Auth & identity
Nov 10, 2025
AI agent authentication methods

Company
Latest
Oct 30, 2025
Stytch has joined Twilio to build the intelligent identity layer for the internet
Product
Oct 17, 2025
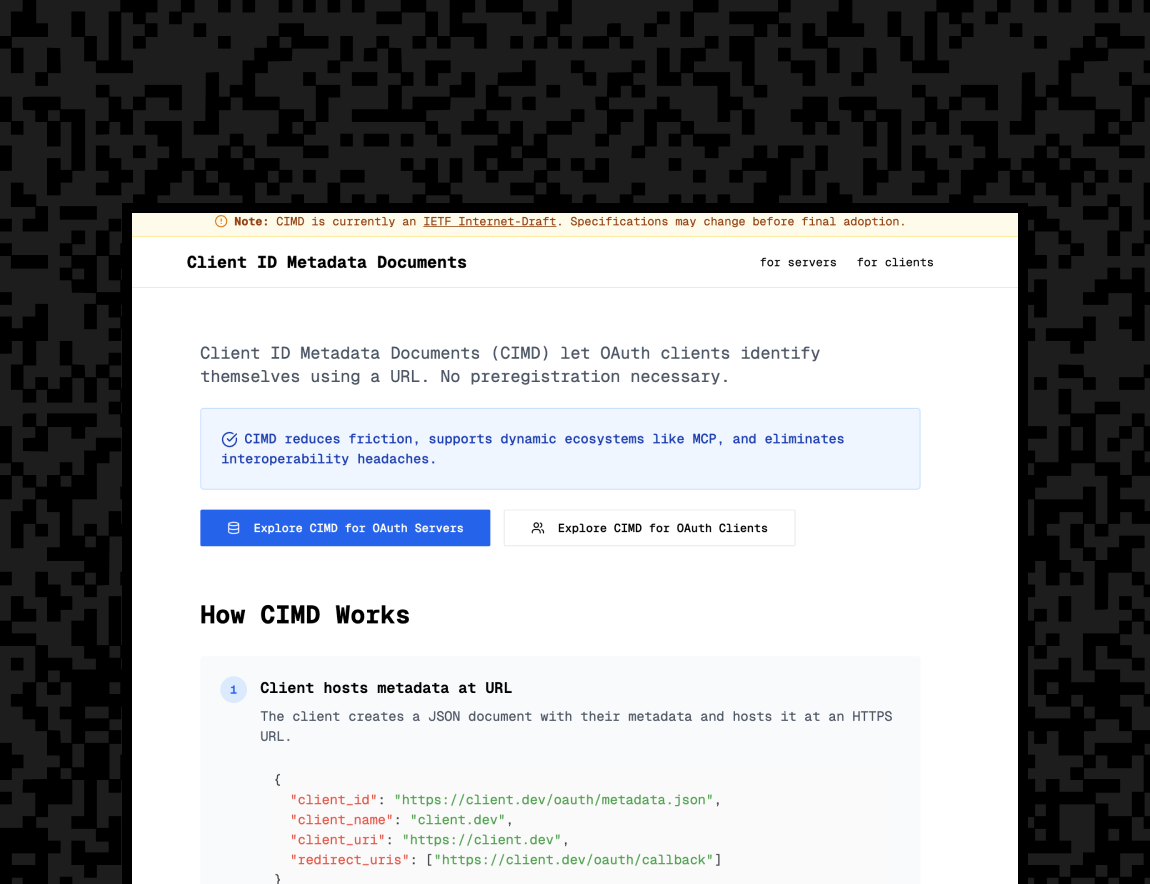
Stytch supports CIMD for OAuth

Auth & identity
Oct 8, 2025
Guide to authentication for the OpenAI Apps SDK
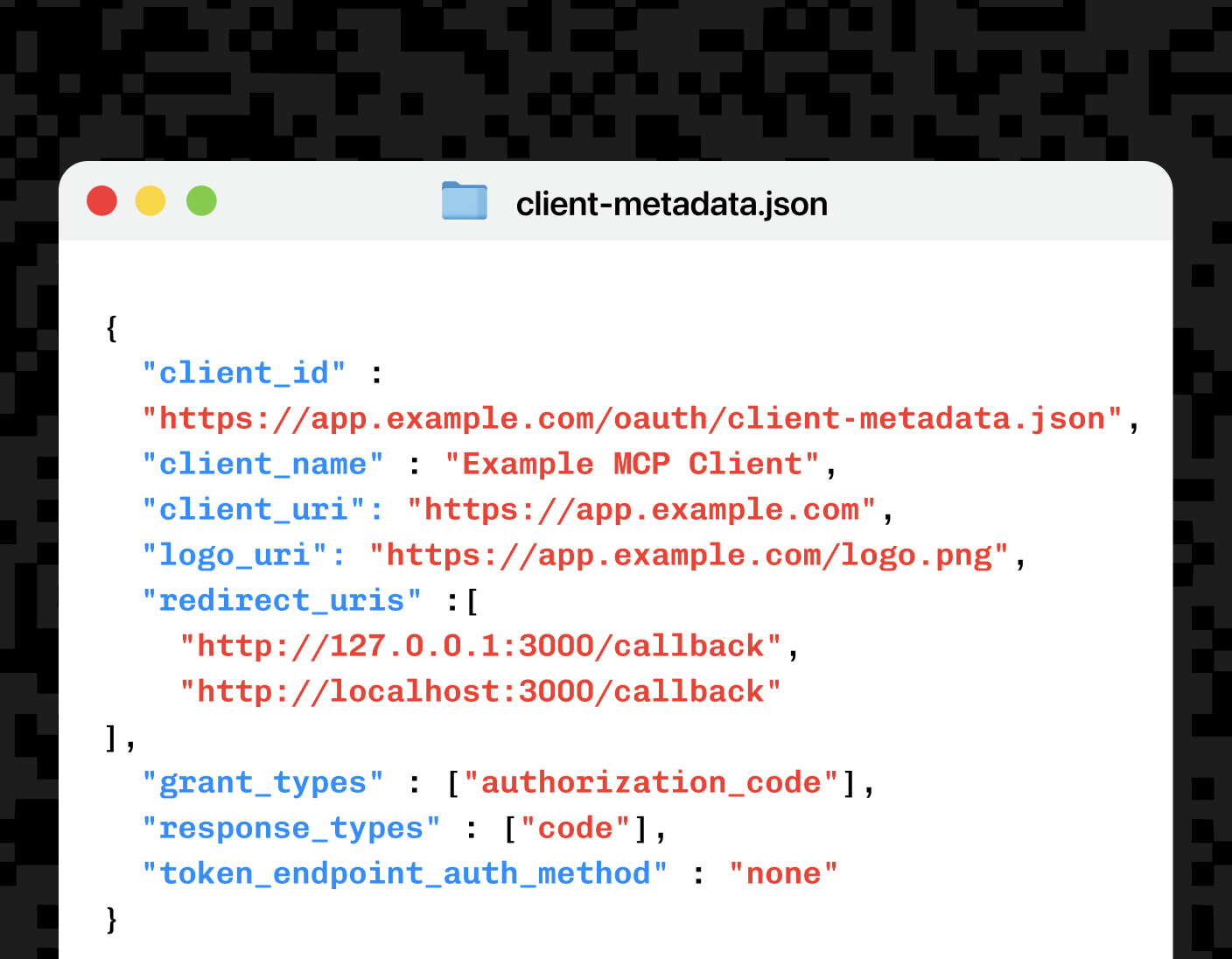
Auth & identity
Sep 29, 2025
Building MCP with OAuth Client ID Metadata (CIMD)
Auth & identity
Sep 29, 2025
AI agent authentication: securing your app for autonomous agent access

Auth & identity
Sep 24, 2025
Agent ready episode 8 with Anthropic, Cloudflare, and Arcade: evolving architectures for AI agents

Latest
Auth & identity
Product
Sep 23, 2025
Stytch supports Web Bot Auth for agent and bot verification

Latest
Auth & identity
Engineering
Sep 23, 2025
How to implement Web Bot Auth for your AI agent, bot, or crawler (and why you should)

Auth & identity
Sep 16, 2025
Agent ready episode 7 with Stytch: AI agent fraud and threat prevention
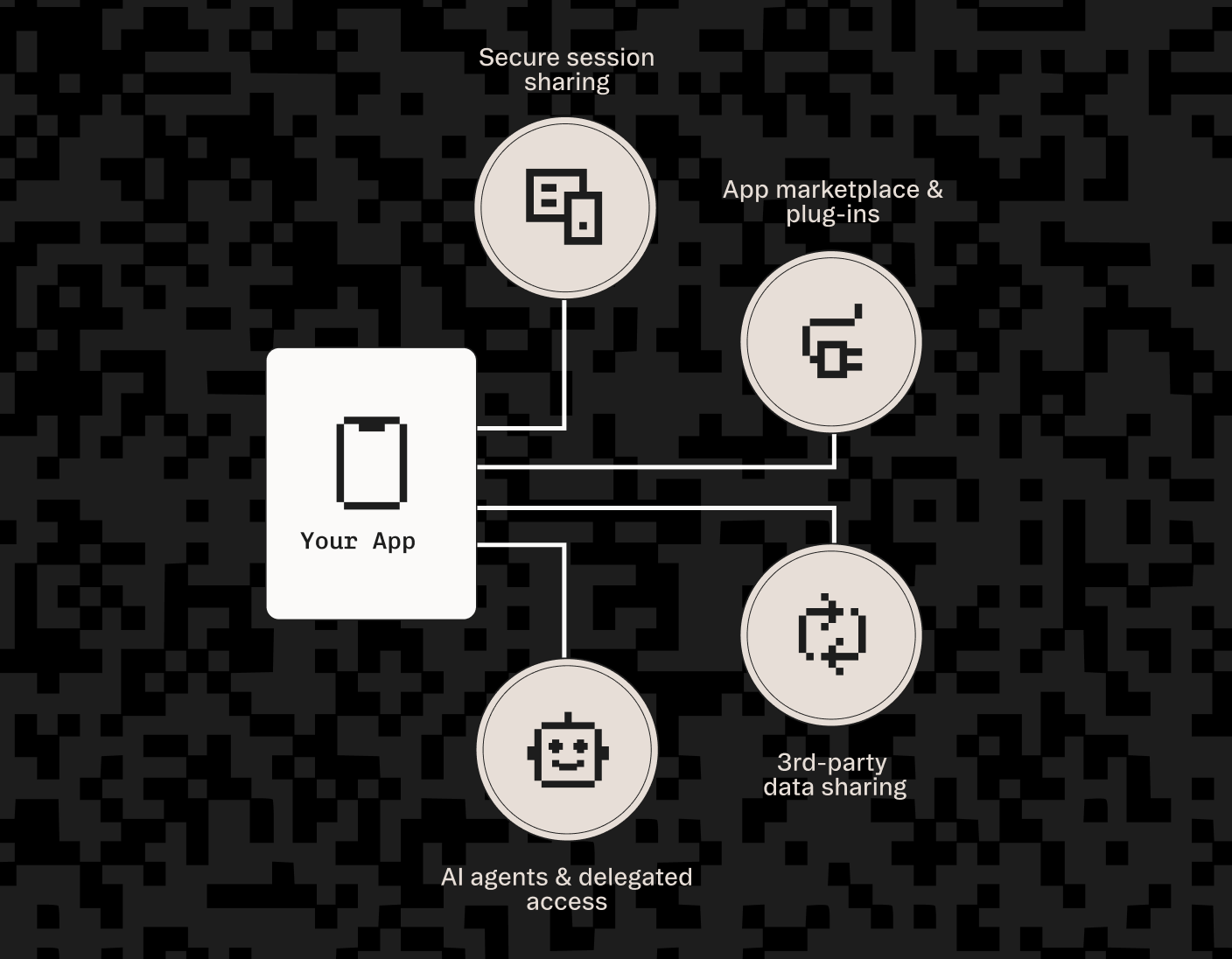
Product
Sep 9, 2025
Stytch Connected Apps: auth for AI Agents & MCP that fits within your existing identity stack

Auth & identity
Sep 4, 2025
Agent ready episode 6 with Honeycomb: observability & SLOs with AI agent workloads

Auth & identity
Sep 3, 2025
Agent ready episode 5 with Arcade: tool calling, orchestration, & agent development

Auth & identity
Aug 28, 2025
Agent ready episode 4 with Stytch: identity, auth + consent for AI agents

Auth & identity
Aug 26, 2025
Agent ready episode 3 with Cloudflare: deploying remote MCP at the edge
Auth & identity
Aug 21, 2025
Agent ready episode 2 with Stainless: auto-generating an MCP server & client

Auth & identity
Aug 19, 2025
Agent ready episode 1 with Langflow: RAG workflows & agent development
Auth & identity
Aug 18, 2025
Agent-to-agent OAuth: a guide for secure AI agent connectivity with MCP
Auth & identity
Aug 15, 2025
The top 7 passwordless authentication solutions for developers
Auth & identity
Aug 14, 2025
SCIM API explained: how it works and how to integrate with identity providers

Auth & identity
Aug 13, 2025
Sam Altman was wrong: AI didn’t defeat auth. Single factors did.
Auth & identity
Aug 12, 2025
What Is device fingerprinting? Guide and implementation techniques

Auth & identity
Aug 11, 2025
SCIM protocol: how it works, what it solves, and why it matters

SAML Shield
Aug 5, 2025
Introducing SAML Shield: open source protection for SAML CVEs
Engineering
Aug 1, 2025
Introducing IsAgent: understand and support AI agents using your site
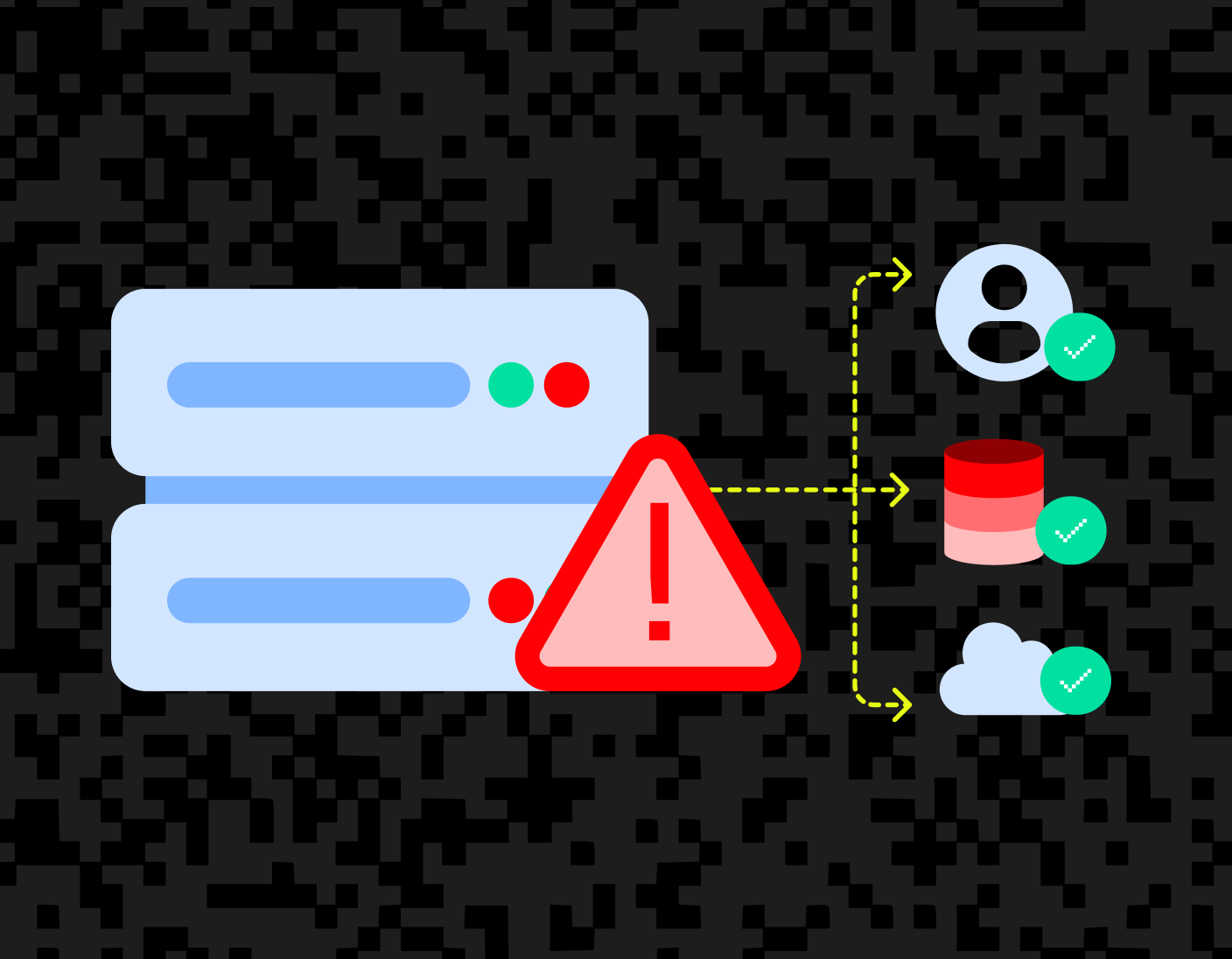
Auth & identity
Jul 23, 2025
Securing identity APIs against server-side request forgery (SSRF) at Stytch
Auth & identity
Jul 21, 2025
MCP authentication and authorization implementation guide
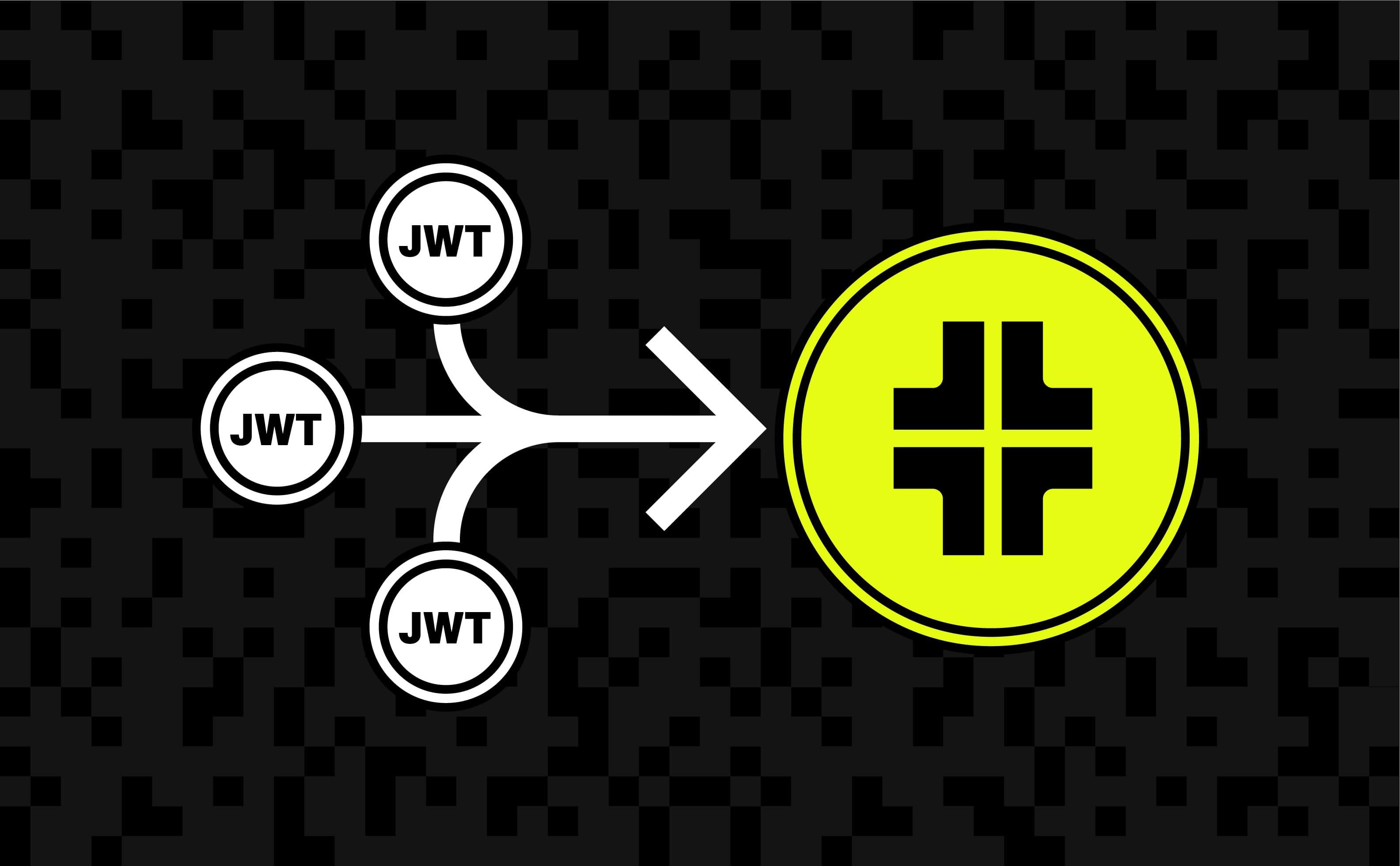
Product
Jul 18, 2025
Trusted Auth Tokens: handle any custom auth flow in minutes

Auth & identity
Jul 16, 2025
Browser fingerprinting: implementing fraud detection techniques in the era of AI
Auth & identity
Jul 16, 2025
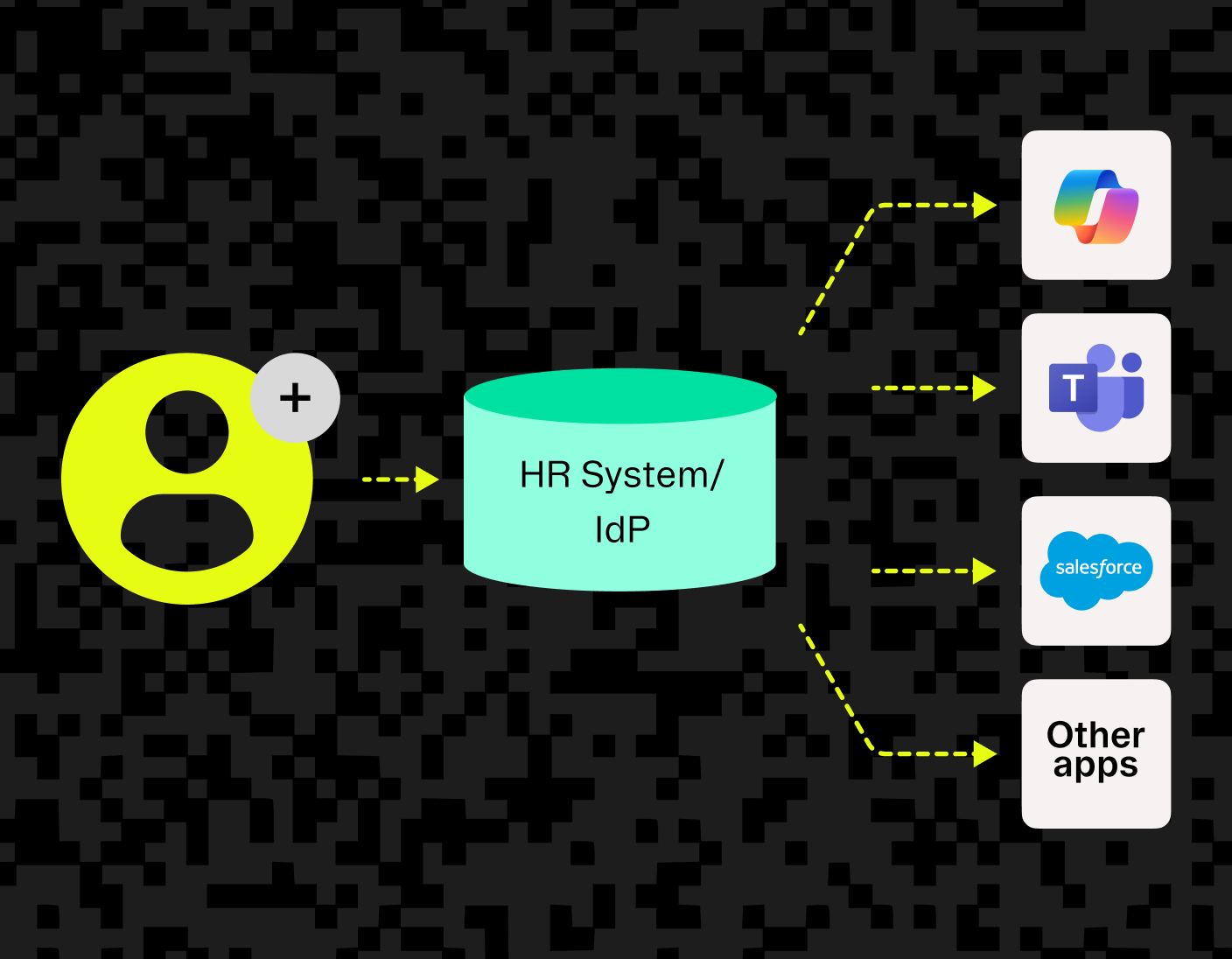
Top SCIM Tools to Streamline B2B Identity Management in 2025
Product
Jul 7, 2025
Introducing the Stytch MCP Server

Product
Jul 3, 2025
Combating AI Threats: Stytch's Device Fingerprinting
Auth & identity
Jun 30, 2025
How to secure model-agent interactions against MCP vulnerabilities
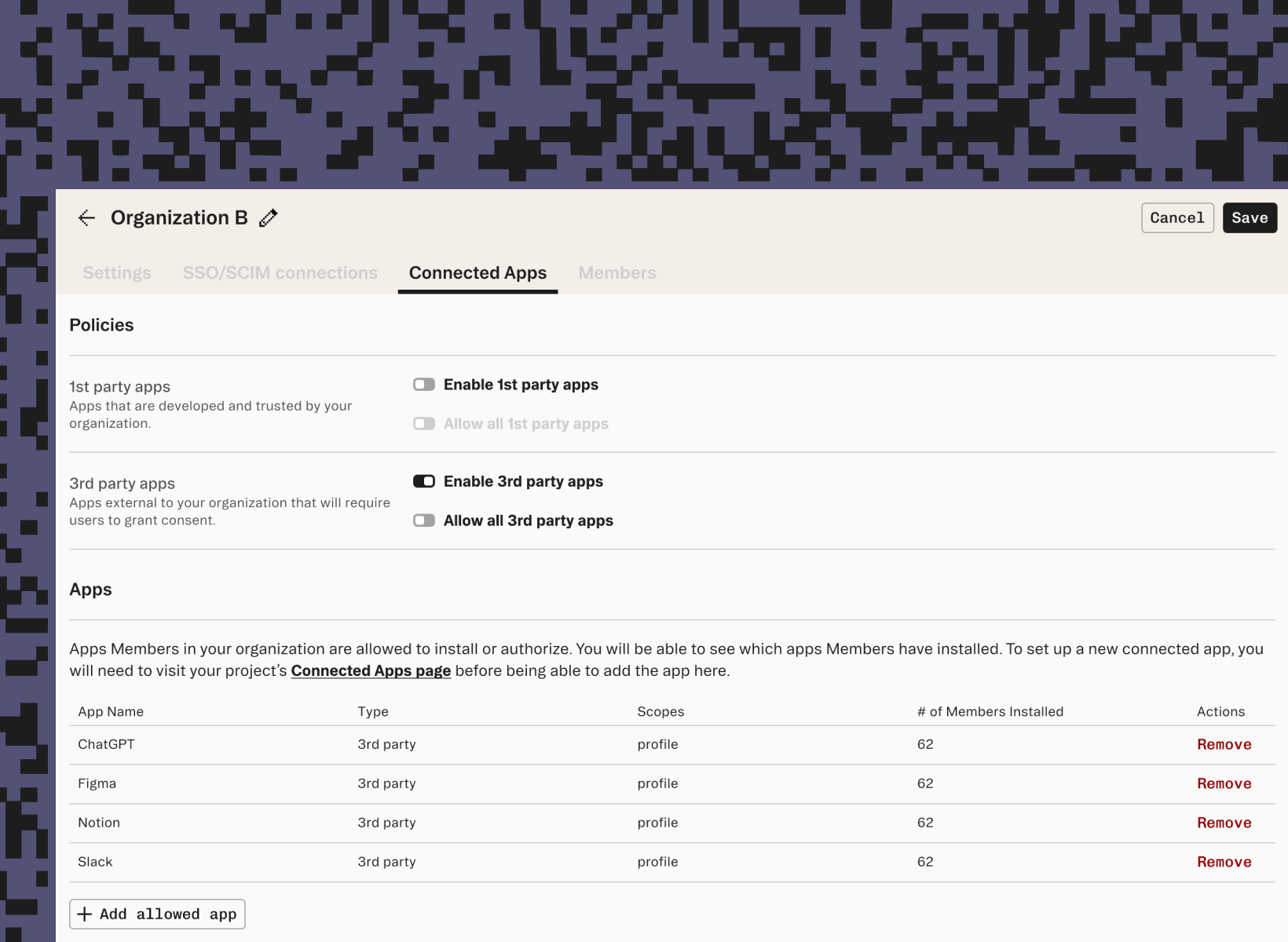
Product
Jun 17, 2025
Enabling consent for AI agents & apps with Connected Apps

Auth & identity
Jun 11, 2025
OAuth for MCP explained with a real-world example
Auth & identity
Jun 4, 2025
The age of agent experience: now with MCP servers
Auth & identity
Jun 4, 2025
How to secure MCP: threats and defenses

Auth & identity
Jun 4, 2025
Bears, mice, and moles aren’t enough: a better approach for preventing fraud
Product
May 23, 2025
Stytch Component Playground: a live UI builder for your next login flow

Product
May 22, 2025
Unified mobile biometrics: ship faster, support everyone
Auth & identity
SAML Shield
May 21, 2025
SAML example: what is SAML and how do you use It?
Auth & identity
May 21, 2025
AI agent fraud: key attack vectors and how to defend against them
Auth & identity
May 21, 2025
How to block AI web crawlers: challenges and solutions
Engineering
May 21, 2025
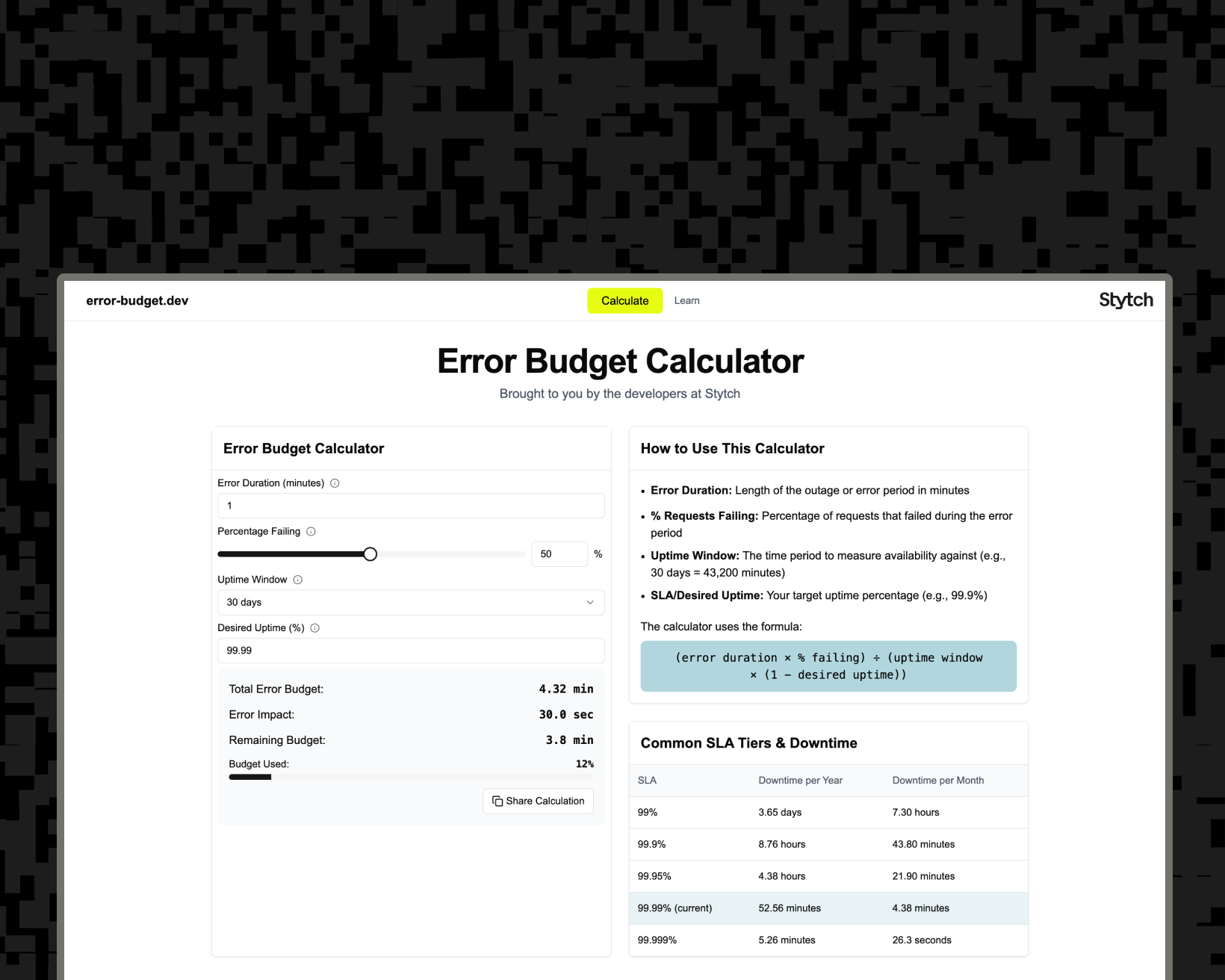
Understanding SLAs, SLOs, SLIs and Error Budgets
Engineering
May 20, 2025
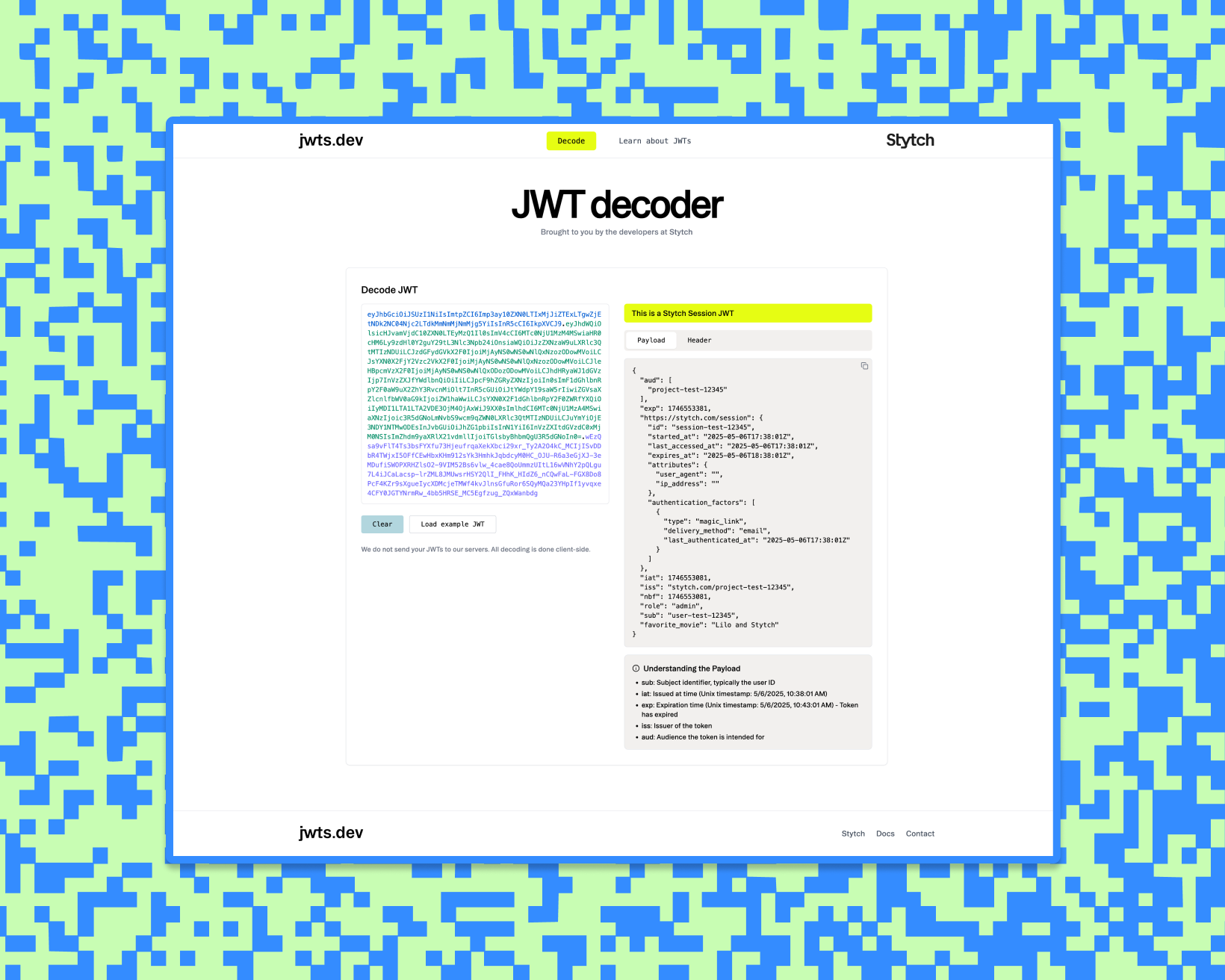
jwts.dev: decode and learn about JWTs in one place

Auth & identity
May 19, 2025
If an AI agent can’t figure out how your API works, neither can your users
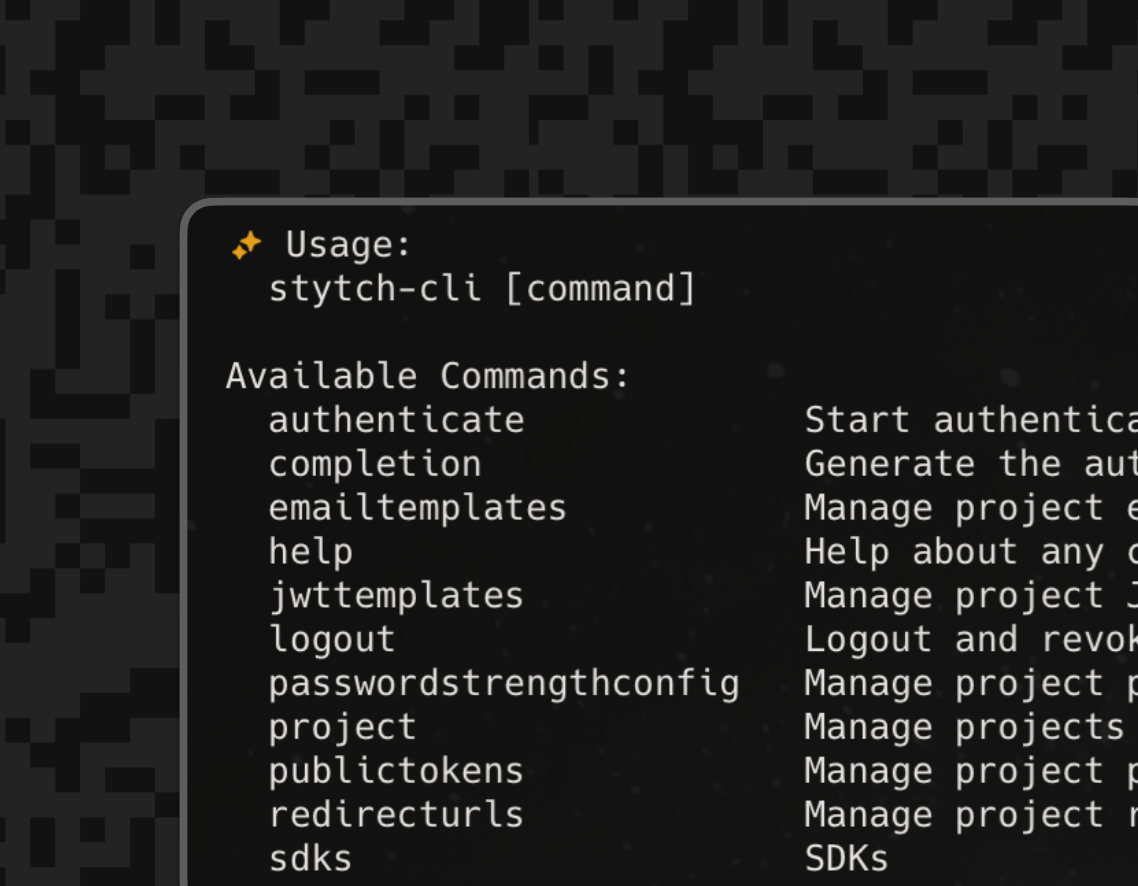
Product
May 19, 2025
Using Connected Apps to build the Stytch CLI and improve the Stytch integration experience

Company
May 18, 2025
Why we hack: the culture of company hackathons at Stytch

Auth & identity
May 2, 2025
npm-audit for MCP security: A deep-dive on mcp-scan
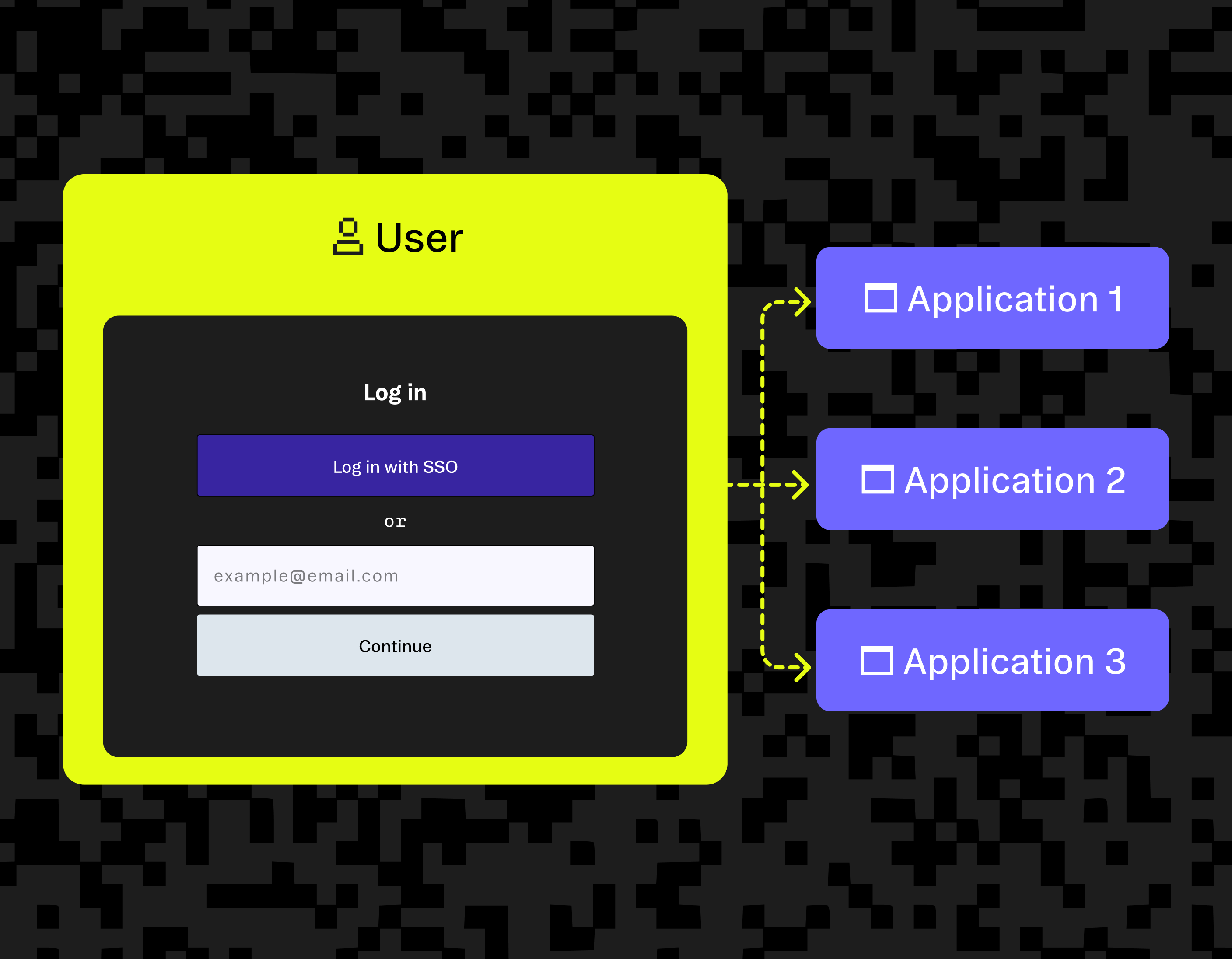
Auth & identity
Apr 25, 2025
Single Sign-On example

Auth & identity
Apr 19, 2025
Building an MCP server with OAuth and Cloudflare Workers

Auth & identity
Apr 17, 2025
What is a SAML service provider? How to integrate your app with enterprise Single Sign-On
Auth & identity
Apr 16, 2025
The best authentication services in 2025
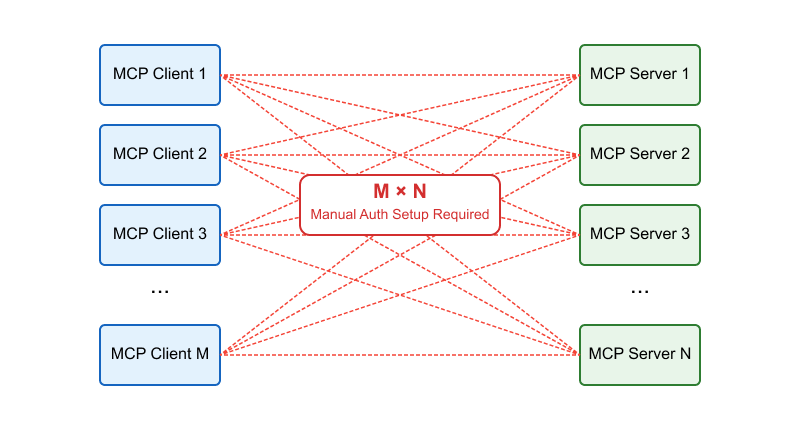
Auth & identity
Apr 12, 2025
MCP and OAuth Dynamic Client Registration
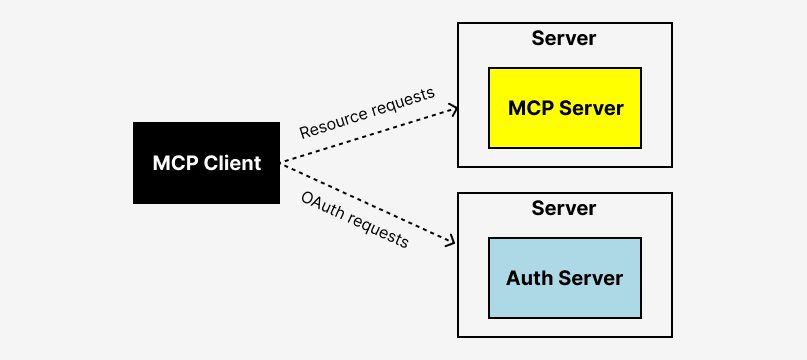
Auth & identity
Apr 11, 2025
MCP authentication and authorization servers
Product
Apr 7, 2025
Secure agent access in Remote MCP with Stytch and Cloudflare
Auth & identity
Apr 4, 2025
Handling AI agent permissions
Auth & identity
Apr 3, 2025
Stytch vs Auth0: Bot detection

Auth & identity
Apr 2, 2025
OAuth 2.1 vs 2.0: What developers need to know
Auth & identity
Mar 29, 2025
AI agent security explained

Auth & identity
Mar 28, 2025
Model Context Protocol (MCP): A comprehensive introduction for developers

Auth & identity
Mar 28, 2025
A developer’s guide to RFC 7519, part 1: JWT structure and claims
Auth & identity
Mar 28, 2025
Authentication as a service: Launch faster with stronger security
Auth & identity
Mar 22, 2025
Multi-factor authentication solutions: Choosing the best MFA provider for your use case
Auth & identity
Mar 21, 2025
Auth0 reviews: Why developers migrate from Auth0 to Stytch
Engineering
Mar 15, 2025
How to create a closed source Objective-C++ framework for Swift Package Manager
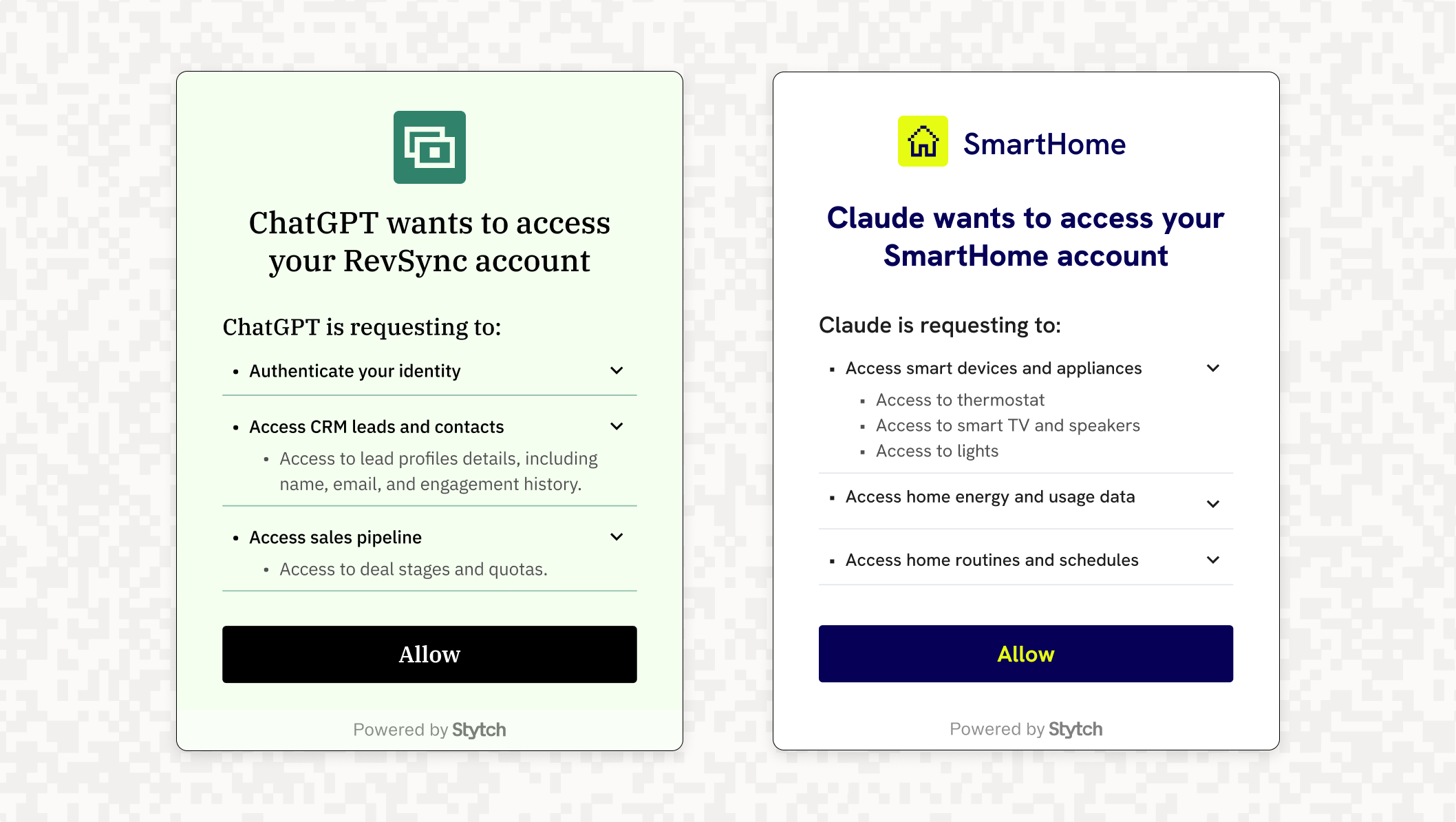
Auth & identity
Mar 8, 2025
Connecting AI agents to every app
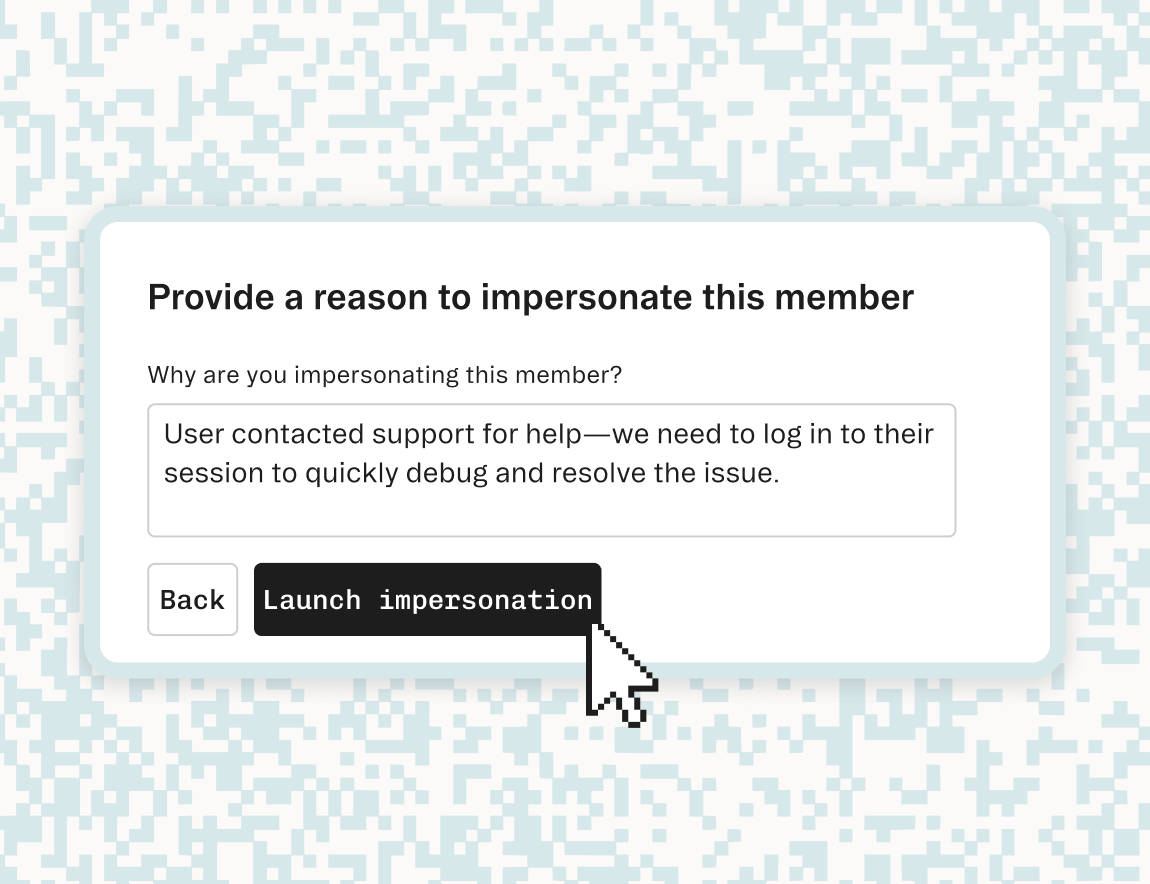
Product
Feb 22, 2025
Stytch User Impersonation: Fast, secure troubleshooting
Product
Feb 22, 2025
Stytch Terraform: Now generally available
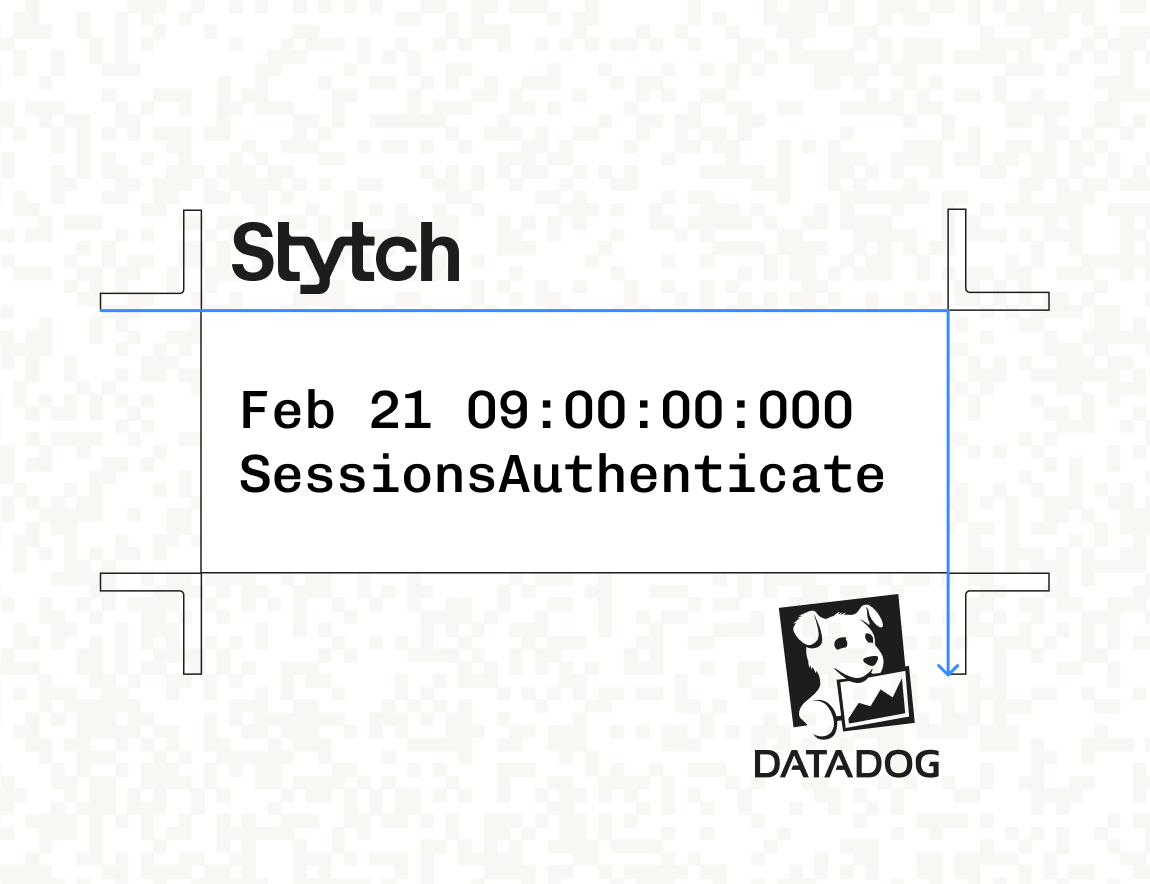
Product
Feb 22, 2025
Stytch Event Log Streaming: Send auth & risk insights to your observability tools
Product
Feb 21, 2025
Stytch Admin Portal: Self-serve management for organizations and enterprise auth
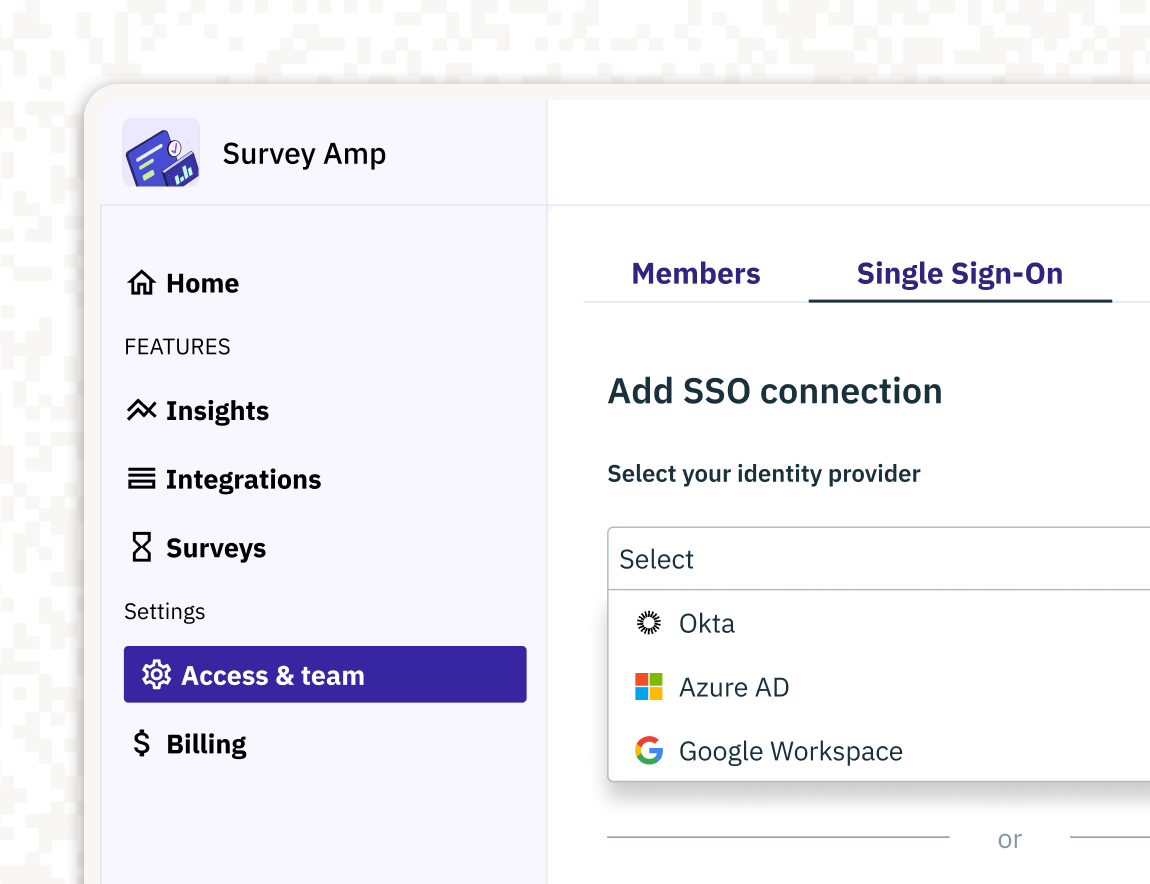
Product
Feb 20, 2025
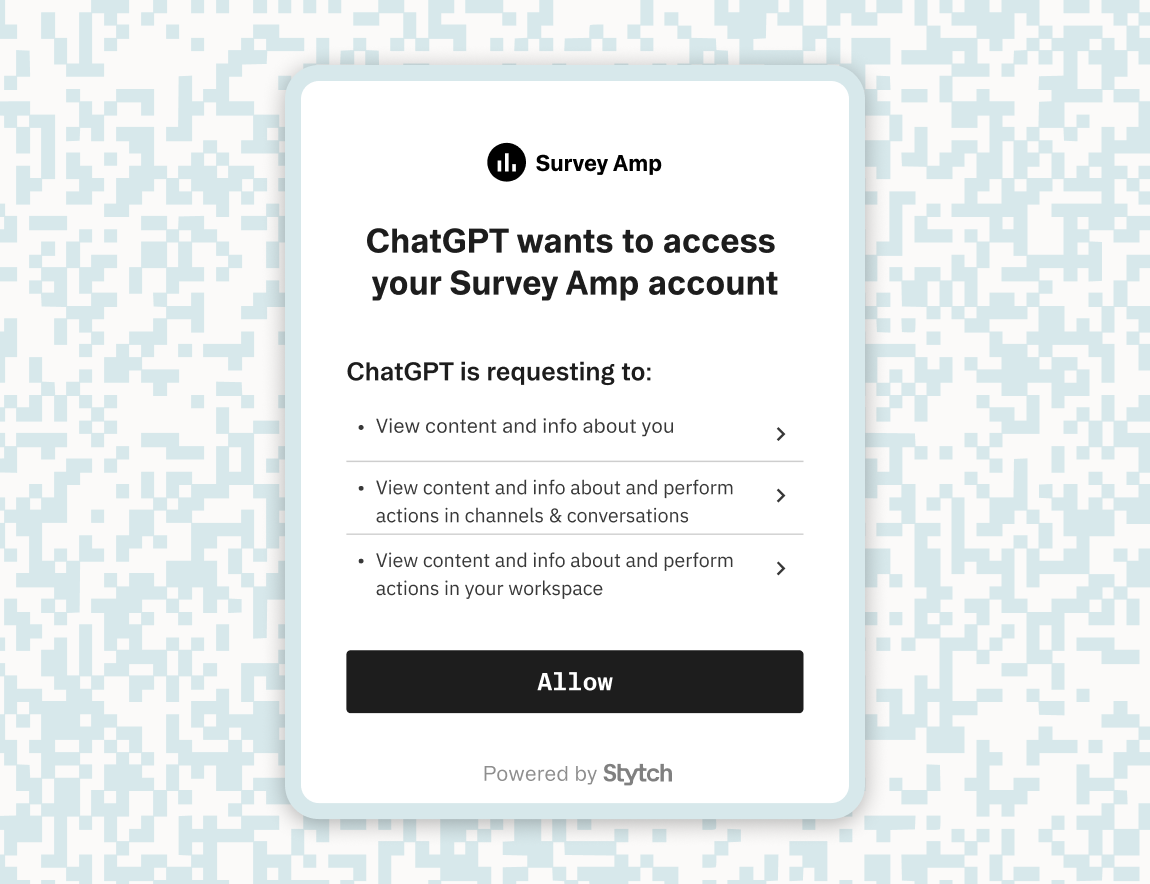
Stytch Connected Apps: Make any app an OAuth provider for integrations and AI agents
Product
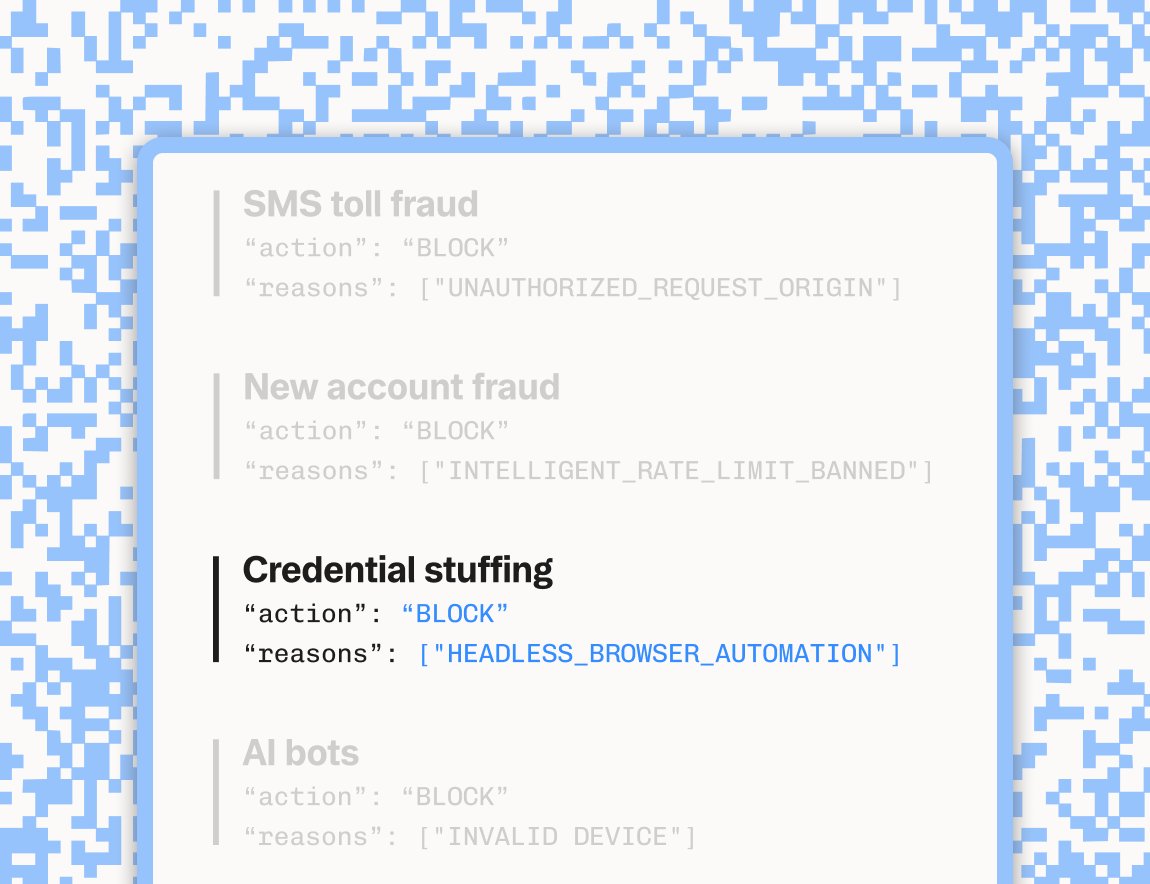
Feb 19, 2025
Stytch Fraud & Risk Prevention: Intelligent Rate Limiting, real-time monitoring, and more

Company
Feb 15, 2025
Rebranding Stytch: A new look for the future of auth and security
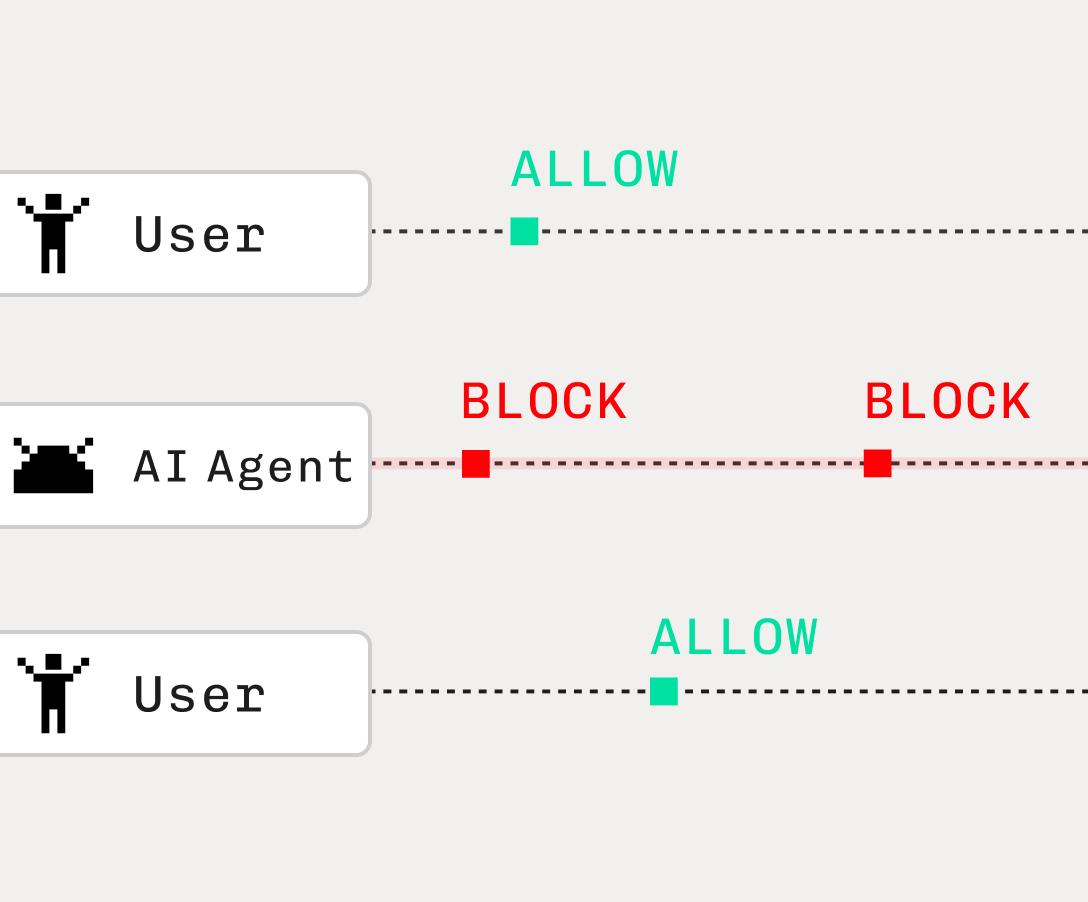
Auth & identity
Feb 15, 2025
Detecting AI agent use & abuse

Auth & identity
Feb 8, 2025
The age of agent experience
Auth & identity
Jan 4, 2025
Why email verification is crucial for B2B applications
Auth & identity
Jan 3, 2025
Bot Detection 101: How to Detect (and Beat) Bot Traffic

Auth & identity
Dec 3, 2024
What Is Anonymous Visitor Identification? How to Identify Visitors to your Website or App

Company
Nov 20, 2024
Announcing Stytch’s new Self-serve pricing: No feature gating, no hard caps, no surprises
Auth & identity
Nov 15, 2024
Canvas fingerprinting: Explained and illustrated

Auth & identity
Nov 1, 2024
Stytch Embedded Auth vs. Auth0 Universal Login
Auth & identity
Oct 31, 2024
Auth0's Security Incidents: How JWT Vulnerabilities Have Repeatedly Impacted the Platform
Auth & identity
Oct 24, 2024
Top techniques for effective API rate limiting

Auth & identity
Oct 17, 2024
Anti-spoofing tools and techniques

Auth & identity
Oct 2, 2024
Top strategies to prevent web scraping and protect your data

Auth & identity
Sep 25, 2024
Auth0 2024 Pricing Update: What They’re Hiding About the Real Cost

Auth & identity
Sep 25, 2024
Adaptive MFA: A smarter approach to authentication security

Auth & identity
SAML Shield
Sep 4, 2024
SAML certificates explained

Auth & identity
Aug 28, 2024
Spotting the spoof: User agent spoofing unmasked
Auth & identity
SAML Shield
Aug 22, 2024
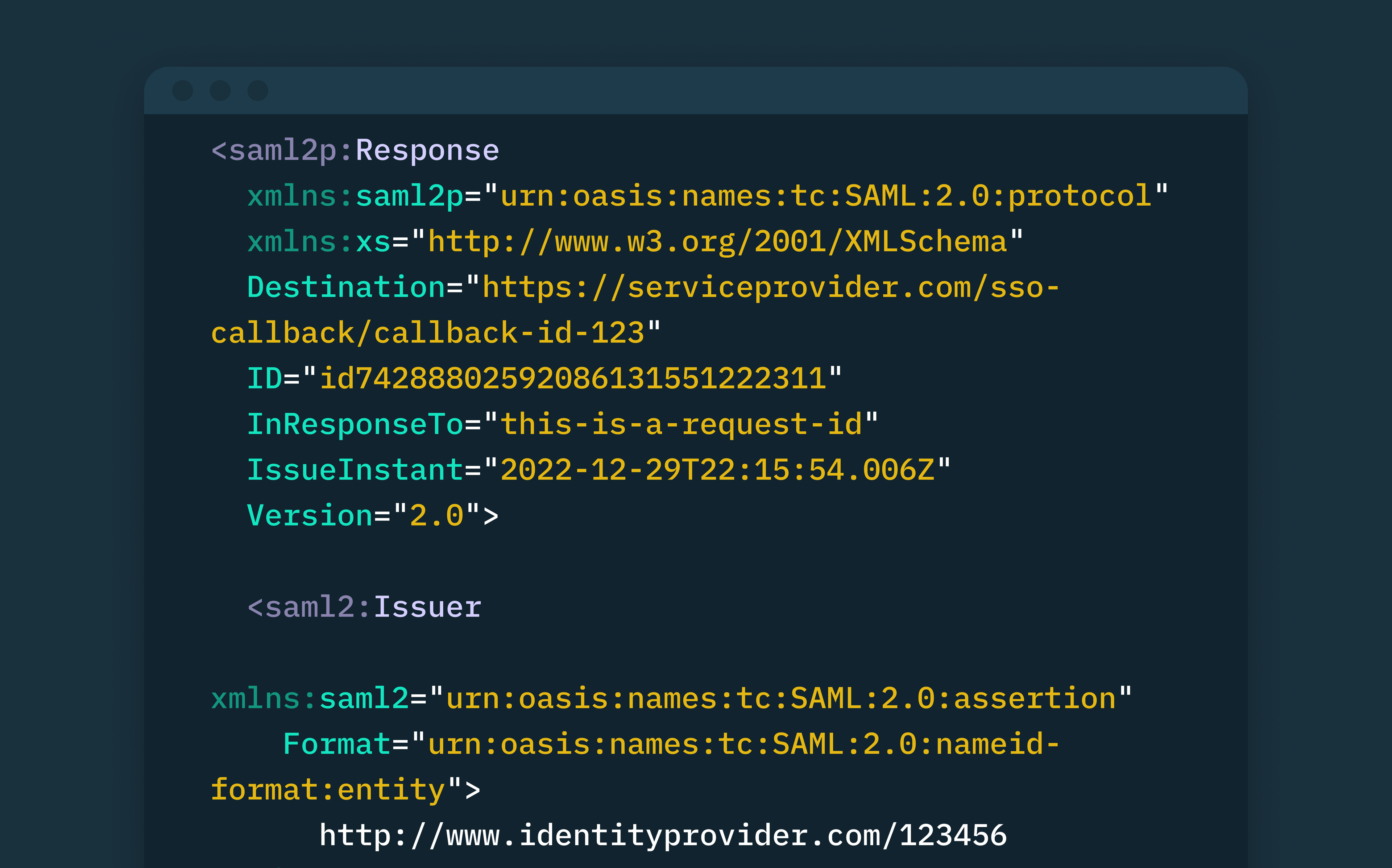
What are SAML assertions?
Auth & identity
Aug 8, 2024
SAML vs LDAP: What's the difference?

Auth & identity
Aug 1, 2024
SAML vs OAuth: Key Differences Explained
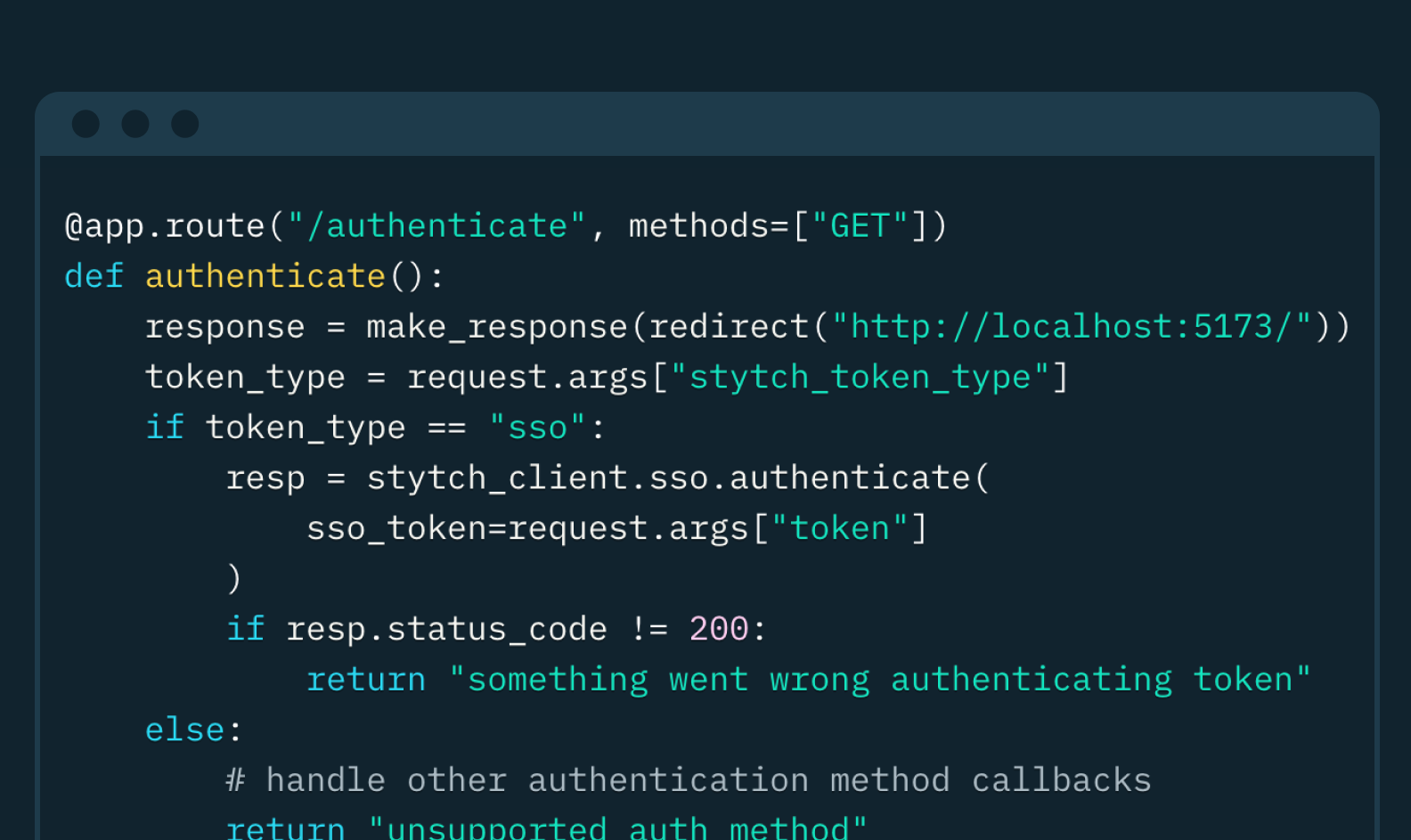
Auth & identity
Jul 25, 2024
Integrating SAML Single Sign-On with Python, Okta, and Stytch

Auth & identity
Jul 23, 2024
Stopping an account takeover before it takes a toll
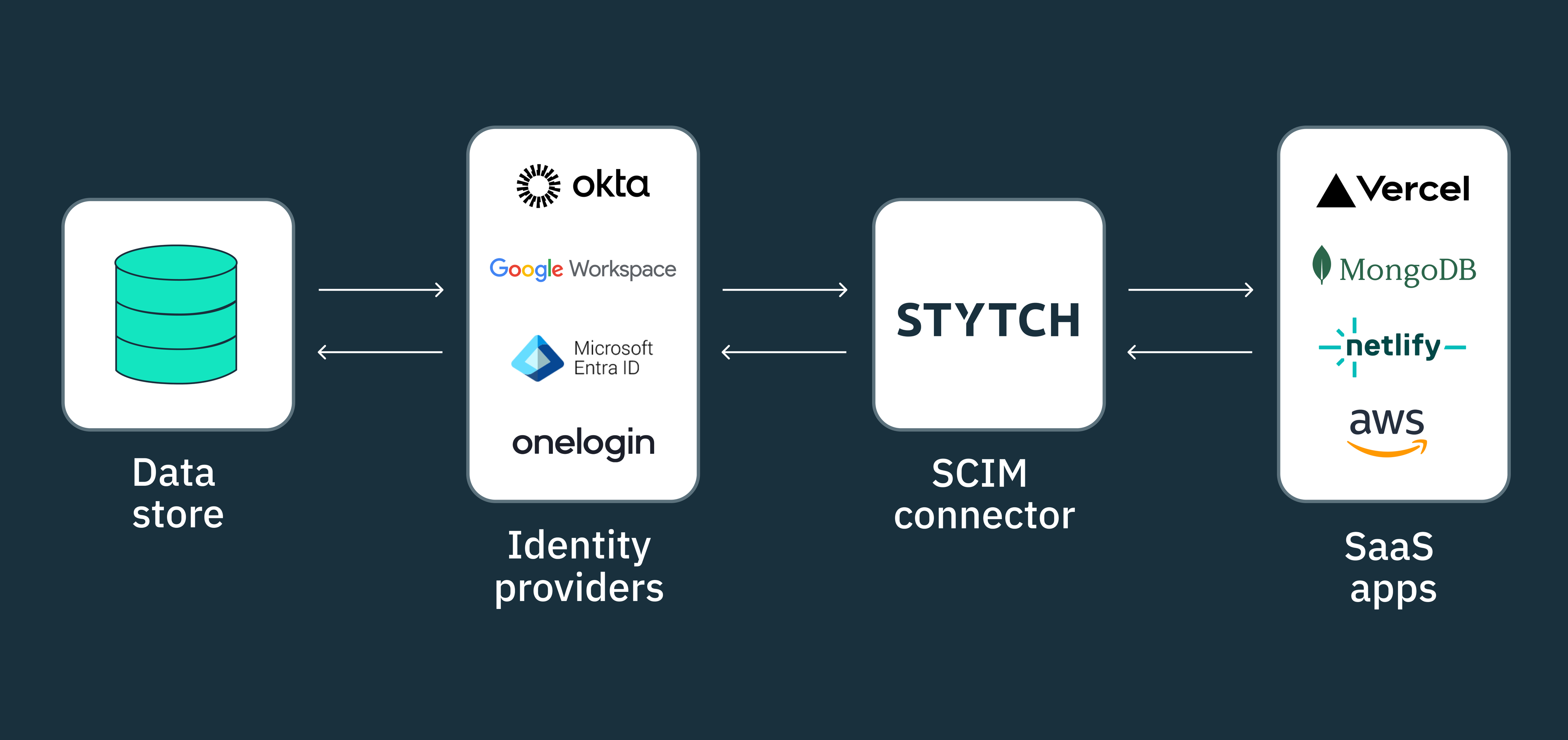
Auth & identity
Jul 9, 2024
SCIM API: Your comprehensive guide and introduction
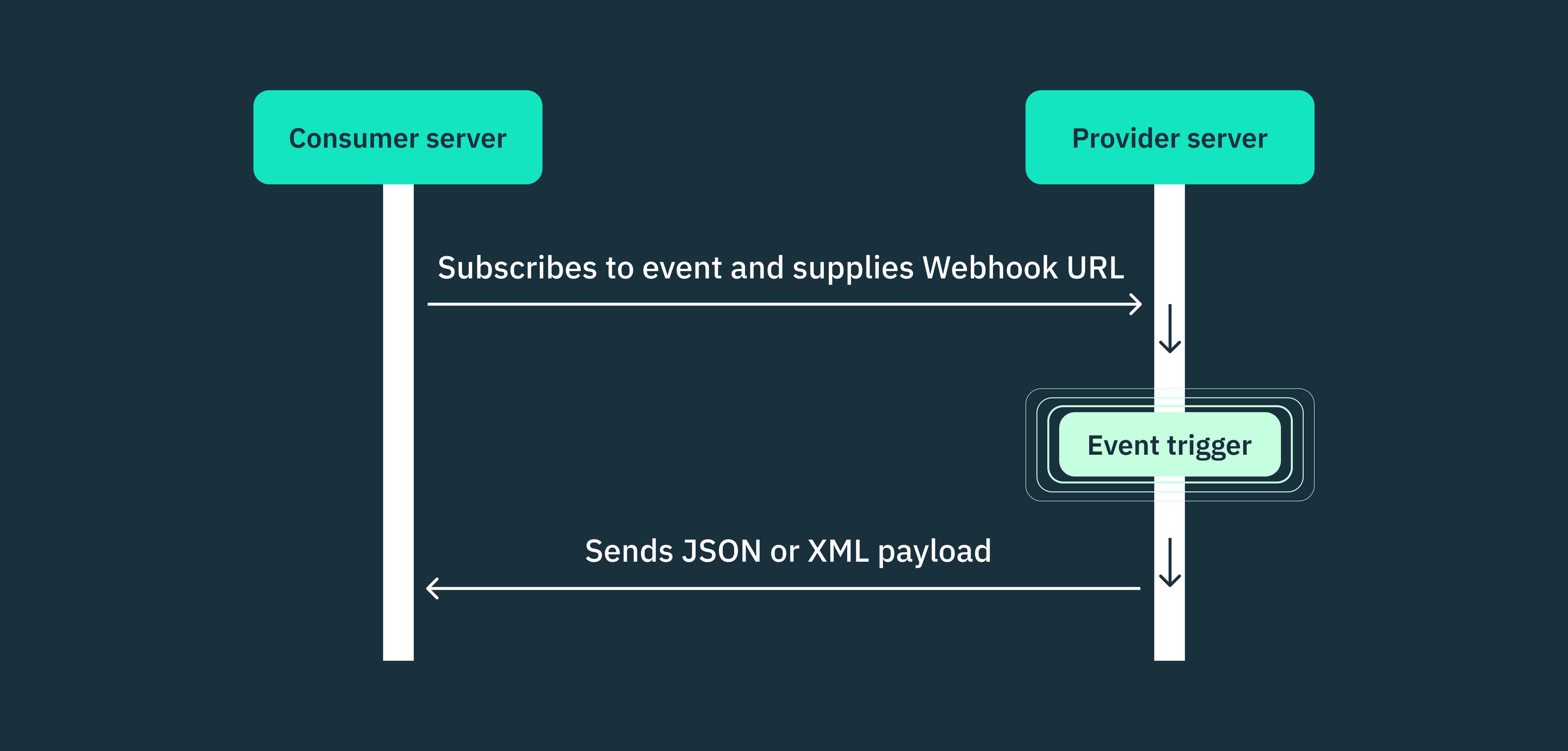
Auth & identity
Engineering
Jun 28, 2024
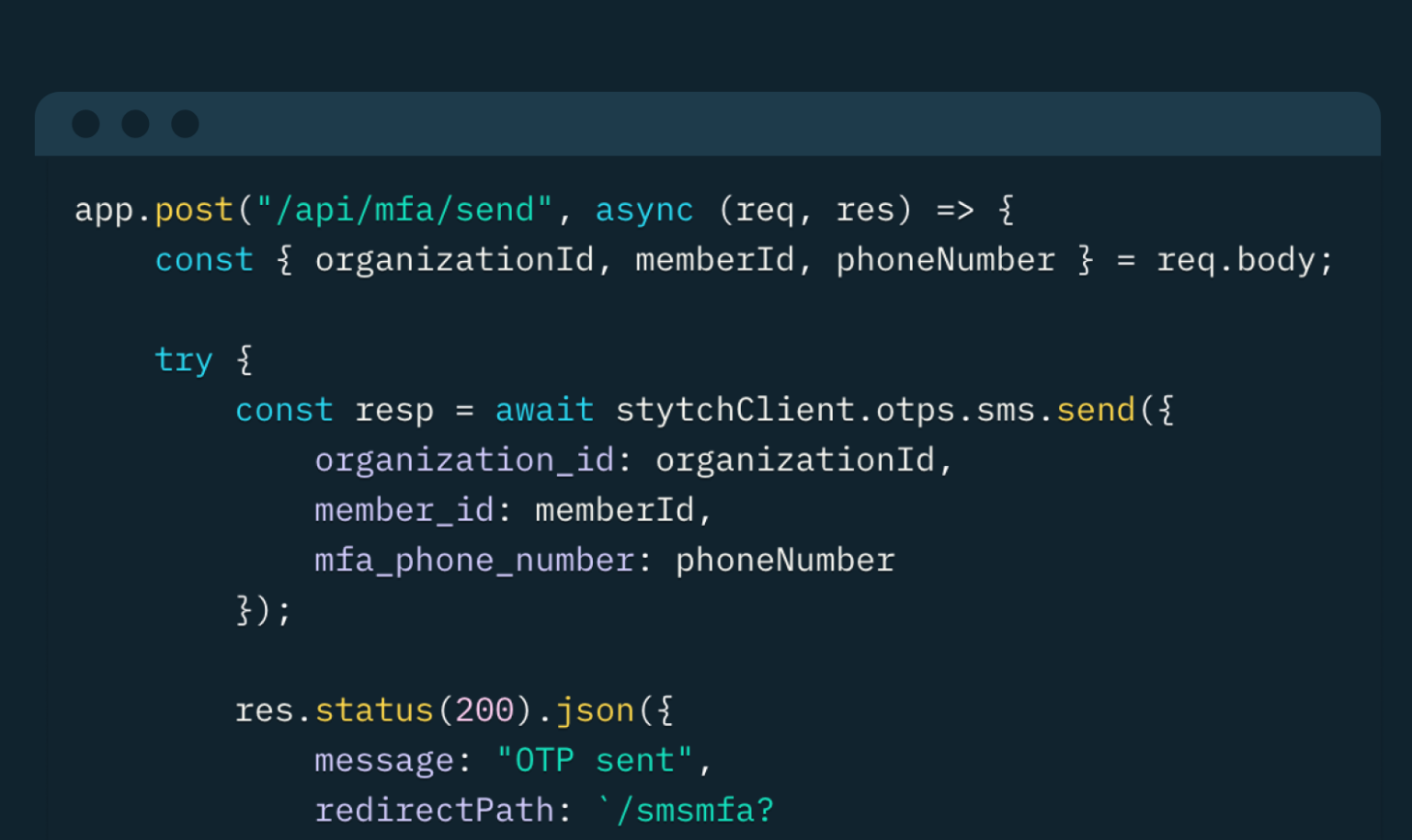
Webhooks security best practices
Auth & identity
Jun 25, 2024
Application security in the age of artificial intelligence: adapting to new challenges and opportunities
Auth & identity
Jun 12, 2024
What is SCIM and how does it work?

Auth & identity
Jun 11, 2024
CAPTCHA vs. reCAPTCHA: What’s the difference?
Auth & identity
May 30, 2024
How to Enforce Multi-Factor Authentication with Node.js and Stytch

Auth & identity
May 24, 2024
Webhooks vs APIs
Auth & identity
May 22, 2024
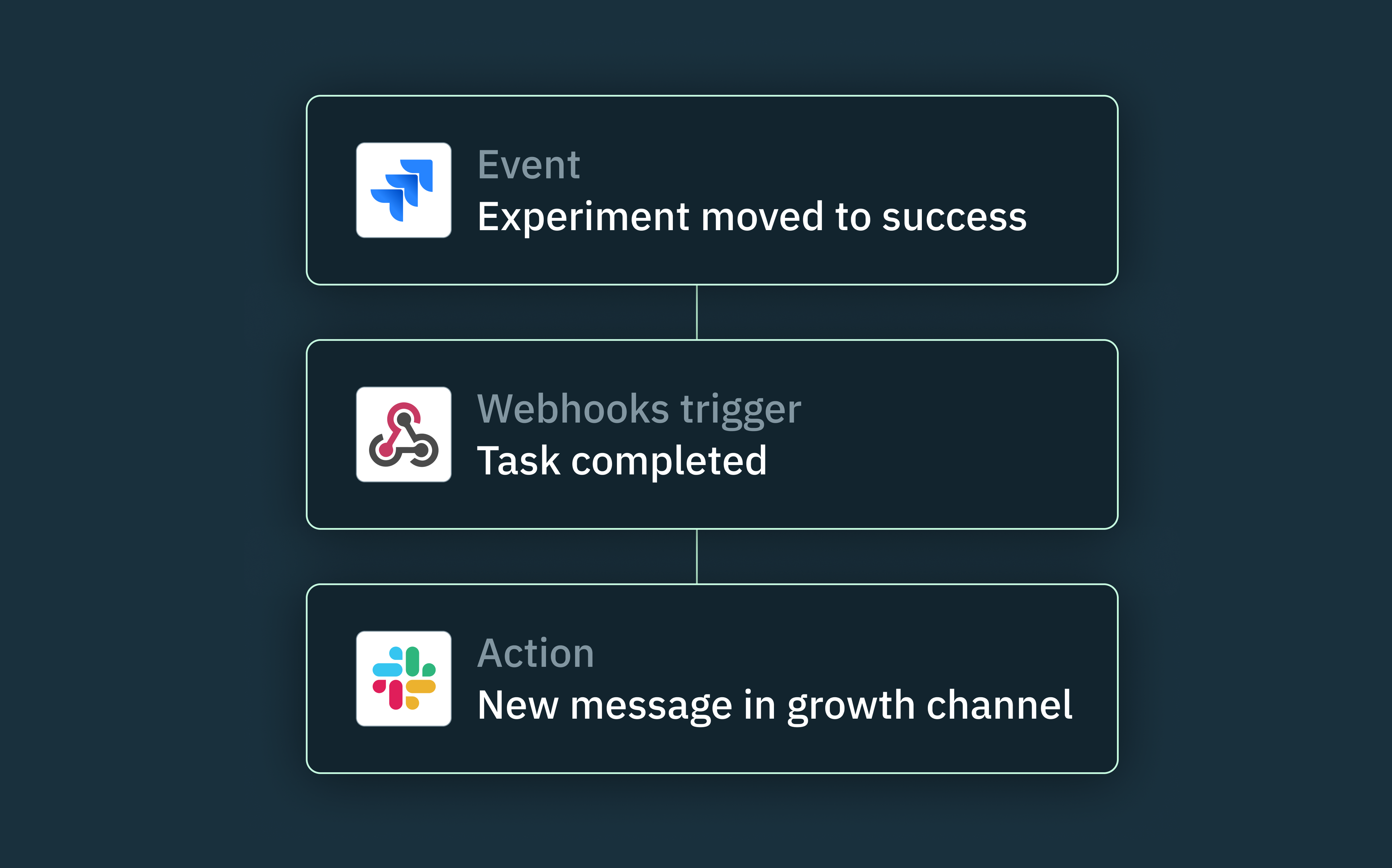
What are webhooks?

Product
Apr 30, 2024
Introducing major updates to Stytch B2B authentication
Product
Apr 29, 2024
Stytch multi-tenant example apps
Product
Apr 11, 2024
Why Switch to Stytch?
Product
Apr 11, 2024
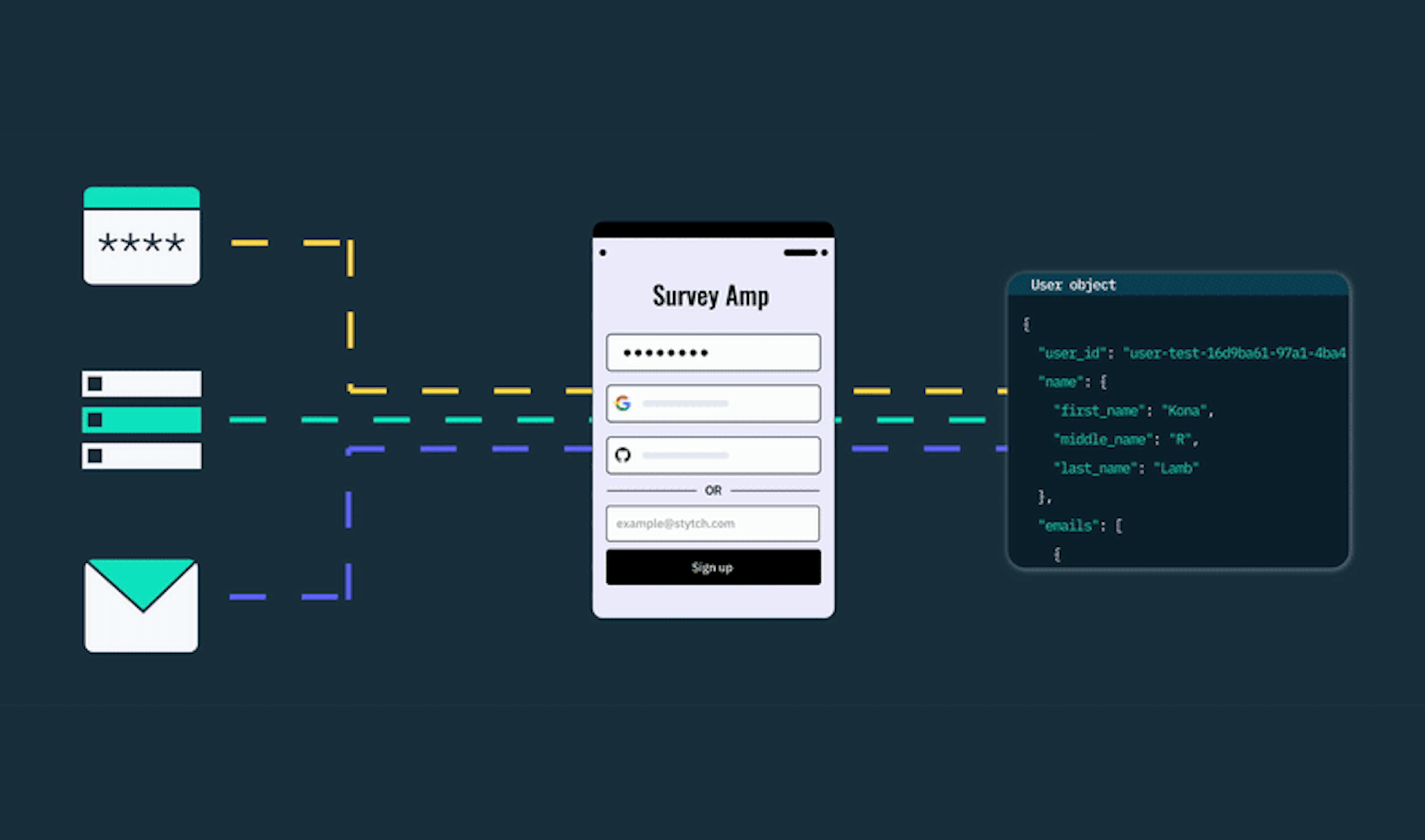
Out-of-the-box: User linking and provider failover with Stytch

Auth & identity
Apr 9, 2024
Account Abuse Prevention
Auth & identity
Mar 14, 2024
Session management best practices

Auth & identity
Mar 5, 2024
Managing user sessions: localStorage vs sessionStorage vs cookies
Auth & identity
Mar 5, 2024
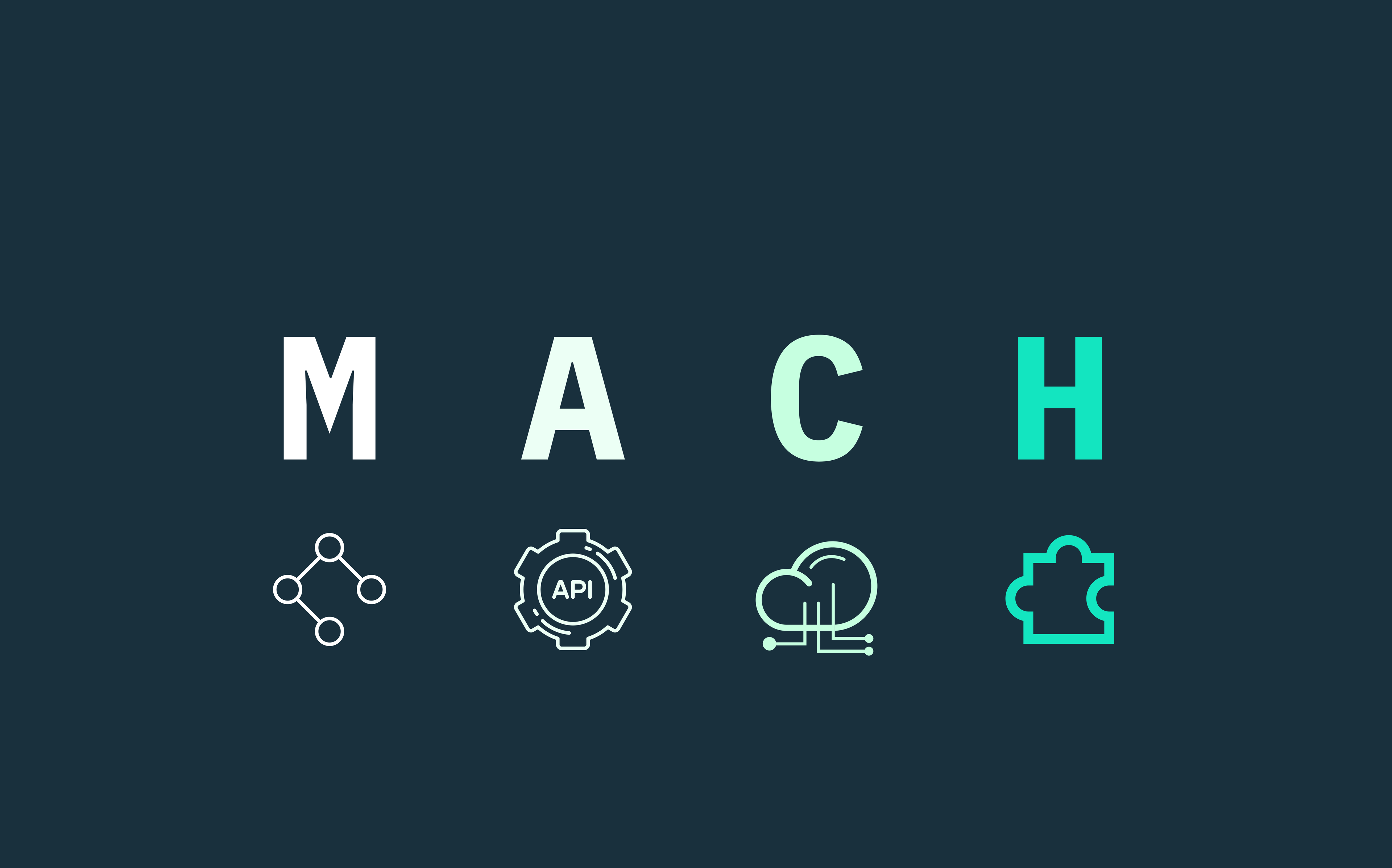
Unpacking MACH architecture: The future of SaaS development
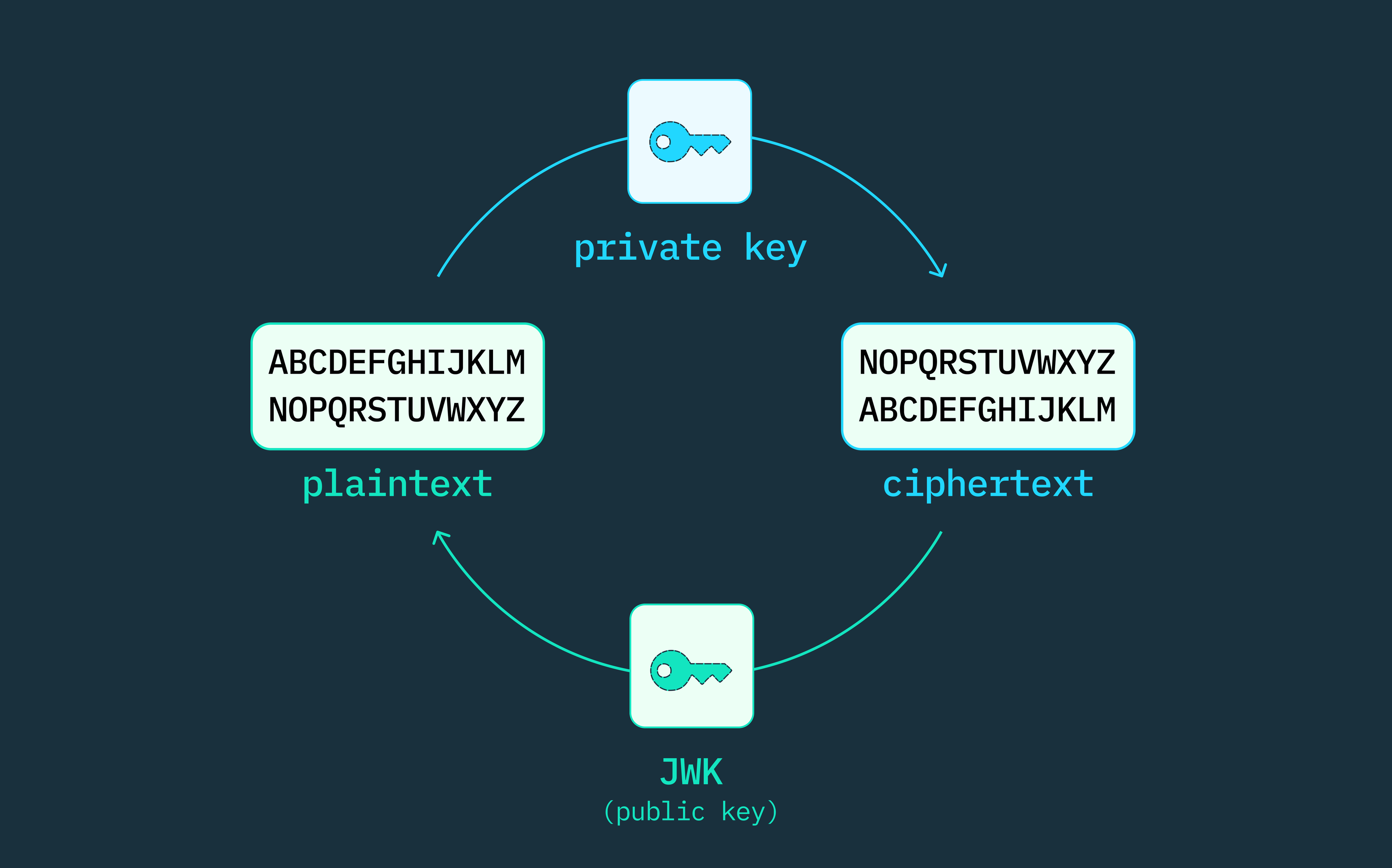
Auth & identity
Feb 29, 2024
Understanding JWKS: JSON Web Key Set Explained

Auth & identity
Feb 23, 2024
B2B SaaS applications: A comprehensive overview

Auth & identity
Feb 13, 2024
What is SaaS integration and why should developers consider it?
Auth & identity
Feb 9, 2024
RBAC vs PBAC vs ABAC
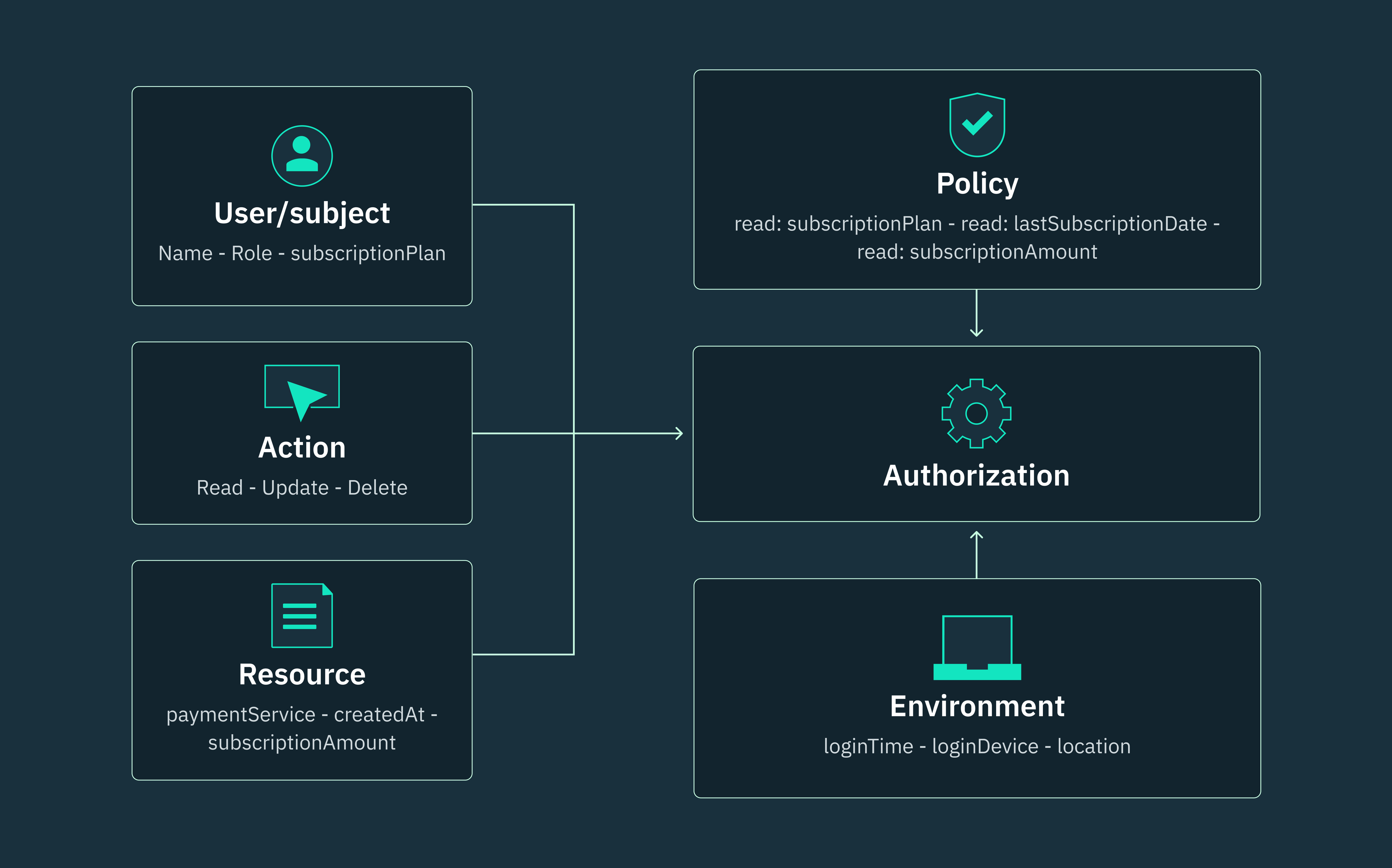
Auth & identity
Feb 6, 2024
What is attribute-based access control (ABAC)
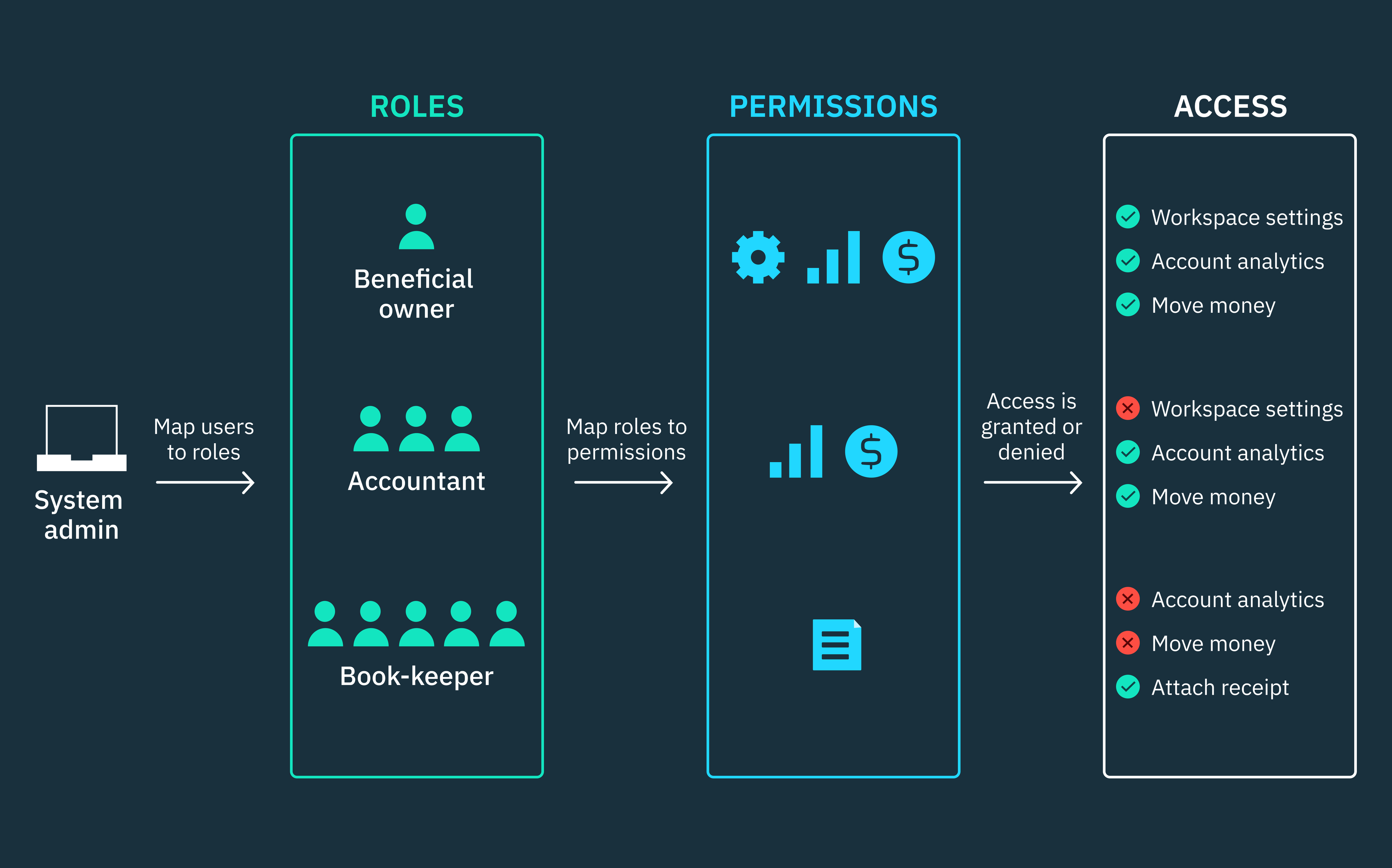
Auth & identity
Jan 29, 2024
What is role-based access control (RBAC)?

Auth & identity
Jan 26, 2024
Keycloak alternatives for enterprise authentication and identity management
Auth & identity
Engineering
Jan 12, 2024
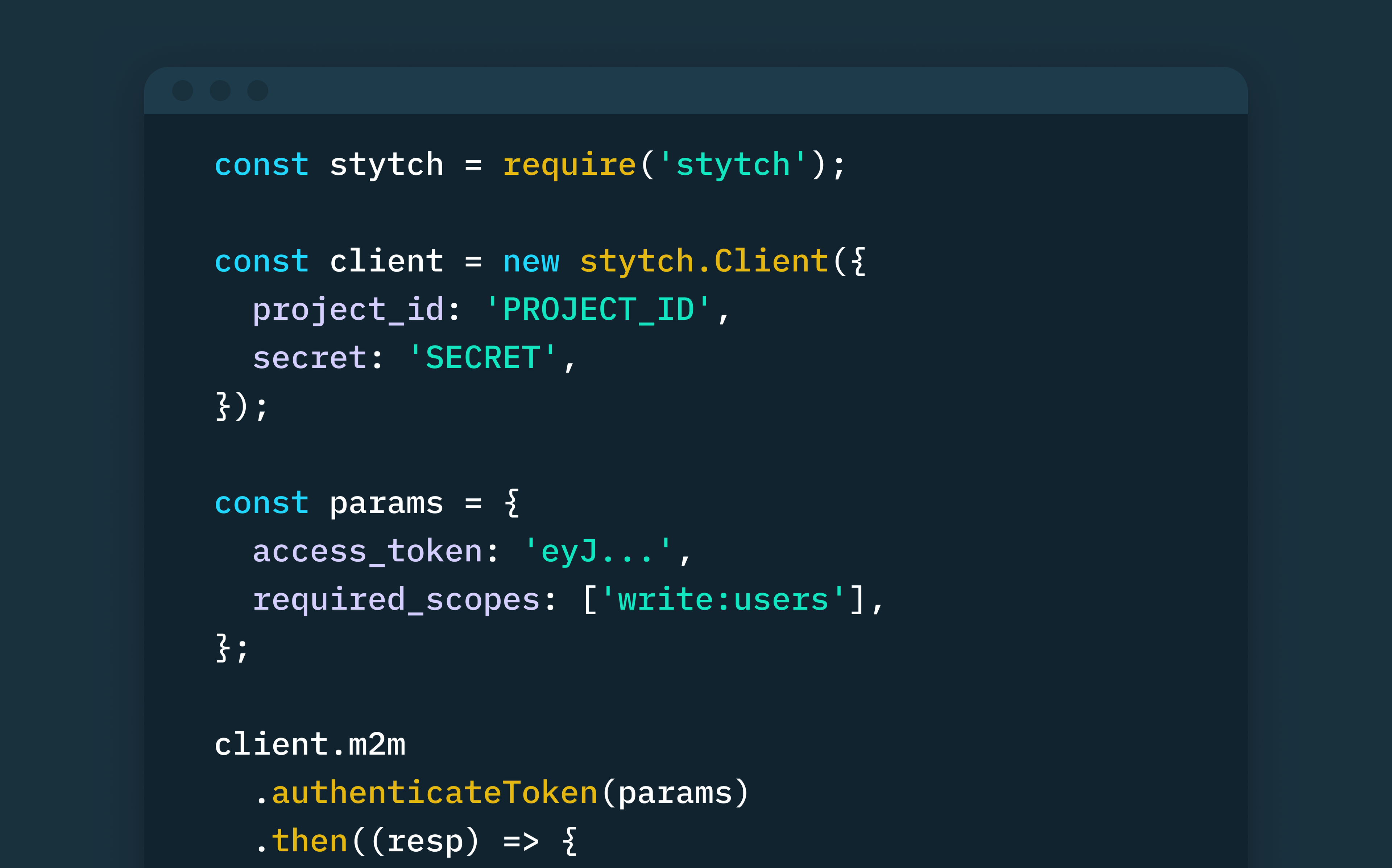
How to securely implement M2M authentication and authorization in Node.js using Stytch

Auth & identity
Jan 11, 2024
What is a reverse proxy?
Auth & identity
Dec 29, 2023
Scalper bots: The box office boom no one wants
Company
Engineering
Dec 29, 2023
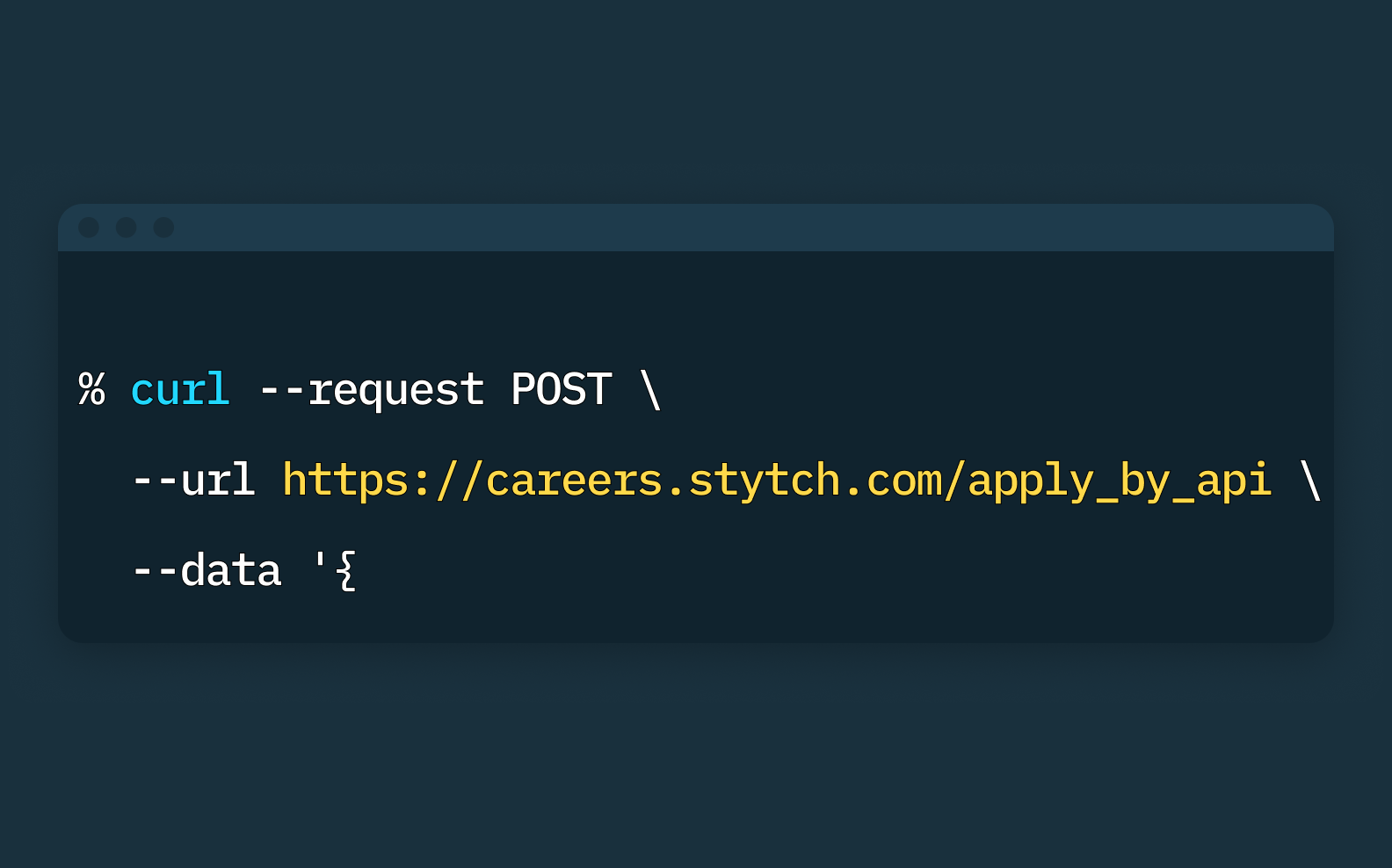
Apply by API: Making job applications developer-focused
Auth & identity
Engineering
Dec 26, 2023
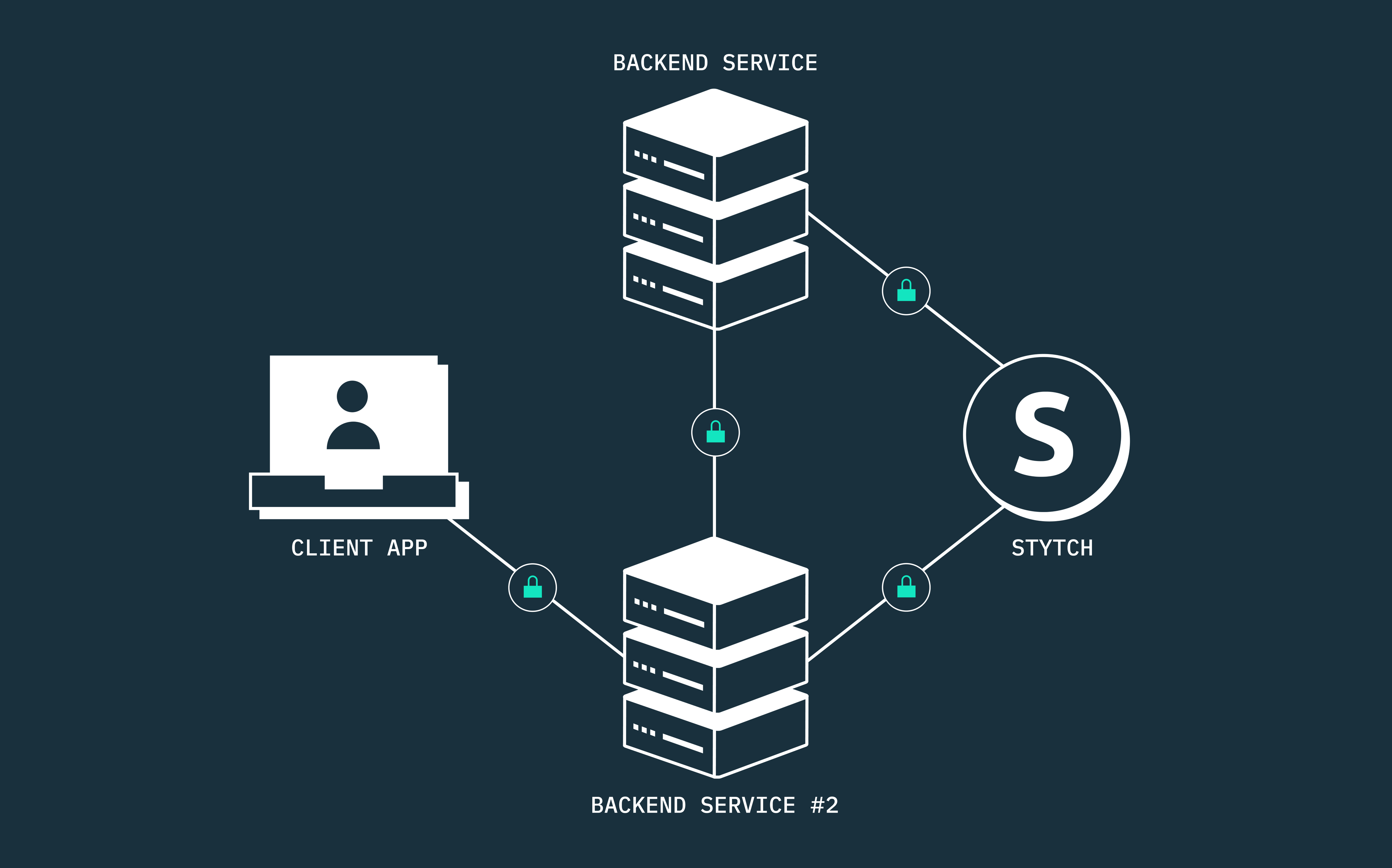
The complete guide to machine-to-machine (M2M) authentication and authorization
Auth & identity
Dec 22, 2023
Bot mitigation software: A fraudster's foil in an automated world
Engineering
Dec 21, 2023
Optimizing DBs at scale: how we reduced writes by 1000x for one of our most accessed tables
Auth & identity
Dec 14, 2023
Beating back bot fraud in 2024
Auth & identity
Product
Dec 5, 2023
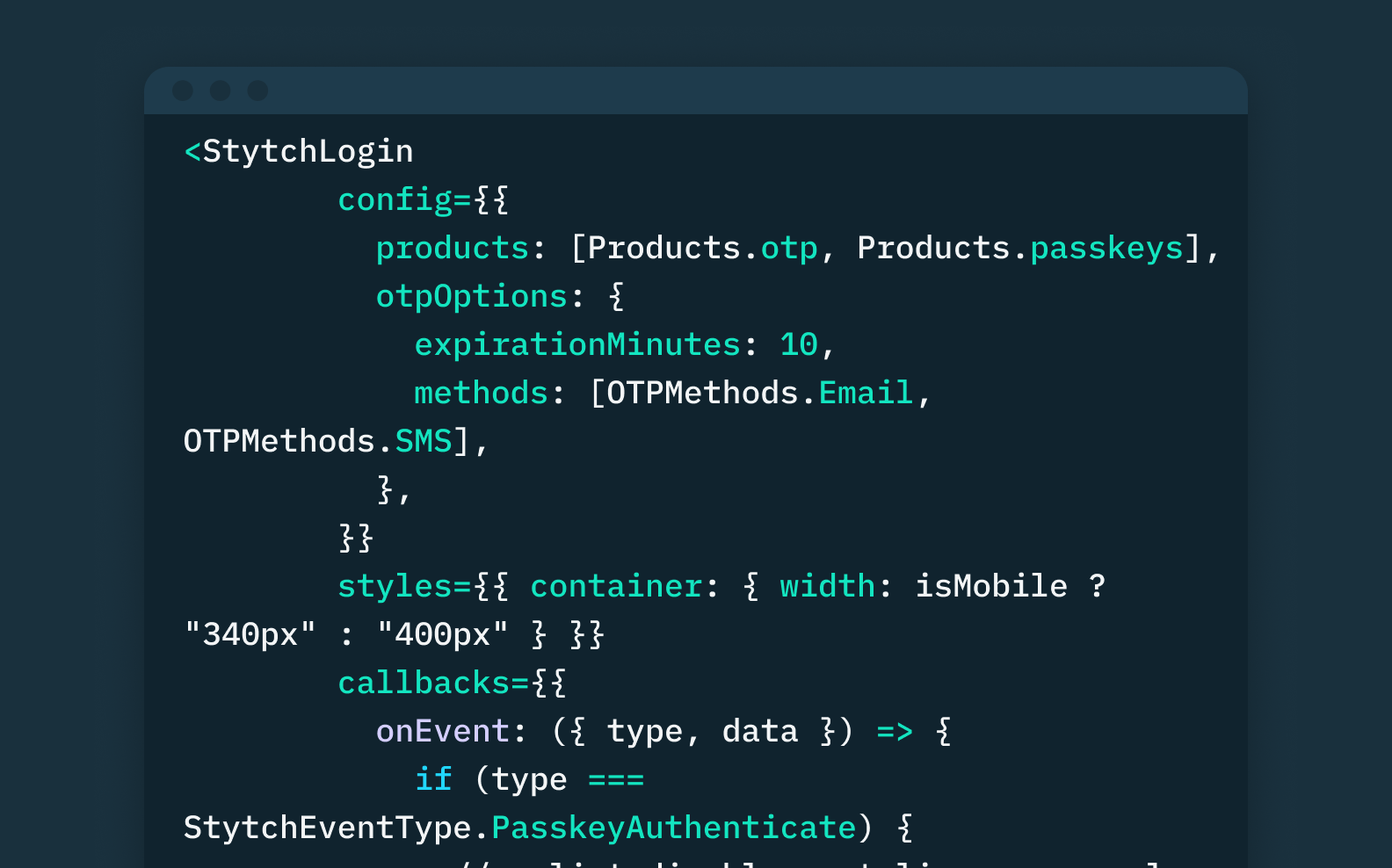
Introducing Passkeys authentication
Engineering
Product
Dec 5, 2023
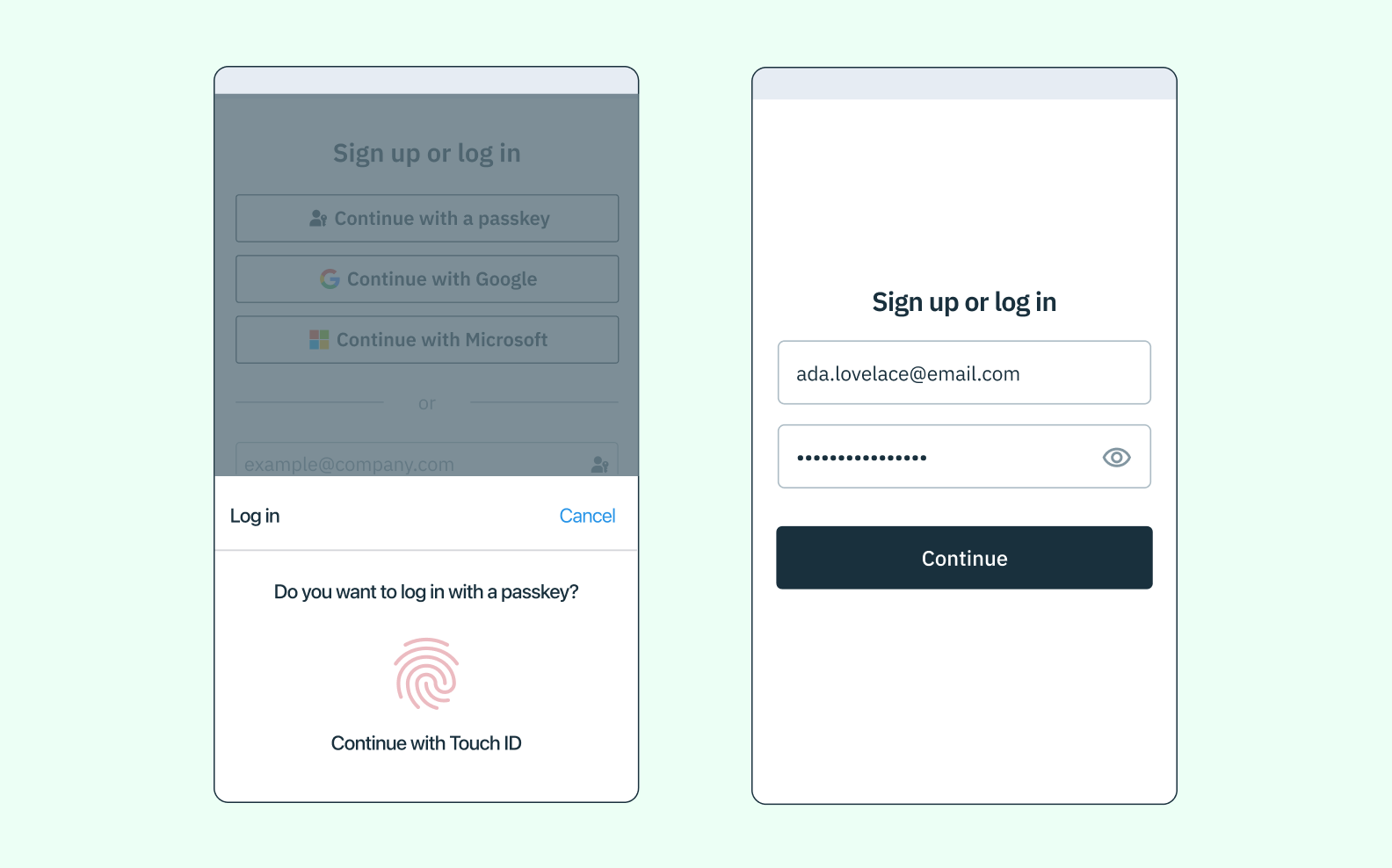
Log in with Passkeys: an example app using React and Stytch’s frontend SDK
Auth & identity
Dec 5, 2023
Passkey authentication: The cure for password dependency?
Auth & identity
Dec 1, 2023
Passkey vs. password: a new era of secure authentication

Auth & identity
Nov 27, 2023
What is a common indicator of a phishing attempt?

Auth & identity
Nov 21, 2023
What is a bot and how do they work
Auth & identity
Nov 10, 2023
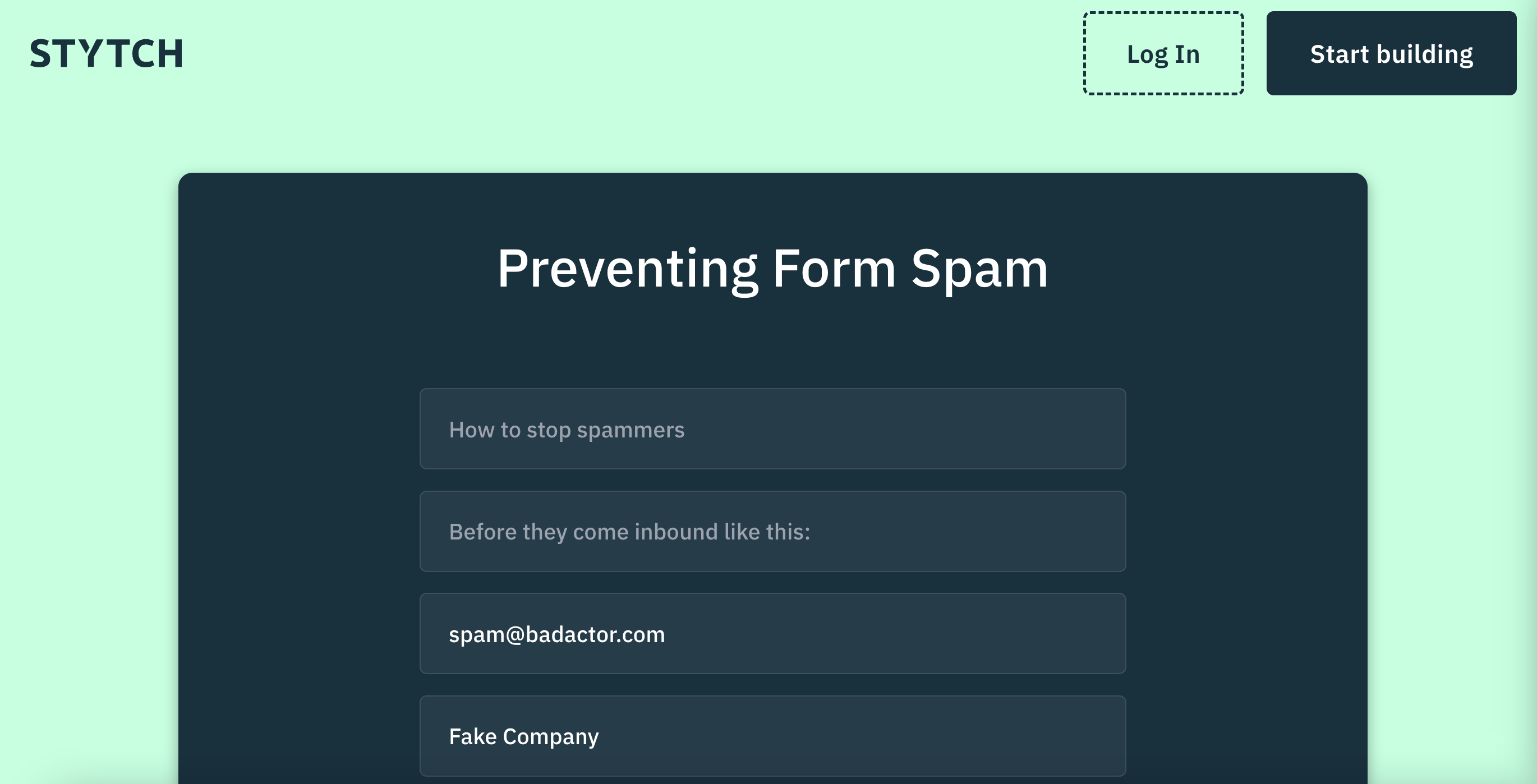
Preventing contact spam form submissions
Auth & identity
Nov 8, 2023
One-Time Password (OTP) bots: what they are and how to stop them
Auth & identity
Nov 3, 2023
What is fraud prevention?
Auth & identity
Nov 1, 2023
What is browser fingerprinting?
Auth & identity
Oct 23, 2023
What is SIM-swap scam, and how can you protect your users against one?

Engineering
Oct 20, 2023
Upleveling our SQL models to manage DBT query speeds

Auth & identity
Oct 4, 2023
JWT claims

Auth & identity
Oct 3, 2023
Evaluating Auth0 alternatives for authentication and authorization

Auth & identity
Oct 3, 2023
What is a JSON web token?

Company
Sep 27, 2023
So you want to write an Engineering career ladder?

Engineering
Sep 1, 2023
Open-sourcing SQX, a way to build flexible database models in Go
Company
Sep 1, 2023
Our approach to developer-focused conferences

Auth & identity
Sep 1, 2023
How to manage Auth0’s rules and hooks deprecation: a shift towards actions

Auth & identity
Aug 30, 2023
Extending authorization code flows with PKCE
Auth & identity
Aug 30, 2023
What is an enumeration attack?

Auth & identity
Aug 30, 2023
How to prevent enumeration attacks
Engineering
Jul 18, 2023
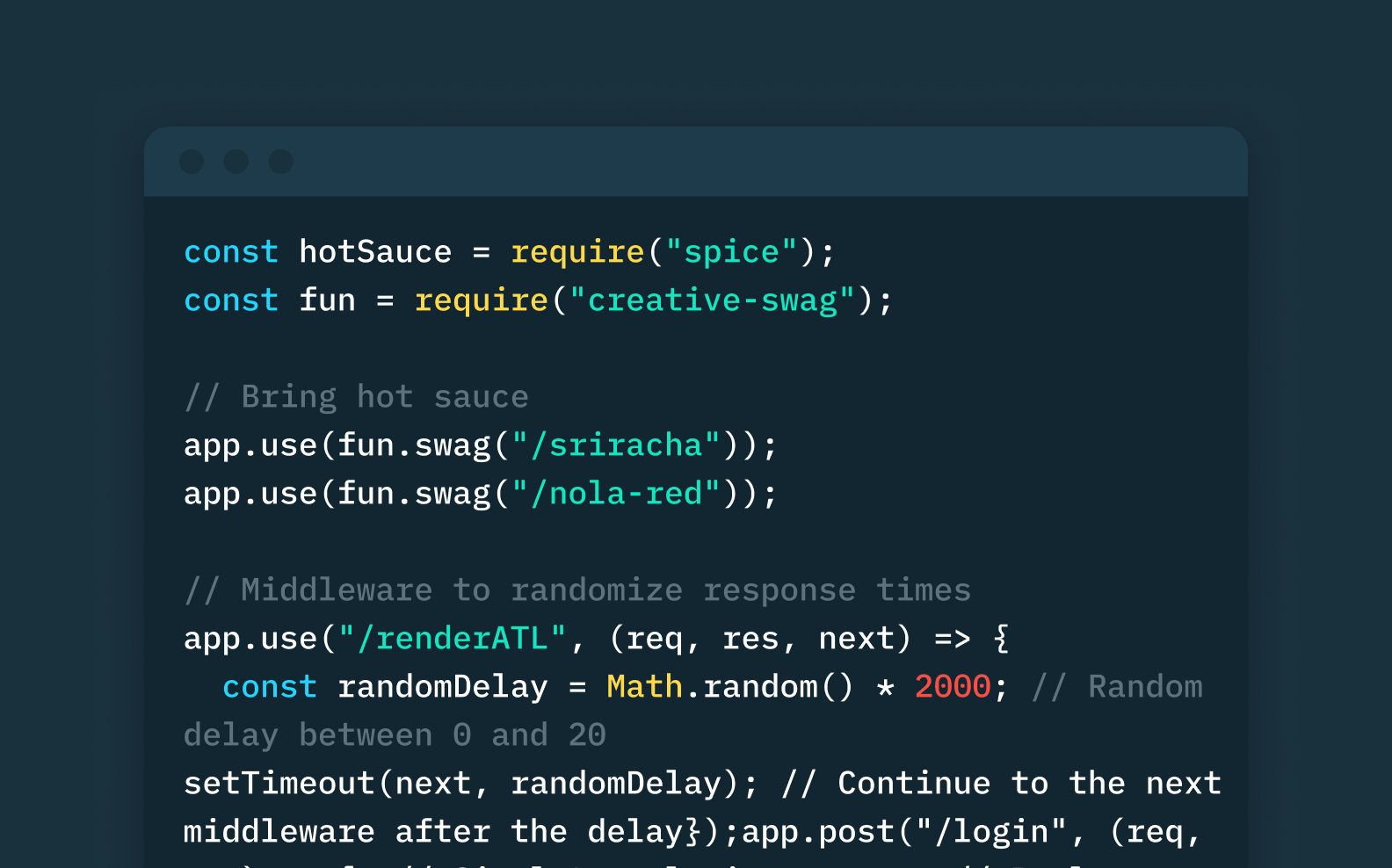
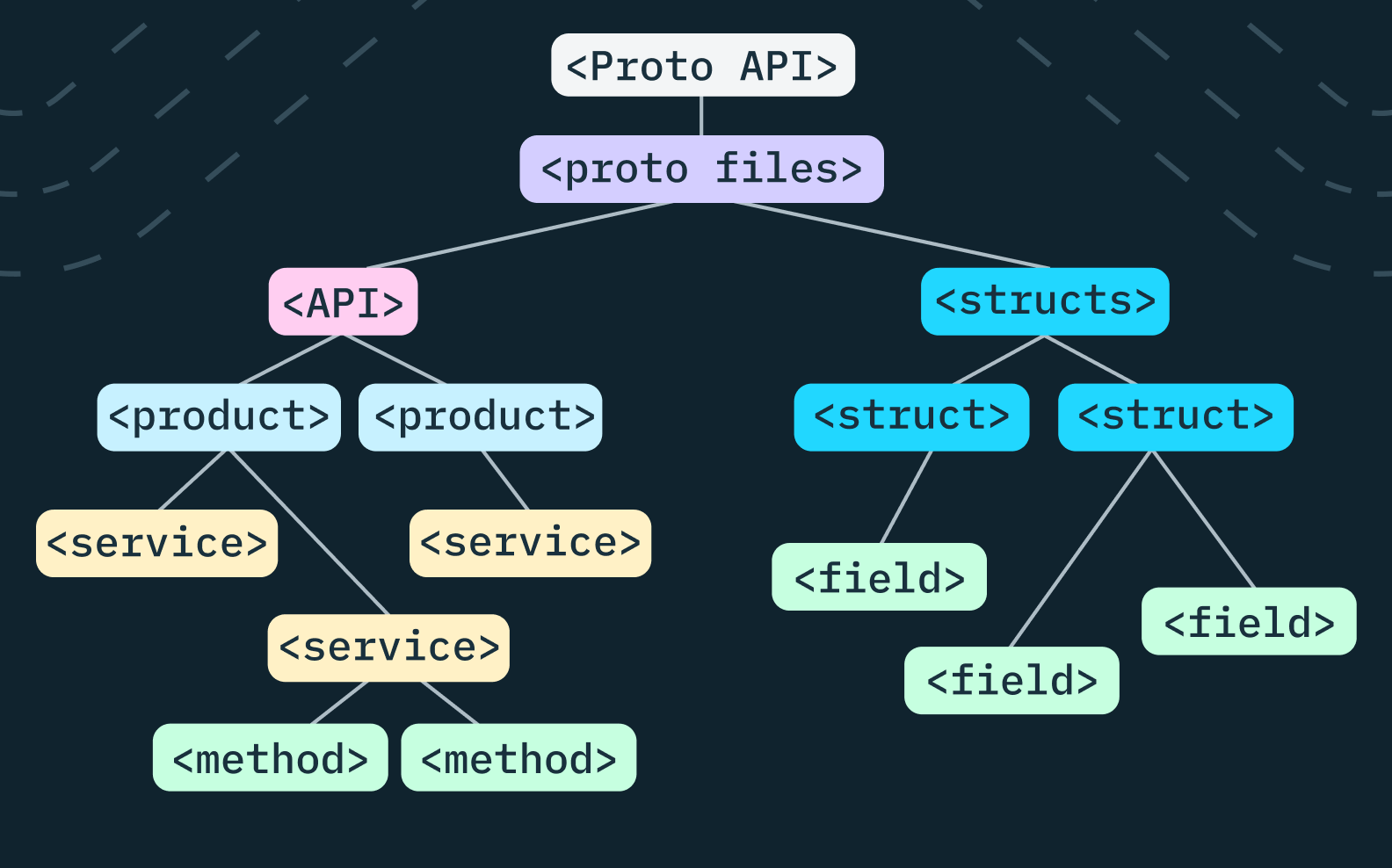
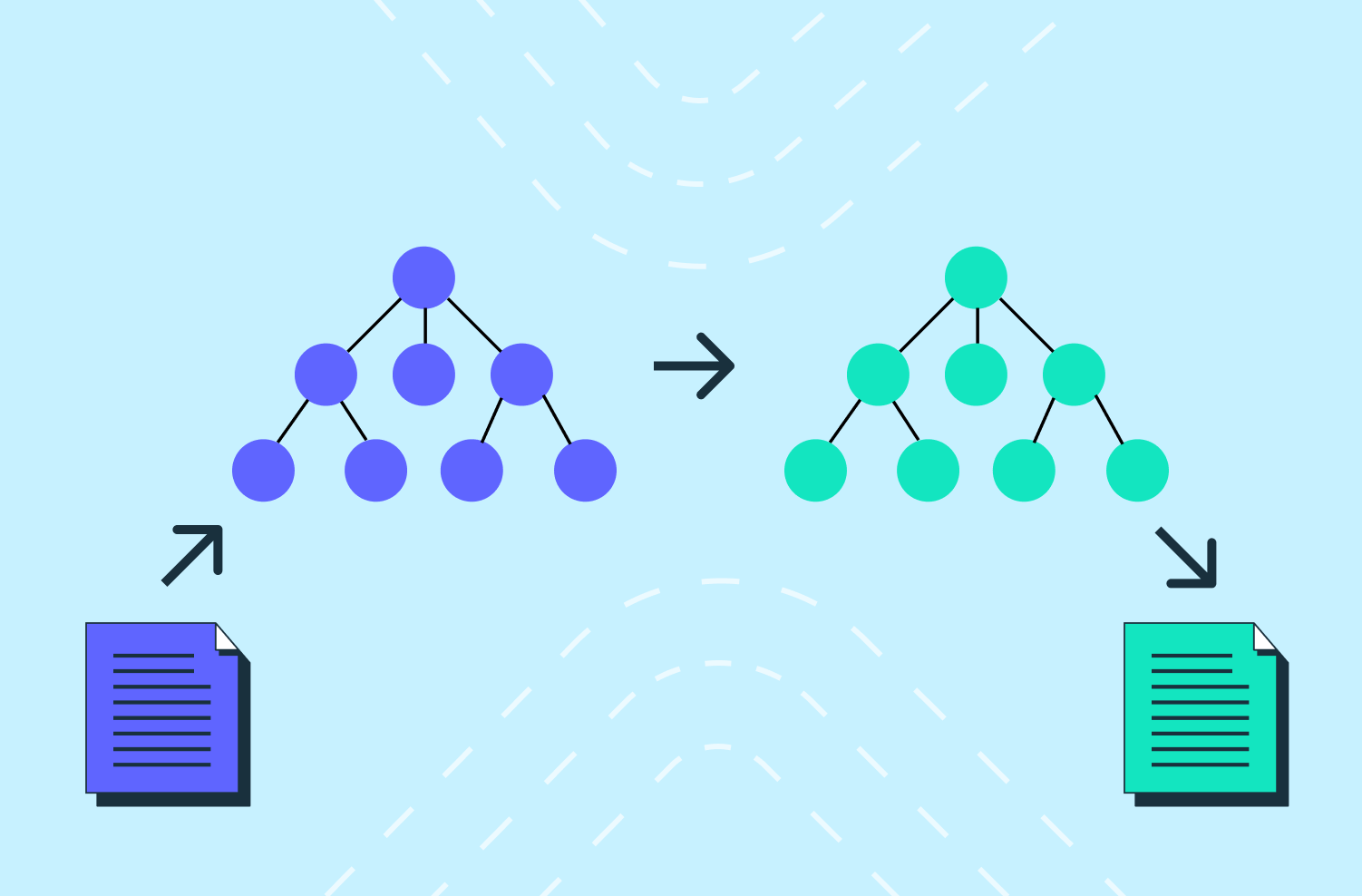
Generating "humanlike" code for our backend SDKs
Engineering
Jul 12, 2023
What does compiler theory have to do with auth?

Auth & identity
Jul 11, 2023
The journey to ISO 27001 certification
Engineering
Jul 10, 2023
An engineer’s guide to mobile biometrics: Android Keystore pitfalls and best practices

Auth & identity
Jul 10, 2023
The top 10 password cracking techniques – and how to outmaneuver them

Company
Jun 23, 2023
Stytch events with Orb: securing and pricing AI products
Product
Jun 2, 2023
Introducing B2B Authentication

Engineering
May 3, 2023
An engineer's guide to mobile biometrics: event- vs result-based
Engineering
May 3, 2023
An engineer's guide to mobile biometrics: step-by-step

Company
May 2, 2023
Stytch Talks with Enzo Avigo: Building a high-performing B2B sign up flow

Product
Apr 27, 2023
Build a no-code signup & onboarding flow with Feathery + Stytch

Product
Apr 24, 2023
Make a memorable first impression with messaging from Enveloop + Stytch

Product
Apr 17, 2023
Announcing new pricing and self-serve options
Auth & identity
Apr 12, 2023
IdP- vs SP-initiated SSO
Apr 10, 2023
What is SOC 1 Type 2?
Auth & identity
Apr 1, 2023
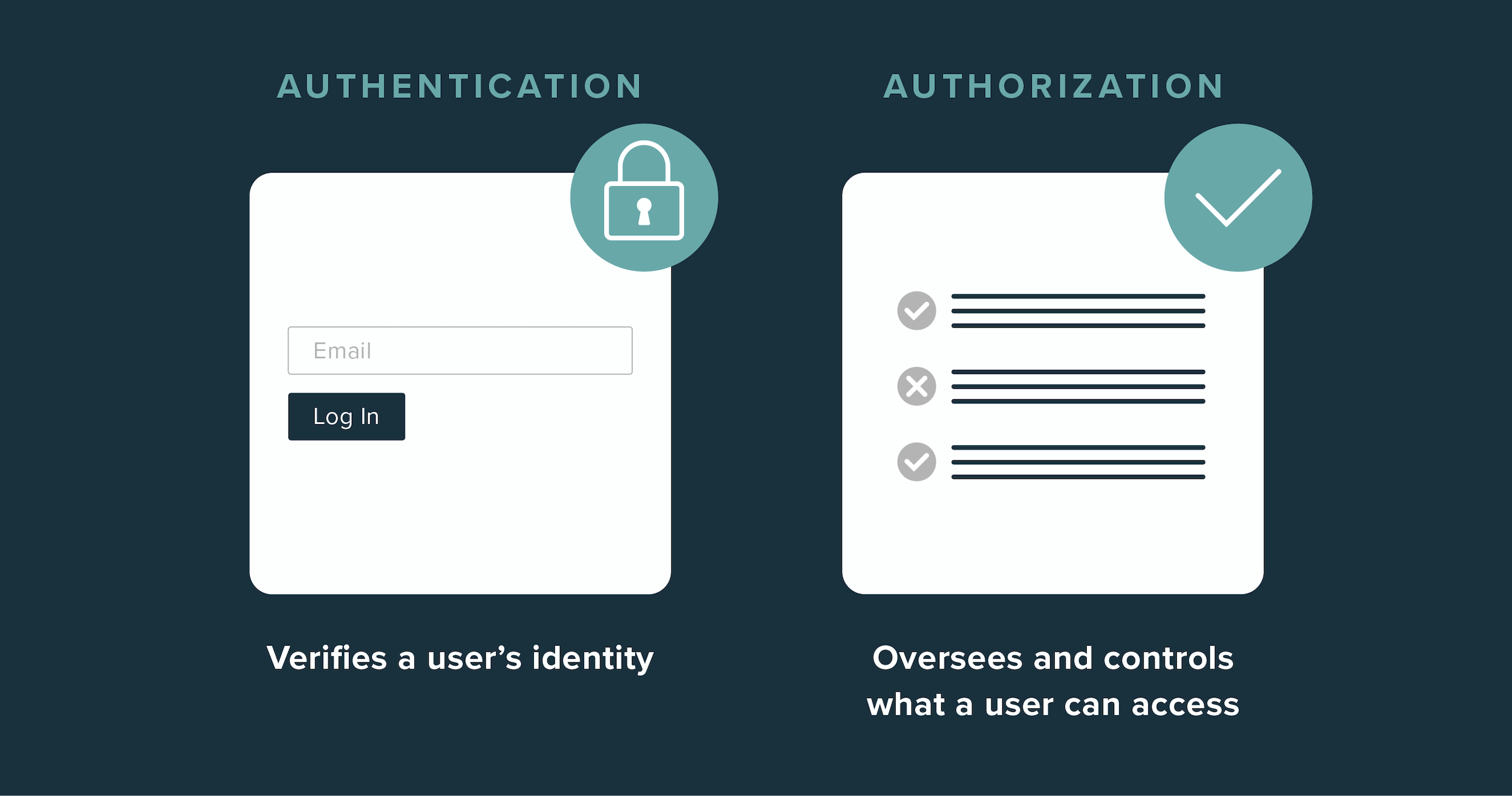
Authentication vs. authorization: what you need to know

Auth & identity
Mar 23, 2023
What is OAuth 2.0?
Auth & identity
Mar 21, 2023
How do voice recognition biometrics work?

Engineering
Mar 17, 2023
Stytch postmortem 2023-02-23
Auth & identity
Mar 16, 2023
Foundations of scalable B2B auth
Auth & identity
Company
Mar 15, 2023
Stytch Talks With Jordan Burris: “The Future of Multi-Factor Authentication (MFA)”

Product
Mar 9, 2023
Onboarding the next Web3 wave with Crossmint + Stytch

Auth & identity
Mar 1, 2023
Argon2 vs bcrypt vs. scrypt: which hashing algorithm is right for you?

Auth & identity
Feb 23, 2023
What is a passkey?

Auth & identity
Feb 15, 2023
All about biometric authentication

Auth & identity
Feb 13, 2023
What is passwordless authentication?
Auth & identity
Feb 10, 2023
What are one-time passcodes (OTPs)?
Auth & identity
Feb 6, 2023
Bot mitigation for identity and access management

Auth & identity
Feb 2, 2023
The FIDO alliance and a passwordless future
Auth & identity
Feb 1, 2023
Balancing security and adoption: preventing account takeover fraud with multi-factor authentication
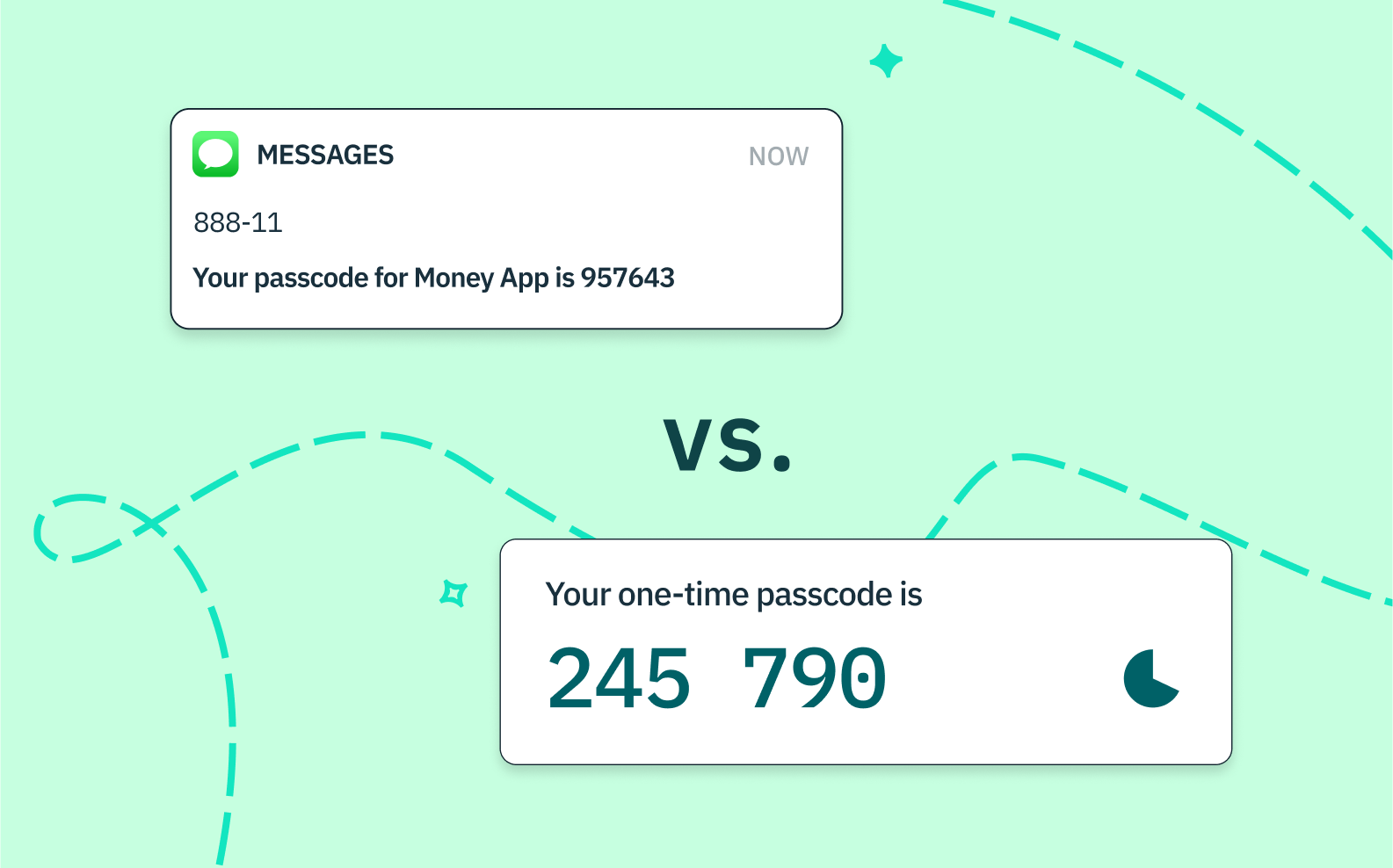
Auth & identity
Feb 1, 2023
TOTP vs SMS: Which one is better for two-factor authentication (2FA)?
Company
Jan 24, 2023
Stytch Talks with Jaren Glover: Building high-powered engineering teams

Auth & identity
Jan 23, 2023
JWTs vs. sessions: which authentication approach is right for you?

Auth & identity
Engineering
Jan 20, 2023
Choosing a B2B auth provider

Company
Jan 11, 2023
Stytch honored with BuiltIn's 2023 Best Places to Work award
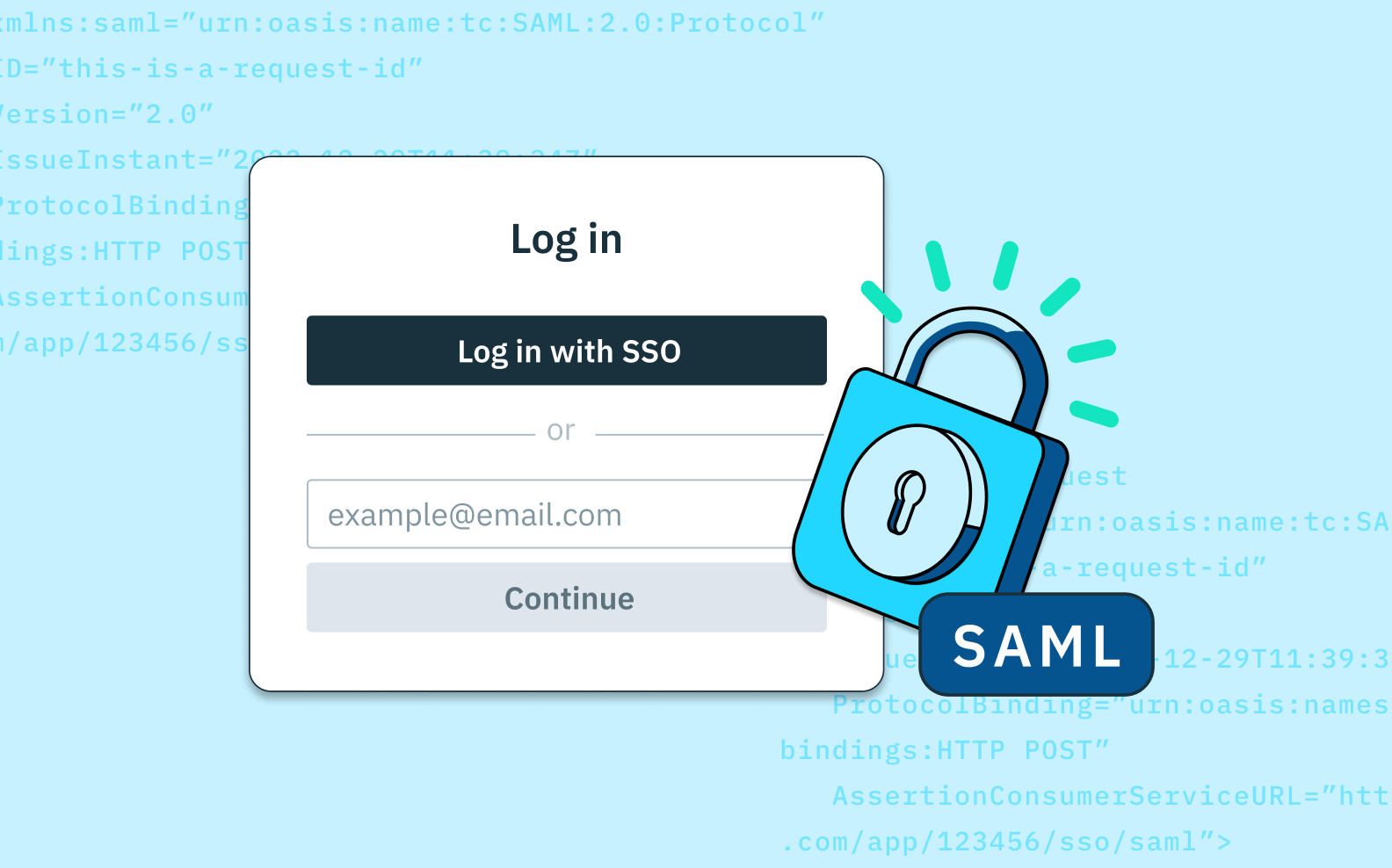
Auth & identity
Engineering
Jan 10, 2023
What is Security Assertion Markup Language (SAML) and how does it work?

Auth & identity
Engineering
Dec 16, 2022
What is OpenID Connect (OIDC)?
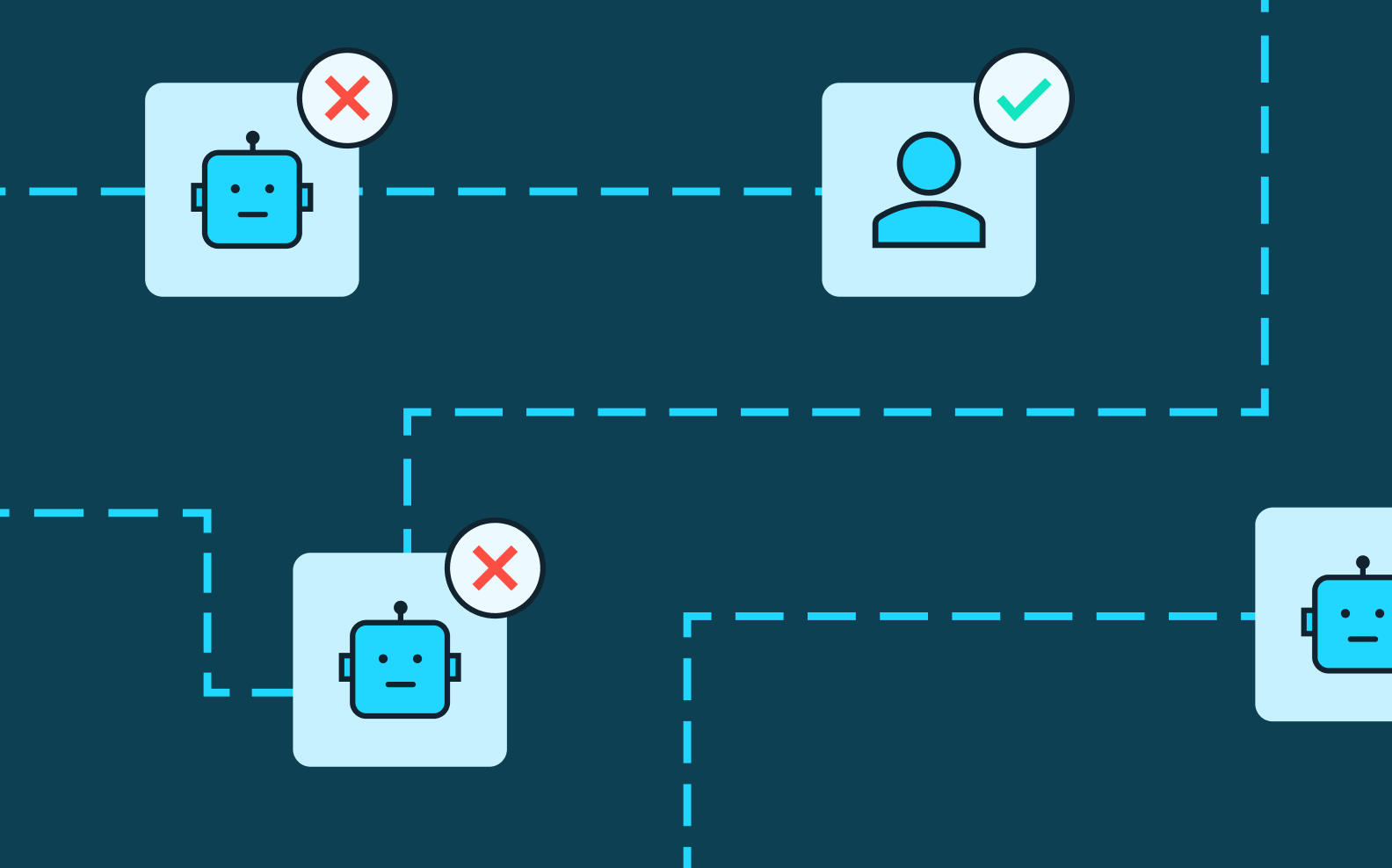
Auth & identity
Dec 16, 2022
Securing AI against bot attacks
Product
Dec 10, 2022
Stytch + Cerbos + FastAPI: Flexible authentication meets decoupled role and access management
Auth & identity
Engineering
Dec 9, 2022
SSO protocols: SAML vs. OIDC

Product
Dec 6, 2022
Designing Passwords in the Stytch SDKs
Company
Engineering
Dec 3, 2022
Engineering the engineering team
Auth & identity
Engineering
Nov 22, 2022
What is single sign on (SSO) and how does it work?
Auth & identity
Nov 17, 2022
What is CAPTCHA, and how does it work?
Auth & identity
Engineering
Nov 17, 2022
Organization tenancy: the foundation of SSO and B2B data models

Engineering
Nov 16, 2022
The remote dev decision: part one
Auth & identity
Engineering
Nov 4, 2022
Introducing B2B Auth School

Auth & identity
Nov 4, 2022
Anatomy of a strong password
Auth & identity
Oct 27, 2022
Do passkeys live up to the hype?

Company
Product
Oct 26, 2022
Stytch Q3 wrap-up

Auth & identity
Oct 24, 2022
What is unphishable MFA?

Auth & identity
Oct 13, 2022
The importance of investing in unphishable authentication

Product
Oct 12, 2022
Introducing Strong CAPTCHA, Stytch’s answer to CAPTCHA fraud

Company
Oct 7, 2022
Stytch named as top authentication provider by Cybernews

Company
Oct 4, 2022
How to use references in your hiring process
Auth & identity
Company
Sep 29, 2022
Stytch Talks with Brian Hale: rethinking user sign-up and login to unlock growth

Company
Sep 28, 2022
Go big or go home: why it’s never too early to think about enterprise

Auth & identity
Sep 16, 2022
What is identity and access management (IAM)?
Product
Sep 13, 2022
How we (re)made Passwords for next-generation auth

Auth & identity
Sep 8, 2022
How compromised passwords lead to data breaches
Auth & identity
Sep 1, 2022
What is TOTP and why does it matter?
Auth & identity
Aug 31, 2022
Making auth your growth lever

Auth & identity
Aug 30, 2022
The definitive guide to choosing a Customer and Identity Access Management (CIAM) solution
Auth & identity
Aug 25, 2022
Eliminate bot attacks from the CAPTCHA equation
Auth & identity
Aug 24, 2022
Multi-factor authentication: how to choose the right approach for your business
Auth & identity
Aug 23, 2022
Step-up versus multi-factor authentication (MFA)
Auth & identity
Aug 17, 2022
Stytch’s guide to adding passwordless options for password-based auth flows
Auth & identity
Aug 15, 2022
How to prevent account takeover (ATO) and improve user authentication

Company
Aug 11, 2022
A founder’s guide to raising your seed round
Auth & identity
Aug 11, 2022
What is password salting?

Company
Aug 4, 2022
How the API economy can radically transform your business

Company
Aug 3, 2022
It's a (double) Stytchiversary! Meet Aiden Forrest & Ovadia Harary

Auth & identity
Company
Jul 28, 2022
Stytch vs. Amazon Cognito

Auth & identity
Jul 27, 2022
What is password hashing?

Auth & identity
Jul 18, 2022
Protect against password spraying
Product
Jul 15, 2022
Stytch introduces a modern upgrade to Passwords

Auth & identity
Jul 13, 2022
How Apple’s passkeys just brought us one step closer to a passwordless internet

Company
Jun 23, 2022
It's a Stytchiversary! Meet Shane O'Neill!

Product
Jun 10, 2022
Landing Email Magic Links in your user's inbox

Company
Jun 3, 2022
It's a Stytchiversary! Meet Spyri Karasavva!
Auth & identity
Product
Jun 2, 2022
4 Ways to use Stytch's Embeddable Magic Links

Company
Jun 1, 2022
It’s a Stytchiversary! Meet Allison Chuang!
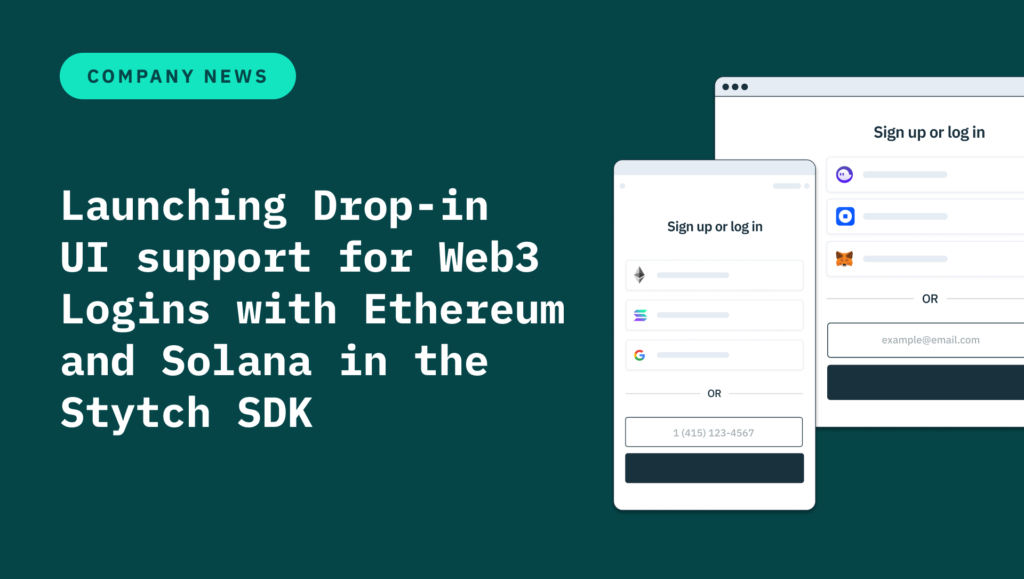
Product
May 31, 2022
Launching Drop-in UI support for Web3 Logins with Ethereum and Solana in the Stytch SDK

Company
May 26, 2022
Painting the town Stytch: the making of an OOH campaign

Product
May 18, 2022
Introducing JWTs for session management

Product
May 17, 2022
Vessel + Ratio: making crypto accessible

Product
May 16, 2022
Behind the scenes with Vessel: designing a brand for the first-ever passport for the internet

Product
May 11, 2022
Introducing Vessel, powered by Stytch

Company
May 10, 2022
It's a Stytchiversary with Cass Roulund!

Auth & identity
May 4, 2022
Web3 and the future of data portability: rethinking user experiences and incentives on the internet
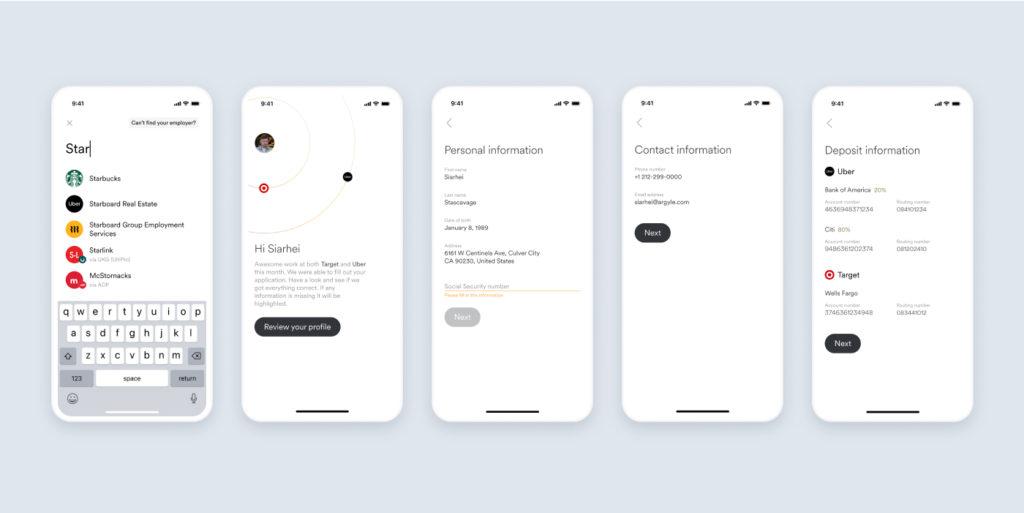
Product
May 3, 2022
FinanceNow demo app - powered by Argyle, Unit, and Stytch

Auth & identity
Apr 22, 2022
Save time, save the planet–go passwordless!

Company
Apr 19, 2022
It's a Stytchiversary with Jeremy Kaplan!
Product
Apr 13, 2022
Introducing Log in with Solana
Product
Apr 11, 2022
Stytch’s new Javascript SDK
Product
Apr 1, 2022
Log in with username

Product
Mar 30, 2022
Build a custom client portal on Airtable using Sequin, Stytch and Next.js
Product
Mar 23, 2022
Introducing Log in with Ethereum

Product
Mar 21, 2022
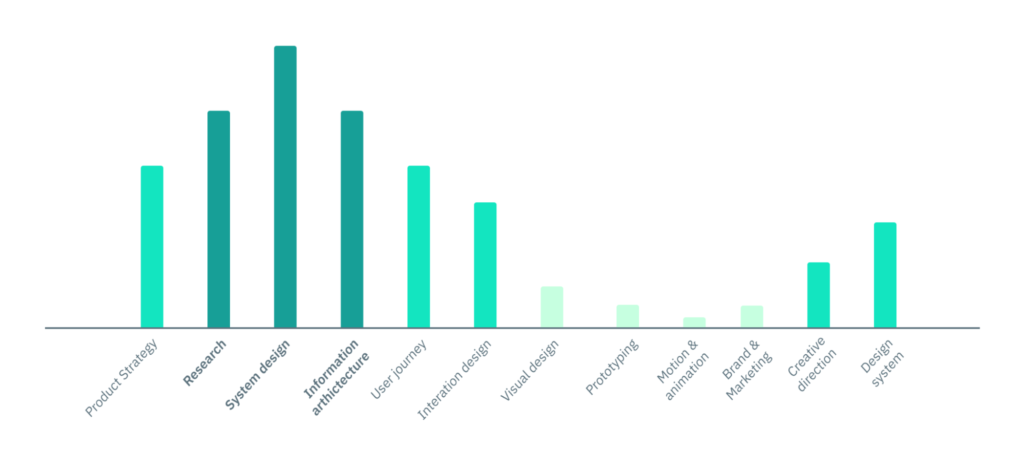
Making research an integral part of your product strategy

Product
Mar 18, 2022
Auth0 pricing (and four other reasons to choose Stytch)
Auth & identity
Mar 16, 2022
What is WebAuthn?

Company
Mar 15, 2022
It's a Stytchiversary! Meet Nikhil Dilip, software engineer

Auth & identity
Mar 12, 2022
Password reuse is a cybersecurity threat
Auth & identity
Feb 24, 2022
Build vs. buy: what to consider when setting up an auth flow
Product
Feb 17, 2022
5 Lessons for founding designers: what I’ve learned in my first year at Stytch

Company
Feb 16, 2022
Spotlight on Dennis Huang

Company
Feb 7, 2022
We've moved!

Company
Jan 31, 2022
Derek St. Onge
Auth & identity
Jan 28, 2022
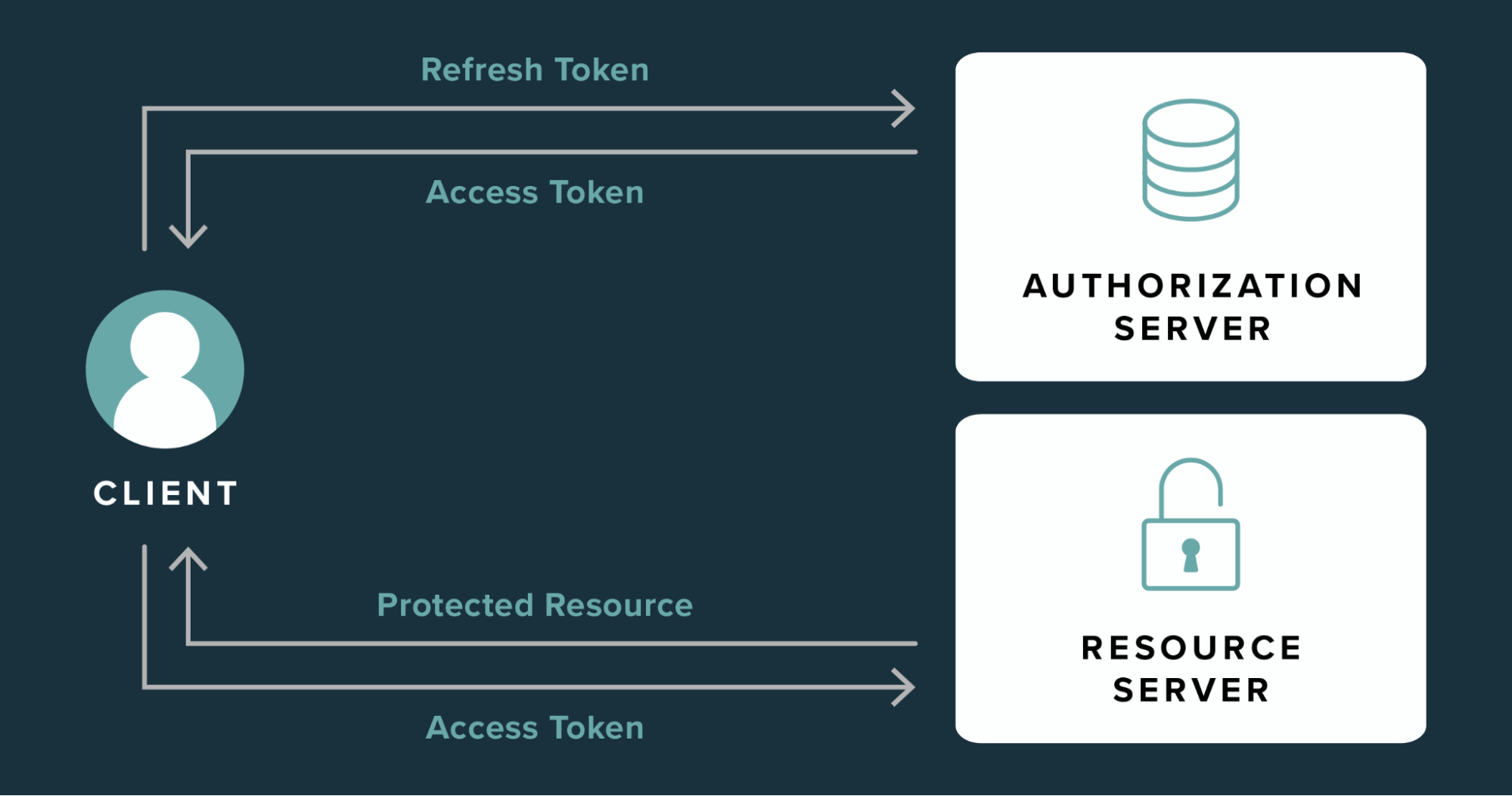
What is the purpose of a refresh token?
Product
Jan 25, 2022
SDK vs. API: What's the difference?
Product
Jan 24, 2022
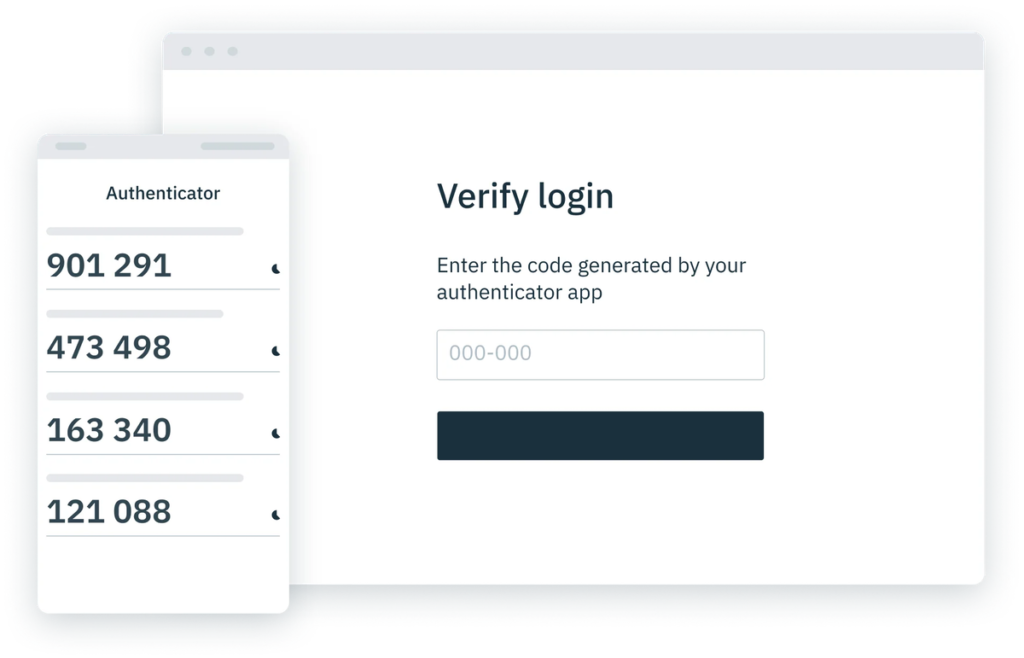
Introducing TOTP Authentication for Next-Level Security

Auth & identity
Jan 18, 2022
10 common cyber attacks

Company
Jan 11, 2022
Bingrui Tang
Auth & identity
Jan 10, 2022
What is MFA (Multi-Factor Authentication) and how does it work?

Auth & identity
Jan 5, 2022
What is credential stuffing? How to prevent credential stuffing attacks
Auth & identity
Dec 17, 2021
An introduction to WebAuthn

Product
Dec 8, 2021
Improving conversion with Google One Tap

Company
Nov 18, 2021
Announcing Stytch's $90M Series B at a $1B Valuation

Auth & identity
Nov 12, 2021
A guide to passwordless authentication solutions by business vertical

Engineering
Nov 9, 2021
Building an app with Stytch and PlanetScale

Product
Nov 1, 2021
Designing for dark mode
Company
Oct 26, 2021
Alex Zaldastani

Engineering
Oct 4, 2021
The ultimate guide to building user authentication into your Next.js application

Product
Sep 24, 2021
Engaging users with embedded authentication

Auth & identity
Sep 16, 2021
Stytch's guide to passwordless authentication

Company
Aug 24, 2021
Grace Baelen-King

Auth & identity
Jul 30, 2021
How just-in-time authentication boosts security and conversion
Company
Engineering
Jul 22, 2021
A founder's guide to hiring engineers
Authentication & Authorization
Fraud & Risk Prevention
© 2025 Stytch. All rights reserved.