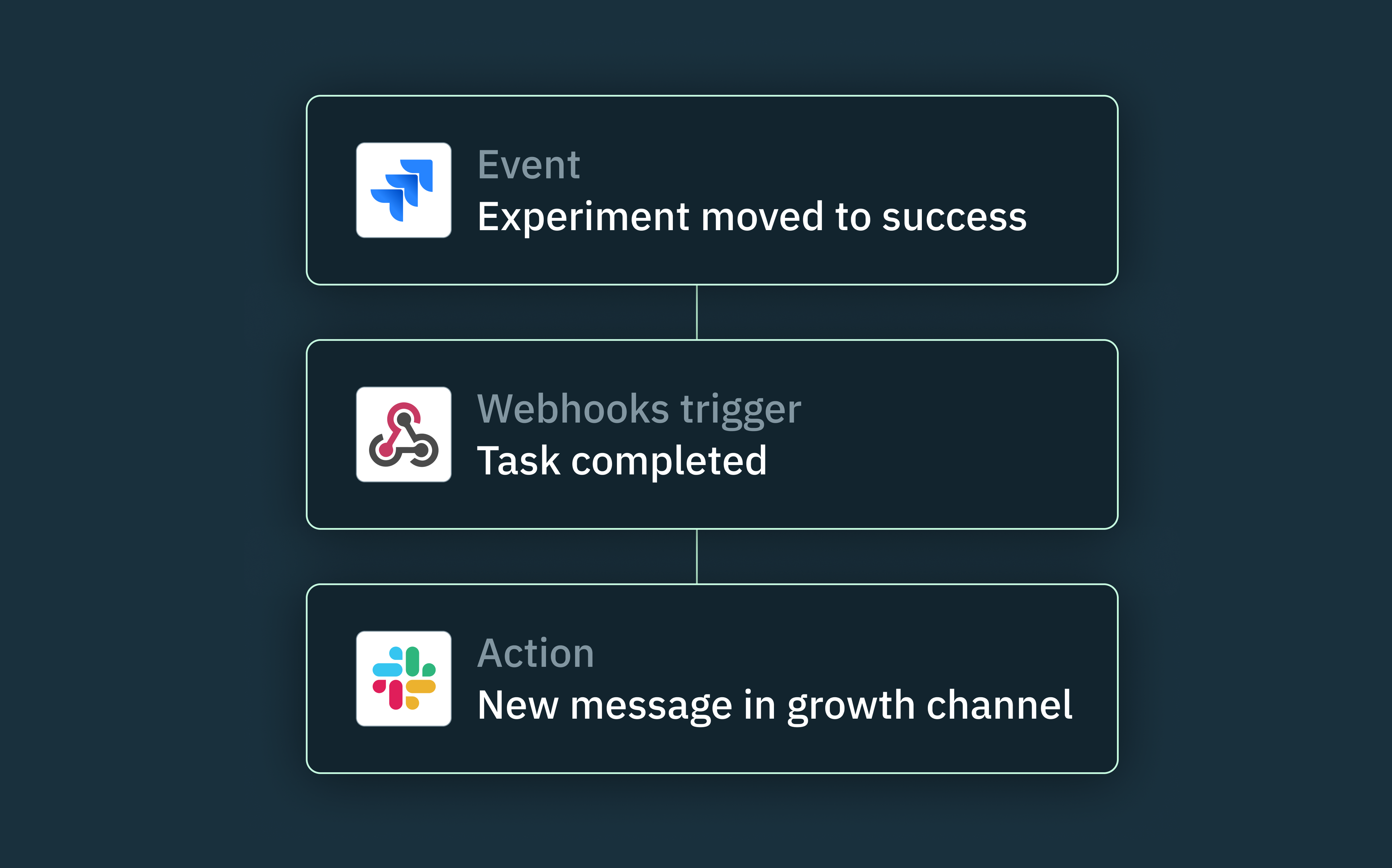
What are webhooks?

Auth & identity
Apr 9, 2024
Account Abuse Prevention
Auth & identity
Mar 14, 2024
Session management best practices

Auth & identity
Mar 5, 2024
Managing user sessions: localStorage vs sessionStorage vs cookies
Auth & identity
Mar 5, 2024
Unpacking MACH architecture: The future of SaaS development
Auth & identity
Feb 29, 2024
Understanding JWKS: JSON Web Key Set Explained

Auth & identity
Feb 23, 2024
B2B SaaS applications: A comprehensive overview

Auth & identity
Feb 13, 2024
What is SaaS integration and why should developers consider it?
Auth & identity
Feb 9, 2024
RBAC vs PBAC vs ABAC
Auth & identity
Feb 6, 2024
What is attribute-based access control (ABAC)
Auth & identity
Jan 29, 2024
What is role-based access control (RBAC)?

Auth & identity
Jan 26, 2024
Keycloak alternatives for enterprise authentication and identity management
Auth & identity
Engineering
Jan 12, 2024
How to securely implement M2M authentication and authorization in Node.js using Stytch

Auth & identity
Jan 11, 2024
What is a reverse proxy?
Auth & identity
Dec 29, 2023
Scalper bots: The box office boom no one wants
Auth & identity
Engineering
Dec 26, 2023
The complete guide to machine-to-machine (M2M) authentication and authorization
Auth & identity
Dec 22, 2023
Bot mitigation software: A fraudster's foil in an automated world
Auth & identity
Dec 14, 2023
Beating back bot fraud in 2024
Auth & identity
Product
Dec 5, 2023
Introducing Passkeys authentication
Auth & identity
Dec 5, 2023
Passkey authentication: The cure for password dependency?
Auth & identity
Dec 1, 2023
Passkey vs. password: a new era of secure authentication

Auth & identity
Nov 27, 2023
What is a common indicator of a phishing attempt?

Auth & identity
Nov 21, 2023
What is a bot and how do they work
Auth & identity
Nov 10, 2023
Preventing contact spam form submissions
Auth & identity
Nov 8, 2023
One-Time Password (OTP) bots: what they are and how to stop them
Auth & identity
Nov 3, 2023
What is fraud prevention?
Auth & identity
Nov 1, 2023
What is browser fingerprinting?
Auth & identity
Oct 23, 2023
What is SIM-swap scam, and how can you protect your users against one?

Auth & identity
Oct 4, 2023
JWT claims

Auth & identity
Oct 3, 2023
Evaluating Auth0 alternatives for authentication and authorization

Auth & identity
Oct 3, 2023
What is a JSON web token?

Auth & identity
Sep 1, 2023
How to manage Auth0’s rules and hooks deprecation: a shift towards actions

Auth & identity
Aug 30, 2023
Extending authorization code flows with PKCE
Auth & identity
Aug 30, 2023
What is an enumeration attack?

Auth & identity
Aug 30, 2023
How to prevent enumeration attacks

Auth & identity
Jul 11, 2023
The journey to ISO 27001 certification

Auth & identity
Jul 10, 2023
The top 10 password cracking techniques – and how to outmaneuver them
Auth & identity
Apr 12, 2023
IdP- vs SP-initiated SSO
Auth & identity
Apr 1, 2023
Authentication vs. authorization: what you need to know

Auth & identity
Mar 23, 2023
What is OAuth 2.0?
Auth & identity
Mar 21, 2023
How do voice recognition biometrics work?
Auth & identity
Mar 16, 2023
Foundations of scalable B2B auth
Auth & identity
Company
Mar 15, 2023
Stytch Talks With Jordan Burris: “The Future of Multi-Factor Authentication (MFA)”

Auth & identity
Mar 1, 2023
Argon2 vs bcrypt vs. scrypt: which hashing algorithm is right for you?

Auth & identity
Feb 23, 2023
What is a passkey?

Auth & identity
Feb 15, 2023
All about biometric authentication

Auth & identity
Feb 13, 2023
What is passwordless authentication?
Auth & identity
Feb 10, 2023
What are one-time passcodes (OTPs)?
Auth & identity
Feb 6, 2023
Bot mitigation for identity and access management

Auth & identity
Feb 2, 2023
The FIDO alliance and a passwordless future
Auth & identity
Feb 1, 2023
Balancing security and adoption: preventing account takeover fraud with multi-factor authentication
Auth & identity
Feb 1, 2023
TOTP vs SMS: Which one is better for two-factor authentication (2FA)?

Auth & identity
Jan 23, 2023
JWTs vs. sessions: which authentication approach is right for you?

Auth & identity
Engineering
Jan 20, 2023
Choosing a B2B auth provider
Auth & identity
Engineering
Jan 10, 2023
What is Security Assertion Markup Language (SAML) and how does it work?

Auth & identity
Engineering
Dec 16, 2022
What is OpenID Connect (OIDC)?
Auth & identity
Dec 16, 2022
Securing AI against bot attacks
Auth & identity
Engineering
Dec 9, 2022
SSO protocols: SAML vs. OIDC
Auth & identity
Engineering
Nov 22, 2022
What is single sign on (SSO) and how does it work?
Auth & identity
Nov 17, 2022
What is CAPTCHA, and how does it work?
Auth & identity
Engineering
Nov 17, 2022
Organization tenancy: the foundation of SSO and B2B data models
Auth & identity
Engineering
Nov 4, 2022
Introducing B2B Auth School

Auth & identity
Nov 4, 2022
Anatomy of a strong password
Auth & identity
Oct 27, 2022
Do passkeys live up to the hype?

Auth & identity
Oct 24, 2022
What is unphishable MFA?

Auth & identity
Oct 13, 2022
The importance of investing in unphishable authentication
Auth & identity
Company
Sep 29, 2022
Stytch Talks with Brian Hale: rethinking user sign-up and login to unlock growth

Auth & identity
Sep 16, 2022
What is identity and access management (IAM)?

Auth & identity
Sep 8, 2022
How compromised passwords lead to data breaches
Auth & identity
Sep 1, 2022
What is TOTP and why does it matter?
Auth & identity
Aug 31, 2022
Making auth your growth lever

Auth & identity
Aug 30, 2022
The definitive guide to choosing a Customer and Identity Access Management (CIAM) solution
Auth & identity
Aug 25, 2022
Eliminate bot attacks from the CAPTCHA equation
Auth & identity
Aug 24, 2022
Multi-factor authentication: how to choose the right approach for your business
Auth & identity
Aug 23, 2022
Step-up versus multi-factor authentication (MFA)
Auth & identity
Aug 17, 2022
Stytch’s guide to adding passwordless options for password-based auth flows
Auth & identity
Aug 15, 2022
How to prevent account takeover (ATO) and improve user authentication
Auth & identity
Aug 11, 2022
What is password salting?

Auth & identity
Company
Jul 28, 2022
Stytch vs. Amazon Cognito

Auth & identity
Jul 27, 2022
What is password hashing?

Auth & identity
Jul 18, 2022
Protect against password spraying

Auth & identity
Jul 13, 2022
How Apple’s passkeys just brought us one step closer to a passwordless internet
Auth & identity
Product
Jun 2, 2022
4 Ways to use Stytch's Embeddable Magic Links

Auth & identity
May 4, 2022
Web3 and the future of data portability: rethinking user experiences and incentives on the internet

Auth & identity
Apr 22, 2022
Save time, save the planet–go passwordless!
Auth & identity
Mar 16, 2022
What is WebAuthn?

Auth & identity
Mar 12, 2022
Password reuse is a cybersecurity threat
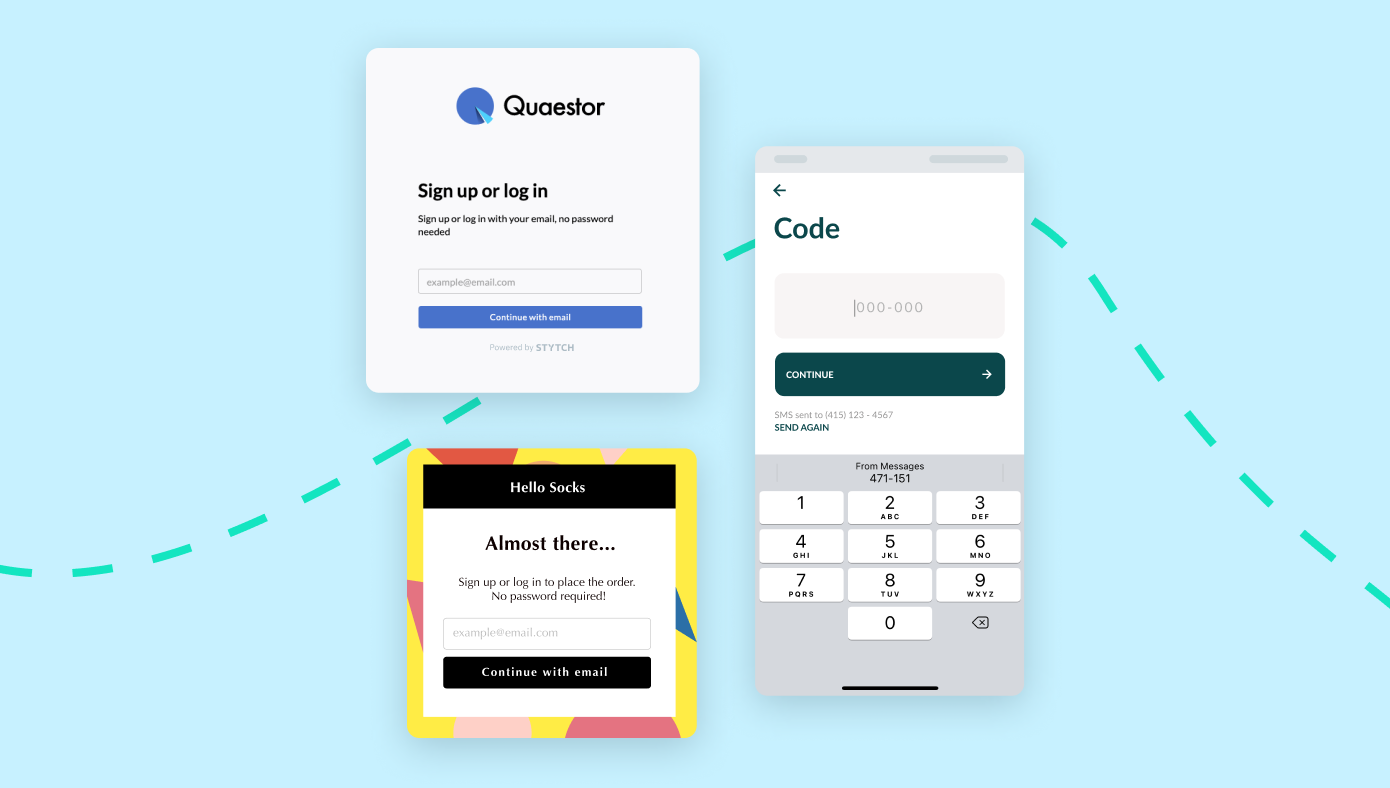
Auth & identity
Feb 24, 2022
Build vs. buy: what to consider when setting up an auth flow
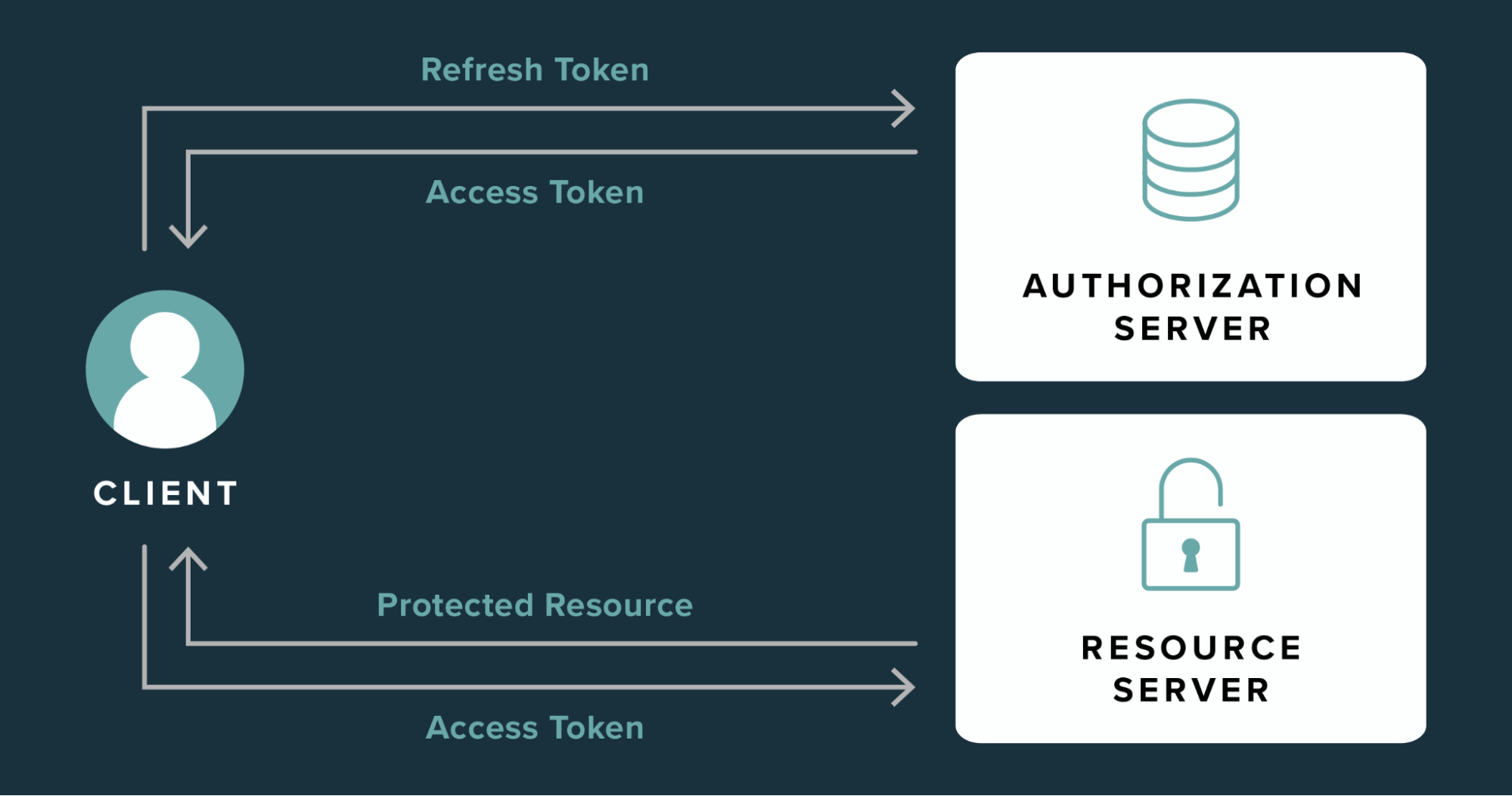
Auth & identity
Jan 28, 2022
What is the purpose of a refresh token?

Auth & identity
Jan 18, 2022
10 common cyber attacks
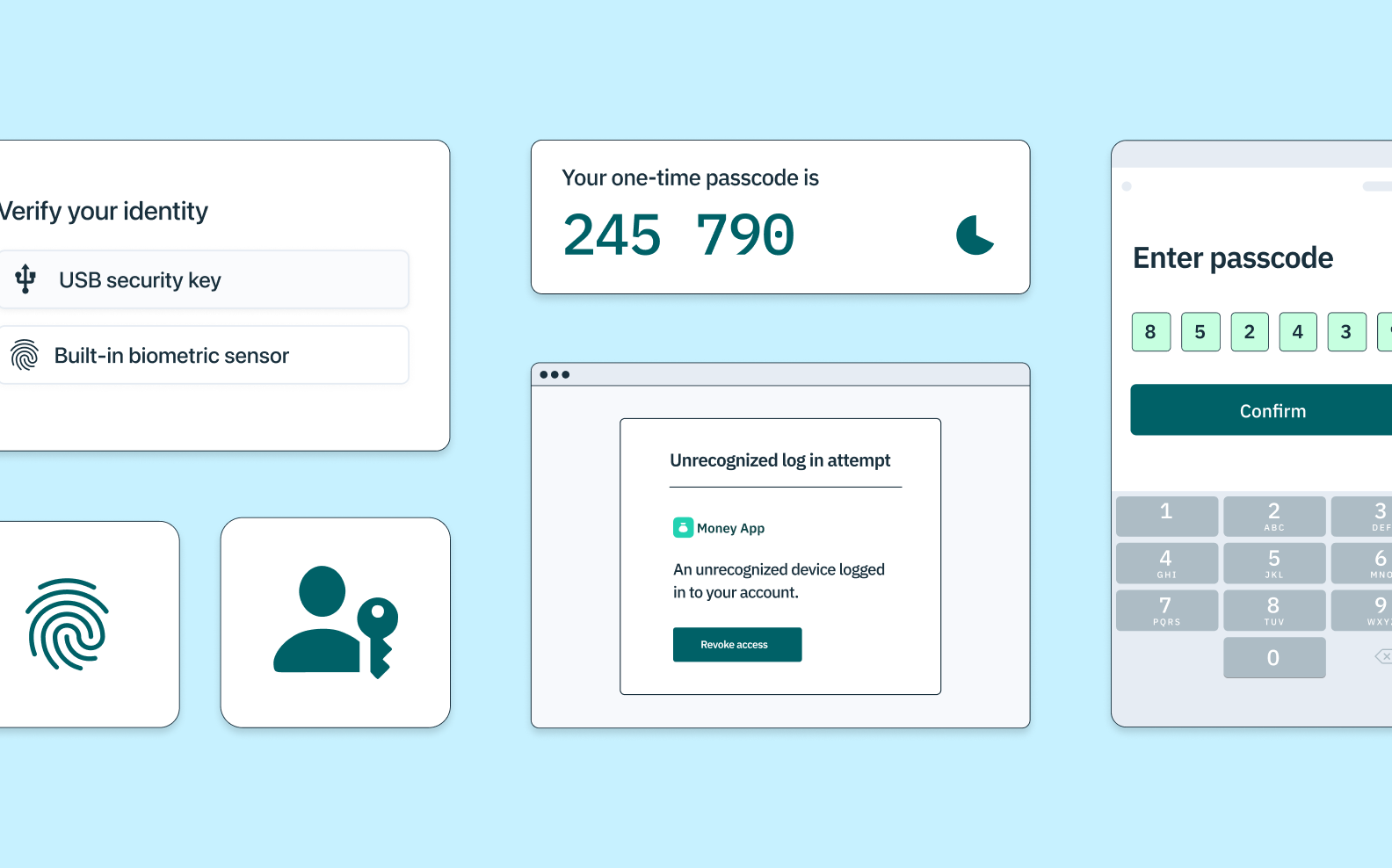
Auth & identity
Jan 10, 2022
What is MFA (Multi-Factor Authentication) and how does it work?

Auth & identity
Jan 5, 2022
What is credential stuffing? How to prevent credential stuffing attacks
Auth & identity
Dec 17, 2021
An introduction to WebAuthn

Auth & identity
Nov 12, 2021
A guide to passwordless authentication solutions by business vertical
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.